漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-064861
漏洞标题:阿里巴巴某处漏洞修复不完整!
相关厂商:阿里巴巴
漏洞作者: Nebula
提交时间:2014-06-14 08:50
修复时间:2014-07-29 08:52
公开时间:2014-07-29 08:52
漏洞类型:未授权访问/权限绕过
危害等级:低
自评Rank:5
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-06-14: 细节已通知厂商并且等待厂商处理中
2014-06-16: 厂商已经确认,细节仅向厂商公开
2014-06-26: 细节向核心白帽子及相关领域专家公开
2014-07-06: 细节向普通白帽子公开
2014-07-16: 细节向实习白帽子公开
2014-07-29: 细节向公众公开
简要描述:
RT!
详细说明:
正好等看世界杯比赛,顺便看看!
WooYun: 内网编织者阿里巴巴集团各业务内网来回编织!
漏洞证明:
现在是对ip访问基本都限制了,还有就是配置了内网ip数量比较多的域名:*.alibaba-inc.com也限制了!
但其他类型的url访问及权限绕过还是有不少的,这里我看了一下,大致分三种的权限绕过访问没处理(其实就是一种:公司所有域名):
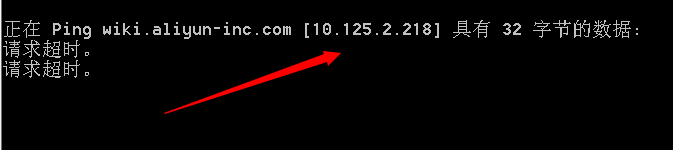
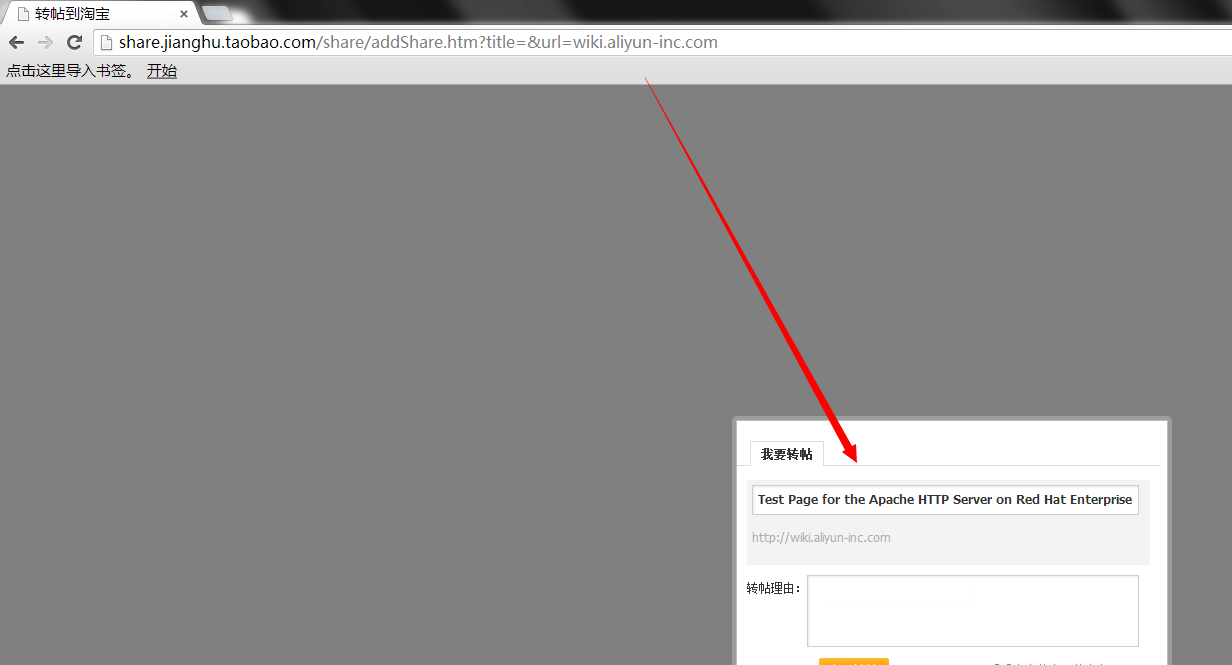
1.比较多的是,配置内网ip的域名,如:
http://share.jianghu.taobao.com/share/addShare.htm?title=&url=wiki.aliyun-inc.com
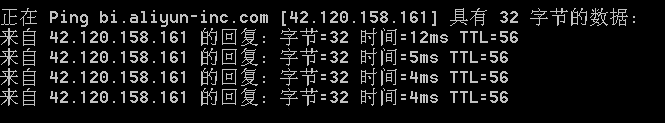
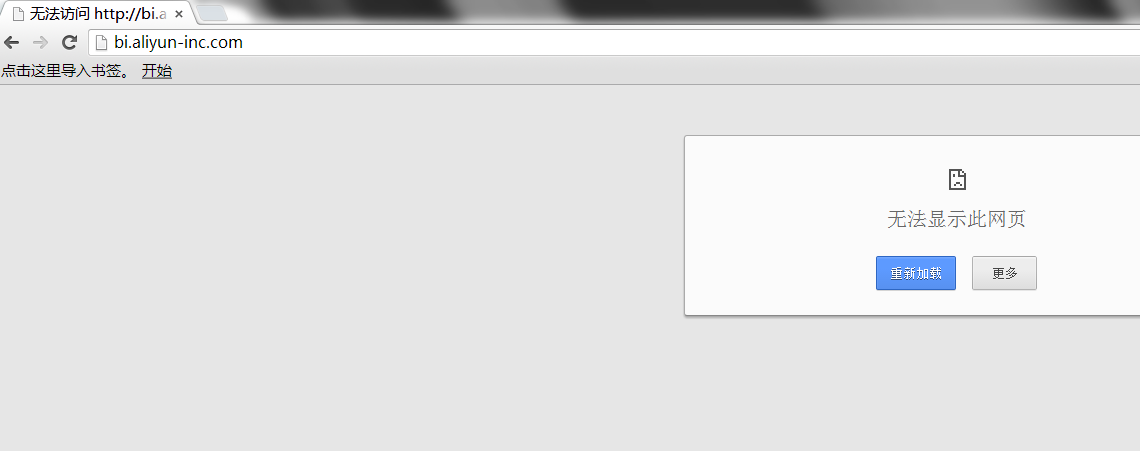
