站点1:
oa.king.tcl.com TCLoa办公系统
使用搜索引擎,搜索关键字,发现该系统出现2个域名
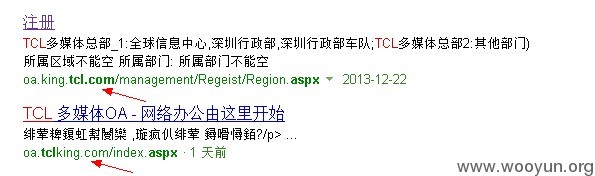
故再次进行了一次安全测试
与 WooYun: TCL#某重要办公系统存在漏洞导致SQL注射及信息泄露 属于同一系统,不过域名不同,厂商是不是部署了2套oa系统,忘了统一了?
ip反查也标明2个域名访问的页面相同,不过ip地址不同
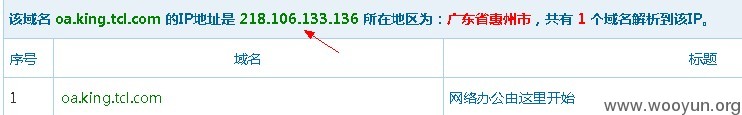
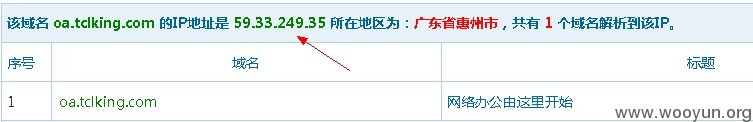
http://oa.king.tcl.com/management/Regeist/Region.aspx
此页面的txt_Account参数没有过滤导致注射漏洞
