漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0134081
漏洞标题:IDC服务商安全之睿江科技邮箱密码泄漏以及多个系统源码泄漏(可连接数据库)
相关厂商:efly.cc
漏洞作者: prolog
提交时间:2015-08-15 17:03
修复时间:2015-09-30 00:12
公开时间:2015-09-30 00:12
漏洞类型:重要敏感信息泄露
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-08-15: 细节已通知厂商并且等待厂商处理中
2015-08-16: 厂商已经确认,细节仅向厂商公开
2015-08-26: 细节向核心白帽子及相关领域专家公开
2015-09-05: 细节向普通白帽子公开
2015-09-15: 细节向实习白帽子公开
2015-09-30: 细节向公众公开
简要描述:
广东睿江科技有限公司成立于2007年,总部位于广东省佛山市,是中国领先的互联网基础服务提供商,致力于为全球的金融、电子商务、移动互联网、网络游戏、门户网站等企业提供最专业的互联网数据中心(IDC)、内容加速服务(CDN)、云计算(私有云解决方案及公有云云平台)及行业应用的整体解决方案。是一家在业务领域专注和专业的云计算数据中心运营商。
详细说明:
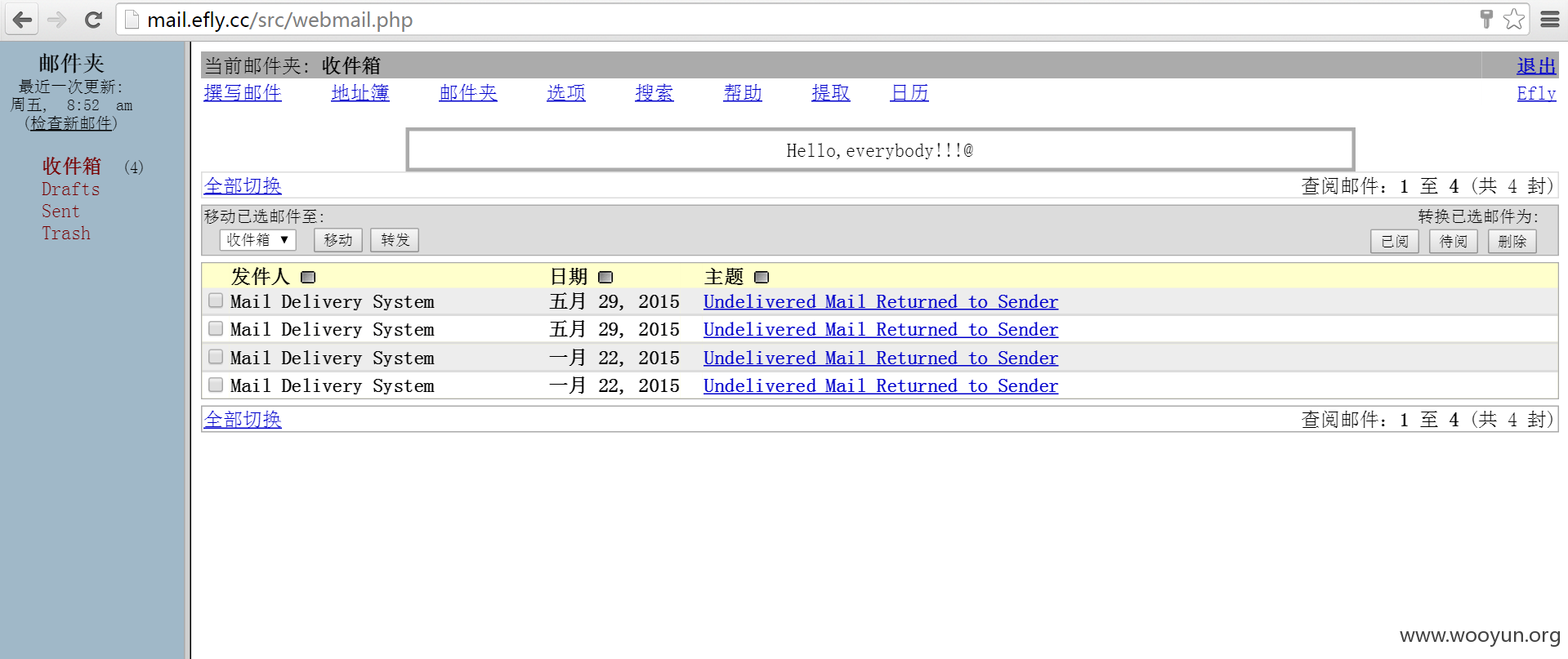
1.邮箱密码泄露可登陆
https://github.com/k518/ddd/blob/270d789b4f7fde0025adea88abcccbdb3cd5103b/monitor/test.py
mail = SendEmail('smtp.efly.cc', '[email protected]', 'eflydns123')
http://mail.efly.cc/src/login.php
2.数据库密码员工用户名,qq邮箱泄露
https://github.com/k518/ddd/blob/270d789b4f7fde0025adea88abcccbdb3cd5103b/monitor/proxy_test.py
db = MySQLdb.connect("localhost","root","rjkj@rjkj","dns_device_monitor")
mailto_list = ['[email protected]']
#mailto_list = ['[email protected]']
#mailto_list = ['[email protected]','[email protected]','[email protected]','[email protected]','[email protected]','[email protected]','[email protected]','[email protected]','[email protected]']
#mailto_list = ['[email protected]','[email protected]','[email protected]','[email protected]','[email protected]','[email protected]']
mail = SendEmail('smtp.efly.cc', '[email protected]', 'eflydns123')
