KPPW最新版SQL注入漏洞七,多处不同注入点
第一处sql注入:
文件/control/user/transaction_works.php:
注意这里:
$fileid没有引号保护进入sql语句,导致存在注入
第二,三处sql注入:
继续看下面的:
$fileid继续进入了函数delFileByFileId,跟进函数delFileByFileId:
文件:/lib/inc/CommonClass.php
这里存在两处注入,$fileid变量进入select和delete语句都没有处理,导致sql注入
第四,五,六处sql注入:
同意的问题出现在文件/control/user/transaction_works.php:
这里的问题跟上面分析的问题一样,存在注入。
第七处sql注入:
文件/control/user/transaction_works.php:
注意这里的:
这里的变量$pk进入了save函数,跟进save函数
文件/lib/inc/keke_table_class.php:
最后$pk的key进入了setWhere条件语句中,导致sql注入
第一处SQL注入:
这里会延迟5秒返回,说明UserName第一个字符为a,继续即可注入出用户信息
第二,三处SQL注入:
这里会延迟5秒返回,说明UserName第一个字符为a,继续即可注入出用户信息
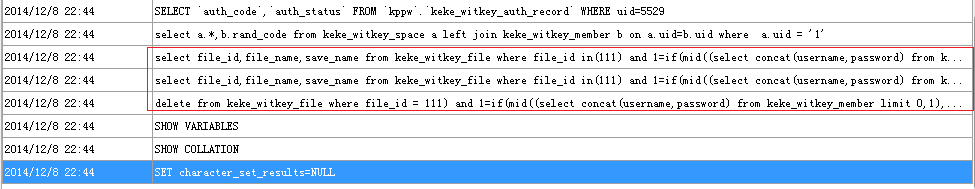
第七处SQL注入:
这里会延迟5秒返回,说明UserName第一个字符为a,继续即可注入出用户信息