burp抓post包
站点2:
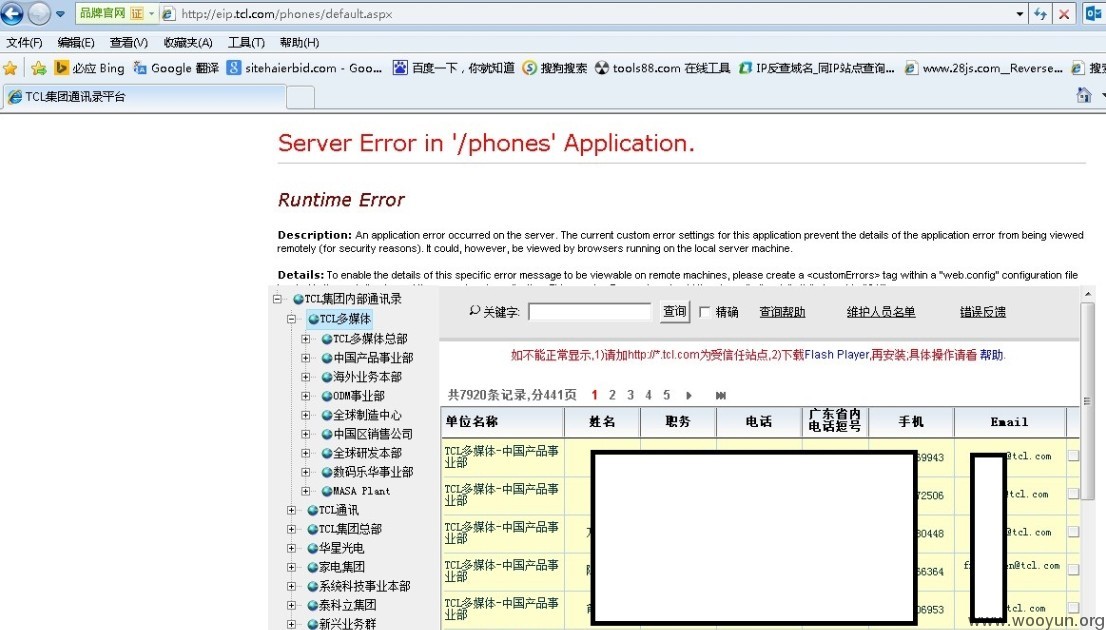
http://eip.tcl.com/phones/login.aspx TCL集团通讯录平台
直接访问eip.tcl.com,提示网站建设中
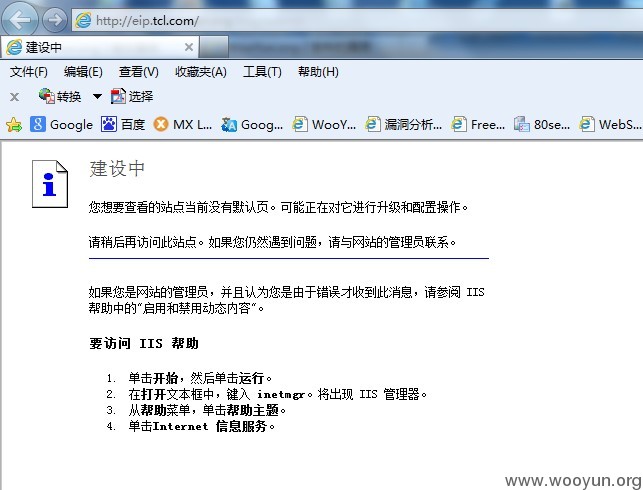
使用谷歌搜索引擎进行关键字识别
用户名密码弱口令 lif 111111
登录通讯录平台,1w多员工信息泄露。
站点3:
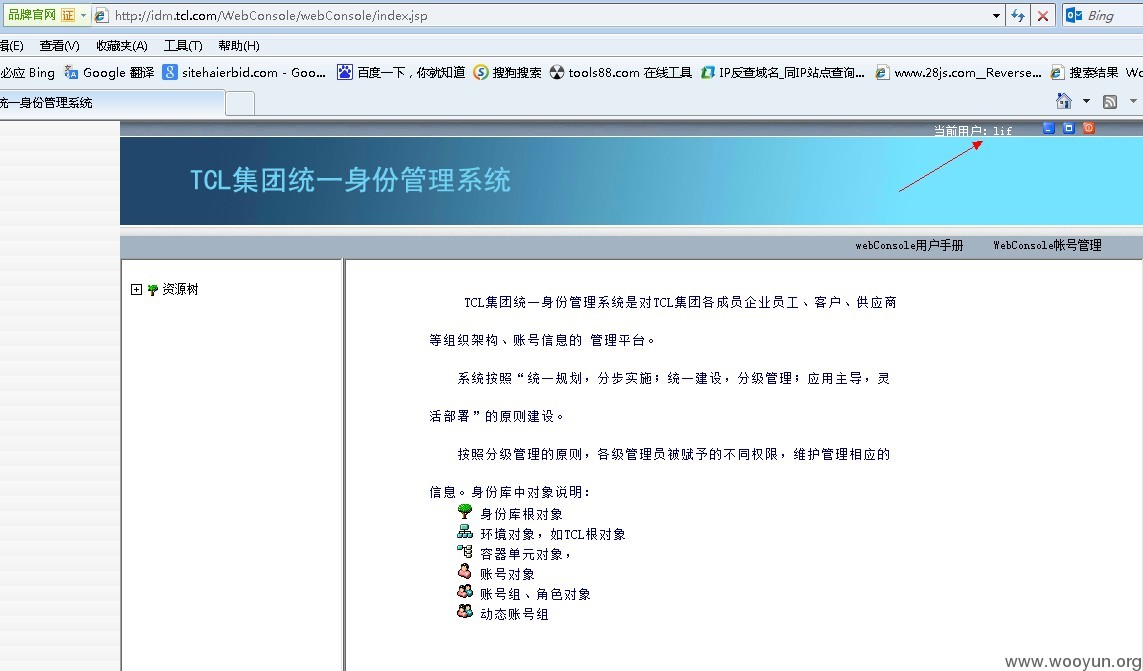
http://idm.tcl.com/WebConsole/login/login.jsp TCL统一身份管理系统
依旧使用弱口令lif 111111 可以进入
未深入
over