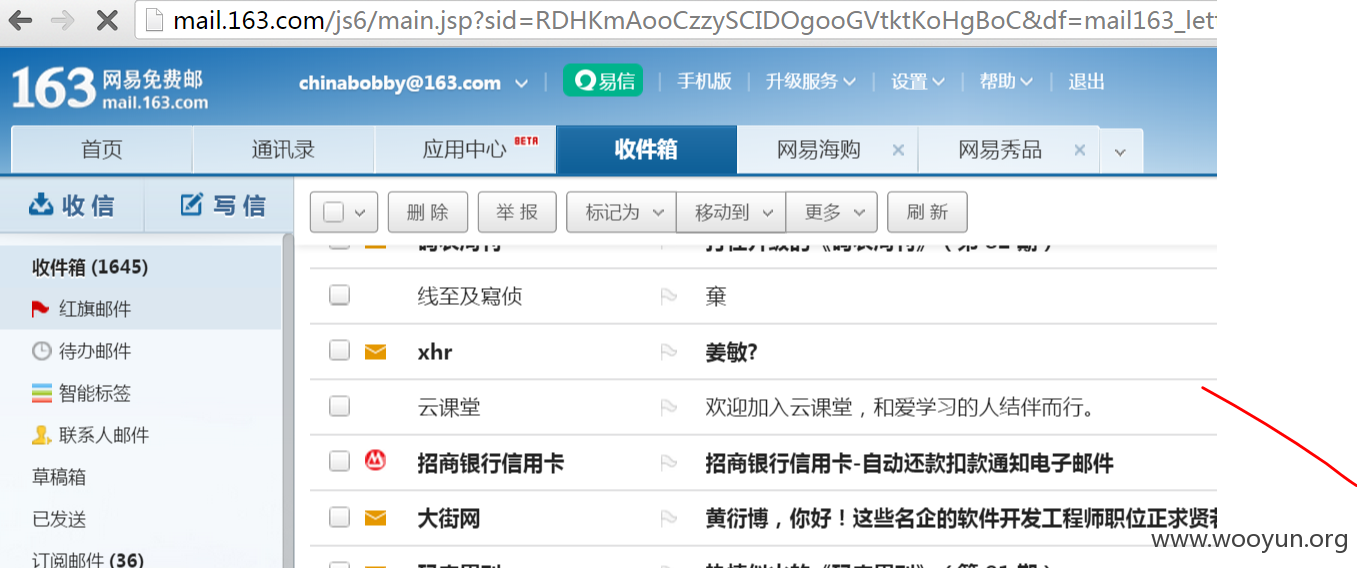
3.员工邮箱密码泄露
https://github.com/k518/ddd/blob/270d789b4f7fde0025adea88abcccbdb3cd5103b/monitor/mail_day.py
mail = SendEmail('smtp.163.com', '[email protected]', 'xinyi520')
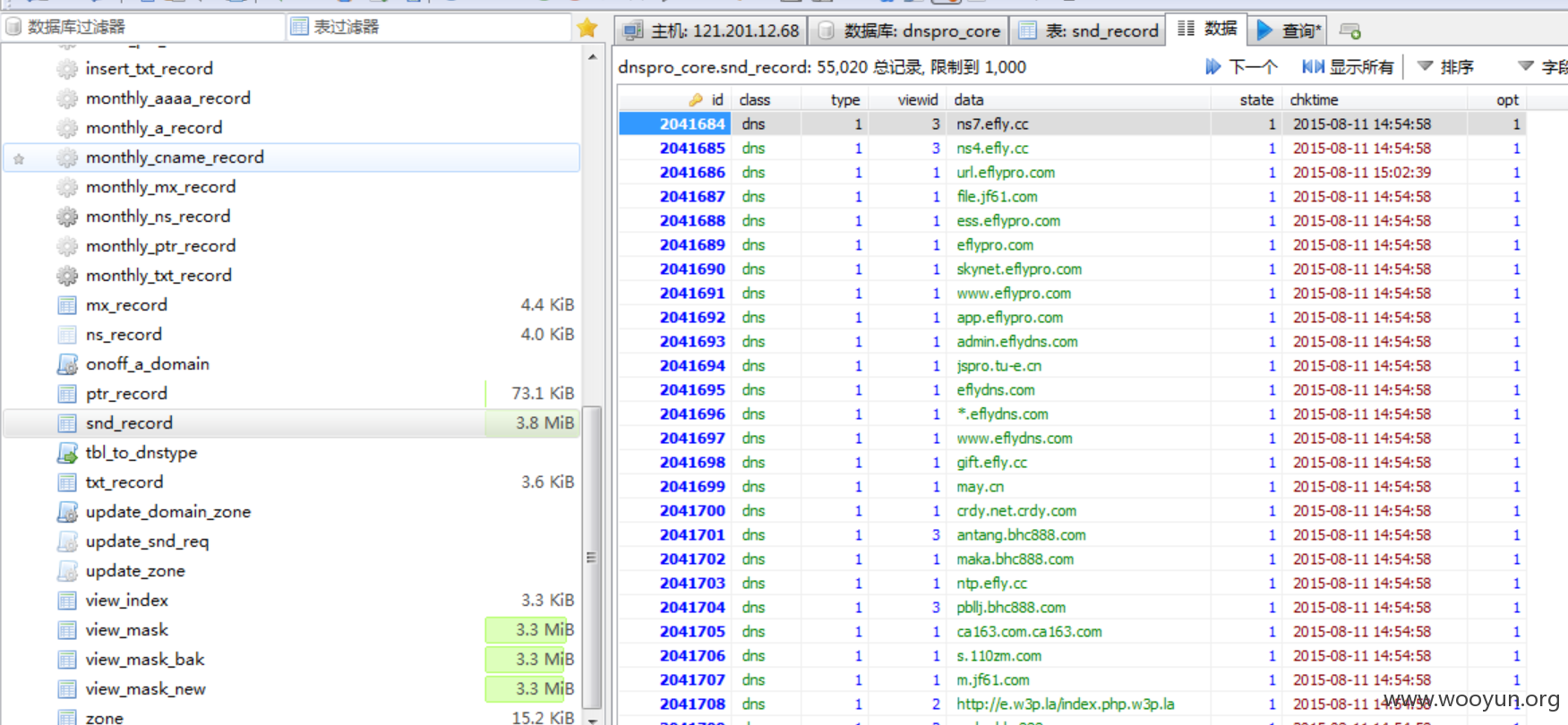
4.数据库密码泄露
https://github.com/k518/ddd/blob/270d789b4f7fde0025adea88abcccbdb3cd5103b/mgr/dbback.sh
mysqldump -h121.201.12.58 -uroot -prjkj@rjkj --opt -RB dnspro_core |gzip -9 > /media/wdata/linuxshare/db_backup/dnspro_core58-`date +%Y-%m-%d_%H%M%S`.sql.gz
mysqldump -h121.201.12.68 -uroot -prjkj@rjkj --opt -RB dnspro_core |gzip -9 > /media/wdata/linuxshare/db_backup/dnspro_core68-`date +%Y-%m-%d_%H%M%S`.sql.gz
https://github.com/k518/ddd/blob/270d789b4f7fde0025adea88abcccbdb3cd5103b/mgr/mgr_conf.py
g_db_ip= 'localhost' #经测试ip是121.201.12.68可连接
g_db_user= 'root'
g_db_passwd = 'rjkj@rjkj'
g_db_db = 'dnspro_core'
g_zkClis = '121.201.12.58:2181,121.201.12.60:2181,121.201.12.68:2181'
5.文档泄露
https://github.com/k518/ddd/tree/270d789b4f7fde0025adea88abcccbdb3cd5103b/doc
6.数据库脚本泄露管理员用户名密码
https://github.com/k518/ddd/blob/270d789b4f7fde0025adea88abcccbdb3cd5103b/dnsbroker/dnspro.sql
insert into `admin`(`id`,`user`,`pwd`,`desc`) values (1,'admin','rjkj@rjkj','');
insert into `server_list`(`id`,`sid`,`ip`,`type`,`subtype`,`status`,`desc`) values (1,'dns_broker_primary','121.201.12.60','dns_broker','primary','true','dns broker 中山BGP'),(2,'db_broker_primary','121.201.12.60','db_broker','primary','true','db broker 