漏洞概要
关注数(24)
关注此漏洞
漏洞标题:上海电信某处服务配置不当导致一系列问题
提交时间:2014-08-11 10:15
修复时间:2014-09-25 10:16
公开时间:2014-09-25 10:16
漏洞类型:系统/服务运维配置不当
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
Tags标签:
无
漏洞详情
披露状态:
2014-08-11: 细节已通知厂商并且等待厂商处理中
2014-08-16: 厂商已经确认,细节仅向厂商公开
2014-08-26: 细节向核心白帽子及相关领域专家公开
2014-09-05: 细节向普通白帽子公开
2014-09-15: 细节向实习白帽子公开
2014-09-25: 细节向公众公开
简要描述:
可惜我不用电信的东西.呵呵.这是一个不通过的,今天心血来潮重新看了看.
详细说明:
http://116.228.171.57:8090/ismp/spportal/
http://116.228.171.57:8090/ismp/cnlportal/
http://116.228.171.57:8090/ismp/euportal/
http://116.228.171.57:8090/ismp/opportal/
Jboss 弱口令
admin/admin
然后封装个war包上传就行了
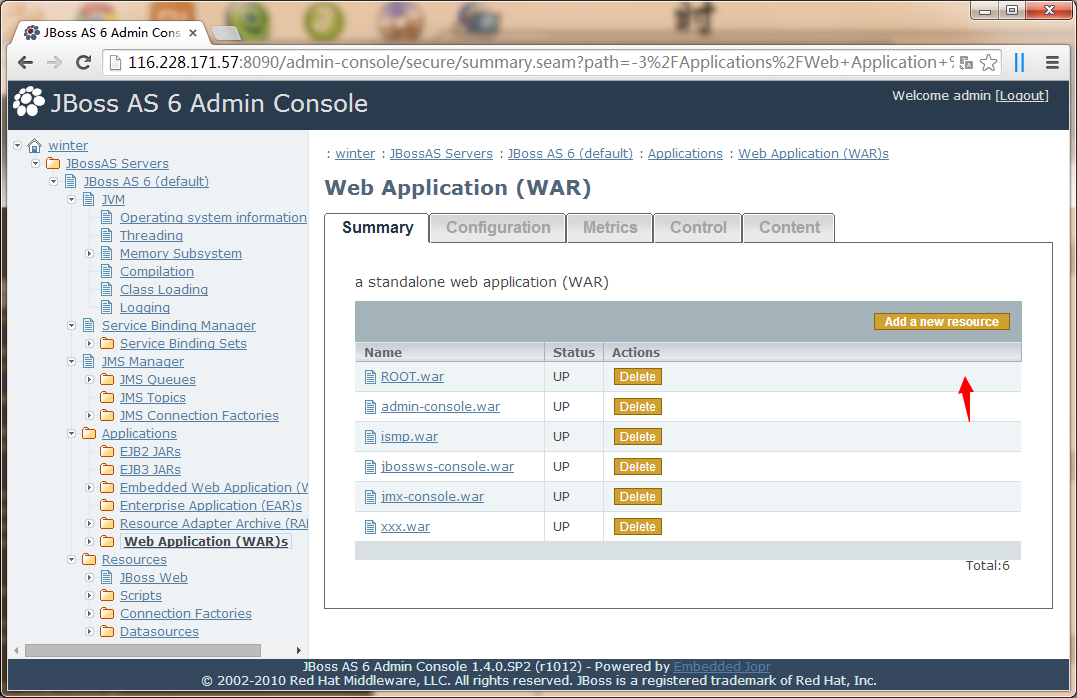
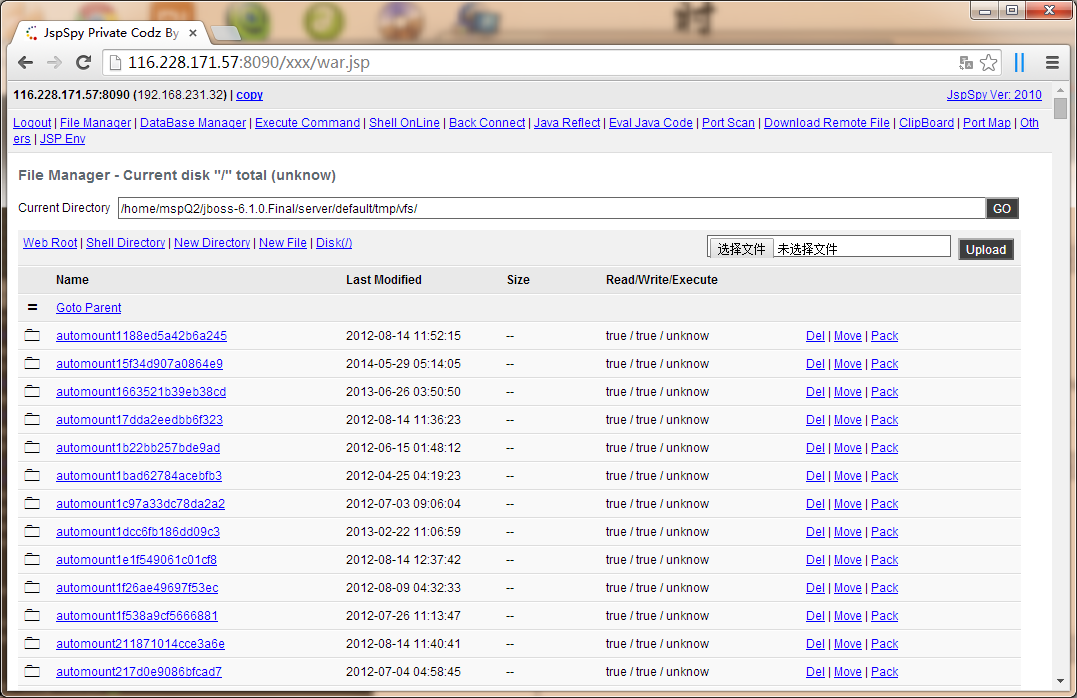
然后提权了
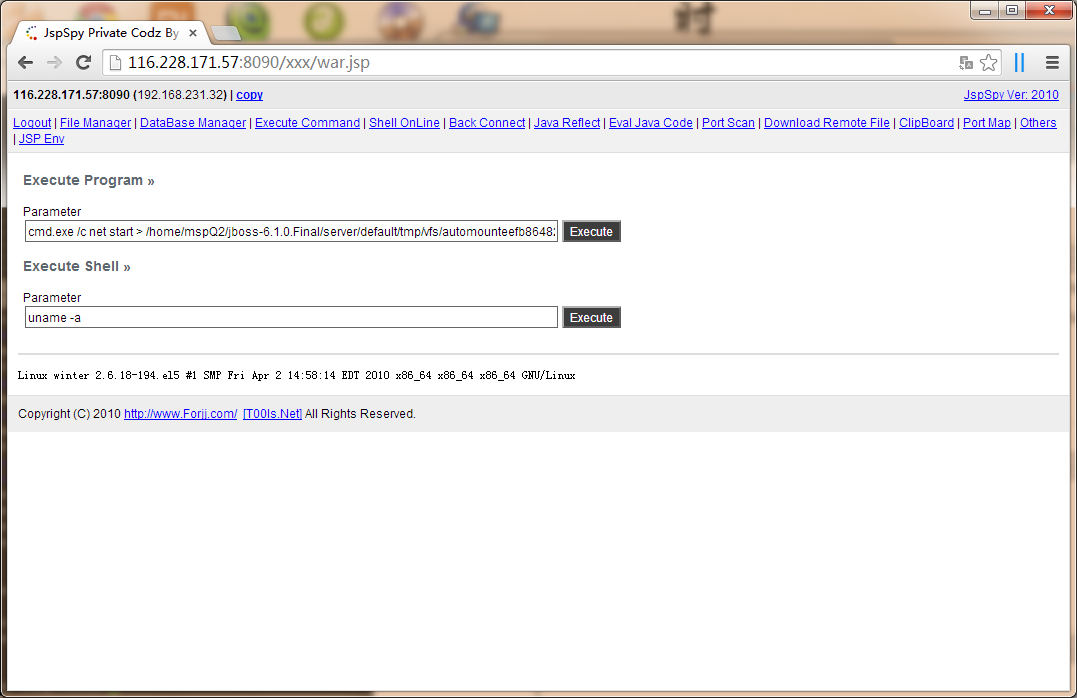