2.域名配置外网ip,但外网访问有ip限制:
http://share.jianghu.taobao.com/share/addShare.htm?title=&url=bi.aliyun-inc.com
3.对页面访问有ip限制:
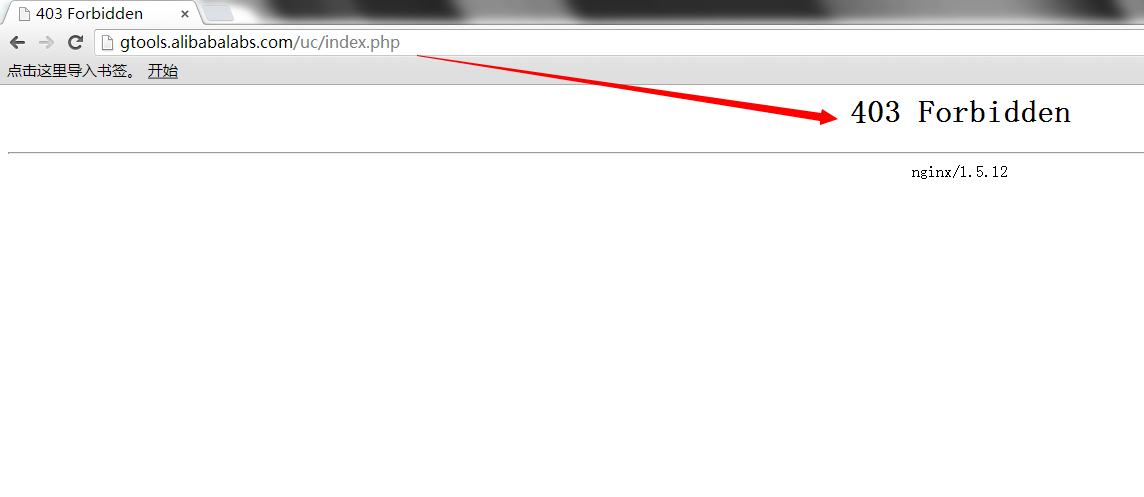
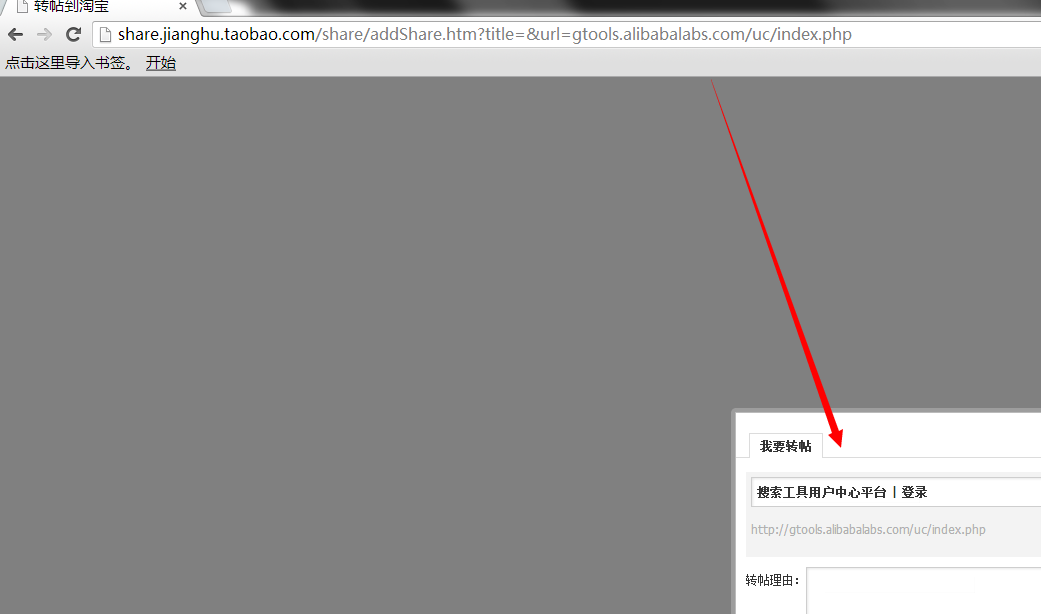
http://share.jianghu.taobao.com/share/addShare.htm?title=&url=gtools.alibabalabs.com/uc/index.php
然后其他信息找了一些:
http://share.jianghu.taobao.com/share/addShare.htm?title=&url=ditu.alibabalabs.com
http://share.jianghu.taobao.com/share/addShare.htm?title=&url=cacti.taobao.com
http://share.jianghu.taobao.com/share/addShare.htm?title=&url=cpgw.taobao.com
http://share.jianghu.taobao.com/share/addShare.htm?title=&url=api.ctu.taobao.com
http://share.jianghu.taobao.com/share/addShare.htm?title=&url=antispam.feedback.taobao.com
http://share.jianghu.taobao.com/share/addShare.htm?title=&url=view.lz.taobao.com
http://share.jianghu.taobao.com/share/addShare.htm?title=&url=svn.simba.taobao.com