中山BGP'),(3,'task_mgr_primary','121.201.12.60','task_mgr','primary','true','task mgr 中山BGP'),(4,'db_primary','121.201.12.60','db','primary','true','主DB 中山BGP'),(5,'db_secondary','121.201.12.60','db','secondary','true','从DB 中山BGP'),(6,'node_mgr_primary_zs_bgp','121.201.12.57','node_mgr','primary','true','node_mgr 中山BGP'),(7,'node_proxy_primary_zs_bgp','121.201.12.56','node_proxy','primary','true','node_proxy 中山BGP'),(8,'node_core_primary_zs_bgp','121.201.12.57','node_core','primary','true','node_core 中山BGP'),(9,'node_mgr_primary_zs_bgp_bak','121.201.12.67','node_mgr','secondary','true','从node_mgr 中山BGP');
DBS_MAIN => array('ip' => 'localhost', 'port' => 3306, 'user' => 'root', 'passwd' => 'rjkj@rjkj' )
7 各个系统源码泄漏,里面大多含有数据库密码,管理员密码,经测试不能连接。。
https://github.com/k518/xxx/
https://github.com/k518/xxx/blob/master/eventCenter/syslogic/mysql.php
$rs=mysql_connect('api.efly.cc','root','rjkj@rjkj');
mysql_query('set names utf8');
mysql_select_db('eventCenter');
https://github.com/k518/xxx/blob/master/productCenter/syslogic/mysql.php
$rs=mysql_connect('api.efly.cc','root','rjkj@rjkj');
mysql_query('set names utf8');
mysql_select_db('productCenter');
https://github.com/k518/xxx/blob/master/gift.efly.cc/webroot/gift/db.class.php
function DB($host='ibss.efly.cc', $username='root', $password='rjkj@2009#8', $dbname='gift'){
https://github.com/k518/xxx/blob/master/web/web%E8%AE%BE%E8%AE%A1/ibss_user/Home/Conf/config.php
'DB_TYPE' => 'mysql',
'DB_HOST' => '121.9.13.254',
'DB_NAME' => 'platform',