漏洞证明:
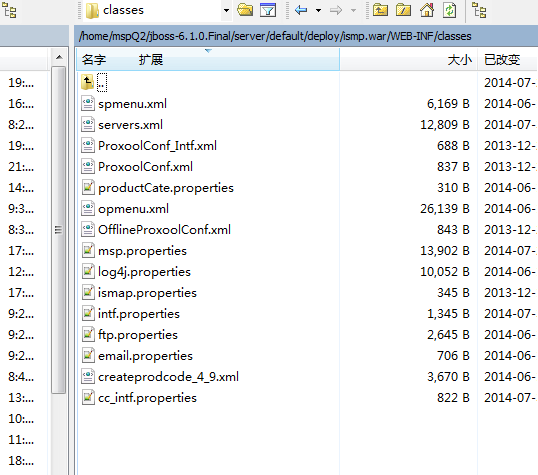
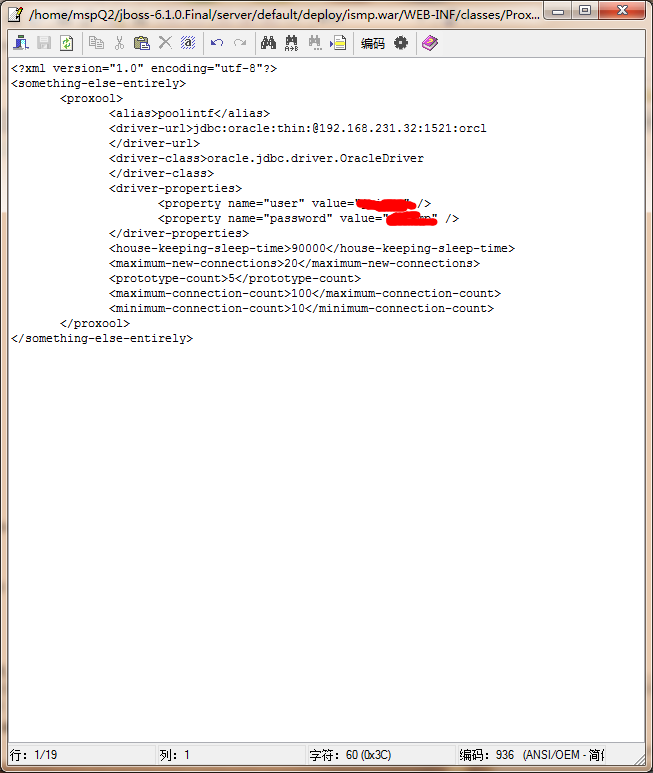
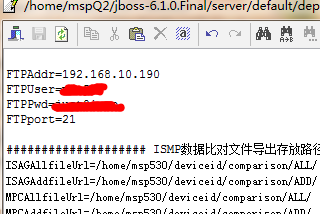
然后连上数据库看看
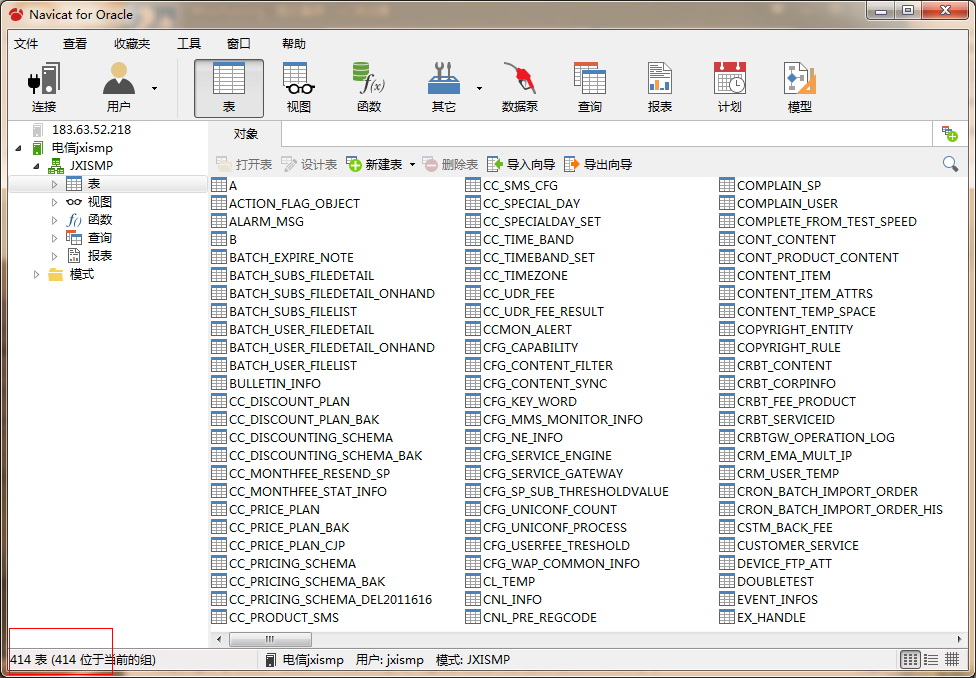
还可以内网渗透哦
就不深入了.
修复方案:
电信业务线长,得加强对运维的要求,
弱口令层出不穷,也是能根本的解决的,教育运维叔叔
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:14
确认时间:2014-08-16 08:32
厂商回复:
最新状态:
暂无