http://share.jianghu.taobao.com/share/addShare.htm?title=&url=bugfree.corp.taobao.com
选了几个域名,字典稍微fuzzing一下(也发现不少):
*.aliyun-inc.com
l.aliyun-inc.com/10.101.168.181
t.aliyun-inc.com/10.230.230.56
ak.aliyun-inc.com/10.138.138.21
bi.aliyun-inc.com/42.120.158.161
go.aliyun-inc.com/42.120.218.191
ls.aliyun-inc.com/42.156.234.5
qa.aliyun-inc.com/10.125.8.229
abc.aliyun-inc.com/42.156.141.171
act.aliyun-inc.com/42.156.141.193
cat.aliyun-inc.com/112.124.142.2
crm.aliyun-inc.com/42.120.158.217
jwx.aliyun-inc.com/42.120.218.9
msc.aliyun-inc.com/42.120.158.213
scm.aliyun-inc.com/10.230.204.45
sla.aliyun-inc.com/42.156.141.247
sls.aliyun-inc.com/10.206.120.26
soc.aliyun-inc.com/110.75.102.152
svn.aliyun-inc.com/10.230.202.47
tms.aliyun-inc.com/10.147.208.62
umm.aliyun-inc.com/10.138.138.21
wiki.aliyun-inc.com/10.125.2.218
......
