漏洞概要
关注数(24)
关注此漏洞
漏洞标题:携程某后台若口令导致数据沦陷(可以拖库)
提交时间:2015-06-22 17:06
修复时间:2015-08-07 10:48
公开时间:2015-08-07 10:48
漏洞类型:重要敏感信息泄露
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2015-06-22: 细节已通知厂商并且等待厂商处理中
2015-06-23: 厂商已经确认,细节仅向厂商公开
2015-07-03: 细节向核心白帽子及相关领域专家公开
2015-07-13: 细节向普通白帽子公开
2015-07-23: 细节向实习白帽子公开
2015-08-07: 细节向公众公开
简要描述:
携程某后台若口令导致敏感信息泄漏,数据库对外开放链接,完全沦陷
详细说明:
1. http://140.207.229.58:9090/
应用地址,改地址是我扫携程c端扫出来的,经确认228和229确实为携程所有
密码:admin/admin
这里边敏感信息比较多,来张图证明一下:
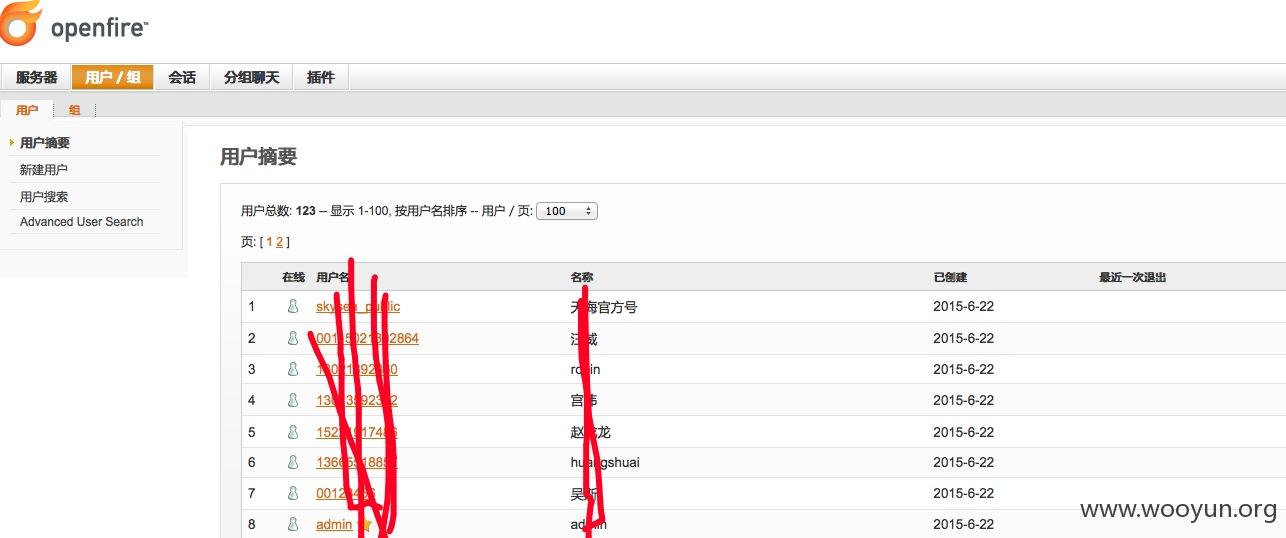
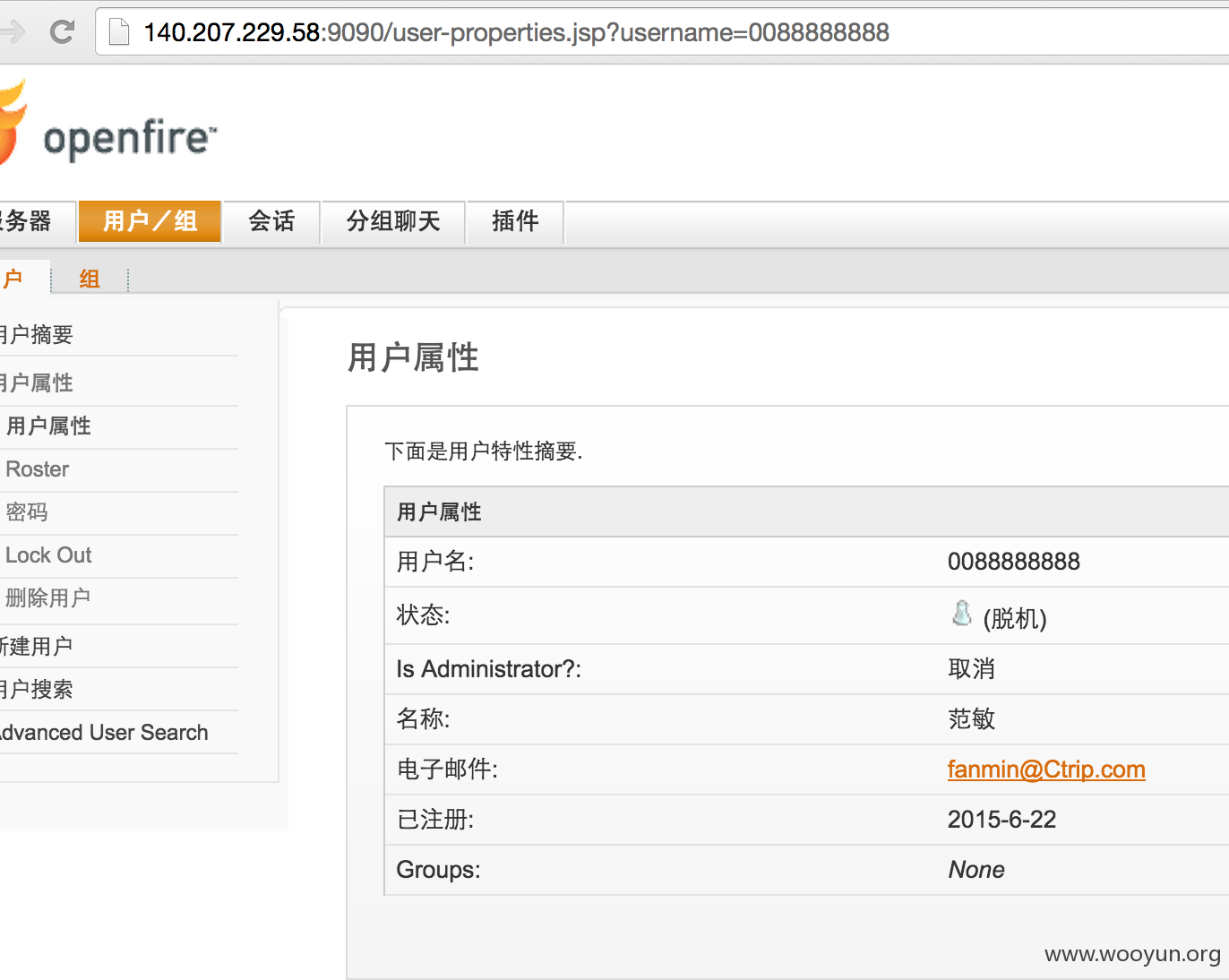
这些都没什么,系统信息中直接把数据库用户、密码直接显示出来,我只能呵呵。
2.数据库对外开放链接,数据完全公开
没查你具体数据,就不打
漏洞证明:
同上
修复方案:
修改口令,修改数据库对外链接限制。(这么多数据,数据库root,我就不拿shell了,求给个20rank)
版权声明:转载请注明来源 new@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2015-06-23 10:47
厂商回复:
非常感谢您对此漏洞信息的提交,已联系相关人员进行处理
最新状态:
暂无