'DB_USER' => 'root',
'DB_PWD' => 'rjkj@2009#8',
'DB_PORT' => '3306',
'DB_PREFIX' => '', //数据库表前缀
'INTERFACE_URL' => 'http://api.efly.cc',
'OPERATION_VM' => 'http://119.145.147.88:8080'
https://github.com/k518/xxx/blob/master/xen/ecloud_admin.sql
INSERT INTO `Pool` (`ID`, `GroupID`, `PoolCode`, `Data`, `State`, `NetVlanBegin`, `NetVlanEnd`, `PrivateIPBegin`, `PrivateIPEnd`, `PrivateMask`, `PrivateGateway`) VALUES
(7, 5, 'HJ-G001-P001', '{"master":"10.11.253.45","user":"root","pass":"Rjkj@efly#123","vnc_proxy_host":"121.201.55.35","vnc_proxy_port":"9000","uuid":"605c0b0b-d8d4-44a5-bba4-f82b4194186b"}', 'enabled', '2', '201', '10.11.0.2', '10.11.0.254', 24, '10.11.0.1'),
(9, 5, 'test1`22332', '111sssss', 'enabled', '99', '88', '77', '66', 55, '4444');
https://github.com/k518/xxx/blob/master/xen/uwsgi/create_temp_vm.py
master_url = "http://%s/"%('10.11.253.43')
session = XenAPI.Session(master_url)
session.xenapi.login_with_password('root', 'Rjkj@efly#123')
https://github.com/k518/xxx/blob/master/xen/mgr-script/collect2.py
master = '10.11.253.43'
slaves = ['10.11.253.44', '10.11.253.45']
user='root'
passwd='Rjkj@efly#123'
https://github.com/k518/xxx/blob/master/xen/uwsgi/create_vlan.py
session = XenAPI.Session('http://121.201.60.66:8000')
session.xenapi.login_with_password('root', 'Rjkj@free7248#8')
漏洞证明:
rt
修复方案:
rt
版权声明:转载请注明来源 prolog@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:17
确认时间:2015-08-16 00:11
厂商回复:
谢谢黑客作者的辛苦劳动,目前我们的技术人员已经在紧急排查中。
最新状态:
暂无