*.alipay.com
adc.alipay.com/110.75.149.119
ads.alipay.com/110.75.149.200
ars.alipay.com/110.75.149.142
bcm.alipay.com/110.75.149.21
crm.alipay.com/110.75.149.22
fbi.alipay.com/110.75.143.170
hjc.alipay.com/110.75.149.81
idb.alipay.com/110.75.149.156
kmi.alipay.com/110.75.149.38
......
*.alibaba.com
dse.alibaba.com
......
*.alisoft.com
alisoft.com/127.0.0.1(当前url页面解析所在服务器)
*.aliloan.com
x.aliloan.com/172.18.74.74
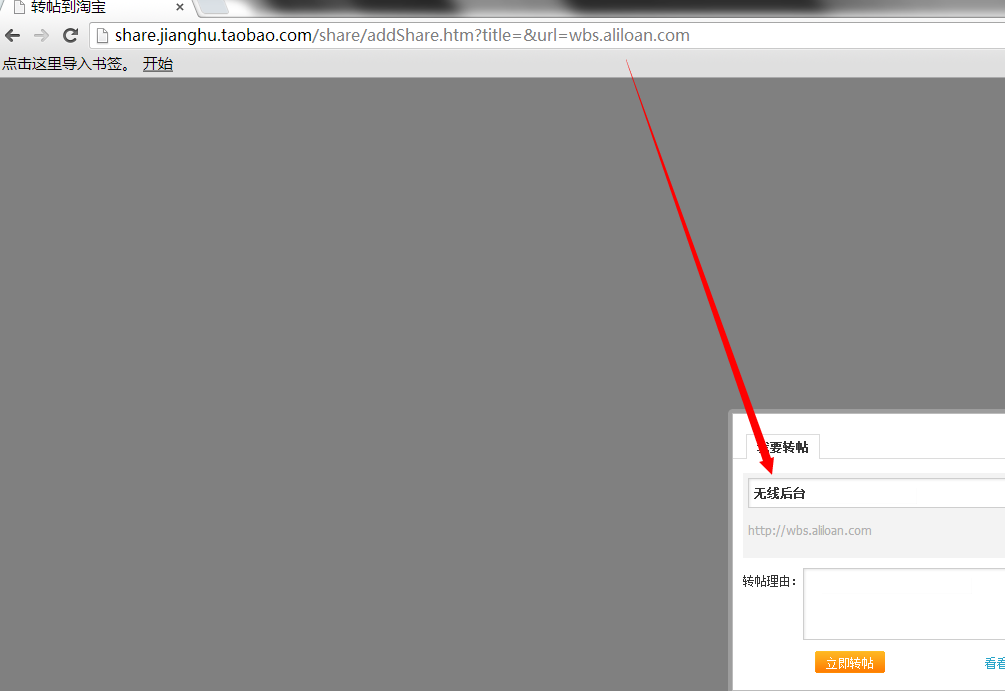
wbs.aliloan.com/42.120.158.205
修复方案:
可能限制的正则代码要加长点了(如果这个只是临时补丁或者业务需要可以承受风险,这个问题可以忽略!)
版权声明:转载请注明来源 Nebula@乌云
漏洞回应
厂商回应:
危害等级:低
漏洞Rank:3
确认时间:2014-06-16 16:47
厂商回复:
感谢您对我们的关注和支持,该漏洞我们正在修复!
最新状态:
暂无