漏洞概要
关注数(24)
关注此漏洞
漏洞标题:什么值得买 存储型xss盲打后台Cookie
提交时间:2015-04-15 14:54
修复时间:2015-06-03 16:08
公开时间:2015-06-03 16:08
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:10
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2015-04-15: 细节已通知厂商并且等待厂商处理中
2015-04-19: 厂商已经确认,细节仅向厂商公开
2015-04-29: 细节向核心白帽子及相关领域专家公开
2015-05-09: 细节向普通白帽子公开
2015-05-19: 细节向实习白帽子公开
2015-06-03: 细节向公众公开
简要描述:
上次提交的和 http://www.wooyun.org/bugs/wooyun-2010-0106326 重复了,于是又来测试一番。
虽然过滤了一些常见的DOM事件,还是可以绕过。并且已经GET到后台COOKIE。
详细说明:
在晒单分享或者经验投稿处:
http://shaiwu.smzdm.com/detail_preview/198007
插入视频,视频的网址填:
保存草稿-预览文章
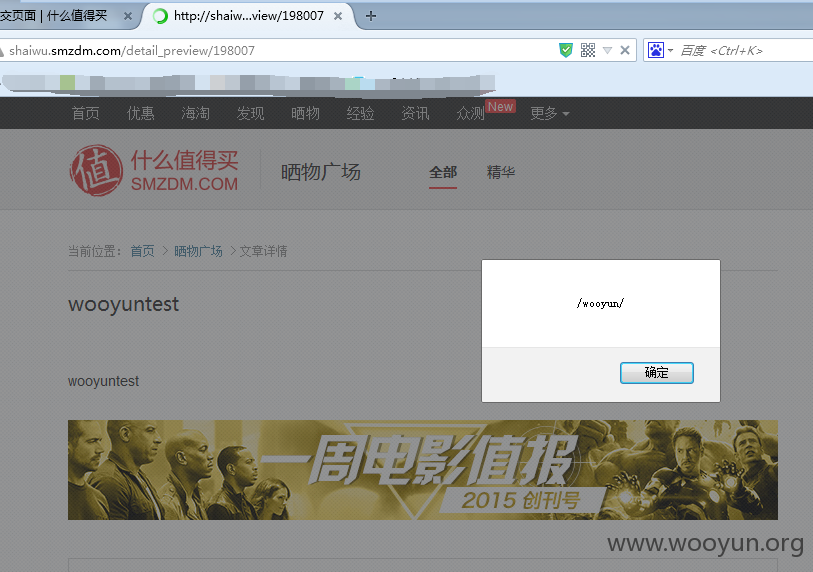
储存型xss,已经打到的后台COOKIE:
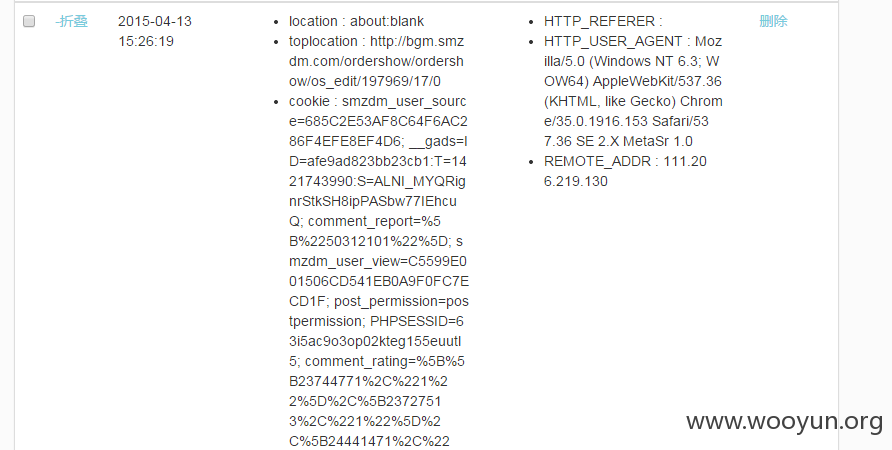
后台加了HTTP基本认证,在使用chrome浏览器的情况下无法基础认证钓鱼。
就不深入了,赶紧修补吧,不仅能打管理员cookie还是打用户的cookie。
漏洞证明:
修复方案:
漏洞回应
厂商回应:
危害等级:低
漏洞Rank:4
确认时间:2015-04-19 16:07
厂商回复:
感谢Pany自留地提交的漏洞,什么值得买已完成修复
最新状态:
暂无




