首先我通过一系列的社工进入了学校的监控系统,这不是重点,登陆之后系统要求我下载一份cab于是我下载,之后发现是软件包
![_KFXE4KP(AKX]$7W(2)GSRM.jpg](http://wimg.zone.ci/upload/201402/19130612a1b536af3c188e20c5ca91ea701cff18.jpg)
之后打开主程序
如图
下载到本地之后发现并不需要密码和账户即可连接,只需要注册到注册表
reg文件的内容如下
并没有什么特殊的限制貌似只要是同型号的监控设备都能进去吧
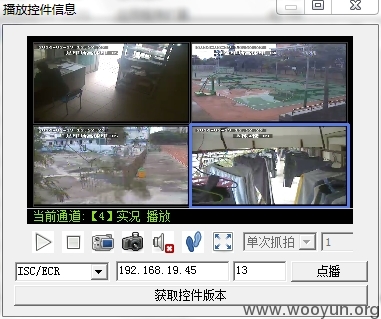
于是我为了证实,我将文件包放到虚拟机上,虚拟机上从来没有通过web登陆过监控设备,再用这个软件能够登陆吗?
实验如下
![HZ[W0C8Z]S(OWU{`8Z10626.jpg](http://wimg.zone.ci/upload/201402/19130305010daf2a03edcb543bc2a094f37dc23c.jpg)
在windows2008上测试只需注册之后点击查看播放控件即可
为此我查看了登陆的日志文件
内容截取一段如下
可以看到,程序貌似只是匹配了端口就能够登陆成功呢?



![_KFXE4KP(AKX]$7W(2)GSRM.jpg](http://wimg.zone.ci/upload/201402/19130612a1b536af3c188e20c5ca91ea701cff18.jpg)


![HZ[W0C8Z]S(OWU{`8Z10626.jpg](http://wimg.zone.ci/upload/201402/19130305010daf2a03edcb543bc2a094f37dc23c.jpg)
![HZ[W0C8Z]S(OWU{`8Z10626.jpg](http://wimg.zone.ci/upload/201402/19130405c6e0dd0532f96a3682789e85bb411392.jpg)